WikiLeaks Vault 7 - Part X: Athena

Today's Vault 7 release features Athena and its sister tool, Hera, which provide enhanced Windows exploitation capabilities. Athena and Hera are similar in concept to the previously mentioned Grasshopper and AfterMidnight but with some notable differences. Perhaps the most significant of these differences are that it was developed together with Siege Technologies, Inc., it can exploit Windows' Remote Access services and it was built to target all current versions of Windows including Windows Server 2012 and Windows 10.
As per usual this post will give a brief technical overview of how Athena operates, footprints for finding it and possible implications for the release.
The complete set of documentation of Athena is available on WikiLeaks.
Here are my summaries of the Vault 7 releases thus far:
- Part I: The CIA and NyanCat: The hackers and tools of Vault 7's "Year Zero"
- Part II: "Dark Matter" - All your Macintosh are belong to CIA
- Part III: Marble Framework - The CIA's cloaking device for hackers
- Part IV: Grasshopper and more research challenges!
- Part V: HIVE, Longhorn and the CIA's reign of cyberterror
- Part VI: Weeping Angel is listening...
- Part VII: Watch out for Scribbles!
- Part VIII: Archimedes/Fulcrum
- Part IX: AfterMidnight
Technical overview
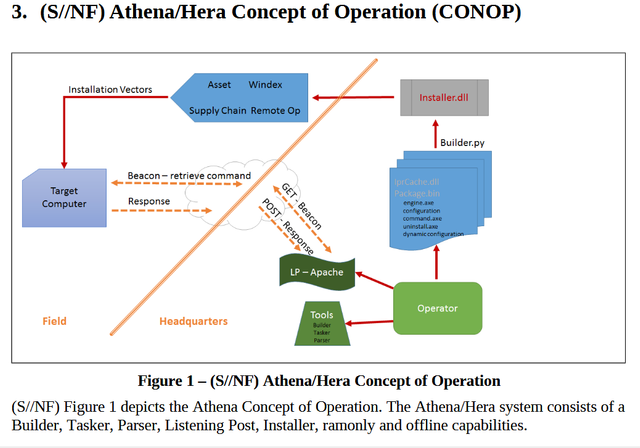
Athena, like Grasshopper and AfterMidnight, uses persistent DLL files to set up a backdoor to communicate with CIA listening posts. This also allows the CIA to send further commands to the exploited machine and upload additional payloads if needed.
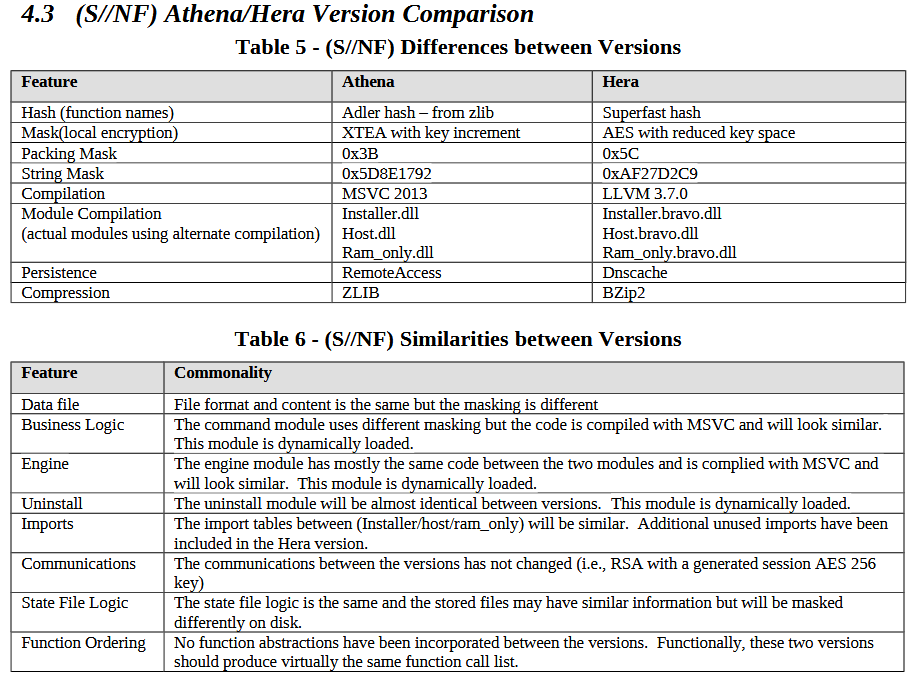
Athena and Hera, while two distinct tools, are almost identical in terms of functionality. In fact, Hera was originaly known as "ATHENA BRAVO". The key differences between the two them seem to be the methods of encryption used between the target machine and the CIA listening post and the Windows service they exploit. Athena, for instance, hijacks the Windows RemoteAccess service while Hera hijacks the Dnscache service. Here's the complete list of differences given in Athena's documentation:
In addition to the similarities above, both Athena and Hera are able to run in "RAM-only" (or diskless) mode. This means that after the first reboot these tools can run with full permissions and without needing to leave a single file on the target's disk.
Both tools are also able to be installed offline or "overtly". Offline installation, again like Grasshopper and AfterMidnight, allows a CIA operative to use a pre-configured USB flash drive to install Athena and Hera on the target system. "Overt" installation, however, utilizes other CIA tools to install the implant via remote means using an Installer DLL file that can be renamed however the agent needs.
While these tools target Windows, Athena and Hera are meant to typically be built on Ubuntu distributions of Linux. The Listening Posts are also meant to be Linux systems. All tools in Vault 7 considered, there should be a massive network of Ubuntu Linux servers throughout the Internet receiving such requests at this very moment.
Footprints
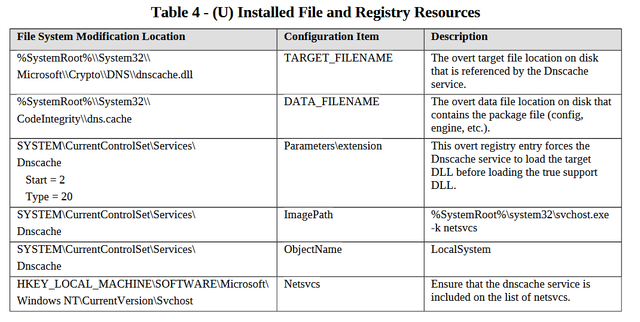
Athena and Hera do leave behind some evidence that they have been executed. If they were run in "RAM-only" mode, however, this footprint is considerably reduced (albeit this does require the use of more CIA tools). Since no file would be left on the target's disk, the only method for detection would be finding the Service or Windows Registry Keys associated with these tools.
These tools, like most CIA Vault 7 tools, were also developed not to set off personal security and anti-virus products. Avira anti-virus, however, is noted in the CIA's documentation as being able to detect RAM-only versions of Athena if they are not properly set up. Overall there is very little mention of PSP's hindering Athena's functions outside of this small blurb, however, which seems to indicate the CIA may have been successful in eventually breaking each PSP's detection methods.
Implications
From that last part you might be starting to get a clear picture for just how clever, if not dangerous, Athena and Hera are. Similar tools like Assassin and AfterMidnight have arguably more enhanced stealth and command functionality, but Athena is impressive in its broad range of target operating systems and its ability to be loaded into RAM only. What does this all mean?
Well over half of all desktop and laptop users run Windows systems with the most popular versions are 7 and 10 respectively.(1) Considering there's more than a couple billion computers in use today(2), this means that there are well over a billion vulnerable systems at this very moment.
To make matters worse this tool wasn't even developed exclusively by the CIA, but also included private software developer Siege Technologies, Inc. In this age where apparently the almighty dollar reigns supreme over all human rights, dignity and decency it seems that there is no underhanded tactic that the CIA wouldn't use to accomplish its own ends.
If you still need convincing as to why private and government agencies should not produce cyberweapons, here's a quote from the founder of Siege Technologies, Inc.:
I feel more comfortable working on electronic warfare. It’s a little different than bombs and nuclear weapons -- that’s a morally complex field to be in. Now instead of bombing things and having collateral damage, you can really reduce civilian casualties, which is a win for everybody.
I guess we'll just have to agree to disagree on the definition of "collateral damage", "civilian casualties" and who exactly "wins" in this situation...

Great summary. Important info to post.

Resharing @phibeteiota
Keep up the great work.
~The Management
Looks like a new "stone age" s fast approaching if we don't do something.
Thank you
thanks