Cellular Automata Data Encryption - Open Source - Free to Use!
Data encryption algorithm developed by myself as a thesis project which was driven by my interest in cellular automata (CA). I initially developed it to be used for instant messaging. But as it turns out it is trickier when you want to encrypt and send data with the same key. With that in mind, I've decided to make it a data encryption algorithm which encrypts text data.
It works by requiring 3 inputs from the user, a pin number, a password and the data itself.
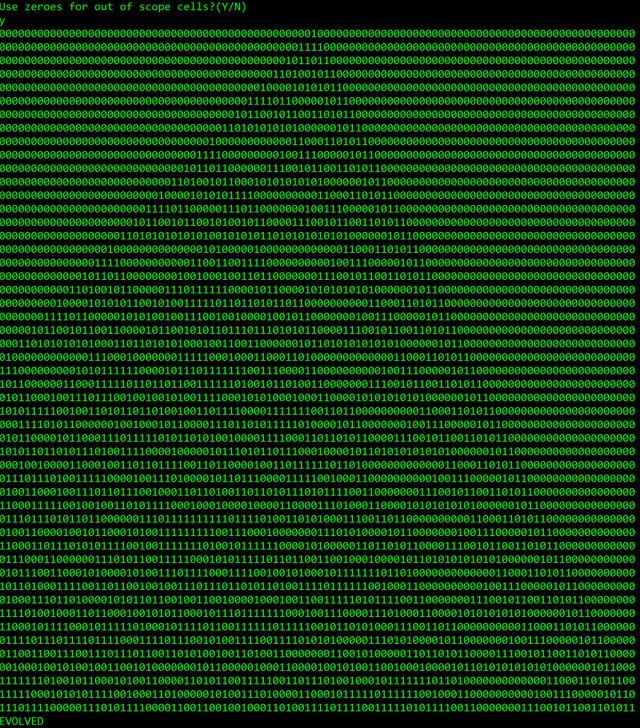
When I say a pin number it's actually the evolutionary stage of the cellular automata and it looks something like this (starting from one alive cell):
"0" Represents "Dead" and "1" represents "Alive" cells. Each line represents an evolutionary stage.
The pseudorandom data is then XOR'ed with the data. The data you input in the first place generates a key that is as long as the data which solves the security issue with XOR.
So encrypted data looks like this with the decrypted data below it:
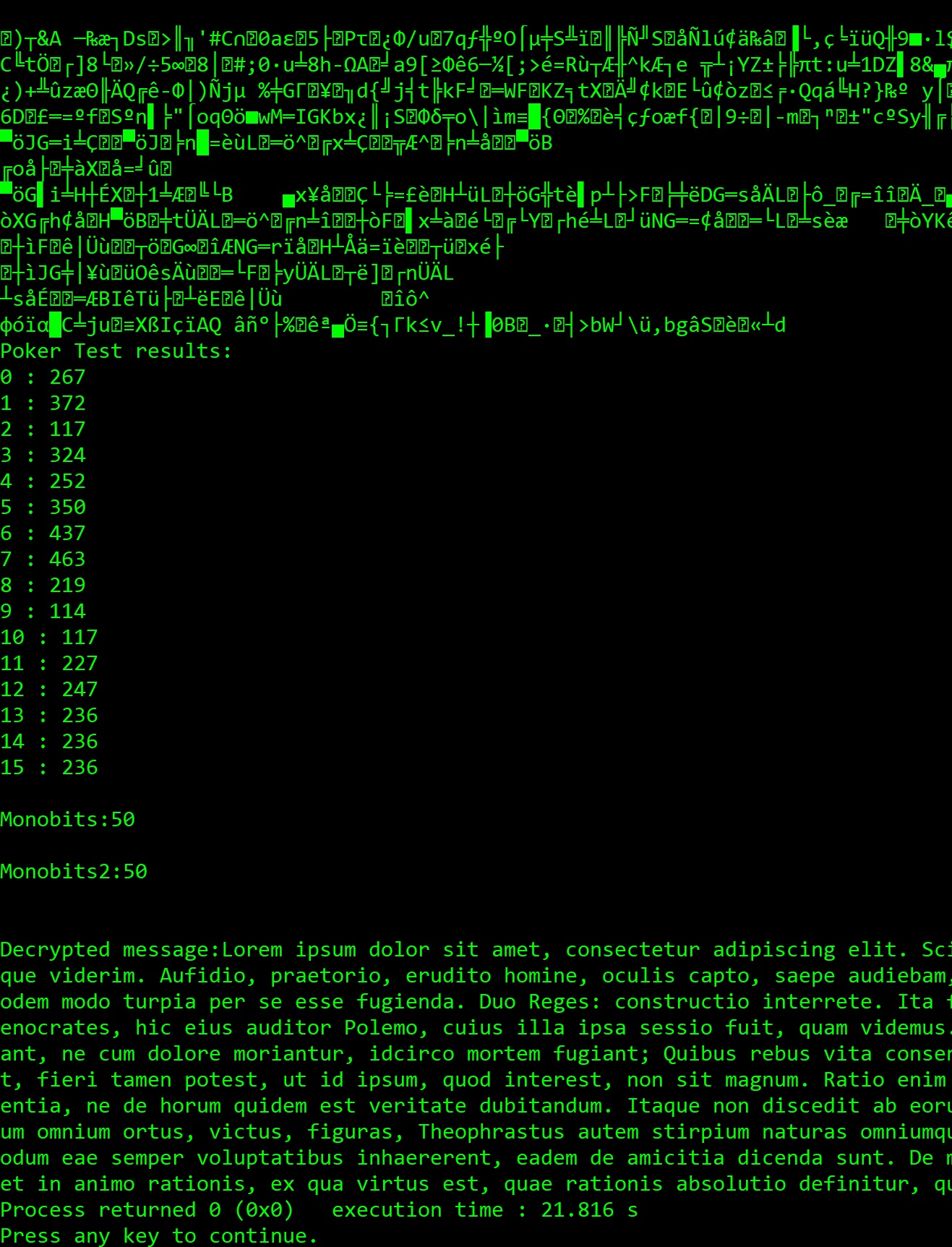
Monobit test and poker test are the crypto tests to ensure security.
You can also download and try it yourself to encrypt your sensitive data.
What can you do with it?
- I encrypted my ethereum wallet file which is in text format, wanted another security measure over my wallet.
- Encrypt your private information on your computer to stop anyone else reading it.
- You can also use it as a key chain. If you have saved passwords in a text file you can put them all in one text file and encrypt it so when you want to use it you can decrypt it with your pin and password.
Download Windows x64 version 1.1
or
Go to GitHub page to compile on your own:
https://github.com/karusb/1DCAEncryption
Please read the README.txt before you use program.
wavi
Hey, thanks for sharing this! I'll take a look at the github later tonight. What benefits does your algorithm have over other algorithms?
@seopril Good question. When you encrypt your data it's almost as if you are hashing it, so you cannot reverse the process unless you actually know the pin (generation number) and password to generate large key that is used to encrypt. Though it's not a hash function because the output is not fixed.
Hello! I just upvoted you! I help new Steemit members! Upvote this comment and follow me! i will upvote your future posts! To any other visitor, upvote this post also to receive free UpVotes from me! Happy SteemIt!
I followed you thanks for your upvote!
I am Groot! :D