Zipato Smart Home Hub Exploits Discovered That Could Allow An Attacker to Open iOT Door Locks
Smart home solutions may seem to provide convenient security compared to conventional home security (door locks). Nonetheless, these IoT solutions can be vulnerable to cyber attacks. Recently, researchers have demonstrated vulnerabilities within the Zipato smart home hub.
Zipato Smart Home Hub Flaws
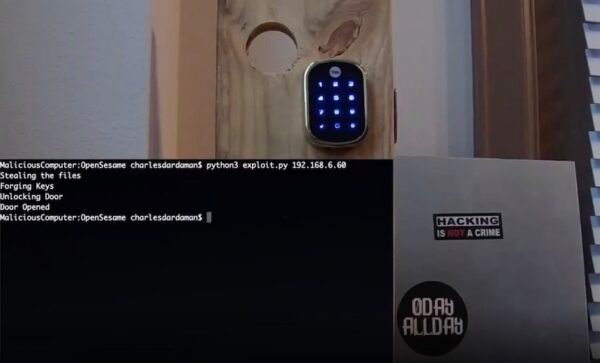
Researchers from Black Marble have found ways to break into the Zipato Smart Home Hub. They have discovered numerous vulnerabilities, exploiting which could allow an attacker open door locks. They have shared the details of their findings in a blog post.
The researchers Charles Dardaman and INIT_6 (Twitter alias) found three different vulnerabilities in the Zipato system. Two of these existed in the Zipato API. Whereas the third one is the non-unique, easily extractable SSH private key for ROOT.
Specifically, the researcher INIT_6 demonstrated the extraction of the Embedded SSH Private key for ROOT (CVE-2019-9560). Extracting this private key was possible simply by removing the SD Card and imaging it. As stated in the blog post,
SSH key was found in '/etc/dropbear/' with the name 'dropbear_rsa_host_key' which is password protected when using this format but you can still extract the Private and Public key.The second one was a Local API Authentication flaw (CVE-2019-9561). The researchers, using the ‘pass-the-hash’ method, could easily place an authentication request without the need to crack password hash.
The third vulnerability (CVE-2019-9562) represents the Local API Authentication exploit via remote attack. As stated in the blog,
The remote API has the same Pass-the-Hash vulnerability as the local API. Depending on the Zipato implementation it could be possible to control all the ZipatoMicro devices.The researchers have shared the proof-of-concept scripts in their blog post. They also demonstrate the attack scenario in the following video.
https://blackmarble.sh/content/images/2019/06/smarthub.mp4
Patches On The Way
Black Marble researchers discovered the flaws in the 0DayAllDay Research Event on February 23, 2019. They found the vulnerabilities in the hubs ZipaMicro Z-Wave Controller Model #: ZM.ZWUS and the Zipabox Z-Wave Controller Model #: 2AAU7-ZBZWUS. They then informed the vendors of the flaws on March 4, 2019. Following their report, Zipato confirmed they fixed the flaws on March 20, 2019.
Regarding the patches, the vendors stated in their email to the researchers, that they disabled user passwords, and rolled out new firmware with changes such as disabled local API, disabled serial console, locally created SSH host key, different root user key, and no root password. They also ‘firewalled Zipato web and API’.
Users must ensure updates for their devices to the Zipato Firmware Version 1.3.60 to say protected from potential exploits. In addition, do not neglect to apply the common security practices to protect against smart home hacks and intrusions.
Let us know your thoughts in the comments.
Posted from my blog with SteemPress : https://latesthackingnews.com/2019/07/05/hackers-can-exploit-zipato-smart-home-hub-flaws-to-break-in/