(Data Encryption) How to Use Cryfs to Encrypt Dropbox Cloud Storage on Ubuntu 16.04 And Share Across Accounts/Machines
(This is my first Howto blog on Steemit, please comment so I can improve my writing, thanks in advance. If you don't need to know the background, you can jump to part II, step by step how-to starts from there.)
Part I. Introduction

Dropbox is one of the oldest commercial cloud storage service provider who survived the early Cloud bubble(we are now in the Blockchain bubble...).
I personally have used both Dropbox and Google Drive and chose to stick with Dropbox as my main cloud storage since Google Drive doesn't even have an official client for Linux (I still use Google Drive on my phone and Mac), not to mention that the native Gvfs implementation for Google Drive comes with most Linux distributions is slow as hell (no disrespect to the developers, it's Google's issue).
Dropbox in other hand offers a Linux client from almost day one. They are also one of the first who adopts the concept of "Referral Marketing" and gained a tremendous user growth/success with it (they used to give away up to 32 GB referral bonus for life).
One of the concerns about traditional cloud storage is Security and Privacy. This is also the reason blockchain technology is very attractive right now thanks to its decentralized model.
Dropbox however still operates a centralized system, like most of other free online storage providers, there is no client-side encryption (Google and Dropbox both only offer server-side encryption and encrypted data transferring, SpiderOak isn't free).
Compare to Google Drive, Dropbox also has a somewhat troublesome security record. Wikipedia even has a dedicated entry titled "Criticism of Dropbox" about all the issues Dropbox has had in the past.
(To find out more about how Google Drive and Dropbox encrypts users' data, give this virtru blog a read.)
The fact is I wouldn't trust either of them when it comes to protecting my privacy, the reasons for me are more political rather than technical (NSA, Snowden's comments, "1984"...).
So why do I stick with Dropbox? The main reason is its popularity. Too many friends use it, same as lots of my clients. Which is understandable; a lot of business apps have better integration with Dropbox ) since it uses Microsoft Office online as its online collaboration tool (the ambitious online editing tool "Paper" is still in open beta). There are lots of middle and small sized company uses their paid services. According to this report , although in decline, Dropbox still owns almost half of the market share of online storage.
I am in no way adverting for Dropbox here. I believe in the future cloud storage solutions will be based on blockchain technology(Storj.io , Siacoin), but unfortunately, we are not there yet, large legit centralized online storage providers like Google and Dropbox still have many advantages in stability, pricing(still can be free if you don't count in the data mining they did on you) and maturity in both user experiences and business adoption rate.
However, as a "die hard Linux fanboy", it is not necessary to compromise my privacy in order to keep using these centralized services. In my opinion, a simple client-side encryption is sufficient enough for personal privacy protection. As long as the data is encrypted before being sent to the server, and only decrypted after being pulled off the server.
To achieve such goal, there are quite a few options since cryptography and data encryption technologies have been around for a long time. Wikipedia has a long list of encryption software you can check out.
Since my only requirements are:
- Works well with the cloud, and;
- Linux friendly.
My eyes were landed on two candidates, Cryfs and Encfs.
Cryfs is a fairly new open source encryption software released under LGPLv3. Initial release was in 2015, the algorithm of choice is Scrypt (Litecoin, Dogecoin shutout). This gives it several advantages compared to other options.
First of all, it was designed to work with cloud storage, in the developer's own words:
"Since all of the solutions above have significant disadvantages when used with Dropbox, we developed CryFS. Like all other solutions described here, it offers a virtual filesystem and you can work with your files without thinking about the encryption that is happening in the background. While it can also be used for local encryption as an alternative to the other tools listed here, it was built specifically to be used together with Dropbox or other cloud storage providers. "
In addition to better performance with cloud storage, the software also manages to
"not only to keep file contents, but also file sizes, metadata and directory structure confidential."
On the default settings, Cryfs cuts the all the files and metadata into small encrypted blocks with the size of 32 KB and then store them using their in-house developed "left-max-data trees" to construct and index the file system. Such design is, in theory, proven to have minimal space overhead and allow fast file-system operations. The Cryfs implementation shows that such file system is not only fast but also practical.
The main developer Sebastian Messmer did publish his master theory "CryFS: Design and Implementation of a Provably Secure Encrypted Cloud Filesystem" to explain the design in details, give it a read if you want to learn more about Cryfs.
Currently, at beta stage, not all its planned features are implemented, as stated on their website:
"The current version meets all security goals regarding confidentiality of file contents, size, metadata and directory structure. The integrity goals mentioned in the thesis are not fully implemented yet. The current version protects the encrypted blocks from being modified by an attacker, since it uses an authenticated encryption scheme like aes-256-gcm. However, it doesn't prevent an attacker yet from rolling back the filesystem by replacing blocks with an earlier valid version of the same block. This issue will be addressed in future versions."
The other drawback for me is currently only Linux and Mac(through homebrew) are supported. At the time this article been written(July 2017), no Windows implementation is found.
Encfs is a much older piece of software (since 2003), because of that it didn't follow certain rules now we see as standard in its category. It does work well with the cloud and also has much better Windows support (take a look at Safe and this question on Superuser). The project moved to Github in 2014 and still in active development, but I wouldn't recommend it until a version 2 overhaul comes out. To find more about Encfs' security concerns, I recommend reading this audit.
Enough of the introduction, now let me demonstrate how to use Cryfs to encrypt Dropbox contents and share them across different accounts on Ubuntu 16.04.
Part II. Install and use Cryfs with Dropbox
(I assume you already have Dropbox client installed and linked. If not, head to this page and follow the instructions to install it.)
1. Install Cryfs
Installation of Cryfs is very straightforward with the installation script they provided. In a terminal run following command and enter your sudo password when prompt:
$ wget -O - https://www.cryfs.org/install.sh | sudo bash
(This script will put Cryfs' repository into your repository list and install two packages: cryfs and libcrypto++9v5 , if you don't want to add their repo you can also get the .deb file from their download page)
Verify the installation with the command:
$ cryfs -v
you should see output like this:
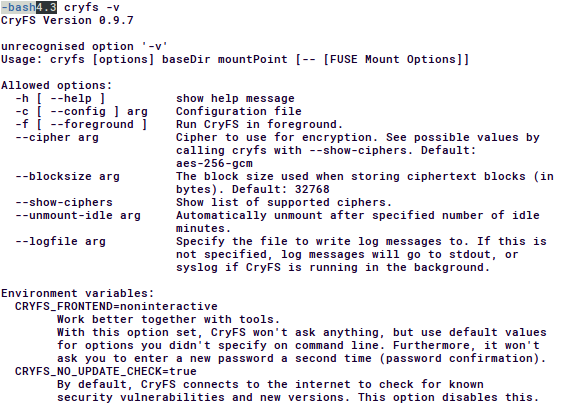
2. (optional) Backup your dropbox folder
Make sure your dropbox folder is fully synced first!
Assume your dropbox folder locates at $HOME/Dropbox (default Dropbox folder):
$ cp -rf $HOME/Dropbox $HOME/Dropbox-backup
Wait till the cp process finish its job if your folder is large.
3. Setup encryption directories
Cryfs need a base directory to store data and configurations, you need to make one in your Dropbox folder(so it syncs with Dropbox's server), I am using the folder named cryfs-basedir in this example.
$ mkdir $HOME/Dropbox/cryfs-basedir
This directory will be used by Cryfs to store encrypted data, so in general, you should not modify it manually.
4. Setup the mount point and password.
Suppose you want to usecryfs-decrypted as the mount point:
$ cryfs $HOME/Dropbox/cryfs-basedir $HOME/cryfs-decrypted #This command is also used to mount
Here's another sceenshot:
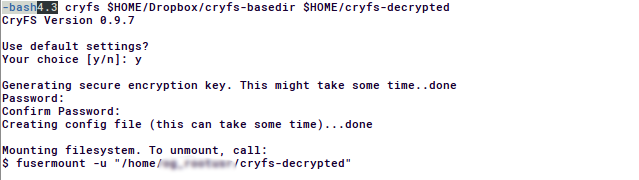
If you answered 'n' on the question "Use default settings?" Cryfs will prompt you with options of different block sizes (default 32kb) and block cipher algorithms(default aes-256-gcm).
Now the encrypted directory is mounted. You can start to move files you want to encrypt into the mounted directory.
5. Encrypt your data
To speed things up a little bit, I made a simple gif to demonstrate the process:

Here is what I did there:
- List current directory.
- copy the file
anonymous.jpginto mounted container directory$HOME/cryfs-decrypted - Make sure the file is copied.
- List the content of the encrypted directory, in this case, it's
$HOME/Dropbox/cryfs-basedir.
Notice that you can see all the block directories and a binary config filecryfs.configthere. - Unmount the encrypted directory, with the
-zoption,fusermountmakes sure all data has been processed before it unmounts. Notice that the mount pointcryfs-decryptedis empty now.
That's it, from now on for every file you put into the encrypted folder, Dropbox has no way to extract any info from it without your assistant. The encrypted directory cryfs-basedir can be mounted on any system runs Cryfs.
You can set up a simple bash script to run the Cryfs command with a terminal (to enter password) and put it in the "Startup Applications" in order to auto-mount at login.
Part III How about GUI?
There are many GUI frontends can handle Cryfs, the most popular one for both Linux and MacOS right now is called Sirikali. Be aware this is just a graphical frontend, it can handle multiple encryption formats but you need to have the actual encryption program (like Cryfs or Encfs) installed in order for it to work.
To install Sirikali on ubuntu 16.04, type in terminal:
$ sudo sh -c "echo 'deb http://download.opensuse.org/repositories/home:/obs_mhogomchungu/xUbuntu_16.04/ /' > /etc/apt/sources.list.d/sirikali.list"
$ sudo apt-get update
$ sudo apt-get install sirikali
Here is their repository page in case you need it for other distros.
Since I don't use it often, I just made a couple of screenshots to demonstrate how to add the encryption folder as a favorite so you can use Sirikali to automount it.
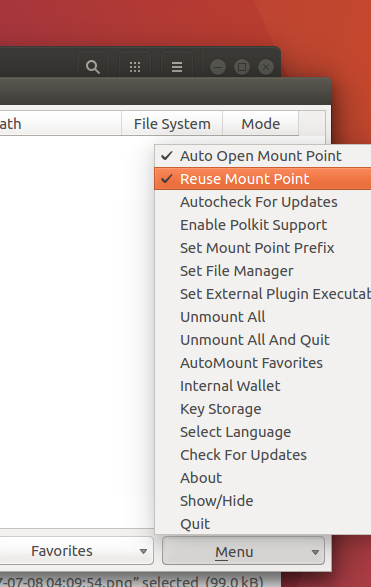
Frist make sure to check "Reuse Mount Point" in the menu, otherwise, Sirikali will complain if the mount point folder has already existed (We made the folder in last Part).
Then we can add the encrypted folder as a favorite and tell Sirikali to automount it. Be careful here when put in the mount point folder, Sirikali likes to create its own mount point ($HOME/cryfs-decrypted/cryfs-basedir instead of $HOME/cryfs-decrypted). So make sure you edit it like I showed here in the next screenshot.
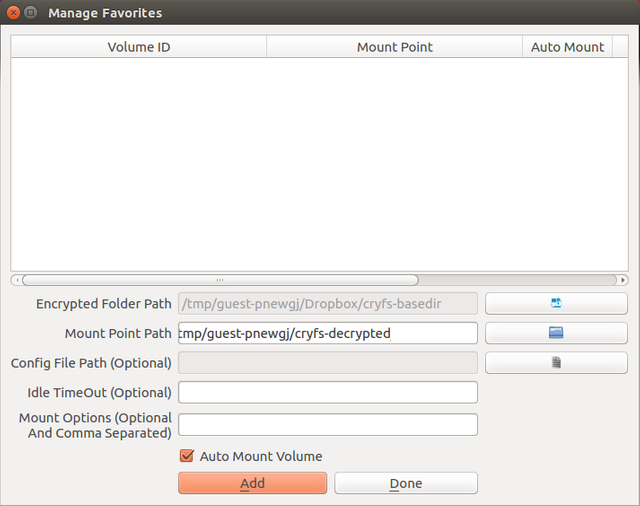
After set favorite you can configure Sirikali to mount/automount with varies options, for more information you can visit the project's Q&A page.
Part IV Conclusion
I hope this blog can help everyone who uses Dropbox and wants better protection of his/her data in the "Cloud". With Linux and Open Sourced Software, there's always a solution. If you have any questions or suggestions, please leave a comment, I will be glad to upvote them! ^^
And
One more thing...
You can also share the encrypted folder with other Dropbox users. Normally when you share a folder in Dropbox, both you and the person you shared with will have the same folder downloaded locally and sync with each other. You can do the same to a Cryfs encrypted folder.
Just make sure other user have the password and Cryfs installed on his/her machine, so he/she can properly mount it locally.
Nice tutorial, very useful!
@androidparanoid
Nice Post!
Thanks for sharing this.
Congratulations @androidparanoid! You have completed some achievement on Steemit and have been rewarded with new badge(s) :
Click on any badge to view your own Board of Honor on SteemitBoard.
For more information about SteemitBoard, click here
If you no longer want to receive notifications, reply to this comment with the word
STOPNice, Thanks.
Nice article, if you want an out of the box solution for Mac, Windows, Android, IOS then take a look at: https://www.sookasa.com/how-it-works/ - I have been using this for a long while now to secure scans of all my paper documents - also supports sharing/access control between people.