How to secure your Steem webservice with a valid SSL certificate for free [Part 2]
Introduction
Hay ho,
in the last part we clarified why we should secure our web services with SSL/TLS and also stepped through some technical basics. In this part we finally want to answer the question „How can we get a free and valid certificate?“ and also want to add this certificate to an Apache Webserver.
As promised, I will show you two common ways how to request a SSL certificate:
- Generating a custom certificate
- Get a free and valid certificate using Let‘s Encrypt
Generate a certificate on your own
Let’s get started with the first approach: A self signed certificate.
Self-signed Certificate
It is quite funny that there are a lot of unsecured service in the internet and also in intranets of companies, because you can generate certificates on your own for 0$ in about one minute using openssl.
Just install it:
sudo apt-get install openssl
And generate a certificate for your domain/hostname:
sudo openssl req -x509 -nodes -days 365 -newkey rsa:2048 -keyout /selfsigned.key -out /selfsigned.crt
This command tells openssl to perform a certificate signing request (req parameter) to generate a self signed certificate (x509 parameter) without a passphrase (nodes) that expires in 365 days and uses a 2048 bit rsa key.
You will be asked some questions that you would also be asked if you request the certificate from an official CA, so just answer them:
Country Name (2 letter code) [AU]:US
State or Province Name (full name) [Some-State]:New York
Locality Name (eg, city) []:New York City
Organization Name (eg, company) [Internet Widgits Pty Ltd]:Bouncy Castles, Inc.
Organizational Unit Name (eg, section) []:Ministry of Water Slides
Common Name (e.g. server FQDN or YOUR name) []:server_IP_address
Email Address []:admin@your_domain.com
The results are a key and the certificate itself, which can be added to your application.
Quite easy – Isn’t it?
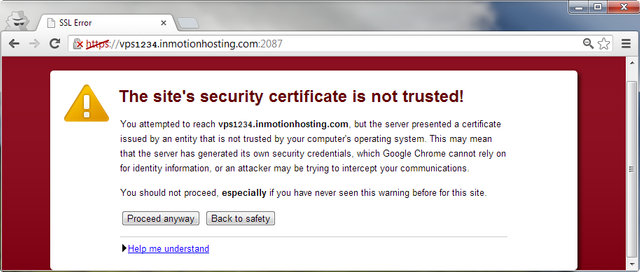
Sadly, this easy solution has one huge disadvantage: You’ve created the certificate on your own which makes you a CA - Great, isn’t it? Not really, because I don’t know you and I would not trust you at all. You can now say that I am a distrustful person, but actually all browsers, operating systems and application are doing the same: They only trust a predefined set of CAs and as long as your CA is not added to the trusted ones, the applications will return some great warnings like this:
Actually it is possible to add your CA to the operating system to get rid of this warning, but if you want to provide a service to customers I can promise you that they will just close the page instead of installing your CA.
So are there better solutions?
Request a certificate using Let‘s Encrypt
Yes, there are! Let‘s Encrypt is a service with the target to make the web more secure. It is mainly sponsored by

As you can see: All big browser companies support this project which also means that the Let‘s Encrypt CA is also installed by default in those browsers which means that your certificate will be trusted.
To make this clear: This type of certificate does not provide a better security than a self-signed one, you just get rid of the warnings.
Prerequisites
Let‘s Encrypt offers validate certificates so it needs to verify that you actually own the domain you want to request a certificate for. This can be done in two different ways:
- Have a DNS entry that points to your machein
- Place a special file on your webserver that can be accessed by Let’s Encrypt using the domain.
I think that most people just have a valid DNS entry for their domain that points to their server, so those of you are down. The others should have a look at the official how to guide.
Hands on
For this tutorial we will use the Let‘s Encrypt client. On my test machine running Ubuntu 16.04 this client can be installed by executing:
sudo apt-get update
sudo apt-get install python-letsencrypt-apache
The client makes it quite easy to request a certificate.
sudo letsencrypt -d example.com -d www.example.com
Please notice that you have to add all your subdomains you want to use the certificate for to the command above with an additional -d parameter.
You will then be guided through process that is nearly equal to the one we’ve seen when using the openssl command. This time, those parameters are actually useful: For example the email address you provide here can be used later to recover the key of your certificate.
After that you can find your certificates under:
/etc/letsencrypt/live
Can it be used for commercial services?
If you think about making money with your service this question is quite important for you – So I checked it.
According to some Let’s Encrypt guys in this thread, there are no limitations who can use this service. Great – We are allowed to use it for commercial services :)
Which one to choose?
Good question and as always the answer is: It depends. As described above Let‘s Encrypt requires that your machine can be accessed from the internet and that you have valid domain. So if you want to secure an internal connection for example in your intranet, Let‘s Encrypt will not work for you.
For all other scenarios you should go for Let‘s Encrypt. I am a lucky guy and fulfill their requirements, so I’ll use Let‘s Encrypt for my services.
Enable SSL to Apache
This step is quite easy. Both methods generate a “.key” file and a “.crt” file which can be easily added to the Apache Webserver by creating a new “.conf” file in the /etc/apache2/sites-enabled” folder:
<VirtualHost *:443>
SSLEngine on
SSLCertificateFile /path/to/cert.crt
SSLCertificateKeyFile /path/to/key.key
DocumentRoot /var/www/
</VirtualHost>
After that you only have to restart your apache Server and you are done!
If you go for Let’s Encrypt you can also just add the “--apache” to you request which will do this configuration automatically for you:
sudo letsencrypt --apache -d example.com -d www.example.com
And that’s it! You’ve successfully cared about the personal data of your customers/users – Good job :)
If you are interested in some technical stuff and java development you should press the button below to stay updated.
Thanks for reading and best regards!

It really is great that you are noting these tools here on steem thank you man.
No problem at all - I hope it will help some people here @steemit :)