[SECURITY HOW-TO] Set up Duo Unix to protect your Steem node with Out-of-Band 2FA

My last post explained how to use Duo in order to protect your LastPass account. Now I will provide a quick run down on how to protect your Unix-variant servers with Duo out-of-band authentication. Leveraging Duo Push with autopush enabled, you can set up your 2FA experience to be less disruptive to your workflow, because it doesn't require the use of one-time passcodes.
When you are running a production critical system, maintaining a high degree of security and uptime is a necessity.
Anyone operating a steemd for the purposes of running a witness, seed node, miner, API server, etc. should ensure this additional factor of authentication is enabled if they haven't already. This provides an additional layer of security against attackers looking to exfiltrate your private keys or disrupt your service.
DISCLAIMER: Please be careful not to lock yourself out of your server. In fact, I would HIGHLY suggest that you make a backup image of your server before trying this. A lot of VPS providers have functionality built into their admin panels to do this.
Step #1: Create a Duo Unix Application
Login to your Duo account, or sign-up for a free account if you haven't already.
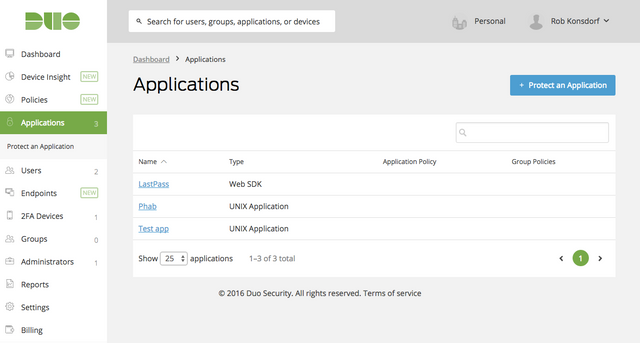
Go to the Applications page and click Protect an application.
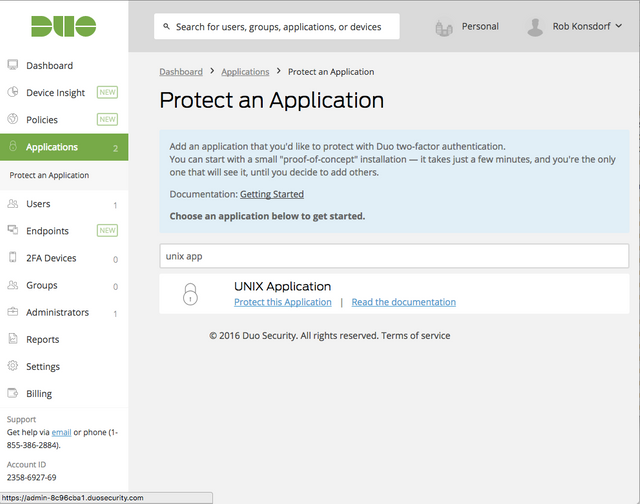
Search for Unix application and protect it.
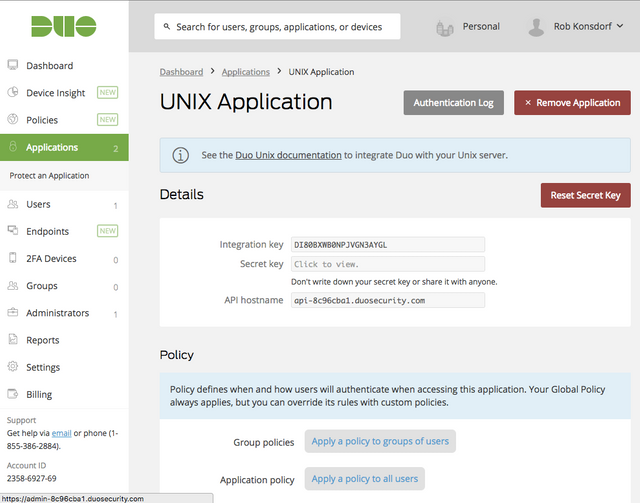
You'll see the integration keys and other information that will be needed later.
Step #2: Install Duo Unix Software
Login to your server via ssh.
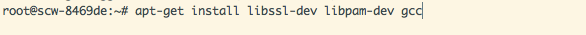
Install Duo Unix dependencies. The commands pictured above are for Ubuntu; if you want to see what packages are required for other distros, look here.
You can install Duo Unix via a package manager on Ubuntu, RHEL, CentOS, or Debian by following the instructions for your target distro here. Otherwise if you'd like to build from source, pull the source from Duo:
wget https://dl.duosecurity.com/duo_unix-latest.tar.gz
tar zxf duo_unix-latest.tar.gz
cd duo_unix-1.9.18
Step #3: Build Duo Unix Software (optional)
Complete this step if you pulled the source code in the previous step, and didn't use a package manager to install Duo Unix.
Run the following command in the duo_unix directory, to make Duo Unix:
./configure --with-pam --prefix=/usr && make && sudo make install
Step #4: Configure Duo Unix Software
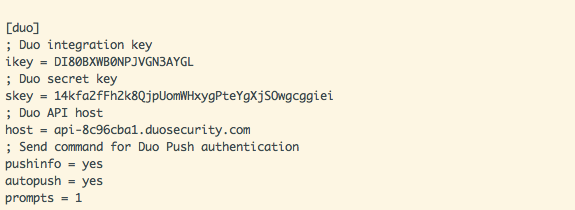
Edit the configuration file located at /etc/duo/pam_duo.conf and add the keys from the application you created in the Duo Admin Panel. Also uncomment pushinfo, and set autopush = yes and prompts = 1. Note: the keys above are invalid. Never expose your actual secret key to anyone.
You can reference all of the config options here.
Step #5: Set up Duo to work with ssh public key authentication (optional)
If you're using ssh to authenticate to your servers, you'll want to take the following steps. Please note, it is always a best practice when configuring ssh to have a separate ssh connection to the server open until you verify this is working, so you don't accidentally get locked out.
Make sure the following options are configured in your /etc/ssh/sshd_config file. If you're using password authentication currently, you'll need to add a public key generated on your local computer to your user's authorized_keys file at ~/.ssh/authorized_keys BEFORE turning off PasswordAuthentication.
PubkeyAuthentication yes
PasswordAuthentication no
AuthenticationMethods publickey,keyboard-interactive
UsePAM yes
ChallengeResponseAuthentication yes
UseDNS no
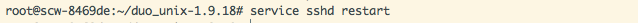
After the sshd configurations are added, restart sshd.
Step #6: Configure PAM with Duo
If you're using ssh, edit the PAM configuration located at /etc/pam.d/sshd to use duo_pam.so, as seen above. Distros other than Ubuntu 16.04 should refer to this documentation to determine the location of the pam configurations and .so files. If the pam_duo.so file is not located in /lib/security, you'll also need to specify the full path to the file in the PAM configuration file. If you're using passwords, you'll want to edit /etc/pam.d/common-auth instead to configure system-wide authentication. See the commands below for that. Notice that the default configuration (top line) is commented out.
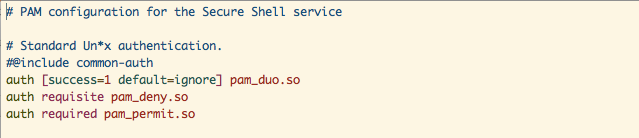
# auth [success=1 default=ignore] pam_unix.so nullok_secure
auth requisite pam_unix.so nullok_secure
auth [success=1 default=ignore] pam_duo.so
auth requisite pam_deny.so
auth required pam_permit.so
Step #7: Enroll a 2FA Device
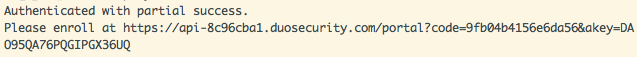
Now, it's time to try it out. Open a separate terminal instance and try to log into your server the way you typically do. You should be prompted to enroll a device in Duo.
Follow the link, and enroll your Android or iOS device into Duo. You'll need to install the Duo Mobile app from your respective platform's official app store if you do not already have it. Otherwise, if you don't have a smartphone, make sure autopush isn't configured, so that you can use the VoIP or passcode flow instead.
Now try it again, this time you should have no problem accessing the service after accepting the Duo Push notification sent to your phone. Make sure you confirm this is working before you drop your remote shell, so you aren't locked out of your server!

Thank you for reading, I hope it was useful! Please leave feedback and don't hesitate to ask me any questions you have in the comment section if you run into a problem.
Until next time,

#security #steemit #mining #witnesses #how-to #duo #unix #2FA #linux #ubuntu #debian #centos #sysadmin
Very technical works here, but understandable, especially with the help of your graphics. Thank you for your work and dedication to the Steem community, namaste :)
You're welcome, Eric. The way I see it, we've all got something useful to contribute!
We do, all for one and one for all! Namaste :)
A good post!
Here are some of mine I consider not bad also...
Beyond the STEEM Whitepaper –2. Where the money come from; New Users DO NOT Increase the Value of Steem (yet)
Beyond the STEEM Whitepaper – 1. Blogging and Curation Rewards Fund; Steem Backed Dollars Creation
Beyond Trading – The Medium Term Fundamentals. 1. – 7.29.2016
Or
Steem – The Solution to Curation Rewards
Thanks, they look interesting!
IT's so weird. more security make me feel nervous. less: same.
I'm in constant anxiety that I overlooked something or that I locked it too well.
It's so bizzare.
I know there are no unbreakable vaults and if they were and i had the key to it i'd lose it.
Am I the only one?
[nice post, rob, as always!]
It is definitely important to err on the side of caution. Actually I'm going to add a little disclaimer here telling people they should save an image of their server before trying this. Thanks for making me think about that!
Great post ! i hope there will be more security tutorials, as this is really valuable content !
Thanks for the compliment. I'm just getting started!
👍nice tutorial..., very interested
Glad you like it!
Thank you robrigo,
I just secured my account with you help. Hope more people will do so. No one leaves the house door open right? So take care of your steemit account as well.
Upvoted this post in the hope more people see it
You're very welcome @timsaid!
As I'm creative person, your design is very set and readable, in my opinion
Thanks Yulia. Props to the #Duo creative team for their hard work!
great post!
nice @robrigo
Nice job on these last two @robrigo ! I can get you guys those free seeds from my giveaway if you or your roommate can get me a shipping address. Thanks for the support and keep up the good work!
You rock Papa!
I'll private message it to you if you make an account on https://steemit.chat!
DONE. I'm papa-pepper on steemit chat now. Let me know and I'll ship your prize-pack from my seed giveaway. I'll throw in the KIWANO seeds too for you guys.
Here's your Prize Pack from the seed giveaway - I threw in some Fatali Pepper seeds, just 'cause I'm @papa-pepper. I'll mail them out shortly. Congratulations, and thanks for the support! Happy growing.
I just wanted to mention how good and I thought that this post once. I think that there's a lot of room for a lot more tutorials on steemit and that this is a great example of a tutorial monetized using steemit system.
Thank you @faddat. I completely agree!