US Air Force Confidential Document Leakage UAV Operation Manual Dark Net Sale
Last month, the threat intelligence company Recorded Future found an auction of the embargoed weapons MQ-9 Reaper drone operation manual in the surveillance of conventional darknet criminal activities. The Insikt Group's team of analysts, Recorded Future, pretend that potential buyers are participating in the auction and are in contact with newly registered English-speaking hackers before confirming the validity of the defamatory documents.

Further interactions allowed analysts to discover other hacked military data held by the hacker. The hacker claimed to be able to get a lot of military documents from a military officer.
These documents include the M1 Abrams series of main battle tank maintenance manuals, tank squad training courses, team survival training courses, and IED removal strategy documents.
Subsequent investigations revealed that the information was obtained from at least one, more likely multiple, unsecured FTP servers. Recorded Future said: "The attacker used well-known tactics to gain access to the Netgear router by setting up improper FTP login credentials."
Researchers warned two years ago that Netgear routers with remote data access are vulnerable to intrusions if they don't update the default FTP authentication credentials. Although two years have passed, the problem still exists and is still widespread. Recorded Future found more than 4,000 vulnerable routers in the study.
The exploit is not difficult. Using Shodan's host data search engine, hackers scanned a large number of Internet segments and looked for a standard 21-port router to hijack all valuable documents on compromised machines.
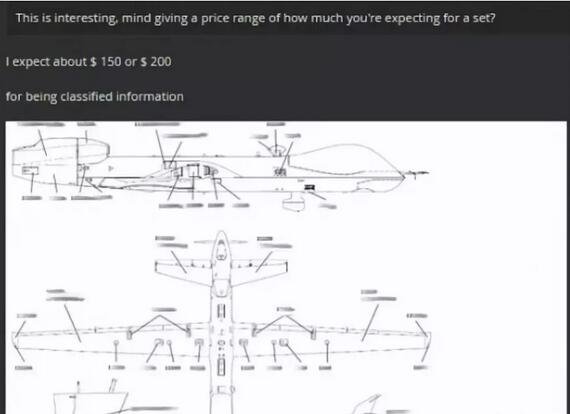
The hacker first infiltrated the computer of a captain of the 432d aircraft maintenance squadron Reaper Maintenance Team of the Crich Air Force Base in Nevada, stealing a series of sensitive documents, including the Reaper drone maintenance training materials, and responsible for maintaining the reaper. List of people. Although the textbook itself is not confidential, it is possible to evaluate the technical capabilities and weaknesses of the world's most advanced drones in the hands of those who care.
The captain's computer seems to have been intruded recently. Although he completed the network security awareness training, he did not set a password for the FTP server that stores sensitive files. This makes it easy for hackers to download the drone maintenance manual. The specific sources of the other dozens of manuals sold by the hacker have not yet been determined.
“The source of the manual was not disclosed to the Recorded Future, but judging from the content, it should be stolen from the Pentagon or an army officer.”
Such a hacker has inadvertently revealed that he has the habit of viewing sensitive videos from border surveillance cameras and drone surveillance. He also boasted that he even intercepted a video of an MQ-1 Predator drone that was cruising over Jock Tash in the Gulf of Mexico.
The researchers dug up the name and country of residence of a person who is believed to be an illegal sale of the US military manual. Recorded Future did not identify the country responsible for the matter, but said it would continue to cooperate with the judiciary to investigate confidential document transactions.
Some early evidence suggests that this is a single hacker or small hacker team committing crimes, not hacking with organized crime or state support.
“The military response team will determine the specific coverage of the leak. But the fact that a medium-level hacker can find several vulnerable military targets and leak high-sensitivity information within a week shows that there is a strong technology and The horror team supported by financial support will achieve such a horrifying result."
The dark market is full of all kinds of illegal information, including personal information, but confidential documents are rarely involved. This latest military handbook sale case is unprecedented.
“It’s not uncommon to find sensitive data such as personally identifiable information (PII), login credentials, financial information, and medical records on the dark. But cybercriminals rarely steal and sell military documents on the open market.”