BUGLAB: CYBERSECURITY PENETRATION TESTING ON THE ETHEREUM BLOCKCHAIN.
Buglab is an Ethereum-based that interfaces organizations with a worldwide system of master cybersecurity analysts.
At the focal point of our biological system, there are two projects - the buglab challenge and Vigilante Protocol, helping organizations everywhere throughout the world to find and fix vulnerabilities on their advanced arrangements or resources.
Who is Buglab for?
The Cybersecurity Market
Effects on Return on Investment (ROI) are hard to measure, so it sets aside time for organizations to perceive the requirement for cybersecurity administrations.
For very numerous undertakings, and in addition people with any advanced resources on their sites (content included), it frequently brings a rupture into their framework before they make a move to shore up security
In the interim, the casualties of digital assaults once in a while promote that they have been targets, except if they should, and information vulnerabilities are infrequently first need as item gets hurried to showcase, so it is troublesome, if certainly feasible, to get thorough insights about cyberattacks subtle elements, including their recurrence or their effect on ROI. In any case, one angle is sure beyond a shadow of a doubt: the pattern is determinedly on the ascent, with some broadly known geopolitical effects.
THE CYBERSECURITY MARKET
A champion case is that of the 2016 U.S. presidential decision crusade, when a huge email spill cast a shadow over the Democratic party in July 2016. Sen. Hillary Clinton's crusade was hit by an extensive scale cyberattack that not just put the Democratic party's discretionary procedure in danger, yet in addition molded the eventual fate of American governmental issues. Around then Reuters announced that a "PC arrange utilized by Democratic presidential chosen one Hillary Clinton's battle was hacked as a feature of a wide digital assault on Democratic political associations." The article went ahead to state that the assault "takes after two different hacks on the Democratic National Committee, or DNC, and the gathering's raising money board for possibility for the U.S. Place of Representatives."
Blockchain Security
The strategy offered by Buglab sends ability and brilliant contracts over the blockchain.
A blockchain is a string of computerized records crosswise over which distinctive kinds of information are put away. Together, these appropriated (or decentralized) records make up a database like the pages of an extensive record book. These virtual records are facilitated crosswise over numerous servers, which confirms and verify any given exchange. It is an extraordinary numerical process, crosswise over numerous machines facilitated by endless members, or excavators. See additionally Advantages of Using the Blockchain to Reshape Pentesting.
Strategies for Fighting Cybercrime
Conventional choices for battling cybercrime are not attainable for private ventures and associations. The cost of two regular systems illustrated here quickly ends up distant for everything except vast undertakings.
Infiltration tests performed by a cybersecurity counseling firm:
Requires that customers pay for the administration as far as aggregate billable hours, paying little respect to the test outcomes. The lion's share of entrance tests performed by counseling firms are finished by one, perhaps two pentesters. This implies the customer is just ready to exploit the technique and range of abilities of two advisors.
Bug Bounty challenges:
Data security analysts are paid on a for every helplessness revealed premise. Organizations regularly wind up getting charged to settle issues not by any stretch of the imagination considerable to their income or clients. This is portrayed in more detail in the following area.
The Buglab Solution
The Buglab stage joins associations that have data security needs, which is just about every one of them, with a network of affirmed cybersecurity entrance analyzers in a boosted domain, where analyzers are compensated when they reveal framework vulnerabilities, positioned by seriousness and potential effects. It's done as a race against time. Vitally, discovering one of a kind vulnerabilities is positioned above just delivering a rundown of issues.
Center Features of the Buglab Platform
The Buglab stage empowers clients to either utilize the mass of pentesters or pick an approved group from a known organization. Groups must incorporate no less than five pentesters.
Open Contest
Private Contest
Determination Filters
Triage System
Reports
Visit
Fix Companion
Customer Managed
Intercession
- Leaderboard
Characterizing Requirements
The rundown of potential utilize cases is very long. Situations may incorporate revealing malignant SQL infusion, which courses database substance to a programmer. A framework may have verification sidestep vulnerabilities. Touchy organization information might be decoded. Document transfers may not be secured. Client sessions might be liable to takeover by malignant elements. Maybe the helplessness is generally straight-forward: for instance, an organization may have deficient login security. The Buglab procedure addresses these and different vulnerabilities in a savvy way to handle cybercrime and its effect on customers' main concerns
Ongoing Reporting
The customer organization staff take after the challenge as it unfurls continuously to see the announced vulnerabilities and relief suggestions. They'll have the methods for speaking with the pentesters to development. The stage can likewise coordinate with other revealing instruments at your organization's attentiveness.
The Contest
A customer joins on the stage and gives data about itself, including its items and administrations. At that point, utilizing a straightforward and easy to understand interface, it buys in to an opposition contract, picking it's guidelines.
Customers can modify the confidentiality1 of the opposition, the kind of administration they need, and the challenge cost, which relies on the chose design and a discretionary reward. As essential, a Buglab group will connect with clients to enable them to set up program parameters.
Challenge Scoring
Upon the challenge dispatch our locale of pentesters that have enrolled with Buglab is informed. Our worldwide cybersecurity pentesters at that point break down, test, and report back on the vulnerabilities of an answer straightforwardly on the Buglab stage.
At the point when the challenge finishes up, the part of Buglab is constrained to helplessness scoring and triage utilizing the Common Vulnerability Scoring System 3 (CVSS3) standard depicted in Vulnerability Timestamp. Pentesters are repaid as per their rank in the challenge.
Weakness Timestamp
Results of infiltration test challenges rely upon the Vulnerability Timestamp (VTS) that compares to the correct minute a helplessness was accounted for.
It was important to set up a positioning framework with a specific end goal to have the capacity to remunerate the best scientists as per both their general score and timing. A pentester's general score for a challenge is equivalent to the total of the majority of the scores they've gotten for revealing a weakness. The score for a helplessness depends on objective and quantifiable criteria, because of CVSS3.
For such cases, analysts get CVSS3 scores in view of the speed with which they could reveal the weakness. The first to have done as such will get full stamps, and those that take after will see their score lessen as indicated by their rank in time and the quantity of pentesters who have revealed that same powerlessness
Fix Companion
At the Enterprise level, Buglab will confirm that the fix has been actualized. Buglab will endeavor to confirm (misuse) the helplessness once more. At the point when affirmed as settled, a Buglab group of investigators will refresh the status in like manner in the stage. A "fix" can be declined by Buglab to allow the organization to address the powerlessness once more. The organization will be allocated up to five endeavors to address the helplessness issue
Through the whole span of the test organizations can talk with pentesters and access reports, they will have the capacity to actualize suggestions to cure the vulnerabilities progressively. This is particularly helpful if the vulnerabilities and the related fixes are time delicate. Organizations require not hold up until the finish of the challenge to execute a fix.
What are Tokens?
A token on the Ethereum blockchain is a computerized resource that is held inside a token contract, in trust for a wallet address.
The buglab token, distinguished as BGL, depends on the ERC20 standard for blockchain tokens.
BGL tokens are required for all exchanges in the buglab biological system, from requesting a challenge to remunerating pentesters and whitehats.
Administration Levels
At a settled cost, Buglab will sort out entrance tests done by specialists pre-affirmed by our group. Features of the highlights with the three administration levels are given in the accompanying table.
Vigilante Protocol
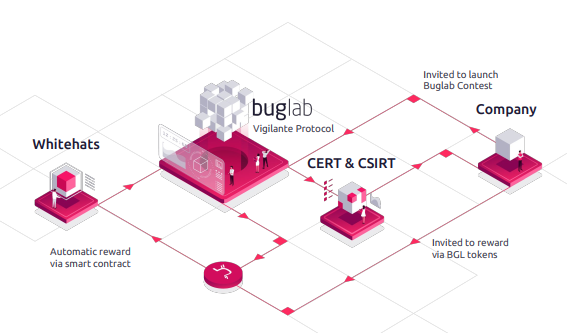
PC Emergency Response Teams
Our Vigilante Protocol Smart Contract empowers correspondence of delicate data in a classified and secure way through the appropriate ensured national specialists, specifically PC security episode reaction groups (CSIRT), which are directed by numerous nations over the globe.
Notwithstanding telling the organization being referred to of a weakness, CSIRT and Computer Emergency Response Teams (CERT) will themselves need to triage and score it. Consequently, once the organization denotes a helplessness as settled, the reaction groups will be remunerated in tokens that leave the Vigilante Protocol Reserve, as associations are produced with Buglab.
Doling out Pentester Status
For a whitehat to reach pentester status and to have the capacity to take part in the different difficulties, they should, when agreeing to accept the Buglab stage, meet two obligatory necessities, i.e. outfit ID in addition to no less than one affirmation. Nation of living arrangement is discretionary. The record is just endorsed once those prerequisites have been approved.
Another approach to accomplish pentester status is by acting under the Vigilante Protocol so as to demonstrate one's capacities and readiness to partake in our protection s.
THE BUGLAB TOKEN
What are BGL Tokens?
A token on the Ethereum blockchain is a digital asset that is held inside a token contract, in trust for a wallet address.
The buglab token, identified as BGL, is based on the ERC20 standard for blockchain tokens.
BGL tokens are required for all transactions in the buglab ecosystem, from ordering a contest to rewarding pentesters and whitehats.
The Buglab Token
The Buglab Token (BGL) is being introduced to incentivize penetration testing in the blockchain environment. In the context of the Buglab experience, token exchange occurs in the following scenarios:
● To reward contest winners— up to the top three in rankings, or as customized by the client.
● To cover the cost of a contest, including transaction costs.
● To enable and tokenize “tipping” functionality for white hats.
● To fund both the VPR and BTR.
● To reward CERTs and CSIRTs for triaging of vulnerabilities and help build new partnerships.
FOR ADDITIONAL INFORMATION :
Website : https://buglab.io/
Whitepaper : https://buglab.io/assets/docs/Buglab_WhitePaper.pdf
Twitter : https://twitter.com/joinbuglab
Facebook : https://www.facebook.com/buglab.co
Telegram : https://t.me/buglab
Reddit : https://www.reddit.com/r/buglabProject/
Bounty Bitcointalk : https://bitcointalk.org/index.php?topic=4446991
Author: mobleland
Bitcoin Profile: https://bitcointalk.org/index.php?action=profile;u=2230408;sa=forumProfile
Etherum Address: 0x08bcD649D8d7266580f89eC5CC898fc77C9E1894