FenixHash Review
Opening Words:
In addition to being a dependable piece of software, Fenix Hash Checker has the power of comparing two files and detecting whether or not they are identical in any manner. In order to compare two distinct versions of the same file, you need to follow this procedure. A document's integrity may also be tested to discover whether or not it has been tampered with or otherwise changed. This approach allows the computer to determine if two files are identical to one another or whether they are dissimilar to one another in less than a second using just one piece of software.

How does it work:
When it comes to filing verification, Fenix Hash Checker offers two options: comparing two files side by side or comparing two hashes side by side. The program enables you to choose the input for the base parameter and the comparison parameter, which may be either a file or a hash entered into the software. You have the option of selecting two files, entering two hashes, or selecting a file and a checksum. The program can rapidly generate the hash of a file based on the MD5 method and compare it to the second value if you load a file into it. It doesn't matter what kind of input you offer, as long as the procedure produces a response immediately.
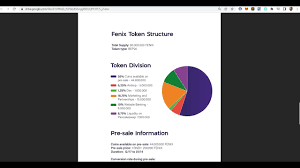
More Features:
Using the hash function, you can tell whether or not a file has been tampered with or altered, as well as whether or not it has been tampered with or changed. An exceedingly simple, yet highly effective, security solution that is also quite simple to implement. Depending on how little an adjustment is made to the file's structure, it is possible that a hash calculator will yield a totally different alphanumeric sequence than it would typically generate. If you want to determine whether or not there are duplicates between two files with different names, you should look at the content of each file in question.
When a file is accurately identified, the hash of the files is instantly generated in the chosen box, allowing you to copy the hash to the clipboard without having to restart the program. You may save time by selecting 'Hash' as the input value instead of manually entering it into the field. Instead of manually entering the value into the box, you may copy and paste it from a document or web page into the box.
When a file is accurately identified, the hash of the files is instantly generated in the chosen box, allowing you to copy the hash to the clipboard without having to restart the program. You may save time by selecting 'Hash' as the input value instead of manually entering it into the field. Instead of manually entering the value into the box, you may copy and paste it from a document or web page into the box.
Final Words:
Bringing FenixHash into reality required the tireless work of a large number of intelligent professionals with extensive expertise in their respective fields, all of whom contributed to its success. Over an extended period of time, the devotion and hard work of a large number of intellectual individuals culminated in the creation of this platform, which is now in its present shape. It has undergone extensive testing, examination, and improvement in order to guarantee that it satisfies the needs of future users who have shown an interest in adopting it in the first place.
To determine whether or not an organization is making an attempt to resolve an issue, a successful company must first determine whether or not the organization is considering possible business partners. A good example of this kind of organization is FenixHash, which fits the bill well. Its user interface and functionality are concise and easy to grasp, ensuring that users have a positive experience while using the application. So we would really appreciate it if you would try out FenixHash and share the word about it inside your social network, as well as publicly on public forums where you participate, in order to assist others while also helping to the cause of FenixHash. Thank you for taking the time to read this and for your consideration.

More About The Project:
Website: https://fenixhash.com/
Tеlеgrаm Offісіаl Grоuр: https://t.me/fenixhash
White Paper Pages: https://drive.google.com/file/d/1P8tteb_PzlYalyKS6oggW1UQPY3YCS_j/view?usp=sharing
Twitter: https://twitter.com/fenixhash

Journalist:
BCT User Profile Name: blackmagic111
Telegram User Profile Name: @blackmagic112
BCT User Profile: https://bitcointalk.org/index.php?action=profile;u=2250283;sa=summary
PROOF OF REGISTRATION LINK: https://bitcointalk.org/index.php?topic=5381545.msg59121346#msg59121346
BSC - BEP20 Wallet address:0xF46a9e110A4E4912CE19B6B46291B18607C95615
An exceedingly simple, yet highly effective, security solution that is also quite simple to implement.