How to know if your PC is infected with a bitcoin miner and how to remove it
It is very likely that you have heard of bitcoin as an anonymous virtual currency, totally decentralized and used to make payments in the darknet among other sites. The truth is that in black markets you can buy almost everything, from service accounts and stolen social networks, to places like Silk Road where you can find all kinds of drugs.
This does not mean that bitcoin is something bad per se. The currency is used to make payments, it does not understand if they are for legitimate or illegitimate purposes. The darknet also has a much friendlier face that goes beyond black markets and custom made hacks.
Returning to the issue of bitcoin, it is designed to operate through the chain of blocks or Blockchain, which is responsible for recording the transactions that are made with this currency and verifying, roughly. One way to earn these cryptographic currencies is through a process known as bitcoin mining.
What is bitcoin mining?
Bitcoin mining is a way to keep the chain of blocks consistent, complete and unalterable by checking again and again and collecting new transactions in issuance in groups of transactions already issued, known as "blocks".
These blocks require complex mathematical calculations to be processed, so the so-called bitcoin miners must provide the additional power for this by sacrificing a part of the resources of their computer. As a compensation, every 10 minutes a bitcoin is generated without an owner that is distributed among all the miners that participate in the processing of the block.
To be able to mine coins it is necessary to install a P2P software that will take from your computer the resources you need. When that bitcoin is generated without an owner, you will receive a share equivalent to the power that you supply or set through a transaction rate.
The mining of bitcoins as malware
For some time cybercriminals have been launching malware campaigns specialized in bitcoin mining, using what is known as bitcoin miner. Through this type of programs, the victim's computer is used to extract the cryptographic currency without it knowing it.
It is much cheaper to infect another person's computer than to invest in equipment to mine bitcoins
Why is there a need for cybercriminals to do this? The answer is very simple: a home computer is not enough to mine bitcoins, and specialized computers that can be used only for this purpose cost a lot of money.
Obviously it is much cheaper to use the infection with malware to avoid having to invest in specific equipment. Why scratch your pocket if you can make someone else's computer do it for you? That is why campaigns are initiated that deceive users to use a malicious download link or to spread the virus through social networks, which are the most common methods of infection.
Some of the most common bitcoin miners are BKDR-BTMINE.MNR, BKDR-BTMINE.DDOS, WORM-KOLAB.SMQX, HKTL-BITCOINMINE and WORM-OTORUN.ASH.
For some time cybercriminals have been launching malware campaigns specialized in bitcoin mining, using what is known as bitcoin miner. Through this type of programs, the victim's computer is used to extract the cryptographic currency without it knowing it.
It is much cheaper to infect another person's computer than to invest in equipment to mine bitcoins
Why is there a need for cybercriminals to do this? The answer is very simple: a home computer is not enough to mine bitcoins, and specialized computers that can be used only for this purpose cost a lot of money.
Obviously it is much cheaper to use the infection with malware to avoid having to invest in specific equipment. Why scratch your pocket if you can make someone else's computer do it for you? That is why campaigns are initiated that deceive users to use a malicious download link or to spread the virus through social networks, which are the most common methods of infection.
Some of the most common bitcoin miners are BKDR-BTMINE.MNR, BKDR-BTMINE.DDOS, WORM-KOLAB.SMQX, HKTL-BITCOINMINE and WORM-OTORUN.ASH.
How to know if you are infected with a bitcoin miner
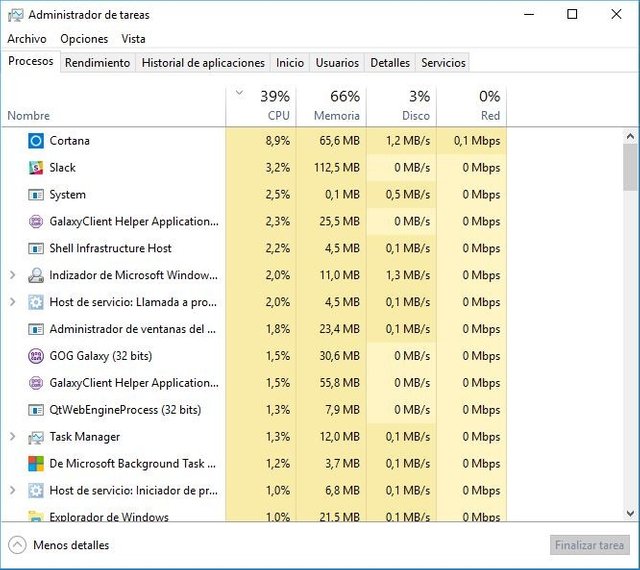
Does your computer run slower than usual? Are the RAM and processor resources unusually high? If the answer to both questions is "yes", then you are very likely to be infected.
As we have already mentioned, in the bitcoins mineo "part of the resources of your computer is eaten" in exchange for a part of the coin without an owner that is created every 10 minutes. To have a greater certainty that, indeed, our computer hosts a bitcoin miner we have several options. First of all, a "manual option", which involves going to the Task Manager and checking how the system resources are developed.
If we do not see anything unusual then there is no need to worry. If any of the processes that appear in the list have a name that we do not know, use a lot of memory or use a lot of processor resources, then we can start worrying.
If any of the names shown by the Task Manager is not only unfamiliar to us, but also consumes a large amount of resources, the simplest is to go to Google to perform a search. If the search reveals that it is a bitcoin miner, we will have to eliminate it immediately.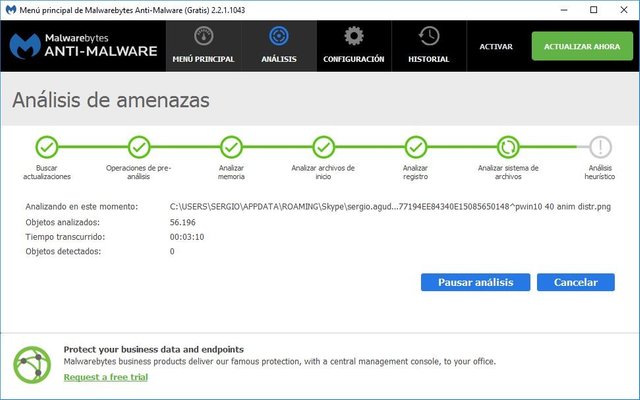
As the first "automatic option" available to us, we found the Malwarebytes Anti-Malware program, which in the case of free protection should identify them and allow them to be eliminated without any problem-we will talk about this later. In its paid version, its action on bitcoin miners should be even more immediate.
As a second option in which we can use a program we find RogueKiller Antimalware, together with Malwarebytes one of the best in its class. With it it should not be difficult to find the virus that mine bitcoins on our PC and take care of it once and for all.
As the third and final program that we will recommend, we have Dr. Web Cureit !, a powerful standalone antivirus that scans and removes malware. Being a program that is not necessary to install is ideal for use in emergency situations.
How to remove a bitcoin miner from your PC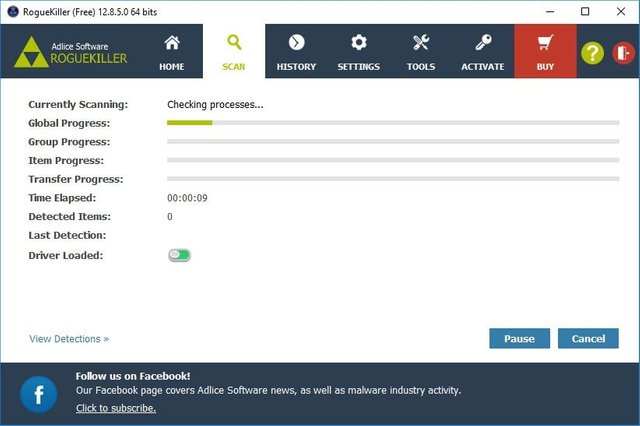
It is likely that by reading all the above you have been able to think that standalone tools already exist that offer a cleaning system that wipes out anything. We'll get to that. First, we are interested in identifying and locating the threat.
In the first place we will have to download at least one of the three antimalware that we just mentioned plus a standalone tool, preferably ComboFix or ADWCleaner. If you use Windows 10 it is worth remembering that ComboFix is not compatible, so you can only use the second program.
The next thing is to disconnect the PC from the Internet completely and execute one of the two programs. If we use Malwarebytes Antimalware we will have to carry out, in this order, a fast scanner and a complete scanner before cleaning.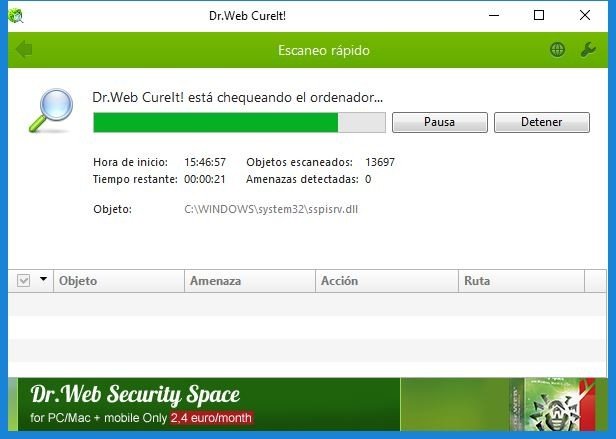
If, on the contrary, we have decided on RogueKiller, the program already carries out an exhaustive analysis by itself. We will just have to wait for it to finish before deleting the infected files. It is worth mentioning that RogueKiller will also analyze entries in the Windows registry that are infected, which will offer us the possibility of eliminating them.
If the program for which we have decided is Dr. Web Cureit !, just press the Scan button so that the program starts looking for threats on the PC. If you find them you will give us the option to clean.
Now what we should do is make sure that the PC is clean. Now we can use ComboFix or ADWCleaner, which will search where antispyros could not reach and, if they detect something, they will give us the option to eliminate it. When the cleaning finishes we will have to restart the system so that the changes are applied.
