Bitcoin income from WannaCry ransomware attacks expected to increase
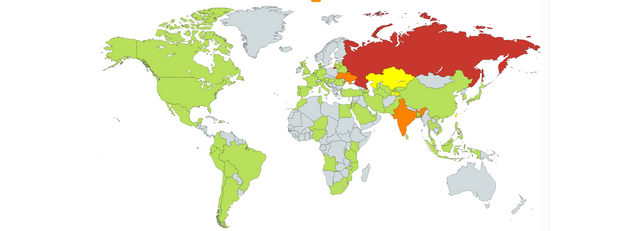
A massive round of ransomware attacks was observed on Friday across the globe. The attackers successfully infected large institutions and companies in about 150 countries, including the United States, United Kingdom, Spain, Russia, Taiwan, France, and Japan. The ransomware only affects Microsoft Windows operating systems. Among infected victims are a large number of workstations at UK National Health Service (NHS) hospitals. Europol states the ransomware attack, dubbed WannaCry, is at an “unprecedented level,” and requires international investigation.
“The latest version of this ransomware variant, known as WannaCry, WCry, or Wanna Decryptor, was discovered the morning of May 12, 2017, by an independent security researcher and has spread rapidly over several hours, with initial reports beginning around 4:00 AM EDT, May 12, 2017. Open-source reporting indicates a requested ransom of .1781 bitcoins, roughly $300 U.S.” - United States Computer Emergency Readiness Team (US-CERT)
The NHS acknowledged the attacks on Friday, “as at 15.30, 16 NHS organisations had reported that they were affected by this issue.” In an updated statement on Saturday, the organisation said they had received no reports of patient data being compromised.
Other reported victims include Spanish multinational broadband and telecommunications provider Telefonica, American multinational courier delivery services company FedEx and universities in China.
The culprit is a new variant, v2.0, of the Ransom.CryptXXX family of ransomware, which is detected as Ransom.Wannacry and is also known as Wcry or WanaCrypt0r ransomware, states American software company Symantec. It was detected early on Friday by independent security researcher MalwareHunter.
Version 1.0 of this ransomware was discovered by Malwarebytes researcher S!Ri on February 10. Microsoft released a security update in March, which addresses the vulnerability that these attacks are exploiting. “Those who have Windows Update enabled are protected against attacks on this vulnerability,” the company claimed on Friday.
Following the Friday attacks Microsoft provided security updates to protect Windows platforms that are in custom support only, including Windows XP, Windows 8, and Windows Server 2003. The company added that customers running Windows 10 were not targeted by the attack.
In its Saturday’s statement, the NHS wrote that the reason some of their systems were not updated “may be because some expensive hardware (such as MRI scanners) cannot be updated immediately.” However, in those circumstances, they will mitigate risks such as by isolating the device from the main network.
“The exploit code used by WannaCrypt was designed to work only against unpatched Windows 7 and Windows Server 2008 (or earlier OS) systems, so Windows 10 PCs are not affected by this attack.” - Microsoft
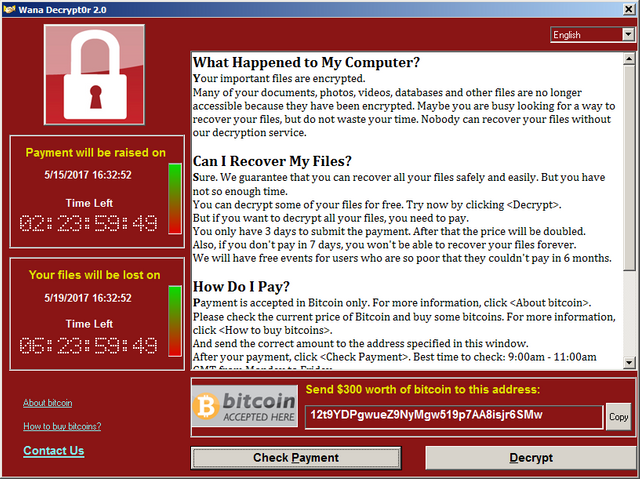
The ransomware presents a text file demanding $300 worth of bitcoin, with no other payment options. The message provides instructions for paying the ransom, and starts a countdown timer. The victim has 3 days to pay before the ransom doubles. If the ransom is not paid in 7 days, the files will be permanently unrecoverable.
According to Microsoft, the message is localized in 28 languages; Bulgarian, Chinese (simplified), Chinese (traditional), Croatian, Czech, Danish, Dutch, English, Filipino, Finnish, French, German, Greek, Indonesian, Italian, Japanese, Korean, Latvian, Norwegian, Polish, Portuguese, Romanian, Russian, Slovak, Spanish, Swedish, Turkish, and Vietnamese.
Three bitcoin addresses were reported to have been used by WannaCry’s latest version. Bitcoins started pouring into each of the three accounts on May 12. Despite the tens of thousands of infected computers worldwide, all demanding $300 so far, only a little over $36,000 USD has been sent to the attackers.
WannaCry V2.0 addresses:
13AM4VW2dhxYgXeQepoHkHSQuy6NgaEb94 had 47 transactions worth over 6.7 bitcoins, or ~US$12,000.
12t9YDPgwueZ9NyMgw519p7AA8isjr6SMw had 50 transactions worth almost 9 bitcoins, or ~US$16,000.
115p7UMMngoj1pMvkpHijcRdfJNXj6LrLn had 39 transactions worth almost 4.7 bitcoins, or ~US$8,300.
“That could well go up though,” says Microsoft Regional Director Troy Hunt, who has examined the attack in depth. “Regardless of the kill switch, many machines remain infected and if there's a 3-day window of payment before the cost escalates, you'd expect plenty of people to be holding off for a bit. It'll be interesting to look at those Bitcoin addresses in another 48 hours.”
Jonathan Levin, a co-founder at blockchain forensics startup Chainalysis investigated the addresses and linked them to addresses at many different Bitcoin exchanges, presumably where the victims purchased their ransom payoffs. Of the 30+ exchanges Chainalysis found, Russian favorite BTC-E was the most used exchange to purchase the coins that sit in the three addresses today.
When asked which country was hit the hardest by recent attacks, Levin told Quartz, “If you look at the infection rates, a lot of it is in Russia, so [the data] is complementing that. Given that we know the infections are also in Russia, I would say, it’s Russian users.”
Kaspersky Lab’s Global Research and Analysis Team agrees. “We have recorded more than 45,000 attacks of the WannaCry ransomware in 74 countries around the world, mostly in Russia,” the researchers stated. A chart on their website shows that over 70 percent of the outbreak’s victims, as discovered by their team, are in Russia, with another five percent in Ukraine.
Microsoft explained that the ransomware threat spread so rapidly as it’s also a worm. This type of malware infects a computer and looks for other connected computers to spread to. This particular worm was developed by the NSA, part of the infamous Shadowbrokers cyber weapons auction.
These software attack vectors are usually social engineered or email driven, relying on users downloading and executing a malicious payload. Calling WannaCry a “unique case,” the Microsoft explained that this ransomware “incorporated publicly-available exploit code for the patched SMB EternalBlue vulnerability.”
The NSA’s Eternal Blue exploit allows the ransomware to spread across computer networks through a vulnerability in commonly used Windows file-sharing systems. This explains why WannaCry has spread rapidly jumping between any linked organisations that may have file-sharing arrangements set up for business purposes.
“What makes Wannacry dangerous is that the attackers are leveraging a Windows exploit developed by NSA called EternalBlue, and reportedly leaked and dumped by the Shadow Brokers hacking group over a month ago. Since then, it has spread rapidly across the world affecting thousands of systems in over 100 countries.” - Singapore Computer Emergency Response Team
Soon after the attack on Friday, a UK cybersecurity researcher working for MalwareTech was able to stop the spread of this ransomware by registering a domain he found hardcoded in the program. However, he noted that “our sinkholing only stops this sample and there is nothing stopping them removing the domain check and trying again, so it’s incredibly important that any unpatched systems are patched as quickly as possible.”
Then on Saturday, the Computer Security Incident Response Team at the Spanish Government’s National Cryptologic Center (CCN-CERT) announced that they have developed a tool to prevent the WannaCry 2.0 ransomware infection.
The "CCN-CERT NoMoreCry Tool" is available to all organizations that need to use it, CCN-CERT announced. “It creates a mutex (mutual exclusion algorithm) on the computer that prevents the execution of the malicious code WannaCry 2.0.,” the organization explained. This tool works on all versions of Windows and should be run after each restart, they advised, adding that it can be automated by modifying with Windows registry. However, they note that the tool is not intended to clean compromised machines.
Commy gets fired, Trump has a meeting with representatives from Russia and Ukrainian on the same day . Then Russia and Ukrainian are the hardest hit by this.
The ransom is for Bitcoin only very interesting - and how they can see the transparency of where the BTC was brought from.
been reading a lot more on this wannacry and you gotta a one low life person to hold hospital files for ransomware.. i do not see the point in this at all and it sucks that in the 7 days for files to be erased that there won't be a person to find a work around.. upvoted ,resteemed
It is not done in "purpose", the virus spreads itself into any non-updated OS.
I find troubling that healthcare establishments are not updating their legal Windows versions.
OFC, the affected versions of windows are mostly, pirated, with no available updates. So, I am wondering if perhaps (and only "perhaps"): Isn't microsoft behind all this as a "you better BUY your OS, because pirating it may become more expensive for you".
Just wrote about this myself.
Horrible affair, hope everyone is updated and protected!
Nope, most people are not updated and protected. That's exactly the reason why this was just the beginning. Let me be a bit more dramatic:
yup im exhausted from working on fixing this. its much much worse than ppl are being led to believe. the Feds gave Empire core biz a heads up early to start fixing this. worked all weekend about 32 hours over weekend.
Update:
13AM4VW2dhxYgXeQepoHkHSQuy6NgaEb94 = $ 20.432,82
115p7UMMngoj1pMvkpHijcRdfJNXj6LrLn = $ 14.637,58
12t9YDPgwueZ9NyMgw519p7AA8isjr6SMw = $ 20.325,12
This guy made some cash.