See how I steal Siacoin.

cause
Things should be told in the evening of June 9th. It was a regular Friday night, and I looked at the Netflix TV show and brushed the reddit forum. Suddenly, the Siacoin Forum (/r/siacoin) jumped out of the following post:
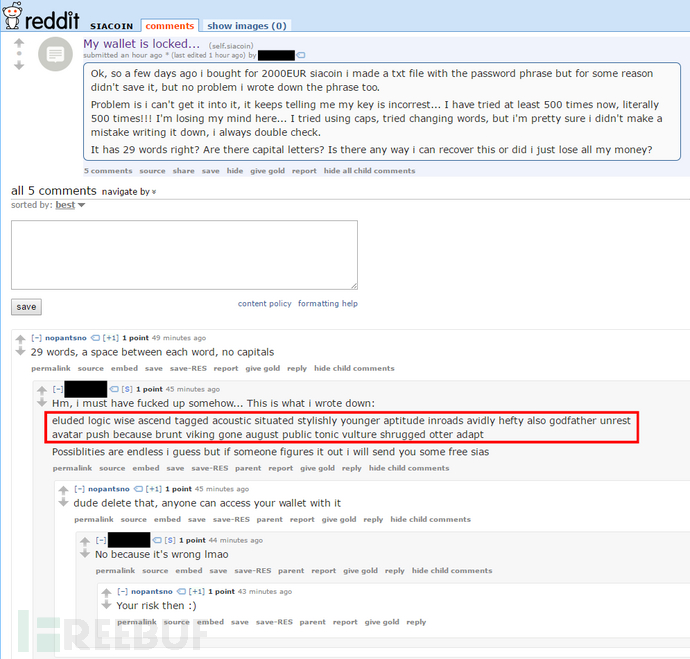
The idea is so.
A few days ago, I bought a coin worth 2000 euro of cloud storage, then I remember to use TXT file key purse, but somehow, then didn't save. Well, I got a copy of the key. But the problem is, the trading platform has always prompted my input key to be wrong! I've tried it no more than 500 times, God, who can help me! If anyone can help me, I can send him some cloud money as compensation...
The affixed then posted the wallet key (red box text) that was copied by his hand.
Introduction of cloud storage
SIA is a decentralized cloud storage platform using block chain technology. Compared to traditional cloud storage, the centralization of the Sia system can make the cloud more secure, faster and cheaper. By coding technology (erasure coding), encryption technology (encryption), and block chain (blockchian), Sia has both traditional cloud storage function and the security and privacy problems of traditional cloud storage.
Siacoin (cloud storage currency / cloud currency): the design of Sia enables the server providing storage space to receive Siacoin (cloud storage currency) - Sia system built in token, so as to encourage more idle space to become a storage provider. Users can use Siacoin to rent or sell storage space.
Draw interest
The user is making a mistake and announces the Sia purse's private key seed on the Internet! The key seed is like a key used to open a storage user to encrypt the money purse, and is an important information of the user's account. As you can see, the user claims that the wallet contains a $2000 value of the cloud, and is generous in putting the key seed out. What I'm interested in is that the user had to copy the seed key and repeatedly stressed that:
I'm very sure that I copied it correctly, and I checked it two times.
But I think he must have made a mistake. I only hope that he made a mistake, if you just leave out a letter or the two letter sequence of anti copy, I think it is possible to infer the correct key and restore the coin storage cloud. That's 2000 Europe, think of oxygen! I don't rule out that other senior people can crack the key and get the money into the bag. I want to act as soon as possible.
Manual crack
First, look at the key of the error that the user has published.
Eluded logic wise ascend tagged acoustic situated stylishly younger aptitude inroads, younger, and it is also known as the following three aspects.
Draw interest
The user is making a mistake and announces the Sia purse's private key seed on the Internet! The key seed is like a key used to open a storage user to encrypt the money purse, and is an important information of the user's account. As you can see, the user claims that the wallet contains a $2000 value of the cloud, and is generous in putting the key seed out. What I'm interested in is that the user had to copy the seed key and repeatedly stressed that:
I'm very sure that I copied it correctly, and I checked it two times.
But I think he must have made a mistake. I only hope that he made a mistake, if you just leave out a letter or the two letter sequence of anti copy, I think it is possible to infer the correct key and restore the coin storage cloud. That's 2000 Europe, think of oxygen! I don't rule out that other senior people can crack the key and get the money into the bag. I want to act as soon as possible.
Manual crack
First, look at the key of the error that the user has published.
Eluded logic wise ascend tagged acoustic situated stylishly younger aptitude inroads, younger, and it is also known as the following three aspects.
Although I'm not familiar with Sia's key seed generation mechanism, Sia is a completely open source project, so I think it should be undifficult to understand.
Right enough facts. In the Sia project wallet.go file, I found a SeedToString function, which referred to the name entropy-mnemonics (entropy mnemonic) file directory, the directory file should contain the seed key dictionary, GOD, as follows:
EnglishDictionary = Dictionary{
"Abbey",
"Abducts",
"Ability",
"Ablaze",
"Abnormal",
"Abort",
"Abrasive",
"Absorb",
"Abyss",
"Academy",
"Aces",
"Aching",
"Acidic",
"Acoustic",
"Acquire",
"Across",
"Actress",
...
You can find the dictionary with 1600 words. I am such a hypothesis: the user of the 29 word segment key should be mostly right, he may copy the seed key, accidentally wrong a word, of course, the wrong word must not be included in the key dictionary, if I can find the wrong word, then, the right key natural it can be solved The case is entirely cleared!
However, to screen the 29 words in more than 1600 words, it is really dazzling, and SO, the violent enumeration can be used.
Violence enumeration
Let's use the code to do automatic testing. Now, I need to find a way to find all the words in the key dictionary, all of which may be the one that has been miswritten in the 29 seed key.
I think the editing distance (Levenshtein distance) may be useful, which can measure the similarity between two words. For example, there are 1 editing distances between "cat" and "car" because there are 1 letter differences. There are 2 letter differences between "cat" and "Scar", and there are 2 editing distances. In order to find possible seed keys between the key dictionary and the private key released by users, I need to write script programs to find words that contain 1 edit distances.
Levenshtein distance, also called the minimum edit distance, refers to the minimum number of editing operations required between the two strings from one to another. A licensed edit operation consists of replacing one character with another character, inserting a character, and deleting a character. In general, the smaller the editing distance, the greater the similarity between the two strings.
First, download the dictionary file, extract all the valid key fields from a to Z, and save them as dictionary.txt files:
$WGet -qO- https://raw.githubusercontent.com/NebulousLabs/entropy-mnemonics/master/english.go \ \
| egrep "^\s+" (1) \ ", "
Egrep -o [a-z]+, |
dictionary.txt
After that, the python-Levenshtein library is installed, and, of course, the Sia project is cloned and installed into the system. Next, write a small script that can automatically export the possibility seed key.
Import Levenshtein
Seed = raw_input ('enter your wallet seed: ')
For seed_word in seed.split ():
For dict_word in open ('dictionary.txt'):
Dict_word = dict_word.strip ()
Distance = Levenshtein.distance (seed_word, dict_word)
If distance! = 1:
Continue
Print '"%s" - > "%s" \n%s\n' (seed_word, dict_word%,
Seed.replace (seed_word, dict_word))
The script copies the paste from the 1600 line dictionary file to my Python target file, and the following code operation can show its function well.
Violence enumeration
Let's use the code to do automatic testing. Now, I need to find a way to find all the words in the key dictionary, all of which may be the one that has been miswritten in the 29 seed key.
I think the editing distance (Levenshtein distance) may be useful, which can measure the similarity between two words. For example, there are 1 editing distances between "cat" and "car" because there are 1 letter differences. There are 2 letter differences between "cat" and "Scar", and there are 2 editing distances. In order to find possible seed keys between the key dictionary and the private key released by users, I need to write script programs to find words that contain 1 edit distances.
Levenshtein distance, also called the minimum edit distance, refers to the minimum number of editing operations required between the two strings from one to another. A licensed edit operation consists of replacing one character with another character, inserting a character, and deleting a character. In general, the smaller the editing distance, the greater the similarity between the two strings.
First, download the dictionary file, extract all the valid key fields from a to Z, and save them as dictionary.txt files:
$WGet -qO- https://raw.githubusercontent.com/NebulousLabs/entropy-mnemonics/master/english.go \ \
| egrep "^\s+" (1) \ ", "
Egrep -o [a-z]+, |
dictionary.txt
After that, the python-Levenshtein library is installed, and, of course, the Sia project is cloned and installed into the system. Next, write a small script that can automatically export the possibility seed key.
Import Levenshtein
Seed = raw_input ('enter your wallet seed: ')
For seed_word in seed.split ():
For dict_word in open ('dictionary.txt'):
Dict_word = dict_word.strip ()
Distance = Levenshtein.distance (seed_word, dict_word)
If distance! = 1:
Continue
Print '"%s" - > "%s" \n%s\n' (seed_word, dict_word%,
Seed.replace (seed_word, dict_word))
The script copies the paste from the 1600 line dictionary file to my Python target file, and the following code operation can show its function well.
There are several possibilities, and manual input validation is all right. Let me first try the first possible seed, in the wrong seeds published by the forum users, replacing wise with wife, as follows:
SIAC wallet init-seed
Seed:
Could not initialize wallet from seed: error when calling /wallet/init/seed: seed failed
It's not that good luck. Let's try every one. Finally, the correct key seed for replacing tonic with ionic was found.
SIAC wallet init-seed
Seed:
Wallet initialized and encrypted with seed.
Be accomplished!
Now, the user's wallet has been controlled by me. Let's turn on the wallet.
SIAC wallet unlock
Wallet password:
Wallet unlocked
SIAC Wallet
Wallet status:
Encrypted, Unlocked
Confirmed Balance: 594.8 SC
594.8 SC (Siacoin)! No, it's only worth about 10 euro, which is far away from the claim of the forum users for 2000. WTF! I'm not cheated, right? Or does the user deliberately exaggerate the amount of the wallet to attract people to help him? Or is there any other cow who had a step earlier than I did, deliberately leaving 10 European accounts ridiculing and taunting me?
Protect the spoils of war
When I think about it, I think my speed is fast enough. How can I have this balance at the end of the day? I'm not sure if anyone else who sees this post has unlocked my wallet in the same way as I do. Oh, no matter so much, to steal these clouds first!
So I moved all the cloud money into my Sia wallet, and even if other people cracked the seed key, I couldn't get the money.
A probe into the earth
Now the cloud is safe, let's see what it's going to do. Check the history of the user's wallet trading.
SIAC wallet transactions
[height] [transaction id] [net siacoins] [net siafunds] 108589 427b72c98e8ea64fba234ca2a00288f7a750003a243e6b3e967f5c6d426c2f9f 594.83 SC 0 SF.
109002 32ad2729fe6b487aedc1b70d0dff0843404ff1cef69223d5f03699dcd1dbe568 0 SC 0 SF
109002 2304da26d61bd2cb7fcac5c7b38a553d788d8dfc386ae4eb47772e36e4a9269d -594.55 SC 0 SF
The last transaction record is my above transfer stealing money operation, and 0.00SC's record is Sia's wallet's two address, after the transaction produces the noise record, may not manage. What I'm interested in is the first record: it shows that it turns to 594.83 SC in the height of the 108589 block. As the block height corresponds to the time unit of cloud storage, I read the transaction record in Sia block explorer, and found that the transfer operation came into being in June 7, 2017, that is, the first two days when the user posted on the forum.
Hardy-boys.jpg
He has only 10 European purses. Why should he claim to be 2000 Europe?
In cotton trading records
In fact, in that period, the largest cloud exchange platform, Poloniex, also appeared to be mistaken for the transfer of cloud storage to the user's wallet. They did not lose the user money, just put the money from the trading account sent to personal wallet when the user, the chaos Carlton, trading mechanism but fortunately, Poloniex kept a few weeks trading backup.
It is possible that when the user transferred 2000 Europe to his personal wallet, a similar Poloniex transaction chaos also occurred, and the 2000 Europe may be in a lag state. Eventually, it will still arrive at the user wallet.
This is an interesting question. So how do I steal the money that I didn't get to my wallet in real time? I decided to write a script to implement it. The final script functions are as follows:
For /l%%x in (1, 0, 100) do (
SIAC wallet send siacoins 2000SC fff0228f02a01cf8e037047a5ea0db5a88d614913af5f21de209ebf2e58431c68cfc9c27d0e4
)
The script executes an infinite loop of 0, from 1 to 100, and keeps trying to send 2000SC from the user's wallet to my own wallet. If the user's wallet received 2000 European accounts, it would transfer 2000SC to my wallet each time and send me all the 2000 European value of the cloud. Because the 2000 euro 125000SC, to avoid other each transfer 2000SC is New problems crop up unexpectedly., because this is a credit transfer amount is relatively low and relatively safe.
Inform the victim
10 euros can't do anything to me, a private plane, a Rolex, a mansion with a swimming pool... .? Finally, I decided to return these 10 European dollars to the victims. "Hey, man, are you posted to help find 2000 European purses? I've been unlocked, but it's only 10 euros in it! " Think it's a little embarrassed.

Then, in the user posting after two hours, I sent a private letter to him, I explained how to restore the key, how to put the coin storage cloud transfer to his account, and that he told me a new address, I turn him back again. But a few hours passed, and there was no response. And he also removed the content and the posting of the seed key. It seems like there's no such thing.
Finally, on a Monday morning, the victim contacted me. He said in the post after he realized that he used to buy the 2000 euro coin cloud storage may be in the trading state (I guess!) And the money bought may not have reached his Sia wallet at all. Because he could continue to operate and control the 2000 European accounts at the moment, he immediately moved the money to another security account. Finally, the money lost, he deleted the post, there is no attention to my private letter to his message.
He is very glad that I can restore the key and Sia to find his wallet, he admitted that he copied the wrong key, and stick to my 10 SC, I think it should be 10 dollars to its origin owner, nor make me a fortune. At the end of my request, he finally gave me the address, and I sent the 10 cloud money to him.
Postscript
Never let your Sia Wallet Key seeds be posted on the Internet. From the above examples, we can see that even a partial key or error key can be used by people to break out the correct key and open your wallet.
This may be not only for Siacoin, but all of the encrypted currencies. Although other currencies are different from Siacoin, you may also use some kind of key combination, so keep your keys well.