Use of Secure Shell Inside the internet network
Secure Shell (SSH) is a widely used network protocol for controlling and modifying servers over the Internet. Unlike telnet (Telecommunication network) services, telnet is not encrypted and uses cryptographic techniques to ensure all incoming and outgoing communications from remote servers occurs encrypted. so we can use SSH to control tablet computer computers and other devices that can connect with SSH, Like the example of controlling the existing VPS in a country like Singapore, then with SSH we can control it directly from a remote or can be called a remote
Secure Shell (SSH) is a cryptographic network protocol for operating network services securely over an unsecured network. The best known example application is for remote login to computer systems by users. source : wikipedia
essentially this service refers to a protocol that provides a function that allows an internet user to access to a terminal in an Internet network environment.usually the common protocol used for remote login purposes is Telnet. But the use of Telnet remote login can actually contain the risk, especially from users who roam the internet that is not responsible.
To minimize this risk, SSH (secure shell) protocol is present to replace Telne in remote login. We can distinguish both services port from telnet and SSH services. telnet has a standard port 23 whereas ssh is usually the standard port used is ports 22 and 443. SSH service was created in 1995 by Tatu Ylönen because of a security attack on a university
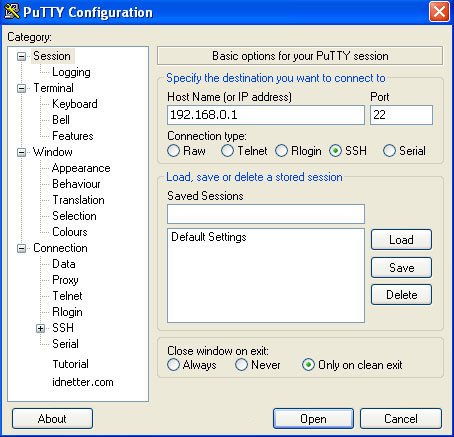
The following processes that occur during the ssh port for ssh server can determine the port manually or can use the standard port
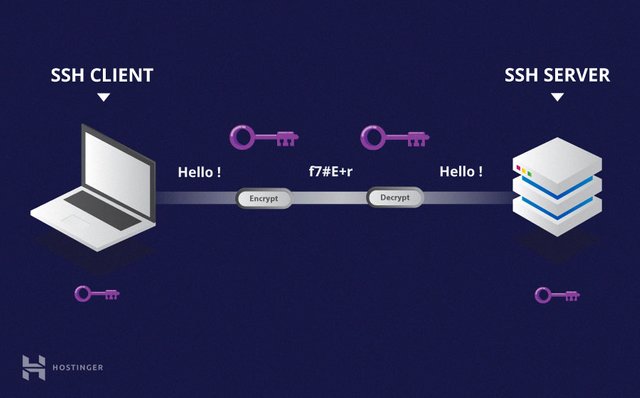
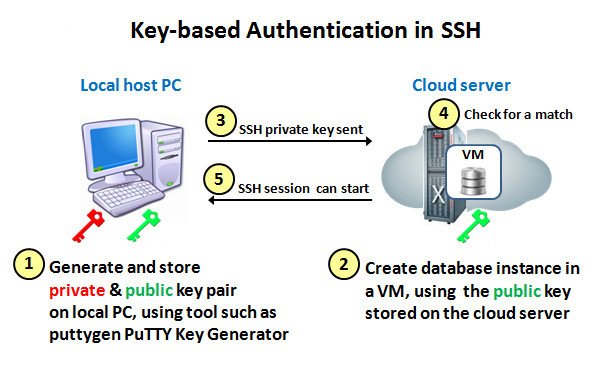
the simplest way SSH works is when the SSH Client accesses the SSH Server or sends data to the SSH Server via a network, whether it is a local network or a public network between the SSH service on the server and client computers. they share the same key pairs for data encryption between devices.now many of the people already know SSH, even people call it a tool for free internet because it is commonly used in conjunction with an injector application.
with the existence of ssh among others now many use ssh to save internet data for browsing at various provider. ssh users take advantage of free internet many who use the network ineternet to mendownlod large files and streaming it is certainly detrimental to the provider.
therefore it is advisable to use SSH properly and wisely as needed.
so as not to happen things we do not want there is nothing wrong if we use the media learning.