Kelly 303: The 7/7 IFF Theater Club, Serco Patented Death Pool Re, Rothschild’s Con Air AWACS Wagers
General John F. Kelly
White House Chief of Staff
Washington, D.C. 20528
Open letter from the Cloud Centric Crime Scene Investigators of Abel Danger
June 27, 2018
Dear General Kelly:
Please accept Brief 303 from Field McConnell – United States Marine Corps whistle-blower and Global Operations Director of Abel Danger (AD) – wherein he announces AD’s proposal to set up a joint venture ‘7/7 IFF Theater Club’ in a London community injured by the switch from simulation exercises to live fire events in which fifty-two people were killed on the morning of 7th of July 2007 (7/7) after Serco (formerly RCA GB 1929) shareholders, Pool Re members and investment banker NM Rothschild & Sons Ltd., appear to have equipped Con Air SWAT teams, 22 SAS and friend-or-foe crisis actors with a patent pool of weaponised devices originally assembled by the late Victor Rothschild prior to Pearl Harbor 1941 to support wagering on spot-fixed body counts and times of victim deaths at mass casualty events.
AD believes that the victims of the 7/7 IFF events died after AWACS weapons directors switched from simulated exercises to live-fire attacks at times spot fixed by Serco agents who had been given custody of the NPL caesium fountain clock under the ‘Rothschild’s Cat for All Pigeons’ principle for U.K. government-funded research.
7/7 IFF Theater Club – Cast in Order of Appearance wherein actors play named individuals whose roles are based on information and belief of the Cloud Centric Crime Scene Investigators of Abel Danger
Christopher Hyman – Former Serco CEO. Scene 1 opens with a flash back to a 9/11 breakfast meeting at Windows on the World restaurant on the top floors (106th and 107th) of the North Tower (WTC1) before Hyman leaves at about 8:30 am to join representatives of Serco‘s private-equity groups, Serco‘s investment banker at N M Rothschild (Wilbur Ross) and Serco shareholders in a 47th Floor junket room to wait for 1st impact. On 7/7, Hyman coordinates fake news injects and media plays through 7/7 with the UK Cabinet Office and Peter Power.
Peter Power – Served in the 10 Battalion Parachute Regiment Territorial Army. Joined Metropolitan Police in 1971 attached Anti-Terrorist Branch. Set up his own company in central London, Visor Consultants in 1995. Dealt with terrorist bombs during the Provisional Irish Republican Army campaign. On 7 July 2005, he staged a crisis management simulation exercise with Serco’s CEO Christopher Hyman which was switched to live/digital fire for the 7/7 IFF events which killed 52 people.
Ghost of Jerome H. Lemelson (July 18, 1923 – October 1, 1997) – Inventor of Friend or foe detection system and method and expert system military action advisory system and method US 6166679 and Prisoner tracking and warning system and corresponding methods US 6054928 A who allegedly worked with former IP lawyers Hillary Clinton and Michelle Obama on ‘Con Air Lutnick Death Pool’ patents used in crashes of aircraft in the three major airline alliances of OneWorld, SkyTeam and Star Alliance.
Ghost of Victor Rothschild (31 October 1910 – 20 March 1990) – The Sixth Man. Bomb-disposal expert, chemist, biologist and former chairman of the Royal Commission on Gambling, allegedly assembled WWII patent pools which AD has now classified into the Four Horsemen of the Apocalypse families– Con Air, Boeing, Lutnick and Dum Dum – transferred by the Tizard Mission to the United States in 1940 as per RCA Corp’s Resonant cavity magnetron 1944-05-16 US2348986A Grant Priority date 1940-10-24 and currently in the custody of Serco agents at the United States Patent and Trademark Office.
David Hawkins – Play as Cambridge One Inventor of Deductive computing machine Priority date 1988-11-11 1991-04-03 EP0369695A3 Application. David tracked Victor Rothschild as the Fifth Man who transferred a patent pool in the 1940 Tizard Mission which matches signature of the Pearl Harbor attack.
Nicholas Soames – Churchill grandson. White’s Club member and part of the death pool elite. To be played as a Mycroft Holmes. Former Minister of State for the Armed Forces from 1994 to 1997 in the government of John Major. Introduced Mendenhall oath rituals to McConnell’s sister Kristine Marcy.
Rupert Soames – Churchill grandson. White’s Club member and part of the death-pool elite. Deployed Aggreko SWAT teams to power the Resilience mortuary at Honourable Artillery Company Grounds and ensure a bypass of 7/7 IFF autopsies which would have shown Con Air use of mil spec explosives.
Wilbur Ross – On 9/11, apparently hosted the Serco meeting on 47th Floor of WTC1 at the offices of Adjusters International in live communications with Pool Re command center in hall of The Worshipful Company of Insurers hall at Aldermanbury, near London Wall, a building owned and managed by the Chartered Insurance Institute and shared with the Worshipful Company of Firefighters.
Howard Lutnick – On 9/11 CEO of Cantor Fitzgerald who delivered his son to school while 658 of his colleagues died in WTC1. Bundler for Hillary Clinton. Inventor of Real-time interactive wagering on event outcomes US 8512129 B2 and with Lee M. Amaitis (The Brooklyn Bruiser) System and method for convenience gaming Priority date 2005-02-21 2006-02-21 EP20060735821 Withdrawn which allowed Serco Death Pool Re bettors access to wireless devices to conceal spot fixed betting from friends or foes.
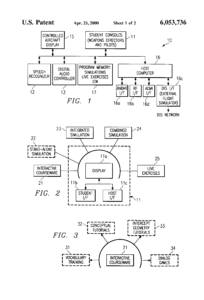
General Alexander Haig – Former SACEUR and alleged scriptwriter for Southwest Research Institute’s (SwRI) Interactive training system for AWACS weapons directors US6053736A device to switch simulations to live-fire or digital-fire attack on 9/11.
General John Shalikashvili – On 9/11 in Boeing’s new HQ in Chicago concealing the attacks with Boeing’s Encryption for asymmetric data links US7023996B2. Former Boeing director and former CJCS. Sent to China by Bill Clinton in 1997 to transfer details of all America’s weapons programs.
Kristine Marcy – On 9/11 in a Con Air war room. McConnell’s sister and former SBA COO. Marcy allegedly used money laundered by Rothschild through the U.S. DoJ Asset Forfeiture Fund to buy a Boeing 727 for the U.S. Marshals prisoner transportation service and create the largest transporter of prisoners in the world. Allegedly deployed SBA protégé companies for MitM attacks on AWACS weapons directors. Used Rosalyn N. Olsen’s Psychological analysis, communication, and educational apparatus US5511981A to identify SWAT teams members willing and able to execute 9/11 or 7/7 missions.
Field McConnell – United States Marine Corps whistle-blower and Global Operations Director of Abel Danger (AD). Has been tracking his Con Air sister Kristine Marcy since December 1988 when he briefed her how to handle a mutiny by droning her prisoner-transportation aircraft after which she appears to have procured Boeing Co’s Intervention flight management system 1989-03-07 US4811230A for targeted airlines.
Ed Butler – Head of Risk Analysis at Pool Re. Three decades of counter terrorism, international relations, intelligence, security and risk management experience much of which was gained during 24 years on front line service with the British Army. Commanded 22 SAS through AWACS weapons directors where the attacks on WTC1 and 2 were initiated with Lockheed Martin’s Rocket-Boosted Guided Hard Target Penetrator US 6276277 B1 and the Twin Towers demolished by crews dressed in Ace Elevator uniforms.
Oliver ‘Buck’ Revell – Former Senior Executive Service (SES-6) and FBI Director deputy in charge of Criminal Investigative, Counter-Terrorism and Counter-Intelligence activities who allegedly used Motorola’s Dynamic encryption key selection for encrypted radio transmissions US5222137A to hack a multichannel device held by the late FDNY Chief of Department Peter James Ganci Jr.; ignite WTC elevator-shaft incendiaries embedded in Arconic’s Double sheet aluminum panel US 20160096343 A1 with Qinetiq Explosive Device US20060243151A1 and conceal evidence of 9/11 murder for hire.
Dr. Thomas Barnett and Jules and Gideon Naudet – On 9/11 the brothers filmed attack on North Face of WTC1 and South Face of WTC and recorded the money shots for the first live broadcast mass snuff film in human history for distribution through the back channels of the BBC World Service.
Abel Danger invites you to check back into the apparent Con Air SWAT team snuff-film murder of JonBenet Ramsey on Christmas Day 1996 and ask yourself if the crime scene signature of S.B.T.C on the ransom note for $118,000 was telling officers of the military-industrial complex that Kristine Marcy's Small Business Theater Club could kill them or any members of their family at a time and a place of their choosing.
We hope one day soon you will help us fight digital fire with digital fire and that we can invite you and your cabinet colleagues to the opening nights of the world premieres of the 7/7 IFF and Twin Towers Theater Clubs.

Resilience Mortuary operated by Serco and UK Cabinet Office processed 7/7 IFF bodies without autopsies. Spoliation of evidence = Aggressive inference of guilt.


Yours sincerely,
Field McConnell
USMC 0116513
P O Box 39
Plum City WI 54761”
+001-715-307-8222
“Digital Fires Instructor Serco – [Marine Corps Base!] Camp Pendleton, CA Uses information derived from all military disciplines (e.g., aviation, ground combat, command and control, combat service support, intelligence, and opposing forces) to determine changes in enemy capabilities, vulnerabilities, and probable courses of action.”
“7 July 2005 London bombings
From Wikipedia, the free encyclopedia
"7/7" and "2005 London bombings" redirect here. For the calendar date, see 7 July. For the bombings that happened two weeks later, see 21 July 2005 London bombings. The 7 July 2005 London bombings, often referred to as 7/7, were a series of coordinated terrorist suicide attacks in London, United Kingdom, which targeted commuters travelling on the city's public transport system during the morning rush hour.
Four Islamic terrorists separately detonated three bombs in quick succession aboard London Underground trains across the city and, later, a fourth on a double-decker bus in Tavistock Square.[1] The train bombings occurred on the Circle line near Aldgate and at Edgware Road, and on the Piccadilly line near Russell Square.
Fifty-two people, all UK residents but of 18 different nationalities, were killed and more than 700 were injured in the attacks, making it Britain's deadliest terrorist incident since the 1988 bombing of Pan Am Flight 103 over Lockerbie, Scotland, as well as the country's first Islamic suicide attack.
The explosions were caused by homemade organic peroxide-based devices packed into backpacks. The bombings were followed two weeks later by a series of attempted attacks that failed to cause injury or damage. The 7 July attacks occurred the day after London had won its bid to host the 2012 Olympic Games.”
“Coincidence of bomb exercises?
By Nicholas Glass
Updated on 17 July 2005
It began when Peter Power, one time high ranking employee of Scotland Yard and member of its Anti-Terrorist Branch, reported in two major UK media outlets that his company Visor Consulting had on the morning of 7th of July been conducting 'crisis exercises' whose scenarios uncannily mirrored those of the actual attack.
In interviews on Radio 5 Live and ITV News, Power appeared to claim the exercises involved 'a thousand people' as well as a dedicated crisis team whose number was not specified. The consultant described the simulation of 'simultaneous attacks on a underground and mainline station' and 'bombs going off precisely at the railway stations' at which the actual bombings occurred.
Visor's crisis team, Power explained, were planning to practice the switch from what he called 'slow time' thinking to the 'quick time' thinking required by a crisis situation. In the event, they were forced to do so for real. 'Unusual though it may be to stop an exercise and go into real time,' he comments, 'it worked very well - although there were a few seconds when the audience didn't realise whether it was real or not.'
Three days after the London bombings, Power was in Toronto for the 15th World Conference on Disaster Management. There, he took part in a discussion panel for the Canadian Broadcasting Corporation's news discussion programme CBS: Sunday Night, in which he was quizzed again about what the host called the 'extraordinary' conjunction of his company's planned scenarios and the actual events. Power dismissed this as 'spooky coincidence'.
'Our scenario was very similar, but it wasn't totally identical,' he said. 'It was based on bombs going off - the time, the locations, all this sort of stuff. But it wasn't an accident, in the sense that London has a history of bombs.'
To many, this seemed a huge story wilfully ignored by the mainstream media. Online publishers stepped in to add fuel to the fires of indignation. Colman Jones, an Associate Producer on CBS: Sunday Night, claimed in his blog that, while escorting participants from the building, he enquired of Power 'why there had not been more media coverage of this.' 'They were trying to keep it quiet,' Power purportedly responded, with what Jones called 'a knowing smile.'
The rumours spread like wildfire: perhaps something lay behind the 'co-incidence' presented by Mr. Power. Prison Planet, the investigative journalism site which initially drew attention to the Radio 5 Live comments, set the tenor of online coverage in an article entitled 'London Underground Bombing "Exercises" Took Place at Same Time as Real Attack'. Here the authors argued that the simulated attacks were, whether Power knew it or not, intended to act as a cover for the real ones.
Part two of JJ King's report on the exercises that took place on the day of the London bombings.
'Whether Mr. Power and Visor Consultants were "in on the bombing" [...] is not that important,' their report stated. 'The British government or one of their private company offshoots could have hired Visor to run the exercise for a number of purposes. This is precisely what happened on the morning of September 11th 2001 with the CIA conducting drills of flying hijacked planes into the WTC and Pentagon at 8:30 in the morning.'
News agency Al Jazeera agreed, baldly asserting that 'The London Underground exercises were used as the fallback cover to carry out the attack.'
The background to these startling claims has to be appreciated. The idea that simulations and scenarios were used as decoys for intelligence activity around 9/11 has gained some currency amongst those who decry the 'official version' of events. Occasional reports in the mainstream media have added weight to the speculation.
Associated Press, for example, reported a 'simulated accident', scheduled for September 11th, 'in which an errant aircraft would crash into one of its buildings.' The article reports a spokesperson for the intelligence agency running the simulation, the ultra-secretive National Reconnaissance Office, describing the conjunction as a 'incredible coincidence' - just as Power did.
In the frenzy of linking, cross linking and careless speculation, however, it appears most self-publishers - and Al Jazeera - failed to contact Visor to corroborate their claims. In fact, the 'exercises' he spoke of on Five Live were carried out purely 'on paper', or at least PowerPoint, by a small group of seven or eight executives (Power remains tight-lipped about the client) seeking to examine the impact on corporate decision-making of a potential crisis situation. As Fintan Dunne, editor of BreakForNews.com points out, 'these types of private-sector "risk management" drills never use field staff.
Neither do [such] low-level corporate drills have active involvement of police or other security forces.' The exercise, therefore, was 'in no way comparable to U.S. drills and wargames on 9/11 - which were being run by active-duty security forces in the U.S. military, federal agencies, the FAA and various emergency services.'
As Power explained, the London bombing scenario was in fact one of three explored: another looked at the disruption that might be caused by unruly anti-globalisation demonstrators. In no case was there any real mobilisation of physical or human resources, which makes the case for 'planned' intelligence alibi look awfully flimsy, if not downright silly.
In the light of a brief interview with Power, the 'unbelievable' coincidence of events suddenly seems entirely comprehensible: the train stations targeted, after all, were all in central London -- any planner would pick these amongst a list of possible targets.
Indeed, in developing the London bombing scenario used in this exercise, Power's consultancy drew on the sort of scenario already explored in Osiris 2, a much-publicised major exercise initiated in the City of London to simulate a poison gas attack on the underground. Power further utilised his experience of taking part in Panorama's programme 'London Under Attack', another timely simulation.
And the date? That is indeed coincidence -- but an unbelievable one? 'Every week across the UK there are probably about hundred exercises, tests and simulations going on to get crisis teams familiar with their roles,' Power insists. 'We certainly do this regularly for many clients, the vast majority of them paper-based.'
Given this, the likelihood that one such simulation should fall on the day of an actual disaster is relatively high. Perhaps, who knows, that's the even case with oft-quoted simulations like the NRO's. 'When you hear hooves, think horses, not zebras,' goes the often-quoted popularisation of Occam's Razor.
In the absence of journalistic nous, bloggers would do well to stick by it.”
“Peter Power was born in the UK in 1951. He served in the 10 Battalion Parachute Regiment Territorial Army 1969 - 1971 before joining the Metropolitan Police in 1971. His service in that force included the Special Patrol Group and attachments to the Metropolitan Police Anti-Terrorist Branch and other front line units. In 1990 he transferred on promotion to Dorset. He retired from Dorset in 1993. In 1995 Power set up his own company in central London, Visor Consultants.
Achievements[edit]
He received several commendations [citation needed] for leadership etc.[clarification needed]. and in 1985 became a key architect/ promulgator of the Gold Silver Bronze command structure and also designed several mnemonics for dealing with terrorist bombs during the Provisional Irish Republican Army campaign [citation needed]. He is quoted in the UK government guide, "A Guide to GIS Applications in Integrated Emergency Management" [1] and he is the author of many other advice guidebooks including the original UK government (Department of Trade and Industry) booklet "Business Continuity Management - Preventing Chaos in a Crisis".[2] On 23 November 1984 Power was trapped with others on the London Underground during a serious Oxford Circus fire that started at that station and spread along the Victoria line. He helped to prevent panic amongst other passengers and subsequently led many people to safety.[3]
7 July 2005[edit] Power spoke on ITV and BBC TV news regarding a crisis management simulation exercise his company allegedly ran on this day, working in the premises of a private company in the City of London, using a scenario very similar to the 7 July 2005 London bombings. Power told the BBC that the exercise scenario included bombs going off at exactly the same stations as they actually did in the actual attacks. Power said that this coinciding of his exercise and the real attacks was a coincidence and was based on the previous terrorist incidents in London, including 18 bombs already detonated on the London Underground since 1885 (see Attacks on the London Underground). An investigation by the BBC series The Conspiracy Files identified the client Power's company worked for that day delivering a simulation exercise. It examined allegations about his company and others, involved in an alleged UK government "cover-up" similar to 9/11 conspiracy theories. Power has always denied this and the programme found no evidence to support such allegations.”
“Jerome H Lemelson’s Friend or foe detection system and method and expert system military action advisory system and method Priority date 1999-01-13 2000-12-26 US6166679A Grant Abstract A friend or foe detection system and method is disclosed. Friend or foe warning unit 20 has a geographic locating system, a communication system for communicating with each of the warning units, and a military force detection system for detecting military forces in a combat area and has a signal routing and control circuitry 50 for controlling operations. A number of components, devices, or sub-systems, such as a transmitter/receiver radio 28, an antenna 26, a microphone 30, a speaker 32, a battery 34, a display 36, a microprocessor 38, a memory 40, a camera 56, a radar/lidar input 54, on/off switch 52, a GPS location system 45 that includes a GPS processor 46, a GPS receiver 42, a GPS antenna 44, are coupled to the circuitry 50. Display 36 provides a display to the user of the unit 20 and shows the location of friendly forces as well as unfriendly or unidentified forces in the area. Display 36 displays text messages for the user of the warning unit 20. The microprocessor 38 together with memory 40 provide microprocessor control of the operations of the warning unit 20. The geographic locating system includes GPS processor 46, GPS receiver 42, and GPS antenna 44, and it is used to determine the exact location of the warning unit 20. The unit 20 is able to broadcast and receive military force information, such as location and status (i.e. friendly, unfriendly, unidentified statuses). An expert system military action advisory system and method for advising military troops or personnel of firing decisions is also disclosed. A firing index is determined based on the membership variables, and the firing index is used to help make the firing decisions. The membership variables and the firing index are defined for an expert system or fuzzy logic system, and the expert system or fuzzy logic system helps determine making the firing decisions. The system and method operate by transmitting target and friendly force GPS coordinate information to determine danger. Alternatively, only target coordinates are transmitted with fire danger indices calculated on a distributed basis by individual warning units and transmitted to the source of fire without friendly force location coordinates to assist in making final firing decisions”
“Inventor David Charles Hawkins’s Deductive computing machine Priority date 1988-11-11 1991-04-03 EP0369695A3 Application Abstract A deductive computing machine (30) comprise means which represent the bound energy in time of compositions with a conjunction relationship and/or means which represent the free energy in time of compositions with an inclusive disjunction relationship, and/or means which represent the time of events with an implication relationship. The machine (30) comprises a logic amplifier (13) having an energy tree (14) and a first input arranged to receive premises. The output of the logic amplifier is supplied to a knowledge database (15) comprising an event log(16), a process list (17) and an energy database (18). The knowledge database is connected to an interpolator (19) comprising a functions database (20) and maths routines (21). The output of the interpolator (19) is connected to a second input of the logic amplifier and to a display driver (22) for a colour monitor (23).”
“Of the 2,977 victims killed in the September 11 attacks, 412 were emergency workers in New York City who responded to the World Trade Center. This included:
343 firefighters (including a chaplain and two paramedics) of the New York City Fire Department (FDNY);[1]
37 police officers of the Port Authority of New York and New Jersey Police Department (PAPD);[2]
23 police officers of the New York City Police Department (NYPD);[3] and
8 emergency medical technicians and paramedics from private emergency medical services[4]
1 Patrolman from the New York Fire Patrol[5]”
“Otis to upgrade Empire State Building's elevators by dbcooper41 » Mon Jun 20, 2011 3:22 pm
to me this story is interesting because i firmly believe the world trade center elevator upgrade project was the cover for wiring the buildings to explode. It provided all the unlimited access they needed to pull wires, plant explosives, as well as install and test firing controllers. The charges appear to have been in the elevator shafts and the behavior of the ace elevator techs on 9/11/2001 was quite suspect. Only 1 elevator tech died on 9/11 and he worked for another company, otis iirc, at another building. The ACE guys all scattered like roaches.
I’m not suggesting they are gonna blow up the empire state building(not saying they won't either) but, an important point is made in the story:
"Only three elevator manufacturers — Schindler, ThyssenKrupp and Otis — could credibly compete, he said."
So, how did a no-name company called ACE elevator, which appears to be a mobbed up front company, manage to land the contract to upgrade the WTC elevators following the 1993 bombing?
An upgrade that was the largest in all of recorded history. Then ACE seems to have disappeared, though i have tracked a few employees to Charlotte, N.C. and then England.
The company seems to have gone Brigadoon on us.
If you don't know the ace elevator story i suggest you look in to it.
I'll look for my old reference material on it and answer any questions i can.”
“Serco farewell to NPL after 19 years of innovation
Published: 8 Jan 2015
Serco said goodbye to the National Physical Laboratory (NPL) at the end of December 2014 after 19 years of extraordinary innovation and science that has seen the establishment build a world-leading reputation and deliver billions of pounds of benefit for the UK economy. During that period under Serco's management and leadership, NPL has delivered an extraordinary variety and breadth of accomplishments for the UK's economy and industry. Some of the key achievements during that time have been: -
The beneficial impact of NPL's work to the economy is estimated at £2Bn pa.
In 2012, NPL's role in building the first maser to operate at room temperature was nominated by Physics World as one of the top ten breakthroughs of the year (CERN topped the list for their discovery of a Higgs-like particle).
NPL was instrumental in gaining a 50% increase in European funding for the EMPIR programme, with a total of EUR 600m.
It has been estimated that work carried out by the Centre of Carbon Measurement at NPL will save eight million tonnes of carbon emissions reductions (2% of UK footprint) and over half a billion pounds in economic benefit over the next decade.
Annually over 145,000 people undergoing radiotherapy have relied upon NPL for accurate delivery; it has been estimated that NPL's contribution to improving the accuracy of the radiation dose patients receive can save at least an additional 145 lives each year.
NPL's work on graphene - the new material that could revolutionise the future of high-speed electronics - has been widely acknowledged following a paper in Nature Nanotechnology and then was cited as one of 44 papers as part of 2010's Nobel Prize in Physics.
NPL achieved 11% per annum growth in third-party business since 2004; such work now accounts for over 40% of the lab's revenue, with £52M orders achieved in 2014.
Under Serco's management, Alan Turnbull was the first NPL scientist in many years to be elected as a Fellow of The Royal Society; Professor John Pethica, NPL's Chief Scientist was knighted, Seton Bennett was awarded a CBE, Kamal Hossain an OBE, and Patrick Gill and Michael de Podesta were awarded MBEs.
NPL's caesium fountain atomic clock is accurate to 1 second in 158 million years and NPL is playing a key role in introducing rigour to high frequency trading in the City through NPLTime.”
“The Worshipful Company of Insurers is one of the 110 Livery Companies of the City of London.
The Company was formed and became a Livery Company in 1979, on the same day as the Actuaries' Company. The Company is not just a society for those related to insurance and reinsurance but it also supports general charities and the education of students studying in the insurance field, and assists the relief of members, retired members or members suffering hardship, and the wives, widows, children, orphans and others depending upon them.
The Insurers' Company ranks 92nd in the City Livery Companies' order of precedence. Its motto is Omnium Defensor, Latin for Protector of All.
The Company is based at Insurance Hall on Aldermanbury, near London Wall, a building owned and managed by the Chartered Insurance Instituteand shared with the Worshipful Company of Firefighters.”
“Ed Butler is Head of Risk Analysis and a member of the Executive management team at Pool Re. Ed leads the terrorism risk analysis and research team and is responsible for developing the company’s capacity and capability in understanding the terrorism threat landscape. He has extensive experience spanning over three decades of counter terrorism, international relations, intelligence, security and risk management much of which was gained during 24 years on front line service with the British Army. Before joining Pool Re, Ed spent 8 years in the risk consulting sector, including roles as Head of Group Business Development at Salamanca Group and Executive Chairman of Salamanca Risk Management. He remains a Senior Advisor at S-RM. He was privileged to command 22 SAS over 9/11 and was Commander of British Forces Afghanistan in 2006, before retiring as a Brigadier General in 2008. He has an Honours degree in Politics and International Relations and a Masters from Cranfield University in Military Technology and Defence Studies.”
“Rothschild 'spied as the Fifth Man'
By DAVID LEITCH
Sunday 23 October 1994 00:02
The Independent Online
THE LATE Lord Rothschild, scientist, think-tank head, first- class cricketer, bomb-disposal expert and MI5 agent, was a super-spy for the Russians, according to a forthcoming book.
The Fifth Man, by the Australian author Roland Perry, claims to prove that Victor Rothschild stole 'all major UK/US weapons developments in the Second World War', including biological warfare, the atomic bomb and radar.
Specifically, he alleges that Rothschild, not Klaus Fuchs, or, as is generally believed, the civil servant John Cairncross, first alerted Stalin to Allied plans to build an atom bomb using plutonium 235.
Perry also claims that Rothschild, who died in 1990, was involved 'in so many aspects of spying that he seemed like a super-agent, sabotaging every Western intelligence initiative for 20 years after the war'.
The evidence offered is largely derived from three days of interviews in Moscow with seven retired KGB officers, some identified only by initials.”
“During the Second World War Victor worked for the Intelligence Service, and earned the George Medal for his bomb disposal work. In early 1939, he travelled to the United States where he visited the White House to discuss the issue of accepting Jewish refugees from Nazi Germany. In 1939, he was recruited to work for MI5 where he remained for the duration of the War. He was attached to B division, under deputy director Guy Liddell, responsible for counterespionage. In 1940 he produced a series of secret reports on German Espionage Under cover of Commerce and later founded section 'B1c' at Wormwood Scrubs, the wartime home of MI5. This was an 'explosives and sabotage section', and worked on identifying where Britain's war effort was vulnerable to sabotage and counter German sabotage attempts. This included personally dismantling examples of German booby traps and disguised explosives. For this, he was awarded won the George Medal in 1944 for dangerous work in hazardous circumstances. This involved dismantling a pair of German time bombs concealed in boxes of Spanish onions in Northampton. By late 1944, Victor was attached to the 105 Special Counter Intelligence Unit of the SHAEF, a joint operation of MI5 and X2, the counterespionage branch of OSS, a precursor of the CIA, operating in Paris.
After the War, Victor combined his academic interests with work for industry, joining the zoology department at Cambridge University. For his work on fertilization, he gained a DSc in 1950. He served as Chairman of the Agricultural Research Council from 1948 to 1958 and in 1961 he began work for Shell Research Ltd., serving as its Chairman from 1963 until his retirement in 1970. Victor was the first Director General of the Central Policy Review Staff from 1971 to 1974 (known popularly as 'The Think Tank'), a unit which researched policy specifically for the Government. In 1976 Victor chaired the Royal Commission on Gambling. In 1982 he published An Enquiry into the Social Science Research Council at the behest of Sir Keith Joseph, and he continued to work in security as an adviser to Margaret Thatcher. Throughout his life he was a valued adviser on intelligence and science to both Conservative and Labour Governments.”
“The Tizard Mission, officially the British Technical and Scientific Mission, was a British delegation that visited the United States during the Second World War in order to obtain the industrial resources to exploit the military potential of the research and development (R&D) work completed by the UK up to the beginning of World War II, but that Britain itself could not exploit due to the immediate requirements of war-related production. It received its popular name from the program's instigator, Henry Tizard. Tizard was a British scientist and chairman of the Aeronautical Research Committee, which had propelled the development of radar. .. The objective of the mission was to cooperate in science and technology with the U.S., which was neutral and, in many quarters, unwilling to become involved in the war. The U.S. had greater resources for development and production, which Britain desperately wanted to use. The information provided by the British delegation was subject to carefully vetted security procedures, and contained some of the greatest scientific advances made during the war. The shared technology included radar (in particular the greatly improved cavity magnetron which the American historian James Phinney Baxter III later called "the most valuable cargo ever brought to our shores"),[1] the design for the proximity VT fuse, details of Frank Whittle's jet engine and the Frisch–Peierls memorandum describing the feasibility of an atomic bomb. Though these may be considered the most significant, many other items were also transported, including designs for rockets, superchargers, gyroscopic gunsights, submarine detection devices, self-sealing fuel tanks and plastic explosives.”
“Con Air Lutnick Death Pool #1 – September 11 2001 – American Airlines Flight 11, a Boeing 767-200ER with 92 people on board, is hijacked after taking off from Boston, and is flown into the north tower of the World Trade Center in New York City; all on board are killed as well as around 1600 people on the ground and in the building; the collapse of both towers brings the total death toll from the two crashes to at least 2,763, the worst disaster involving commercial aircraft.
Con Air Lutnick Death Pool #2 – September 11 2001 United Airlines Flight 175, a Boeing 767-200 with 65 people on board, is hijacked after taking off from Boston and is flown into the south tower of the World Trade Center in New York City; all on board are killed as well as around 900 people on the ground and in the building; the collapse of both towers brings the total death toll from the two crashes to at least 2,763, the worst disaster involving commercial aircraft.
Con Air Lutnick Death Pool #3 – September 11 2001 – American Airlines Flight 77, a Boeing 757-200 with 64 people on board, is hijacked after taking off from Dulles International Airport and is flown into The Pentagon; all on board are killed as well as 125 people in the building and on the ground.
Con Air Lutnick Death Pool #4 – September 11 2001 – United Airlines Flight 93, a Boeing 757-200 with 44 people on board, is hijacked after taking off from Newark, New Jersey; passengers struggle with the hijackers, and the aircraft crashes in a field near Shanksville, Pennsylvania, killing all on board.
Con Air Lutnick Death Pool #5 – November 12 2001 – American Airlines Flight 587, an Airbus A300, crashes into a Queens neighborhood in New York City when the plane's vertical tail fin snaps off just after takeoff due to overuse of the rudder by the first officer during a wake turbulence encounter. All 251 passengers and nine crew members on board are killed as well as five people on the ground.
Con Air Lutnick Death Pool #6 – May 25 2002 – China Airlines Flight 611, a Boeing 747-200B, disintegrates above the Taiwan Strait in mid-flight due to maintenance error; killing all 225 people on board.
Con Air Lutnick Death Pool #7 – January 1 2007 – Adam Air Flight 574, a Boeing 737-400 with 102 people on board, crashes into the ocean off the island of Sulawesi in Indonesia, killing all on board in the worst ever crash involving the 737-400.
Con Air Lutnick Death Pool #8 – May 5 2007 – Kenya Airways Flight 507, a Boeing 737-800 with 114 people on board, crashes near Douala, Cameroon, killing all on board.
Con Air Lutnick Death Pool #9 – September 14 2008 – Aeroflot Flight 821, a Boeing 737, crashes on approach to Perm Airport from Moscow due to pilot error, killing all 88 people on board in the worst ever accident involving the Boeing 737-500.
Con Air Lutnick Death Pool #10 – June 1 2009 – Air France Flight 447, an Airbus A330 en route from Rio de Janeiro to Paris, crashes in the Atlantic Ocean, killing all 228 occupants, including 12 crew; bodies and aircraft debris are not recovered until several days later; the aircraft itself is not found until 2011. The crash remains the deadliest involving the A330.
Con Air Lutnick Death Pool #11 – January 25 2010 – Ethiopian Airlines Flight 409, a Boeing 737-800, crashes into the Mediterranean Sea shortly after takeoff from Beirut Rafic Hariri International Airport; the flight was heading to the Ethiopian capital, Addis Ababa; all 90 people on board perish.
Con Air Lutnick Death Pool #12 – May 9 2012 – In the Mount Salak Sukhoi Superjet 100 crash, a Sukhoi Superjet 100 crashes into Mount Salak, Indonesia, on an exhibition flight, killing all 45 passengers and crew on board.
Con Air Lutnick Death Pool #13 & #14 – March 8 2014 – Malaysia Airlines Flight 370, a Boeing 777 en route from Kuala Lumpur to Beijing with 227 passengers and 12 crew on board, disappears from radar over the Gulf of Thailand. A wing part was later found in Réunion. …. July 17 2014 – Malaysia Airlines Flight 17, a Boeing 777 en route from Amsterdam to Kuala Lumpur, is shot down over eastern Ukraine, killing all 283 passengers and 15 crew on board in the deadliest civilian airliner shootdown incident.
Con Air Lutnick Death Pool #15 – December 28 2014 – Indonesia AirAsia Flight 8501, an Airbus A320 en route from Surabaya, Indonesia to Singapore, crashes into waters off Borneo, killing all 155 passengers and seven crew on board.
Con Air Lutnick Death Pool #16 – March 24 2015 – Germanwings Flight 9525, an Airbus A320, crashes in southern France en route from Barcelona, Spain to Düsseldorf, Germany as a result of a deliberate act by the first officer. All 144 passengers and 6 crew on board the aircraft die in the crash.
Con Air Lutnick Death Pool #1 7 – October 31 2015 – Metrojet Flight 9268, an Airbus A321, explodes in mid-air over the Sinai Peninsula due to a terrorist bomb, 23 minutes after takeoff from Sharm-El-Sheikh, killing all 224 passengers and crew on board.
Con Air Lutnick Death Pool #18 – May 19 2016 – EgyptAir Flight 804, an Airbus A320, crashes into the eastern Mediterranean Sea after a series of sharp descending turns. All 56 passengers and 10 crew are killed.”
“Serco Awarded $95 Million Patent Classification Contract with the U.S. Patent and Trademark Office
November 30, 2015
RESTON, VA – November 30, 2015 – Serco Inc., a provider of professional, technology, and management services, announced today the Company has been awarded a patent classification services contract with the United States Patent and Trademark Office (USPTO). Serco will provide initial patent classification and reclassification services to support USPTO’s core mission of examining, granting, and disseminating patents and trademarks. The recompete contract has a one-year base period with four one-year option periods, and is valued at $95 million over the five-year period, if all options and award terms are exercised.
Serco’s highly trained Scientists and Engineers are responsible for reviewing, analyzing, and applying classification symbols to newly submitted patent applications to assist with the USPTO examination process. Throughout the classification process, our team performs comprehensive performance management; quality assurance; information security; training; knowledge management; and IT support, engineering, and development of custom software.
Serco has supported the USPTO under this program since its inception in 2006, and currently processes approximately 1,600 applications a day, and over 400,000 applications annually. Under the contract, Serco has been instrumental in assisting the USPTO as it transitioned to a new international classification standard called Cooperative Patent Classification (CPC) and will continue to provide services within CPC that enables the USPTO to align and lead within the global intellectual property environment. Work on this program will continue to take place in Harrisonburg, Virginia.
“We are extremely honored to have been selected to continue to deliver patent classification services to the U.S. Patent and Trademark Office,” said Dan Allen, Chairman and CEO of Serco Inc. “Our team continues our focus on operational excellence and incorporating innovative solutions, for classification services, in the most economic and efficient manner.”
About Serco Inc.: Serco Inc. is a leading provider of professional, technology, and management services. We advise, design, integrate, and deliver solutions that transform how clients achieve their missions. Our customer-first approach, robust portfolio of services, and global experience enable us to respond with solutions that achieve outcomes with value. Headquartered in Reston, Virginia, Serco Inc. has approximately 10,000 employees and an annual revenue of $1.2 billion. Serco Inc. is a wholly-owned subsidiary of Serco Group plc, a $5.9 billion international business that helps transform government and public services around the world. More information about Serco Inc. can be found at www.serco-na.com.”
“Rosalyn N. Olsen’s Psychological analysis, communication, and educational apparatus 1996-04-30 US5511981A Grant An apparatus that aids in the diagnosis and analysis of an individual suffering from a psychological ailment. The apparatus contains a top end and a bottom end wherein the top end represents a manic region and the bottom end represents a depression region. Between these two regions are the mild depression region, the normal region, and the hypomania region proceeding in order from bottom to top. Various elements that represent psychological states are provided so that the user can place the elements that represent that person's current state onto the appropriate region.”
“Healthcare in the UK & Europe Serco is trusted to manage vital healthcare services in the UK & Europe. With over two decades of delivering excellent services for the NHS, we have built a strong portfolio of support services. We employ over 5,000 people in various roles, from facilities management and managing estates and assets, to care coordination and business process services…. In the UK & Europe, we have over two decades of delivering award winning services for the NHS and currently serving 14 Acute Trusts, 5 Mental Health Trusts, 2 Community Services Trusts, 8 Clinical Commissioning Groups, 4 Regional/National NHS Organisations, and 1 Community Interest Company. We employ over 5,000 staff, with significant growth due to stronger outsourcing drives, and have reduced health service staffing costs by up to 35%.”
“Southwest Research Institute’s (SwRI) Interactive training system for AWACS weapons directors US6053736A Abstract A training system for training AWACS weapons directors. The training system is programmed so that the student can select between a number of different training modes. These include interactive courseware, simulation, and live exercise modes. The system includes a voice recognition unit that is trained to recognize AWACS terminology and to interactively teach them. Original Assignee Priority date 1997-10-17 … 2000-04-25 Grant”
“Jerome H. Lemelson’s Prisoner tracking and warning system and corresponding methods US 6054928 A
ABSTRACT A system and method for tracking, monitoring and learning prisoner or parolee behavior involves obtaining prisoner or parolee data and monitoring data for at least one individual prisoner or parolee, storing the prisoner or parolee data and monitored data into a database, learning prisoner or parolee behavior from the prisoner or parolee data and the monitored data in the database, and updating the prisoner or parolee data and the monitored data in the database. Expert system (i.e. including but not limited to fuzzy logic, reinforcement learning, neural networks, artificial intelligence, etc.) algorithms are executed for determining and analyzing deviated behavior by the prisoner or parolee. A parole level is assigned to the prisoner or parolee and it is determined whether the prisoner or parolee is to be moved up or down a parole level depending on whether the prisoner or parolee behavior does not constitute or does constitute prisoner or parolee violations. Furthermore, the system tracks, monitors, and learns the behavior of the prisoner or parolee by controlling and regulating the permitted/prohibited locations or sectors, the permitted/prohibited location or sector dwell times, the permitted/prohibited travel routes, the permitted/prohibited travel times that the prisoner or parolee spends at or between various locations.
Publication number: US6054928 A
Publication type: Grant
Application number: US 09/090,665
Publication date: 25 Apr 2000
Filing date: 4 Jun 1998
Priority date: 4 Jun 1998
Fee status: Paid
Also published as: US6437696, US20020067272
Inventors: Jerome H. Lemelson, deceased, 3 More »
Original Assignee: Lemelson Jerome H., Pedersen; Robert D., Hiett; John H.
Export Citation: BiBTeX, EndNote, RefMan
Patent Citations (55), Referenced by (257), Classifications (17),Legal Events (3)
External Links: USPTO, USPTO Assignment, Espacenet”
“Howard W Lutnick’s Real-time interactive wagering on event outcomes US 8512129 B2
ABSTRACT Systems and methods for real-time interactive wagering on event outcomes are presented. Clients are first qualified and given wagering limits before being allowed to interactively wager on event outcomes. Event outcomes may be based on, for example, financial markets and indices, sporting and entertainment events, casino performances, and natural phenomena such as weather and earthquakes. Events on which wagers can be placed include both those with known and unknown outcome probabilities, and wagers can be a fixed-odds type or a spread-bet type. Wager transactions, including acceptances and confirmations, are executed in real time. Clients can customize displays of events on which they are authorized to wager. Real-time client credit management, automatic dealer hedging, automatic price-spread adjustments, and automatic client and dealer defined wagering limits are also provided.
Publication number: US8512129 B2
Publication type: Grant
Application number: US 09/846,025
Publication date: Aug 20, 2013
Filing date: Apr 30, 2001
Priority date: May 1, 2000
Fee status: Paid
Also published as: CA2407679A1, 17 More »
Inventors: Philip M Ginsberg, Andrew C Gilbert, Howard W Lutnick, Lewis Findlay
Original Assignee: Cfph, Llc
Export Citation: BiBTeX, EndNote, RefMan
Patent Citations (181), Non-Patent Citations (83), Referenced by (5),Classifications (16), Legal Events (3)”
“Howard W. Lutnick’s and Lee M. Amaitis’s System and method for convenience gaming Abstract A convenience gaming system is provided. The convenience gaming system allows users to access applications via gaming communication devices coupled to a communication network. At least a portion of the network may be wireless. The gaming applications include gambling, financial, entertainment service, and other types of transactions. The system may include a user location determination feature to prevent users from conducting transactions from unauthorized areas. Priority date 2005-02-21 2006-02-21 EP20060735821 Withdrawn 2007-11-14 EP1854025A2 Application 2012-01-04 EP1854025A4 Application.”
“Boeing Co’s Encryption for asymmetric data links US7023996B2 Abstract A method is provided for asymmetrically encrypting data communicated between a ground platform and multiple airborne platforms. The method includes packet encrypting ground-based data so as to preserve routing information while encrypting the remaining data. The packet-encrypted data is then transmitted to the airborne platforms. The method also includes bulk encrypting airborne-based data so as to maximize security. The bulk-encrypted data is then transmitted to the ground platform. Priority date 2001-05-04 2006-04-04 US7023996B2 Grant”
“Boeing Co’s Intervention flight management system Priority date 1986-08-15 1989-03-07 US4811230A Grant An Intervention Flight Management System (IFMS) that allows a pilot to intervene in the operation of a preprogrammed flight management computer and change the speed and/or flight path of an airplane in response to air traffic control (ATC) instructions is disclosed. The IFMS includes an IFMS control panel via which the pilot interfaces with an IFMS program. The IFMS program includes intervention subroutines that override the preprogrammed instructions that control the flight management computer. The intervention subroutines include a lateral (direction) control subroutine and several vertical subroutines. The vertical subroutines include altitude, speed and vertical path subroutines. The intervention subroutines can be engaged independently of one another. Control axes unrelated to an engaged intervention subroutine remain under the control of the pre-programmed flight management computer instructions.”
“Serco Inc. Capabilities Chemical, Biological, Radiological, Nuclear and Explosive (CBRNE) Software Support Develop, demonstrate, implement and transition technologies to improve software/hardware development, fielding and sustainment support for chemical/biological detection and reconnaissance systems, individual and collective protection systems, decontamination systems, and information management systems for the Warfighter and First Responder, Homeland Defense and civil support activities. Robotics research using emerging software and hardware technologies such as 3D modeling and simulation and 3D printing for rapid prototyping innovations. Remote Weapon System Software and Control Unit Software Innovative methods in software engineering throughout the life cycle of program, in-house development, maintaining software to respond to future needs, and keeping interoperable with other Army systems. PC-based SW, embedded SW efforts, and the combination of both. Development of sensors and control systems, including lethal and non–lethal applications, military research operations, emergency response, testing, and training. Areas of expertise (1) Graphical User Interfaces (GUIs), (2) munition platform SW and/or munition effects SW, (3) fuse function, guidance, and control of flight SW, (4) sensor SW, (5) radio SW, (6) navigational guidance SW, (7) webbased graphical user interfaces (GUIs), and (8) training simulation SW. Information Systems and Infrastructure Support Manage information technology and computer/building infrastructure information systems. Provide centralized computing support; administrative information systems support; voice, data and video telecommunication support; and technology facilities maintenance. Design, build, install Audio Visual and smart building components to create automated state-of-the-art conference room capabilities. Develop, demonstrate, implement and transition technologies to improve concepts and designs that address DoD information technology needs, including logistics systems support and development, such as automated RFID inventory systems supporting office and depot controls. Information Assurance (IA) Engineering Support Development of prototype software that will streamline and automate Risk Management Framework (RMF). Army ordnance, tactical and battlefield automated weapon systems with embedded software require continual IA engineering and periodic validation to ensure that risk management is applied on Information Systems (IS). RMF defines a DoD-wide formal and standard set of activities, general tasks and a management structure process for the Certification & Accreditation (C&A) of a DoD IS that will maintain the Information Assurance (IA) posture throughout the system's life cycle.”
“The Emergency Planning College also known as “the Hawkhills” is a company based in the United Kingdom which is involved in activities to promote organisational resilience. Since 2010 the college has been operated by Serco, delivering training approved by the Civil Contingencies Secretariat (CCS) of the Cabinet Office. The college buildings are located at Easingwold near York in England. … Simulation and Media Support The method of delivering an exercise is flexible and will be designed with the client to meet their requirements with options ranging from simple paper-based delivery through to full use of their real communications systems and advance computer simulation. In addition, media play can also be added in the form of news injects and the provision of experienced journalists and television crews to help test procedures and also assist in training key staff.”
“A proxy war, occasionally also called a proxy fight, is an armed conflict between two states or non-state actors which act on the instigation or on behalf of other parties that are not directly involved in the hostilities.[1] In order for a conflict to be considered a proxy war, there must be a direct, long-term relationship between external actors and the belligerents involved.[2] The aforementioned relationship usually takes the form of funding, military training, arms, or other forms of material assistance which assist a belligerent party in sustaining its war effort.[2]”
Posted from my blog with SteemPress : https://www.abeldanger.org/kelly-303-the-7-7-iff-theater-club-serco-patented-death-pool-re-rothschilds-con-air-awacs-wagers/