Introduction of MITRE and ATT&CK
Recently, I came across ATT&CK because of my research on security attack and defense technologies, and I don't know much about it, so I want to understand the origin of the concept first.
Ha ha, without further ado, let's go!!!
MITRE:
MITRE is a U.S. government-funded research organization that was spun off from MIT in 1958 and has been involved in many commercial and top-secret projects. These include the development of the FAA Air Traffic Control System and the AWACS Airborne Radar System. MITRE has engaged in numerous cybersecurity practices with funding from the National Institute of Standards and Technology (NIST).
MITRE ATT&CK:
MITRE’s Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK) is a curated knowledge base and model for cyber adversary behavior, reflecting the various phases of an adversary’s attack lifecycle and the platforms they are known to target.
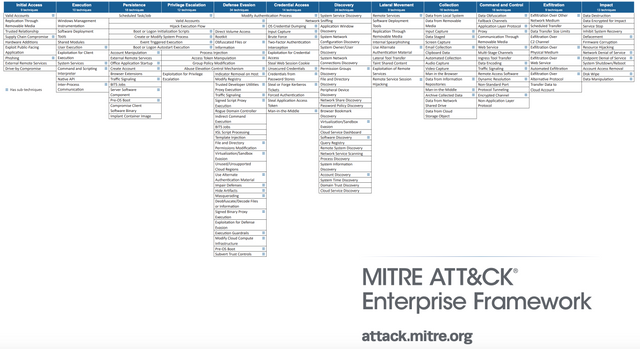
ATT&CK is most visually represented as a matrix, and in simple terms, ATT&CK is the "Counter Tactics, Techniques, and Common Sense" framework provided by MITRE. As follows:
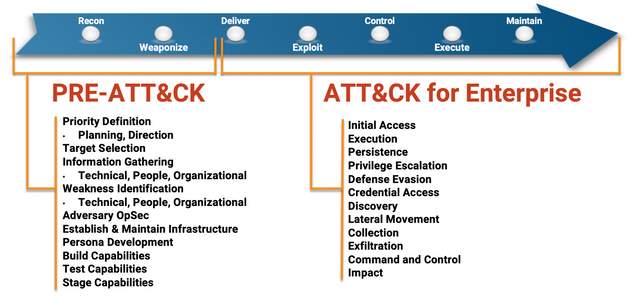
The 11 tactic categories within ATT&CK for Enterprise were derived from the later stages (exploit, control, maintain, and execute) of a seven-stage Cyber Attack Lifecycle[1] (first articulated by Lockheed Martin as the Cyber Kill Chain®[2]). This provides a deeper level of granularity in describing what can occur during an intrusion.
Tactics, techniques and procedures (TTP) are documented in tabular form as the MITRE ATT&CK Enterprise Matrix.
"Tactics" is the name of the column heading and is the general category in which an attacker uses a particular technique.
The "Technique" appears in each box under the "Tactics" column heading and shows how the attacker accomplished a tactic. the ATT&CK matrix assigns a number to each technique, such as T1063 or T1519.
The "Processes" can be accessed through the links in the Techniques box. They show how an attacker performs a technique. Processes provide a more detailed description of how an attacker (or even an attack group) can implement a particular technique in the wild.
MITRE ATT&CK is great because all of the tactics, techniques, and procedures (TTPs) are based on what has been observed by actual attack groups in the real world. Many of these organizations use the same techniques. It's almost as if the hacker groups have their own script when attacking systems and they use that script to quickly gain productivity from new members. When you target an attacker's TTP, you are targeting their behavior.
Ha ha, To be continued。。。