Blockchain Wallet (Types, Uses, Installation) - Steemit Crypto Academy Season 4 - Homework Post for Task 9.

(1) How do you store/secure your keys? What are the different forms of Private Key(Examples/Screenshot)? Download & Install TronLink Wallet(Android/iOS/Extension)? How do you store the key(Hint- write it down on a notepad, demonstrate it with examples)? Which form of the key are you comfortable with to handle your TronLink Wallet? Include Screenshots & hide/blur the sensitive information.
How do you store/secure your keys?
In blockchain as with most decentralized applications, it is inherently anonymous. That is, the details of the users such as name, home address, signature, etc are not needed. That is because the decentralized applications make use of Private & Public Keys. The public key is usually an address in the form of a string that contains alphanumeric characters. The private key can be your password, mnemonic seed, or a string that contains alphanumeric characters. The public keys can be given to anyone as it is through it that another user on the dapp can interact with you, while the private keys are keys that should be kept solely in the possession of the user/owner.
Now, blockchain is a relatively new type of technology, and not many users using the technology are enlightened enough to handle their keys or wallet addresses. As such some of them have fallen prey to the wonders of scammers and hackers. So it is pertinent that users learn how to secure their keys and wallet addresses. Also, users can lose their cryptocurrency because they lose access to their keys, or their private keys get stolen. To prevent a user from losing his funds due to mishandling of the keys given to him, a user needs to have a good understanding of how to store the keys given to them.

One of the best ways a user can use to store the keys given to them is by storing them in hardware such as a flash drive or an external drive. This is a very good means because the hardware is not connected to the internet, so it is not susceptible to hacking. Also, it is not part of the components that make up a computer system, so the data in the hardware is not vulnerable to viruses which can affect a computer system negatively.
Another way to store the keys given to a user is for them to write it down on paper and go ahead to laminate it. Through this method, the keys would always remain in the possession and control of the user. The user can always refer to the paper in case of any eventualities. In addition to writing the keys down on paper and laminating it, a user can go all the way to the bank and store them in a safe deposit box, this way the user can guarantee that the keys are secured in a safe environment.
A good way that a user can secure their keys is by storing them in cloud service platforms like Google Drive, Dropbox, iCloud, OneDrive, etc. These are digital storage platforms where data can be stored on them and then stored in the cloud. Through this means a user can help store and secure their keys and thus their digital assets.
Some other ways to store the keys given to a user are through storage on a compact disk (CD) or in a piece of Drawing. A compact disk has the characteristic to store different types of data in it and the private key of the user is one of them. This is achieved by saving the keys as a file that the compact disk can accept. For the picture, a user can make a drawing where the keys of the user are inscribed to it. One company that is providing such service is CrypoArt.
What are the different forms of Private Key(Examples/Screenshot)?

When a user registers on a decentralized application, a public and a private key are generated and given to them. The private key comes in different forms. They are a String that contains alphanumeric characters, Mnenomic seed, and the Keystore file. I shall be looking into each of them.
String (with alphanumeric characters)
The String form of private keys is made up of alphanumeric characters. The alphanumeric characters are made from a Hexadecimal numbering system or Base of 16 system to represent long binary values of characters because their format is quite compact and much comfortable to operate with long binary strings of 1's and 0's. This numbering system uses 16 different digits with a combination of numbers and alphabet from 0-9 and A-F. They are created at random using cryptography when a new user creates an account or a wallet in a decentralized application.
An example of a string is given below. Another example that we can consider is our keys on Steemit. These keys are given to us to enable us to operate on the Steemit platform in different ways, and they come in different types such as Active key, Master key, etc.

Mnemonic Seed
A mnemonic seed or phrase is the group of Secret Words that are brought together and presented to a user during registration which allows the user to access the platform, which is usually an online wallet. It is equally called the "Recovery phrase or Backup phrase". When users make use of them they are arranged in a sequence of which when arranged successfully, the user can gain access to his wallet. The group of words can be 12 or more, but usually 16. A primary reason why it is called the recovery or backup phrase is that it helps users to gain access to their wallets when the computer holding the wallets gets stolen or crashes.
An example is given in the illustration below. Wallet services such as TrustWallet, MetaMask, TronLink, etc, make use of Mnemonic as a form of private keys given to users.

The Keystore File
A Keystore file is a private key that is Encrypted. They are generated with the use of a user's private key and a password given by the user to encrypt it. When the Keystore file is open in a text editor the data contained therein pertains to the encryption that is done for the private key. It is sometimes called a UTC file. The file extension for a Keystore file is .json. The Keystore file system essentially lets users store their private keys in a "container" so that it would be difficult to be extracted from the device that has the container. A Keystore file is a file that needs to be uploaded online and type in your password to unlock the file.
An example of a Keystore file is shown in the illustration below.
Download & Install TronLink Wallet(Android/iOS/Extension)?
To initiate the process of downloading and installing the Tronlink Wallet you need to visit the Tronlink. These are the processes involved.
First, visit the Tronlink website, then on the home page click on Browser Extension (for those using a computer system), then click on Chrome Web Store. If it is a mobile device, click on Android, iOS, or Huawei HarmonyOS to start the process. You can also click on Scan to download by using a scanner on a mobile device to download the application.
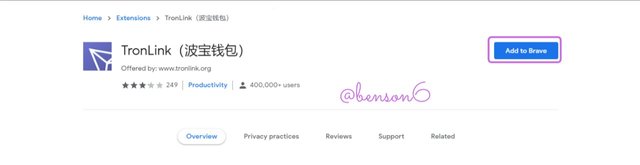
After clicking browser extension, it would take you to a page where you would install the application on your browser. Click on Add to Brave (Browser).
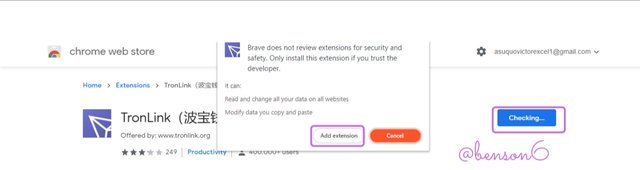
Afterward, a prompt would display to seek your consent to install the app. Click on Add Extension. At this time it would be checking.
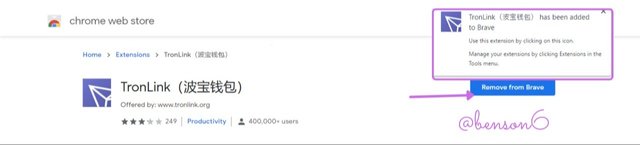
When you have done so, a few moments later, it shows a prompt that the application (Tronlink) has been added to your browser. In case you have any issues at the time of installation, you can click Remove from Brave.
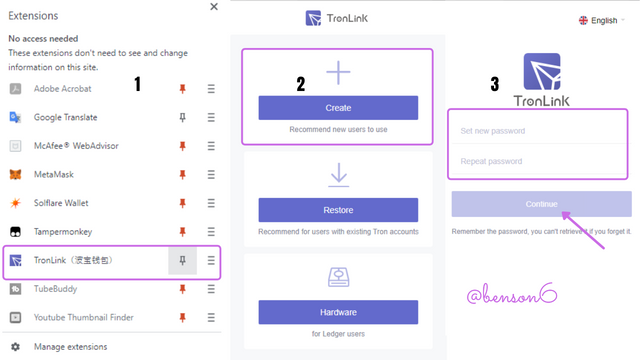
Then after that, a sequence of steps would follow. In this image, I listed them from no. 1-3. In no. 1, I pinned the application on my browser and clicked on the application. Then no. 2, I created a new account by clicking on Create. Then no. 3 I input my password and click on Continue.
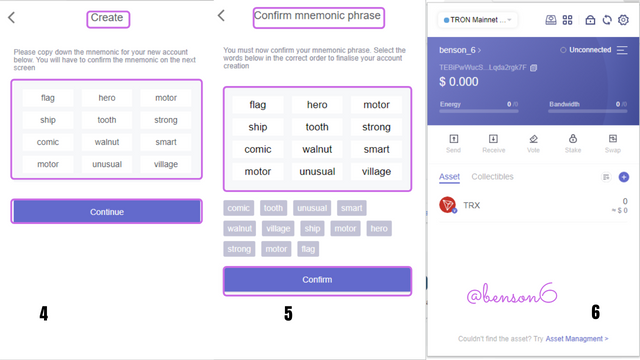
The next sequence of steps is listed no. 4-6. In no. 4 a Mnemonic seed would appear after clicking on continue. It is meant to be written down and stored somewhere, and then used to confirm the mnemonic on the next page. On the next page, that is, no.5 you input the mnemonic in the correct order that it is presented. After that click on Confirm. Once you do that successfully, you would have successfully created a Tronlink wallet. It is shown as no. 6. The name of the wallet is benson_6 and the wallet address is directly under the name.

How do you store the key(Hint- write it down on a notepad, demonstrate it with examples)?
In this exercise, I shall do an illustration using some of the storage techniques mentioned previously. While installing the Tronlink address, I was given a mnemonic seed to use and create my Tronlink wallet. Here's how I'm going to store it:

This is an image of the screenshot of the original mnemonic seed given to me. So I cropped it out and store it on my devices such as inside my computer system, email address, and cloud storage software. I don't have external hardware like a hard drive or a flash drive. When I do, I would eventually store them there.
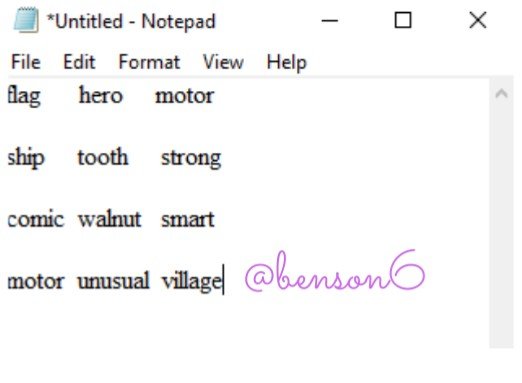
This is another image of the mnemonic seed, but in this case, it is copied on a notepad. I copied and paste the seed phrase from the original place into my notepad. I also followed the same pattern as above by storing them on my devices and online software.

Finally, in the image above, I wrote down the seed phrase on a fresh page in my notebook. This specific one accompany to wherever I go to. I also took a picture of it and stored it on my different devices.
Which form of the key are you comfortable with to handle your TronLink Wallet? Include Screenshots & hide/blur the sensitive information.
So far we have discussed three forms of private keys. Having looked at them it is obvious that the string (with alphanumeric characters) and the mnemonic seed forms are the most common as well as the easiest to use and store.
For the Tronlink exercise, we are given two keys, the wallet address which is in the form of a string (with alphanumeric characters), and the mnemonic seed which is used to create an account. The wallet address is not that much important as it is always on your Tronlink wallet when you access it. And when you want to send it to someone you can always copy it from the wallet and give it to the person you want to send it to.

Therefore, it is the mnemonic seed phrase that is of great importance here and I'm also very comfortable handling it as I have been able to store it in different ways that my capacity can reach the moment.
Conclusion
In the traditional financial applications which are inherently centralized, a user has to give out details of their identity which includes their name and signature. In decentralized applications, a user is given a public key and a private key. These keys come in different forms but they essentially act as the wallet address (account) and the access to operate the state of the wallet (signature). Because these decentralized applications are operated differently, therefore it is of paramount importance that users store the keys given to them in a very safe place.
Invest/Delegate your Steem Power and be assure of your daily income. Click here for more details.
Join our Discord Server & Community for more details
#club5050 😀