CYBR; First, Professional Security for oOur Crypto Money Investments...
%20CYBRToken%20-%20Home%20-%20https___www.facebook.com_CYBRToken_.png)
Safety: is not living a critical phenomenon that affects our quality of life at all times and in all areas of our lives? One of the essential concerns that begin with human existence is security, even the most important. If you have security concerns, you will not also have the most basic needs. Man built castles, fortifications, sets, and invented Gates, sliders, locks during the ages of history only to feel safe. If you want to protect, especially if it is something that is very valuable to you, your concern increases, as well as your efforts to protect it, increases at that rate. Many encryption methods enable protected safes, many keys, and locks. You want help from banks' rental coffers of severe fees.
What if the information you're trying to protect is in a digital environment. Remember how nervous you were at first in your internet banking operations? What about the credit card information you provide during your online purchases? Remember your occasional remorseful wait until the card statement arrives. I know people who say I still don't shop online and don't share my card information with anyone. If your money, which is your future security, is entrusted to a number of binary digit codes? At this point, your sleep begins to run away for your precious asset, which you do not know what to entrust to whom. Moreover, you are very right to be nervous about this issue and to have security concerns. Especially for cryptocurrency owners using blockchain technology, there are so many negative examples in their environment.
Start from governments and giant companies, with both money and valuable information, deals or valuable paper, that is, tons of digital assets being thrown into the internet by almost all businesses and even individuals around the world. And that information can be captured by hackers almost as easily as they put it with their hands. Over the last ten years, platforms using Cryptocurrency and blockchain technology, which have been touted as the best protected against hacking by a large number of characters, decentralized structure, and blockchain technology, have lost millions of dollars to incredible hacker attacks. In 2014, Mt.Gox sought bankruptcy by announcing it had lost 750,000 bitcoins. "In June 2016 (Decentralized Autonomous Organization)$ 50 million of Dao was stolen. The reason was the solidity software, which was very easy to access to the Ethernet card. After the attack in April 2017, the South Korean Exchange Youbut said: "security should be started with recruitment, and then it should not neglect to improve system maintenance." In December 2017, Youbut was attacked again, and its holdings lost 17 percent of its total password. Parent company Yapian filed for bankruptcy. In January 2018, Coincheck was attacked for the Japanese cryptocurrency exchange. It lost about the US $ 534 million. Bancor collected the US $153 million in June 2017 and lost$23.5 million in an attack in July. You can expand this list further. And so far, I've never given an example of individual hacking.

Even with so many examples, I can undoubtedly write that the asset class, which we can call DLT (distributed ledger technologies) and cryptocurrencies, is absolutely vulnerable. Although governments try to take measures against digital theft through the anti-Hacking and computer fraud laws, the cost of the measures they create is more than the money stolen or there are demands for investigations that prevent investigations into social crimes such as the FBI.
So what to do then?
There can also be many answers to this question. But the common feature of these answers is that there are undoubtedly vulnerabilities in the world of blockchain, for which professional security companies need help from their professional software. So what is meant to be professional at this point? Or let's ask ourselves this question:

Who best protects us from hackers?
Of course, the best answer to this question is the experienced hacker who has used the vulnerabilities of digital networks, computers that have hacked federal networks many times!

Today I will introduce you to the security company CYBR and its founder:
Shawn Key became interested in vulnerabilities in Computer Networks and entered numerous federal networks in the late 90s. He revealed the" White Hat Pirate." He is known as the first to describe the concept of cybersecurity. Key, who has done serious work as a cybersecurity expert in the US military, developed his own software "Blindspot" to counter hacking attacks. It caught the attention of the" Dell's founders 50 " club. He has won numerous grants and awards for his work. The similarity of attacks on Cryptocurrency to traditional internet attacks caught his attention, and he turned to vulnerabilities in blockchain technology with blindspot software. He devoted his final years to working on securing smart contracts through the development of Blindspot. There is also a tiny museum in Virginia, where this interesting man, who has a hobby of detecting metals in civil war relics, collects and creates music in the background of Steve Augeri (former lead singer of Journey) on his multi-million selling album. Now let's look at the CYBR project created by this extraordinary personality.
CYBR is a holistic cybersecurity solution and constantly develops itself by combining with the latest technological software. Digital values bear the pretense of securing smart contracts and related activities. Daily antivirus software is nothing more than a compilation of known threats. BlindSpot, on the other hand, not only detects illegal file activity and APTs related to the "bad player," but corrupts them. There are three basic principles of risk management related to CTI
- Privacy 2. Integrity 3. Usability.
BlindSpot captures attack signatures by improving artificial intelligence (AI) machine learning. Good Cyber Threat Intelligence (CTI) constantly heals the information the software stands on, ensuring it is prepared for potential or current attacks that could threaten the system. In fact, the issue of cybersecurity is very important in the world, and yet another well-known fact is that there are few qualified people who will provide the level of security that will be needed.
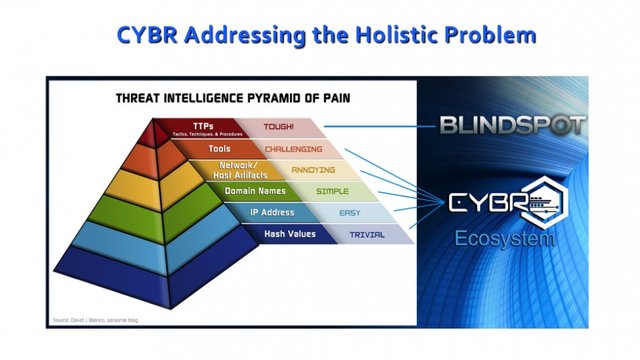
CYBR is like a two-fisted attack that provides real-time safeguards and measures against attacks. Threat intelligence secures operations through two different methods.
1-Blindspot: a special software and Threat Identification that generates potentially unlimited power
2-Portal: real-time data feed is used to ensure continuous preparedness.

Identifying a threat is also possible by trying to block his return. In a continuous effort to constantly evolve malware and therefore viruses, you've got to be identified and blocked. BlindSpot not only detects this type of illegal file activity and APTs but also disrupts them. By providing a safe port, it also rewards its users who are alert to threats. The number of companies using blockchain technology, which holds valuable paperwork such as the cryptocurrency world and smart contracts, is growing. The technology, which has recently attracted the attention of banks with its capabilities such as blockchain structure and the ability to evaluate enormous data with incredible speed and smartbook options, urgently needs to round up security vulnerabilities. And CYBR Security portal and Blindspot are candidates to deliver the gold standards needed in this regard.
One of the most important features of the CYBR project is that it creates a cybersecurity solution that uses its own software. With a preventative approach to the problem, it is assertive about uninterrupted security. Offering token rewards incentives to its users who identify threats, CYBR generates reports on them, analyzes data, makes risk determinations based on programmed AI algorithms, and distributes processed data reports to its subscribers.
An active cybersecurity system reaches a solution with four key:
- Infrastructure protection as a whole
- Proactive security,
- Timely Threat Identification
- Extracting information from the data that will turn into counter-action. With the promise of complete security in CYBR software, it offers its users a real security framework.
%20I%20Twitter%20-%20https___twitter.com_CYBR_Official.png)
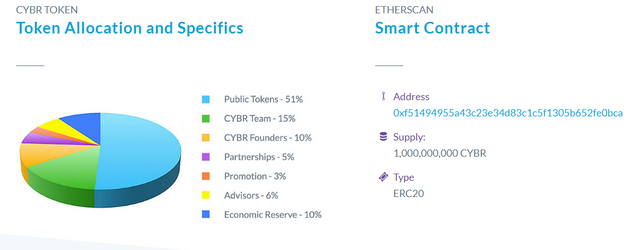
CYBR TOKEN:
CYBR Portal has also developed its own token CYBR i. The TNS feature of the wallet it creates has eliminated the danger of sending tokens to false or fake wallet addresses. One of the most beautiful features of the wallet is that it has facial recognition and a fingerprint reading (biometric).
CYBR TOKEN and ICO structure:
TokenSembolü: CYBR
Total Supply Quantity: 1,000,000,000
Platform: Ethereum
Type: ERC20
Soft cap: $ 2 million
Hard cap: $ 15 million
Token price: 1 CYBR = 0.08 US dollars
Token sale began on October 15, 2018, and will end on November 30, 2018
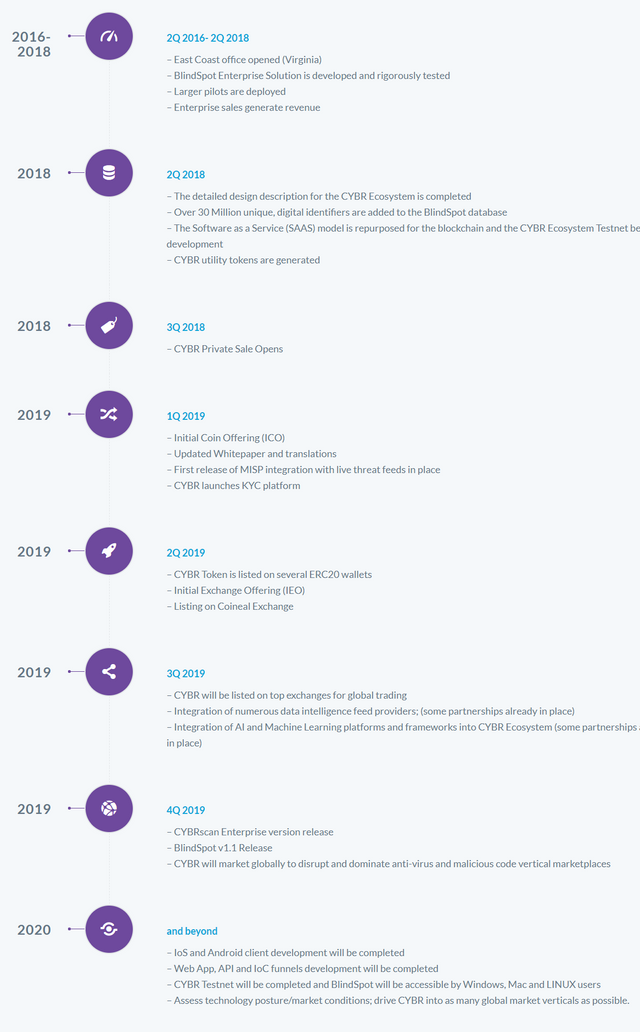
CYBR Roadmap
CYBR TEAM:

SUMMARIZE:
There are dozens of things to write to outline the project, which is headed to an extremely important issue for the entire blockchain world. However, I'll sum it up with three basic points:
1-those who know the vulnerabilities of the digital world are the hackers who capture them, and Shawn Key, the head of the developers of this project, is an ethical hacker who has entered many federal networks and worked for the military in the Middle East and Afghanistan.
- Key, the founder of the company, has an ambitious software that receives very important awards. Blindspot. And his work on security has also received serious grants.
2-most importantly, the project has already received serious support from investors and has passed the soft cap target.
I list below useful links for my investor friends where they can provide more information. I wish everyone plenty of wins.
By N.ipek Celik
Bitcointalk Username: naz14
Bitcointalk profile link: https://bitcointalk.org/index.php?action=profile; u=2221283
Partners:

USEFUL LINKS:
Website: https://cybrtoken.io/
Telegram: https://t.me/CYBRnetwork
Alpha version: https://cybrtoken.io/blindspot-mvp/
Whitepaper: https://cybrtoken.io/wp-content/uploads/2018/09/cybr-whitepaper.pdf
Bitcointalk ANN: https://bitcointalk.org/index.php?topic=5023957
Twitter: https://twitter.com/CYBR_Official
Facebook: https://www.facebook.com/CYBRToken/
MEW: 0x3b19a4A034Fd3687ba803a18F6779267893dFEff
Congratulations @nipek! You have completed the following achievement on the Steem blockchain and have been rewarded with new badge(s) :
You can view your badges on your Steem Board and compare to others on the Steem Ranking
If you no longer want to receive notifications, reply to this comment with the word
STOPVote for @Steemitboard as a witness to get one more award and increased upvotes!