What you need to know about the private keys
Whosoever controls the private key controls the coin
.jpg)
Is A Number But Very Important
A non-public key is a complicated type of cryptographic code that lets users attain get entry to to their cryptocurrency. A non-public key is a core section of each bitcoin and altcoin, and its impervious nature ensures that users are blanketed from theft and unauthorised get entry to to their funds.
In effect, it is a string of characters that can be used in the encryption or decryption of a given algorithm. These keys have been a key part of crypto transactions considering that 2008, even though wallets that have been developed extra lately have been built with techniques that enable users to operate them without having to apprehend the complexity of this software.
Guild it like a precious stone
In essence, the ownership of the private key of a coin capability that you are the owner of that coin. In different words, every person who has get admission to to a coin’s personal keys can use them to send a transaction. Any entity who possesses a private key can create a valid transaction.
Many opportunities are handy for these who desire to steal personal keys. The most common have a tendency to be storage media and communications channels. Because of this, one should be very cautious each time storing or transmitting non-public keys.
.jpg)
Software wallets typically take care of personal keys in a “wallet file” that can be kept somewhere facts is stored. By default, a computer will store this file in a standard, regular directory when the pockets software is installed, making it a important target for malware that pursuits crypto.
To fight this threat, software program wallets furnish customers with the possibility to encrypt the wallet file. Any hacker attempting to gain get admission to to the pockets file would then need to decrypt it. The complexity of doing this varies on the nice of the encryption and electricity of the password being utilized. Most wallet documents can be encrypted on software wallets via the simple addition of a password.
Many crypto users select to again up their pockets files. While this is generally a suitable idea, this practice has the attainable to leak personal keys. For example, it can be tempting to retailer a backup of your software wallet to a cloud storage service. However, every body capable to view this backup online would be in a function to acquire get entry to some or all of your funds.
A very similar problem can come about via emailing backups to your self or leaving a private key around at your house. Encryption can decrease the threat of compromise, however can’t hold you definitely safe.
Private Keys are used to sign and send crypto transactions
.png)
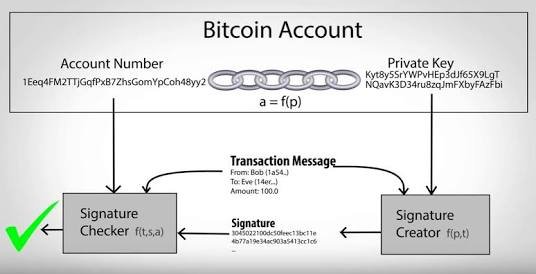
To forestall forgery, the Bitcoin community ensures that each transaction has a “digital signature”. This signature, like a non-public key, is simply a wide variety selected from a very giant range. Wallet software produces a signature with the aid of mathematically putting forward a transaction collectively with the terrific private key.
This gadget is useful because absolutely everyone with a transaction and its signature can be certain of the authenticity of a message. However, a transaction signature is nearly impossible to fake. The possible way to create a valid signature for a given transaction is to utilize the excellent personal key.
As antagonistic to a signature you would write in actual life, a transaction signature modifications if the transaction changes even a little bit. The way the signature will change is impossible to predict, making certain that solely a character in possession of a non-public key can provide the correct signature.
Private keys are used to make public address
.jpg)
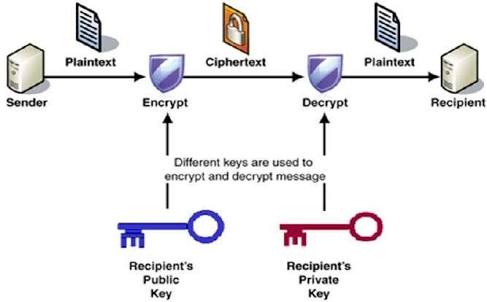
Public key cryptography is frequently utilised to impervious electronic communication over an environment with an open network, an instance being the Internet, barring having to count on a hidden channel. They make messages unreadable, working with personal keys to make sure security.
A public key comes from encrypting a private key with a set of mathematical equations. They work together in a type of mathematical trapdoor, some thing you can feature that’s handy to function in one direction, however cannot in the other. This uni-directional trapdoor is at the core of Bitcoin’s safety model.
No network is required at any point in the introduction of a non-public key or the address. Every computer on the Bitcoin network is conscious of the complex mathematical relationship between public and private keys. This allows each and every member of the community to pick out non-public keys and sign transactions in separation to the Bitcoin network. The big personal keyspace permits that any properly-selected key will be unique.
I need this information. Thanks for the post.
Thanks for stopping by.
nice informative post
Thanks