PRISM did it come from PROMIS software stolen by a government agency. History of comms and devices for info gathering. Evidence of the data collection on sites and a bug involving All Devices.
This is a continuation of the article titled,
The history of PROMIS software and how it was developed from someone who worked for NSA, then had it allegedly Stolen by the DOJ
found here,
Here an overview found at the end of the article which tries to summarize and give a time line of this very involved story related to software allegedly stolen by the Department of Justice from a small company.
We went through all of the history of Promis earlier,
Quick breakdown again for a refresher,
Hillary Clinton was a Corporate Lawyer and Not a children's advocate for Rose Law Firm
Hillary Rodham Clinton was the intellectual property lawyer for Systematics. Part of this "intellectual property" involved a banking transaction software system based on the **PROMIS software.
A federal bankruptcy court ruled in 1987 that the US Justice Department "stole" the PROMIS software from a small company called Inslaw Inc when the DOJ refused to pay Inslaw for the software program and forced Inslaw into bankruptcy.
The US intelligence community took the PROMIS software and added a hidden "backdoor" for monitoring banking transactions and money laundering.
Systematics was the firm that the National Security Agency (NSA) used to get the PROMIS software with the hidden backdoor into the hands of banks worldwide.
The intellectual property that Hillary Clinton handled, and that Systematics marketed, was stolen from Inslaw.
Owners/Starters of Inslaw William Anthony Hamilton and his wife, Nancy Burke Hamilton
History of William or Bill Hamilton,

Bill Hamilton was employed by NSA for six years. He left the agency in 1966.
Bill's description of PROMIS,
PROMIS was designed to track the vast amount of criminal cases piling up in DOJ offices across the country. Bill Hamilton, in an interview for this story, recounted, “It was always a tracking program. It was designed to keep track of cases in local U.S. Attorneys’ offices, which means street crimes, keep track of the scheduled events in court, what actually takes place, who’s there, witnesses, police officers, conclusions, convictions, acquittals, whatever.”
- This stolen software was part of a major dispute in which Inslaw claimed the DOJ had stolen their software.
During the 12-year long legal proceedings, Inslaw accused the Department of Justice of conspiring to steal its software, attempting to drive it into Chapter 7 liquidation, using the stolen software for covert intelligence operations against foreign governments, and involvement in a murder. These accusations were eventually rejected by the special counsel and the Court of Federal Claims.
Did they have basis?
A little more history of PROMIS,
PROMIS was designed in the late 1970s and ‘80s to bring Department of Justice criminal case management from the dark ages into the light of the computer age. In the spring of 1981, the Reagan Administration hailed PROMIS as one of law enforcements greatest assets. By 1983, PROMIS had morphed into the behemoth of intelligence gathering. It was not state of the art – it was the art.
Over the ensuing decades PROMIS is reported to have been used by the DOJ, CIA, NSA, and several foreign intelligence agencies including Israel’s Mossad. The ownership of PROMIS has been the subject of federal court hearings and a congressional investigation.
The capabilities of PROMIS as a data collection and tracking program have never been a secret. But the only discussion of PROMIS has been about theft and black-market sales. Neither the courts nor Congress have ever inquired as to privacy issues or the ethics of the program. There has been no rending of political robes as seen with the Snowden case. In fact, the function of PROMIS has been discussed in open court and various public arenas.
As the LEAA dissolved in the late days of the Carter Administration, the Hamiltons formed Inslaw and began to make modifications to the public domain PROMIS. The short version: as originally designed, PROMIS ran only on 16-bit computers, using their own funds. INSLAW converted the program to run on 32-bit VAX computers which were massive for their time.
The Reagan administration was very taken with the Inslaw version of PROMIS. In March 1982 Inslaw was awarded $9.6 million to install the program in 20 U.S. Attorney’s offices, with further installations in the remaining 74 offices, if successful. This would be the last government contact the Hamiltons would receive, not because the system failed quite the contrary, it was too successful.
Hamilton explained,
“We developed it originally just for prosecutors.
But some of our users wanted to have it shared with the courts and the police.
So, the software was engineered to make it adaptable. In making it highly adaptable, a byproduct was to make it useable for non-prosecutor tracking and that made it adaptable totally outside the criminal justice system.”
It became obvious with the latest round of modifications any data system could be integrated into PROMIS.
And those data systems could interact that is, combine with each other forming a massive tracking data base of people via government documents such as birth and death certificates, licenses, mortgages, lawsuits or anything else kept in a data base.
PROMIS could also track banking transactions, arms shipments, communications, airplane parts again, anything kept in a data base.
Even more of the theft story,
With the discovery of these new capabilities Inslaw’s problems began. Unknowingly, the Hamiltons had embarked on an odyssey winding from the White House and the heart of the Reagan inner circle, bankruptcy court, a congressional investigation, secret informants, the CIA, NSA, and the Mossad.
The odyssey began in February 1983 when Dr. Ben Orr, an Israeli prosecutor, came to Hamilton’s office for a demonstration. He left, never placed an order and was never seen again. This was just one of the many demonstrations the company provided potential customers and the press. There was no shroud of secrecy about PROMIS or its capabilities.
Shortly after Dr. Orr’s visit, DOJ terminated payments to Inslaw, but refused to return the software. The company soon [June 1986] found its way into bankruptcy court. Inslaw put forth the claim that DOJ had stolen their software and made a concerted effort to drive them out of business. Bankruptcy Judge George Bason agreed.
In a 216-page opinion delivered in 1987, Judge Bason wrote that DOJ used “trickery, fraud and deceit” to steal PROMIS. He was later overruled by the DC District Court of Appeals on jurisdictional grounds. A previous district court supported his findings that PROMIS had been stolen. Bason became one of the very few Bankruptcy judges to not be re-appointed.
So in our reconstructed timeline Now Enter Prism which came from Promis.
During the 12-year long legal proceedings, Inslaw accused the Department of Justice of conspiring to steal its software, attempting to drive it into Chapter 7 liquidation, using the stolen software for covert intelligence operations against foreign governments, and involvement in a murder. These accusations were eventually rejected by the special counsel and the Court of Federal Claims.
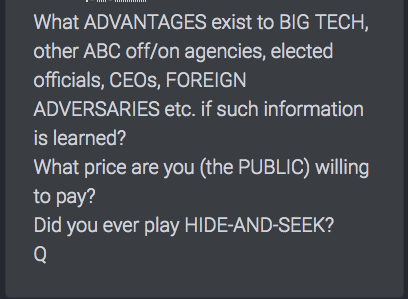
Q has pointed to the evidence of how the Deep State, Shadow Government, Globalist Controllers, whatever you wish to call them have been able to track info, communicate and control the information seen on various social media platforms and Search engines.
Here are a couple of examples.
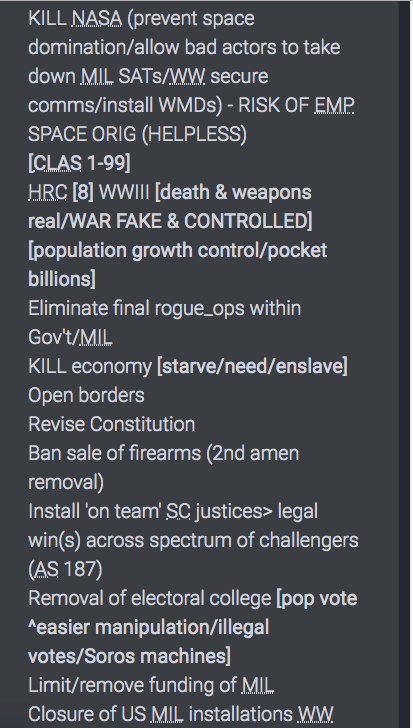
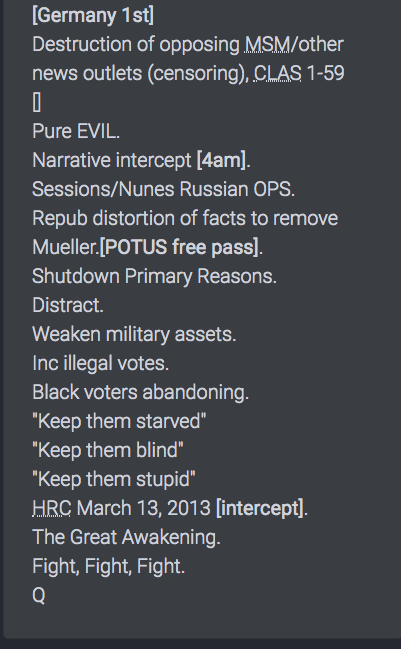
Another post from August 2018
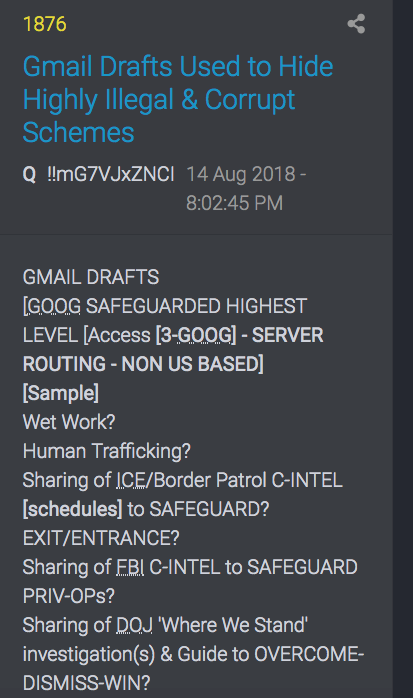
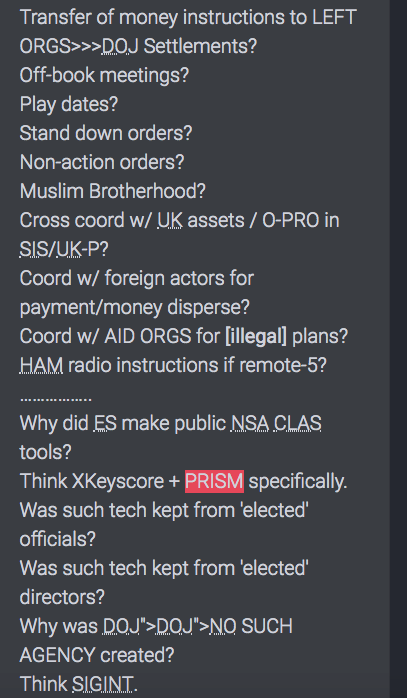
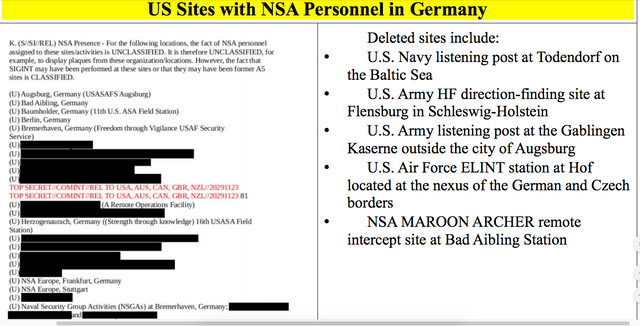
Remember SIGINT
Signals intelligence (SIGINT) is intelligence-gathering by interception of signals,
whether communications between people (communications intelligence—abbreviated to COMINT) or
from electronic signals not directly used in communication (electronic intelligence—abbreviated to ELINT).
Signals intelligence is a subset of intelligence collection management As sensitive information is often encrypted, signals intelligence in turn involves the use of cryptanalysis to decipher the messages. Traffic analysis—the study of who is signaling whom and in what quantity—is also used to derive information.
Historically involved like this,

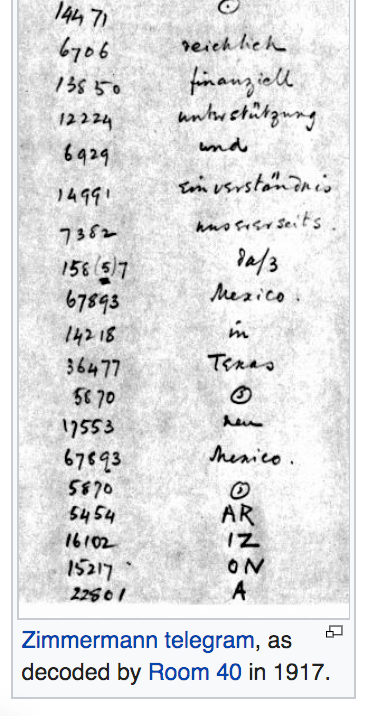
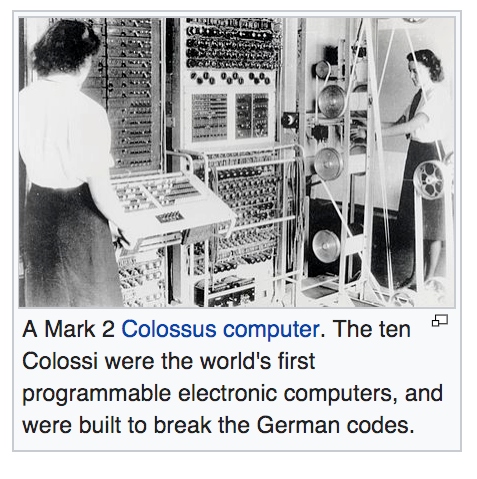
The use of SIGINT had even greater implications during World War II. The combined effort of intercepts and cryptanalysis for the whole of the British forces in World War II came under the code name "Ultra" managed from Government Code and Cypher School at Bletchley Park.
Government Code and Cypher School now known as Government Communications Headquarters or GCHQ,
Once again,
intelligence and security organisation responsible for providing signals intelligence (SIGINT) and information assurance to the government and armed forces of the United Kingdom
GCHQ was originally established after the First World War as the Government Code and Cypher School (GC&CS) and was known under that name until 1946.
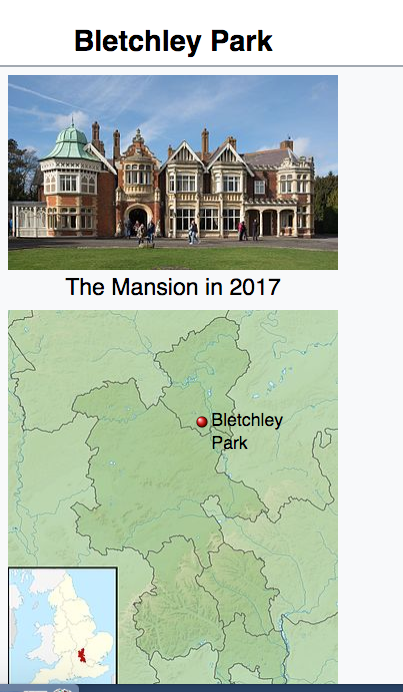
Bletchley Park is a nineteenth-century mansion and estate near Milton Keynes in Buckinghamshire, constructed during the years following 1883 for the English financier and politician Sir Herbert Samuel Leon in the Victorian Gothic, Tudor, and Dutch Baroque styles, on the site of older buildings of the same name. It has received latter-day fame as the central site for British (and subsequently, Allied) codebreakers during World War II, although at the time of their operation this fact was a closely guarded secret.
During the Second World War, the estate housed the British Government Code and Cypher School (GC&CS), which regularly penetrated the secret communications of the Axis Powers – most importantly the German Enigma and Lorenz ciphers; among its most notable early personnel the GC&CS team of codebreakers included Alan Turing, Gordon Welchman, Hugh Alexander and Stuart Milner-Barry.
The team at Bletchley Park devised automatic machinery to help with decryption, culminating in the development of Colossus, the world's first programmable digital electronic computer.
Modern SIGINT systems, therefore, have substantial communications among intercept platforms. Even if some platforms are clandestine, there is still a broadcast of information telling them where and how to look for signals.[16] A United States targeting system under development in the late 1990s, PSTS, constantly sends out information that helps the interceptors properly aim their antennas and tune their receivers. Larger intercept aircraft, such as the EP-3 or RC-135, have the on-board capability to do some target analysis and planning, but others, such as the RC-12 GUARDRAIL, are completely under ground direction. GUARDRAIL aircraft are fairly small, and usually work in units of three to cover a tactical SIGINT requirement, where the larger aircraft tend to be assigned strategic/national missions.
On July 1, 2019
14 Russian Sailors Killed in Fire on Nuclear Sub
Remember when?
In December 2016, a Russian military plane carrying 92 people, including dozens of Red Army Choir singers, crashed into the Black Sea en route to Syria where Russian forces are deployed. Everyone on board was killed.
Many military movements in the Black Sea currently.
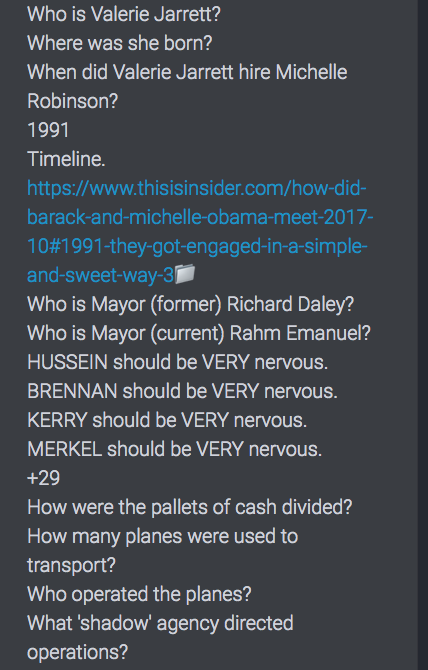
Jarrett was born in Shiraz, Iran
Jarrett got her start in Chicago politics in 1987 working for Mayor Harold Washington[12] as deputy corporation counsel for finance and development.
Jarrett continued to work in the mayor's office in the 1990s. She was deputy chief of staff for Mayor Richard Daley, during which time (1991) she hired Michelle Robinson, then engaged to Barack Obama, away from a private law firm.
Jarrett served as commissioner of the department of planning and development from 1992 through 1995, and she was chairwoman of the Chicago Transit Board from 1995 to 2005.
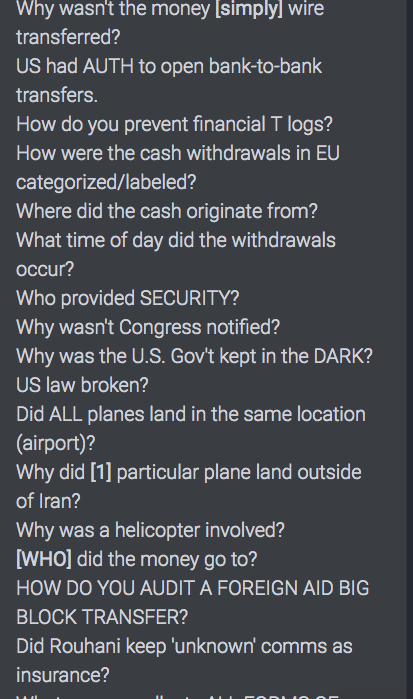
Israel says it is bracing militarily for possible U.S.-Iran escalation
The Iranian Deal. . .were we lied to and should the U.S. get out?
Now, let's pick up our story on the PROMIS software now that you have more background and connectors to have this ties in,
Taken from Richard L. Fricker, who lives in Tulsa, Oklahoma, and is a regular contributor to The Oklahoma Observer, where this article first appeared. His latest book, The Last Day of the War, is available at https://www.createspace.com/3804081 or at www.richardfricker.com. The entire story of the PROMIS software, Inslaw and what became known as “The Octopus” can be found in Fricker’s article that appeared in Wired magazine: http://www.wired.com/wired/archive/1.01/inslaw.html
With the discovery of these new capabilities Inslaw’s problems began. Unknowingly, the Hamiltons had embarked on an odyssey winding from the White House and the heart of the Reagan inner circle, bankruptcy court, a congressional investigation, secret informants, the CIA, NSA, and the Mossad.
The odyssey began in February 1983 when Dr. Ben Orr, an Israeli prosecutor, came to Hamilton’s office for a demonstration. He left, never placed an order and was never seen again. This was just one of the many demonstrations the company provided potential customers and the press. There was no shroud of secrecy about PROMIS or its capabilities.
Shortly after Dr. Orr’s visit, DOJ terminated payments to Inslaw, but refused to return the software. The company soon [June 1986] found its way into bankruptcy court. Inslaw put forth the claim that DOJ had stolen their software and made a concerted effort to drive them out of business. Bankruptcy Judge George Bason agreed.
In a 216-page opinion delivered in 1987, Judge Bason wrote that DOJ used “trickery, fraud and deceit” to steal PROMIS. He was later overruled by the DC District Court of Appeals on jurisdictional grounds. A previous district court supported his findings that PROMIS had been stolen. Bason became one of the very few Bankruptcy judges to not be re-appointed.
As the PROMIS odyssey continued, information began to surface that DOJ had provided the NSA and CIA with the enhanced 32-bit PROMIS. Stories began to circulate that friends of the Reagan Administration were selling black-market versions of PROMIS to anyone willing to pay the price.
Time and time again the veracity of government employees was called into question. In 1989 the chairman of the House Judiciary Committee, Rep. Jack Brooks D-Texas, launched what would become a three-year investigation into the theft of PROMIS and DOJ efforts to drive INSLAW out of business.
The Brooks report dated Aug. 11, 1992 not only agreed with Bason’s findings but went further: “High government officials were involved individuals testified under oath that Inslaw’s PROMIS software was stolen and distributed internationally in order to provide financial gain and to further intelligence and foreign policy objectives.”
The report includes scathing comments about former Attorney General Richard Thornburgh and several ranking DOJ staffers. Brooks recommended a settlement of Inslaw claims for damages and the appointment of a special prosecutor. Neither happened. Brooks said in an interview at the time, “[Inslaw] was ravaged by the Justice Department.” They were, he said, “treated like dogs.”
By this time nothing in the report surprised the Hamiltons. Seven months earlier they had discovered that their 1983 visitor, Dr. Ben Orr, was in fact Rafael Etian, chief of the Israeli Defense Force’s [IDF] anti-terrorism intelligence unit.
- They further learned he left Washington carrying a copy of PROMIS.
The DOJ explanation was that he was given the 16-bit version, not the new improved 32-bit VAX version. The question would be: why the subterfuge? And why show off the superior 32-bit VAX version and then only provide the cheaper model? DOJ has never answered the question.
Through all this, Inslaw has survived; Ireland installed PROMIS for case management, to track land records and in the bank credit system. Hamilton noted that every credit card transaction is tracked by PROMIS.
The Netherlands uses the program to keep track of all the inmates in their prison system. The city of Rome has PROMIS for use in their tax office. In fact PROMIS is being legally used in several countries around the world.
Illegally? Who knows. The Canadian government once wrote Inslaw asking for an operating manual. Inslaw never sold PROMIS to Canada. A similar event popped up with Lithuania when a member of their parliament asked for help with their PROMIS program. In each case, when told they may have a bootleg version, the reply was, it must be a different PROMIS.
To date, Inslaw has never received a dime for any government recommended settlements, some as high as $50 million.
Hamilton has declined to suggest that PROMIS was the frontrunner to PRISM. He said flatly in the interview for this article that his only information about PRISM is from news accounts.
Regardless of the Inslaw affair, PROMIS is still out there, still tracking whatever its masters require. And still, to this day, no one in government or otherwise has inquired, not about what PROMIS can do, but rather what is PROMIS doing, for whom and why.
PROMIS has been toiling in the intelligence caverns for nearly 30 years that’s a lot of data consumption, that’s a lot of tracking. Where is the PROMIS data? Compared to 30 years of information gathering and tracking by PROMIS, PRISM could be considered the equivalent of digital binge drinking.
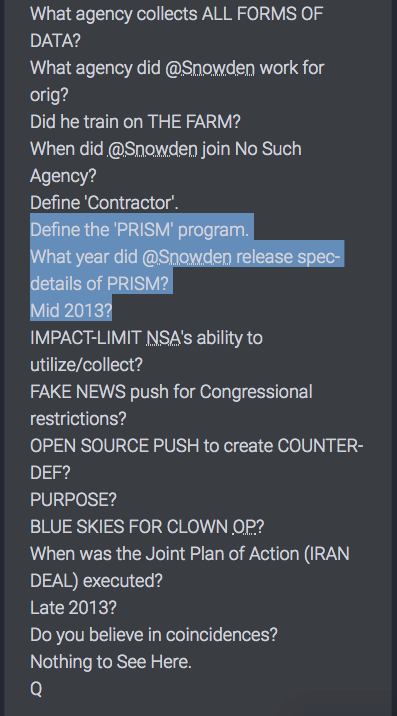
What is PRISM, which some believe came from PROMIS (developed by Inslaw),
PRISM began in 2007 in the wake of the passage of the Protect America Act under the Bush Administration. The program is operated under the supervision of the U.S. Foreign Intelligence Surveillance Court (FISA Court, or FISC) pursuant to the Foreign Intelligence Surveillance Act (FISA).
Its existence was leaked six years later by NSA contractor Edward Snowden, who warned that the extent of mass data collection was far greater than the public knew and included what he characterized as "dangerous" and "criminal" activities.
Washington Post releases four new slides from NSA's Prism presentation
https://www.theguardian.com/world/2013/jun/30/washington-post-new-slides-prism

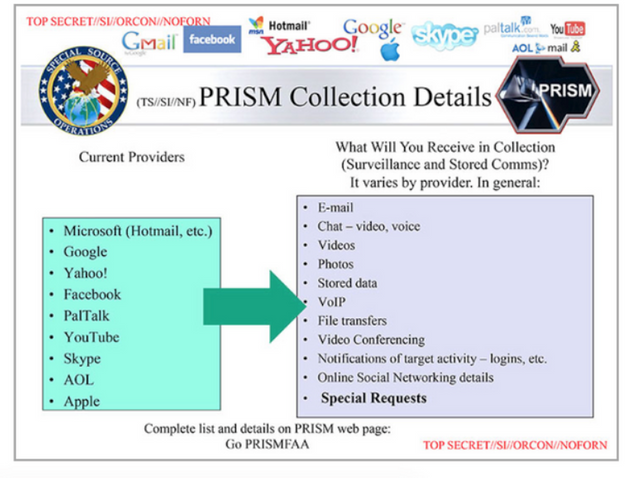
The newly published top-secret documents, which the newspaper has released with some redactions, give further details of how Prism interfaces with the nine companies, which include such giants as Google, Microsoft and Apple. According to annotations to the slides by the Washington Post, the new material shows how the FBI "deploys government equipment on private company property to retrieve matching information from a participating company, such as Microsoft or Yahoo and pass it without further review to the NSA".
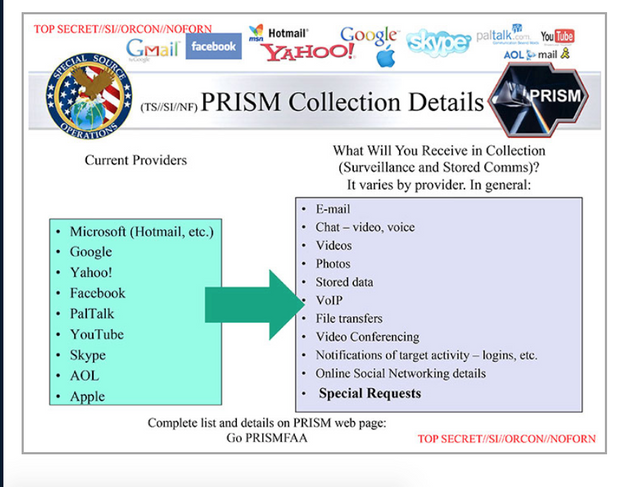
They also explain Prism's ability to gather real-time information on live voice, text, email or internet chat services, as well as to analyse stored data.
The new slides show how Prism interfaces with the internet companies as government agents track a new surveillance target.
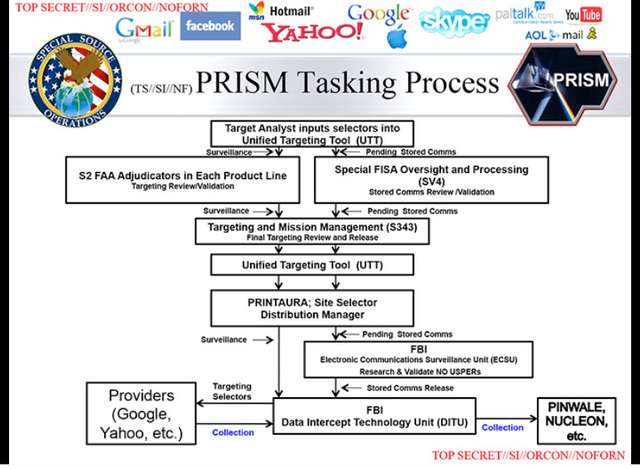
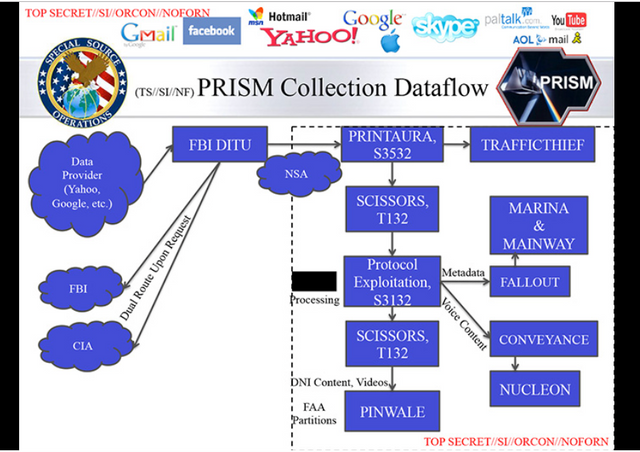
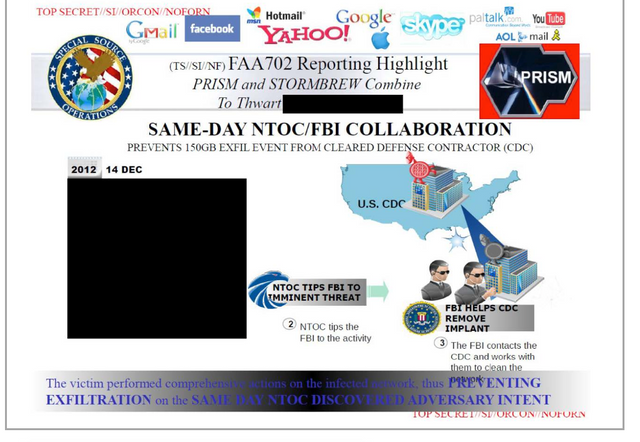
The data is intercepted by the FBI's "Data Intercept Technology Unit", the new slides suggest. From there it can be analysed by the FBI itself, or can be passed to the CIA "upon request".
It also automatically passes to various monitoring sections within the NSA. These include, the annotated slides suggest, databases where intercepted content and data is stored: Nucleon for voice, Pinwale for video, Mainway for call records and Marina for internet records.
One of the areas of greatest concern surrounding Prism and other NSA data-mining programmes has been that although they set their sights on foreign terror suspects, their digital net can catch thousands of unsuspecting Americans on US soil. The slides do not reveal how many US citizens have had their communications gathered "incidentally" in this way.
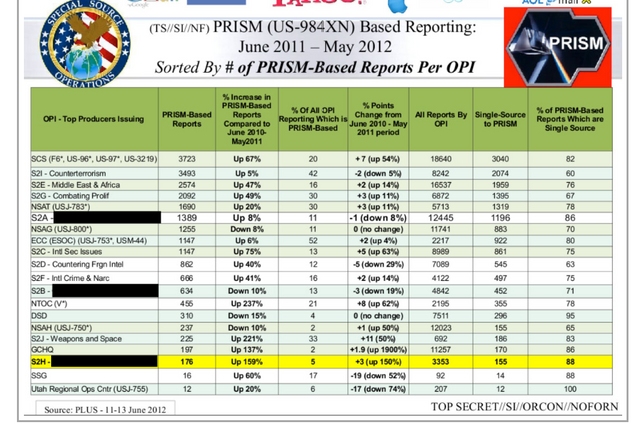
Subsequent documents have demonstrated a financial arrangement between the NSA's Special Source Operations division (SSO) and PRISM partners in the millions of dollars.
Documents indicate that PRISM is "the number one source of raw intelligence used for NSA analytic reports", and it accounts for 91% of the NSA's Internet traffic acquired under FISA section 702 authority."
The leaked information came to light one day after the revelation that the FISA Court had been ordering a subsidiary of telecommunications company Verizon Communications to turn over to the NSA logs tracking all of its customers' telephone calls.
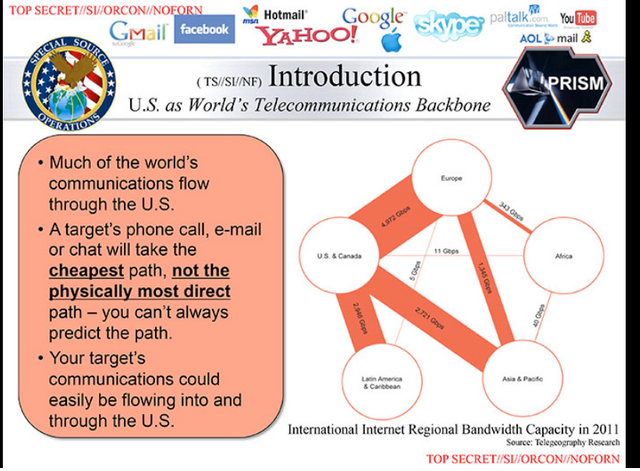
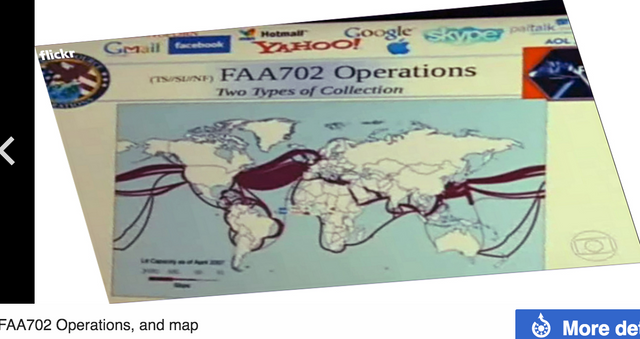
The slide presentation stated that much of the world's electronic communications pass through the U.S., because electronic communications data tend to follow the least expensive route rather than the most physically direct route, and the bulk of the world's Internet infrastructure is based in the United States.
The presentation noted that these facts provide United States intelligence analysts with opportunities for intercepting the communications of foreign targets as their electronic data pass into or through the United States.
Several of the participating companies listed on the third new slide released by the Washington Post – Microsoft, Yahoo, Google, Facebook, PalTalk, YouTube, Skype, AOL and Apple.
Snowden's subsequent disclosures included statements that government agencies such as the United Kingdom's GCHQ also undertook mass interception and tracking of Internet and communications data – described by Germany as "nightmarish" if true – allegations that the NSA engaged in "dangerous" and "criminal" activity by "hacking" civilian infrastructure networks in other countries such as "universities, hospitals, and private businesses", and alleged that compliance offered only very limited restrictive effect on mass data collection practices (including of Americans) since restrictions "are policy-based, not technically based, and can change at any time", adding that "Additionally, audits are cursory, incomplete, and easily fooled by fake justifications", with numerous self-granted exceptions, and that NSA policies encourage staff to assume the benefit of the doubt in cases of uncertainty.
Inside the New York hospital hackers took down for 6 weeks
https://www.cbsnews.com/news/cbsn-on-assignment-hackers-targeting-medical-industry-hospitals/
Hacking of Health Care Records Skyrockets
https://www.nbcnews.com/news/us-news/hacking-health-care-records-skyrockets-n517686
U.S. hospitals have been hit by the global ransomware attack
https://www.vox.com/2017/6/27/15881666/global-eu-cyber-attack-us-hackers-nsa-hospitals
Hospital network hacked, 4.5 million records stolen
https://money.cnn.com/2014/08/18/technology/security/hospital-chs-hack/index.html
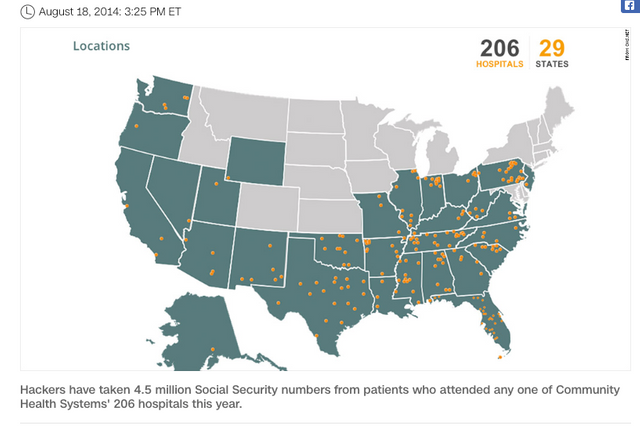
U.S. hospitals are getting hit by hackers
https://money.cnn.com/2016/03/23/technology/hospital-ransomware/index.html
The hospital held hostage by hackers
https://www.cnbc.com/2016/02/16/the-hospital-held-hostage-by-hackers.html
Why is this happening?
Is this all by mere accident or by design?
referred to is Section 702 of the FISA Amendments Act ("FAA"), and not the Federal Aviation Administration, which is more widely known by the same FAA initialism.
Intro slide,
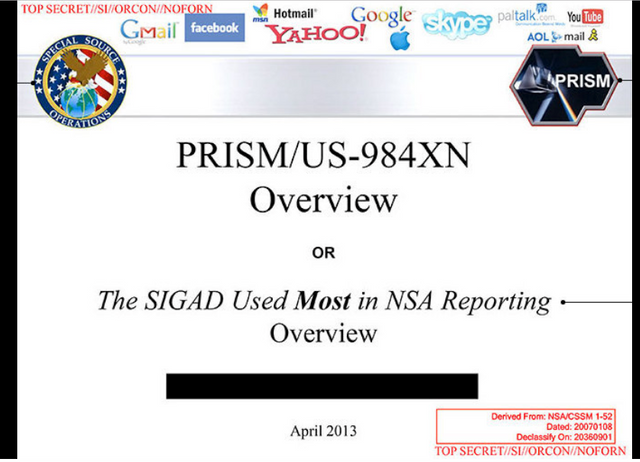
Slide showing that much of the world's communications flow through the U.S.
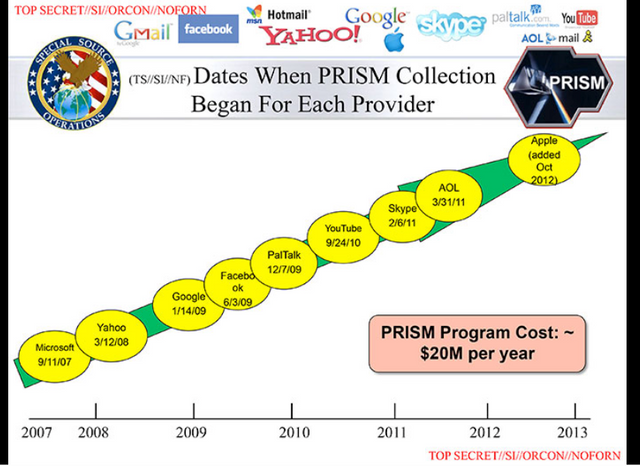
Details of information collected via PRISM

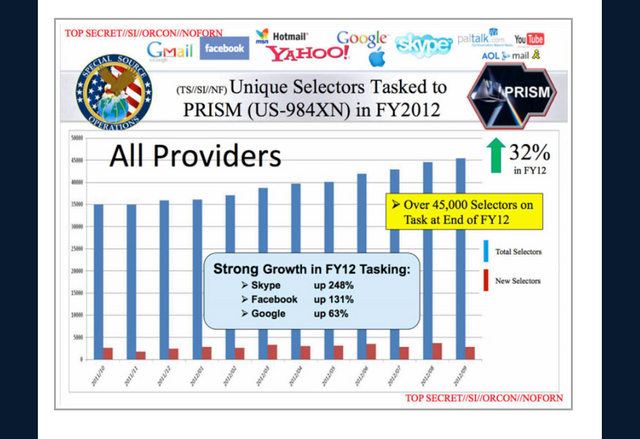
companies and the date that PRISM collection began
PRISM's tasking process
PRISM collection dataflow
PRISM case numbers
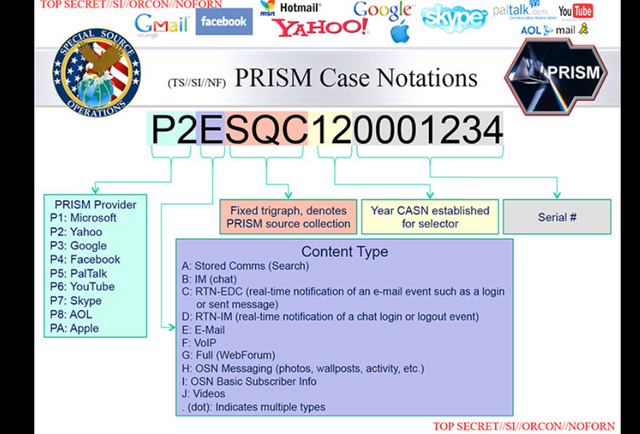
REPRISMFISA Web app

Upstream collection





Unredacted,


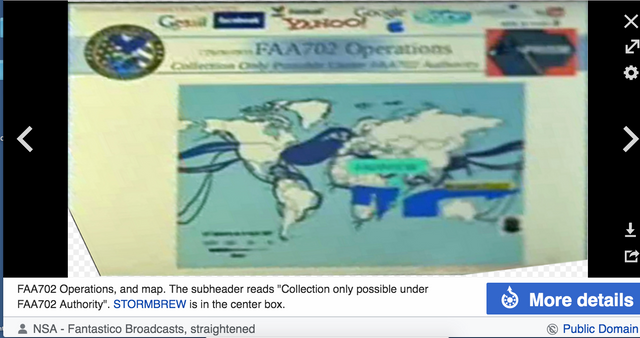
Some SIGADs, like PRISM, collect data at the ISP level, but others take it from the top-level infrastructure. This type of collection is known as "upstream". Upstream collection includes programs known by the blanket terms BLARNEY, FAIRVIEW, OAKSTAR and STORMBREW
Data that is integrated into a SIGAD can be gathered in other ways besides upstream, and from the service providers, for instance it can be collected from passive sensors around embassies, or even stolen from an individual computer network in a hacking attack.
Not all SIGADs involve upstream collection, for instance, data could be taken directly from a service provider, either by agreement (as is the case with PRISM), by means of hacking, or other ways.
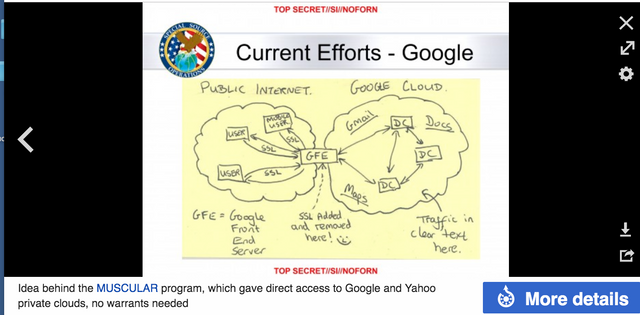
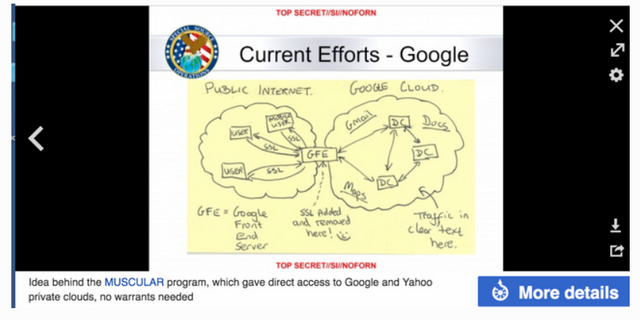
MUSCULAR program requires no (FISA or other type of) warrants.
Qanon drops Eric Schmidt Google used corporate power to influence an election! We have All the emails. See vital one here. Nothing is Ever Erased!
Besides the information collection program started in 2007, there are two other programs sharing the name PRISM:[201]
The Planning tool for Resource Integration, Synchronization and Management (PRISM), a web tool used by US military intelligence to send tasks and instructions to data collection platforms deployed to military operations.
The Portal for Real-time Information Sharing and Management (PRISM), whose existence was revealed by the NSA in July 2013. This is an internal NSA program for real-time sharing of information which is apparently located in the NSA's Information Assurance Directorate.
Remember PRISM aka SIGAD US-984XN
What is Spectre?
a vulnerability that affects modern microprocessors that perform branch prediction
a digital circuit that tries to guess which way a branch (e.g. an if–then–else structure) will go before this is known definitively.
The branch that is guessed to be the most likely is then fetched and speculatively executed.
Thus why this is they logo,
- an optimization technique where a computer system performs some task that may not be needed. Work is done before it is known whether it is actually needed, so as to prevent a delay that would have to be incurred by doing the work after it is known that it is needed. If it turns out the work was not needed after all, most changes made by the work are reverted and the results are ignored.
A website can read data stored in the browser for another website, or the browser's memory itself.
As of 2018, almost every computer system is affected by Spectre, including desktops, laptops, and mobile devices. Specifically, Spectre has been shown to work on Intel, AMD, ARM-based, and IBM processors.
It was discovered measuring the access time to data lets a nefarious application determine if the information was read from the cache or not. If it was read from the cache the access time would be very short, meaning the data read could contain the private key of encryption algorithms.
Spectre is a vulnerability that tricks a program into accessing arbitrary locations in the program's memory space. An attacker may read the content of accessed memory, and thus potentially obtain sensitive data.
On January 28, 2018, it was reported thatIntel shared news of the Meltdown and Spectre security vulnerabilities with Chinese technology companies, before notifying the U.S. government of the flaws.
Covert channels were found, especially on processors with a pipeline used by more than one processor core.
Instead of a single easy-to-fix vulnerability, the Spectre white paper describes a whole class of potential vulnerabilities. They are all based on exploiting side effects of speculative execution, a common means of hiding memory latency and so speeding up execution in modern microprocessors.
Spectre centers on branch prediction, which is a special case of speculative execution. Unlike the related Meltdown vulnerability disclosed at the same time, Spectre does not rely on a specific feature of a single processor's memory management and protection system, but is a more generalized idea.
The basic difference between Spectre and Meltdown is that Spectre can be used to manipulate a process into revealing its own data. On the other hand, Meltdown can be used to read privileged memory in a process's address space which even the process itself would normally be unable to access (on some unprotected OSes this includes data belonging to the kernel or other processes).
On January 29, 2018, Microsoft was reported to have released a Windows update that disabled the problematic Intel Microcode fix—which had, in some cases, caused reboots, system instability, and data loss/corruption
According to Amazon Deutschland, Cyberus Technology, SYSGO, and Colin Percival (FreeBSD), Intel has revealed details on the third Spectre-NG variant CVE-2018-3665 (Lazy FP State Restore, Intel SA-00145) on June 13, 2018. It is also known as Lazy FPU state leak (abbreviated "LazyFP") and "Spectre-NG 3".
There were far more variants of Spectre attacks revealed in different locations remotely.
One was at the end of July 2018, researchers at the University of Graz in Australia revealed "NetSpectre", a new type of remote attack similar to Spectre V1, but which does not need attacker-controlled code to be run on the target device at all.
Spectre has the potential of having a greater impact on cloud providers than Meltdown.
Spectre can allow malicious programs to induce a hypervisor to transmit the data to a guest system running on top of it.
In February 2019, it was reported that there are variants of Spectre threat that cannot be effectively mitigated in software at all.
The Spectre bug means White hats have intel on the Clintons and other information related to pedogate. Once this info has been acquired, it is archived so "We have it All!"
Sources,
https://consortiumnews.com/2013/07/11/prisms-controversial-forerunner/
https://www.theblackvault.com/documentarchive/nsa-surveillance-program-promis/#
http://members.efn.org/~paulmd/OwnWork/FallingRedactions2.pdf
Curated for #informationwar (by @wakeupnd)
Ways you can help the @informationwar!
Never forget. . .Hillary played a roll in patents and information protection. . .who was she and all the cohorts who try to keep information attempting to hide it from? Civilians, the population, those they feel beneath them as they continue to try to control.
Don't let them!
https://www.upcounsel.com/classified-patents?fbclid=IwAR2gZOvUv-DgAJ-pRsZk1j3XldzHUVui4MqMFMHeZ6YSXShZcZv2WZg8GWg