A Monero Introduction for Beginners

Monero is a rather unique cryptocurrency. It doesn't try to do anything unusual, or be Turing-complete like Ethereum. It just tries to be very good at one thing: the private and secure transfer of value.
This post will cover the very basics of Monero. It expects the reader to be technology-literate, but not necessarily know anything about how either Bitcoin or Monero work. These will all be discussed on a high level.
Let's Begin with Bitcoin
As with most resources, we will actually start by discussing Bitcoin, since it is much simpler to understand. Bitcoin is a decentralized network that is maintained by thousands of computers around the world. In the simplest sense, Bitcoin's network consists of nodes and miners.
Nodes maintain a copy of all the transactions that have ever happened. Suppose I sent you 0.1 BTC. The record of my address sending you this Bitcoin would appear in a block. Blocks contain the most recent ~10 minutes of transactions. All these blocks together form a chain, thus named the blockchain. The blockchain forever grows larger with more and more history of transactions happening on the network.
Miners aid the network by signing these blocks. The network creates a problem set that takes many attempts to solve it. The faster your computer is, the more attempts it can make each second. Miners compete against each other to solve the next puzzle, and the one who solves it get a reward. Bitcoin stays secure since the next miner to solve this puzzle is unknown. It can be any miner, and so long as no one controls a substantial portion of "hashing" power, then the network can stay secure. No one attacker can manipulate the network to solve a substantial number of blocks in a row. You don't need to trust these miners, since no one entity is large enough to negatively impact the network.
Each transaction is given a unique identifying ID, and details regarding the sending address, receiving address, and amount are all visible. Note that most of these details are long strings of randomly-generated numbers and letters.

Now let's look closer at this individual transaction. Suppose Bob's wallet contains 4 inputs of 0.1 BTC, 0.5 BTC, 0.75 BTC, and 1 BTC (for a total balance of 2.35 BTC), and he would like to send 0.1 BTC to Alice. You can think of these inputs as dollar bills. It's similar to saying Bob has $180 in his wallet, divided into one each of a $100 bill, $50 bill, $20 bill, and $10 bill.
In person, if Bob wanted to give $20 to Alice, he can just hand her the $20 bill. On the blockchain, a similar thing happens with these Bitcoin inputs.
Note: I am showing the transfer of a singe input for the exact amount for simplicity. The transfer is slightly more complex with more inputs and when sending a different amount than a single input, but the general ideas are the same.
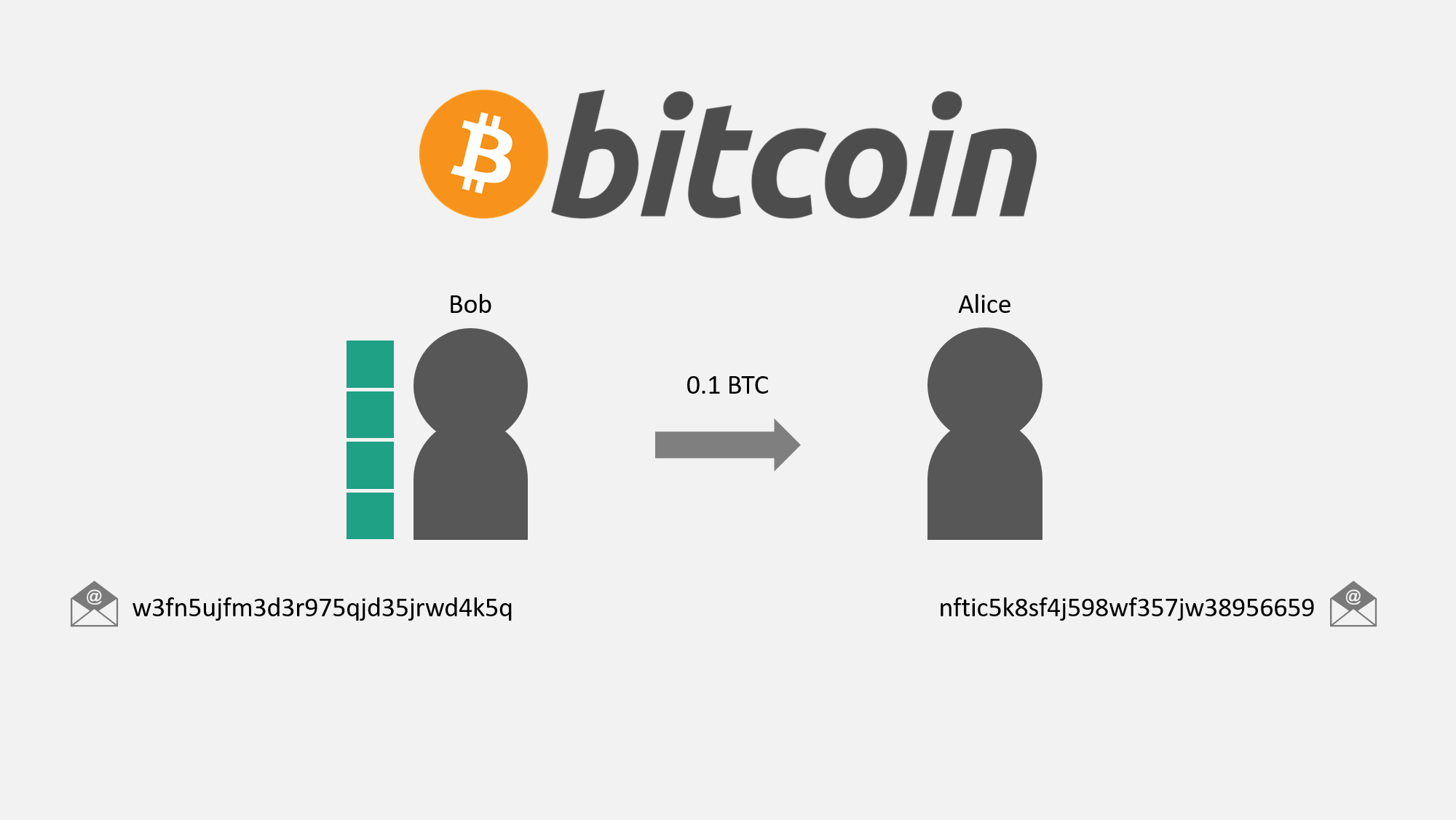

You can see how Alice now has control over this output. The information recorded in the blockchain simply states that Bob's address sent this output to Alice's address.
Bitcoin as a Private System
Many people may see the randomly-generated addresses and assume that since they are random, Bitcoin is private. They may claim that no one can see who the money belongs to and how it is being used. Unfortunately, this is not the case.
Addresses can be trivially liked together. There will be a permanent record of Bob sending money to Alice. Suppose Bob's address is hosted on a popular exchange compliant with local law, and suppose Alice later spends that money on a darknet market. Bob may be questioned about this transfer, since he has an association to how the money is spent in the future.
Similarly, suppose the money Alice receives from Bob was obtained from the WannaCry ransomware attack. Alice may be questioned, even if the transfer between these two people is completely legal.
Several companies exist whose entire purpose it is to track the transfer of funds between addresses on transparent blockchains. Below is a web provided by one of these companies, Elliptic.

Privacy Systems Added to Bitcoin Don't Really Work
Developers originally sought to add systems to Bitcoin that certain people can optionally use for privacy. The most commonly used of these is a mixer.
Mixing, whether used with a website or CoinJoin, works in the following way. Users send their Bitcoin to one of these mixers, who (as the name implies) mixes up whose Bitcoin is whose. They keep a fee, and send each participant a fraction of all the coins.
Ideally, this would provide some level of untraceability. The previous source of money is now unclear. No one should know how it was previously spent, or what source of funds is being spent in the future.
However, there are several shortcomings of this approach, and I argue that it does not provide a meaningful level of privacy.
Since this is an optional service that people need to go out of their way and pay additional fees to use, very few people actually mix their coins. Thus, the anonymity set is relatively small, and the few people who do actually draw attention to themselves. Mixing does not work very well if the majority of money is laundered or used on darknet markets. If the proportion of the total money supply used in mixing services is small, services could even block funds that have been mixed entirely. No knowledgeable person is going to pay extra money to mix new coinbase transactions, that's for sure.
Second, there is a level of trust in the system. Remember when I mentioned earlier that you do not need to trust miners on the network? Well, you need to trust these mixing services, even more decentralized ones like with CoinJoin or masternodes. These mixing services can retain a copy of how the funds were mixed without you even knowing. In many cases, this risk is exacerbated by how these mixers are hosted. The hosting providers can keep logs without even the owner knowing.
Recently, several researchers published a paper about BlockSci, a new system that can be used for analysis of transparent blockchains. They looked into the risk of the amount of money being used in a mixer being transparent, among other things. They found that for Dash (a cryptocurrency like Bitcoin with a CoinJoin-based mixing service), over half of their test mixed transactions could be traced back with absolute certainty by simply following the transaction amounts.
Finally, from a practicality perspective, mixing is inconvenient and can take a long time. If you attempt to mitigate the logging risk by chaining several mixing sessions together, this can take several days. Most people do not have the patience for this.
zk-SNARKs were more recently introduced, which function similarly to a mixer for coins but with very different underlying technology. I will discuss more about these new systems in a different post.
Introducing Monero
Monero takes a different approach. Instead of adding some service on top of a transparent one, Monero uses several privacy technologies at the protocol-level and makes use of these technologies mandatory. I'll explain all of these in further detail so that you can have a working understanding of all of them.
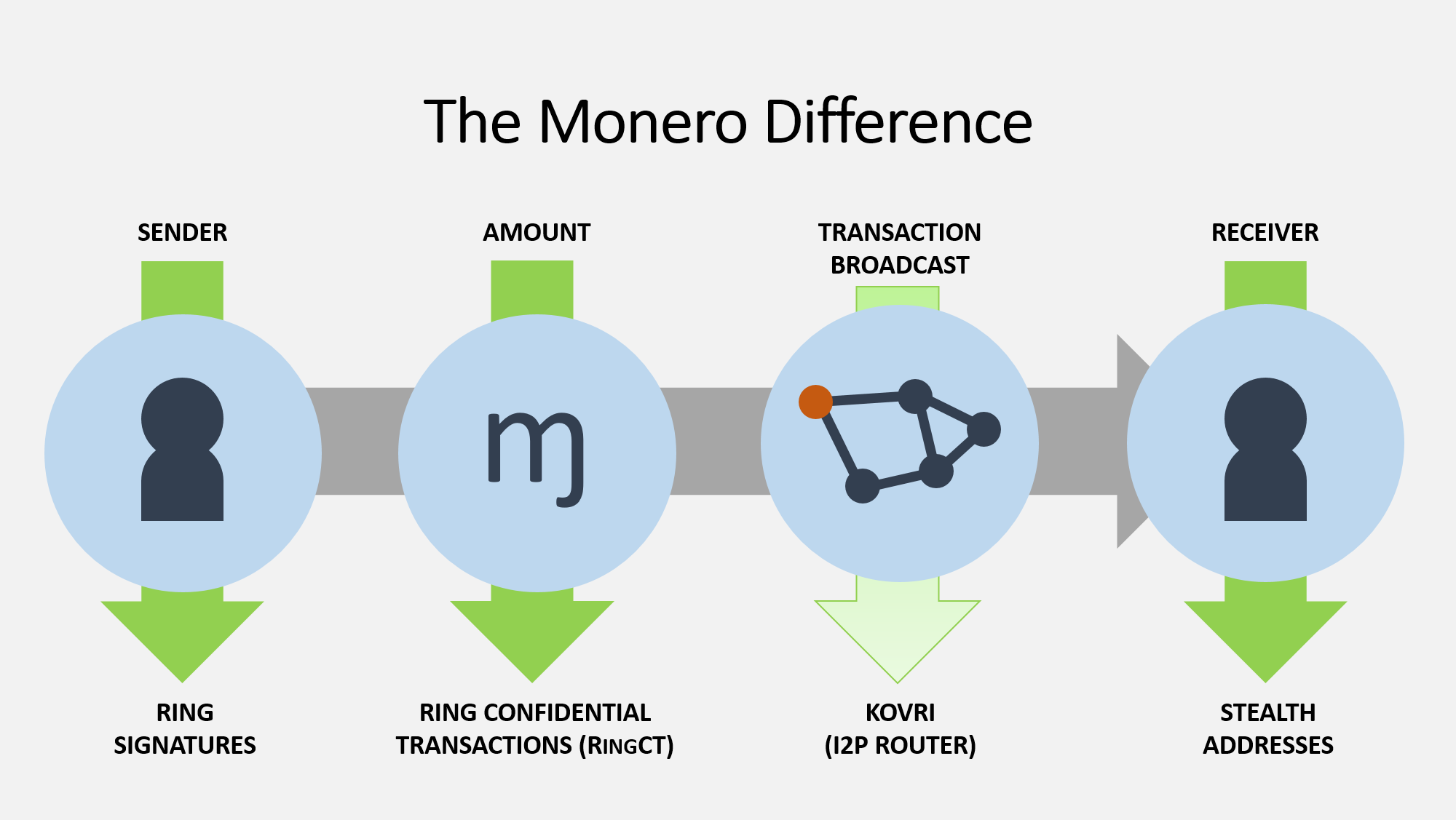
In the simplest sense, Monero hides the sender, amount, transaction broadcast, and receiver with ring signatures, RingCT, Kovri, and stealth addresses, respectively.
Let's start by taking a dive into ring signatures.
Ring Signatures and RingCT
Just as the US money supply is divided into different dollar bills and coins, the Monero money supply is divided into outputs. These outputs store a certain value of Monero each, and the value they hold can change over time. Suppose that in the picture below, these are all the outputs that exist, and the one you control and can spend is highlighted in red.
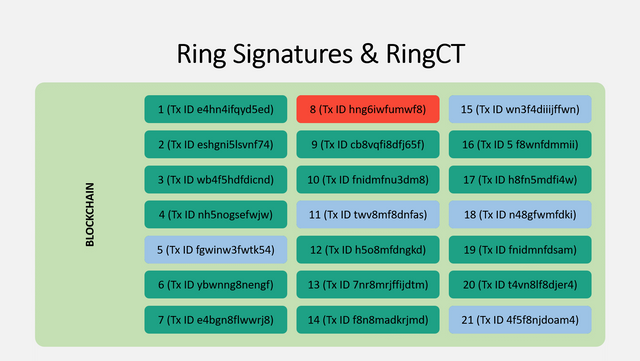
Keep in mind that unlike with Bitcoin, these outputs are NOT linked to addresses. I will speak more about why later.
When you create a Monero transaction, you will use a ring signature to hide which input is actually being spent. This is done by making it seem as if all of the chosen inputs are the possible real sender. In the photo, your real input is red, and five selected inputs are blue. These inputs can be controlled by anyone else, and you do not need their permission to add their input to the ring signature. Furthermore, this selection can be done entirely offline with only a copy of the blockchain. Without getting into the cryptography, you will sign all of these inputs such that an outside observer can not determine which is the real one being spent. Obviously, no one knows that yours is highlighted red :)
Now hang on, since I'm going to cover a lot of details at once. Once you have selected the other inputs, you need to finish creating the RingCT ring signature.
You sign it so it appears in such a way that all these inputs appear to be the real one used. This signature includes several other important elements.
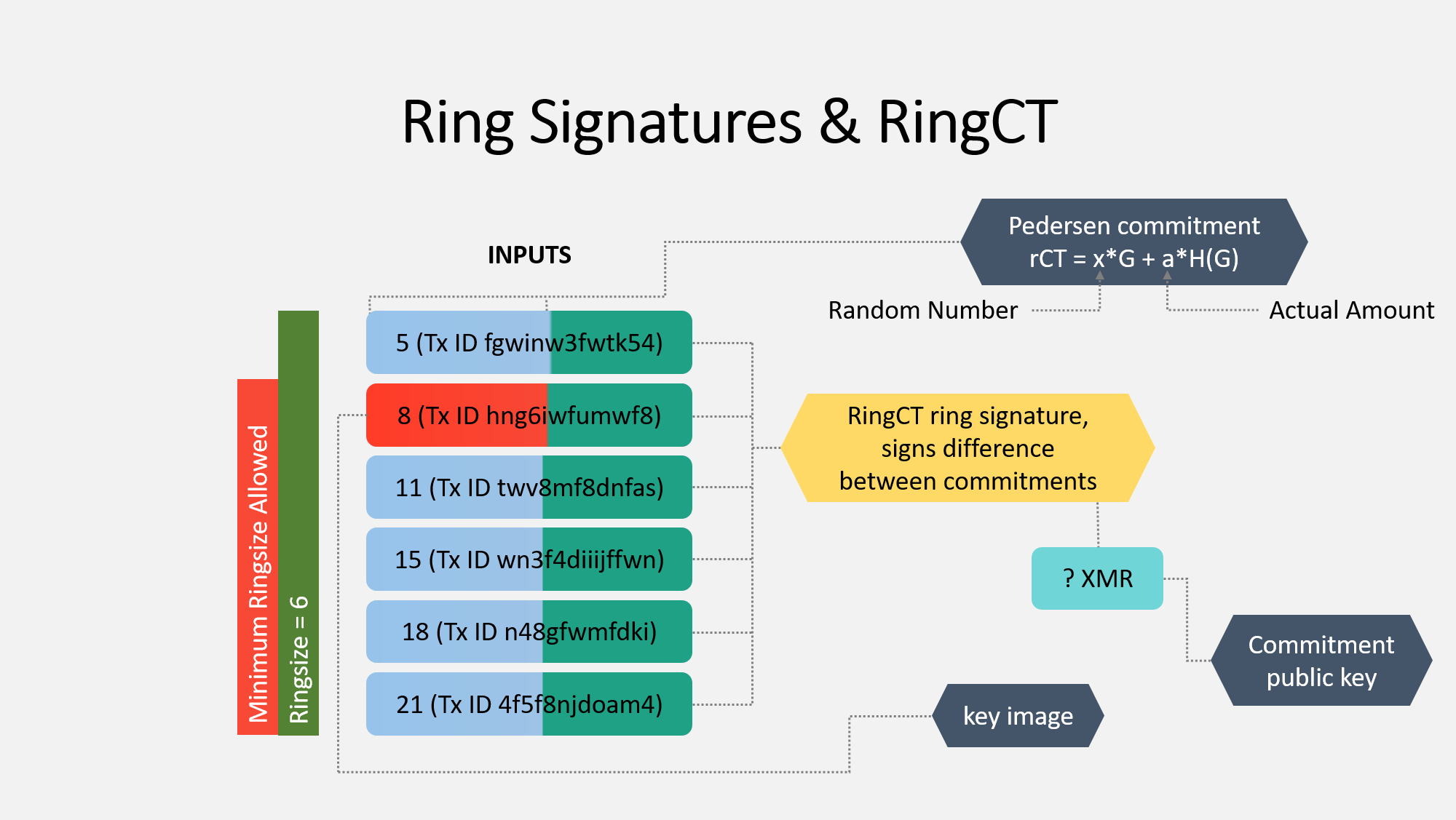
The key image is critically important. It's a one-way reference to the real input (the red one). This key image is given to the network as proof that the signature was created appropriately. The network verifies that this image has not been used before (to prevent double spends) and that it isn't a made-up number (to prevent people from spending money they never had). The network can verify this information without knowing which input is the real one.
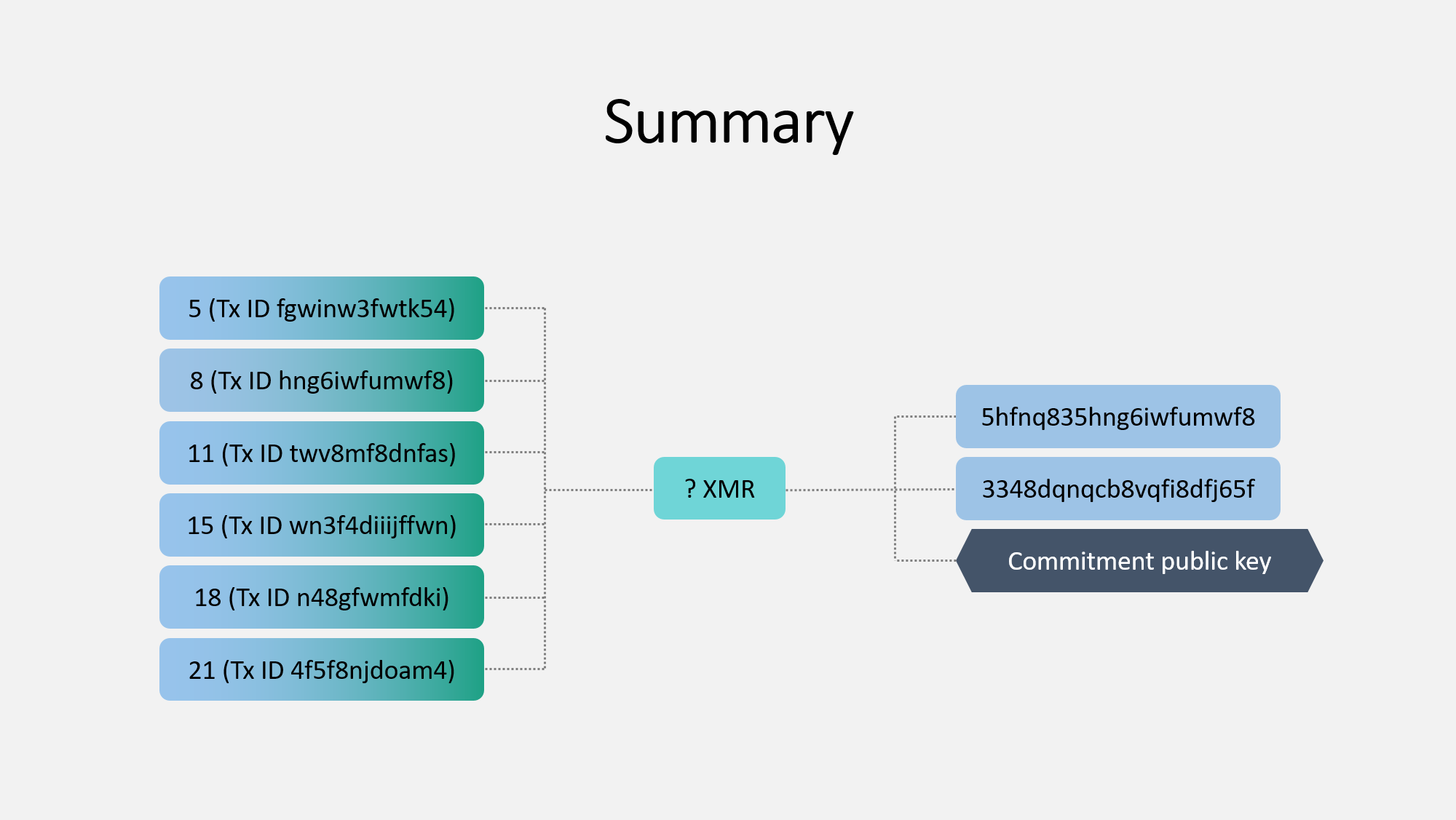
Next is the pedersen commitment. This is very complex, but let's take a very simple look at it. This is used to prevent other people from knowing how much is actually being spent. You can use this commitment to, er, commit to spending a certain value that you have the authority to spend, but other people no longer know what this value is.
This pedersen commitment is the critical component of ring confidential transactions, or RingCT. It hides the actual value a by adding a random number x. The commitment value is calculated for the set of inputs and outputs in the transaction, and it is broadcast to the network. Let me give you a simplified example:
Bob is sending Alice 1 XMR. Bob creates the commitment as follows:
Real amount (a): 1
Random number (x): 273
Commitment (given to network): 274
Bob's wallet will give this number (274) to the network. The network will verify the sum of the committed inputs and outputs are both 274. If they are different, the transaction is rejected.
Now, everything I explained earlier all comes together to form the RingCT ring signature. This results in an unknown amount of Moneor being spent. The commitment public key is what is used by the network to verify the commitment.
So how do outputs get used over time? Let's compare Bitcoin and Monero to find out.
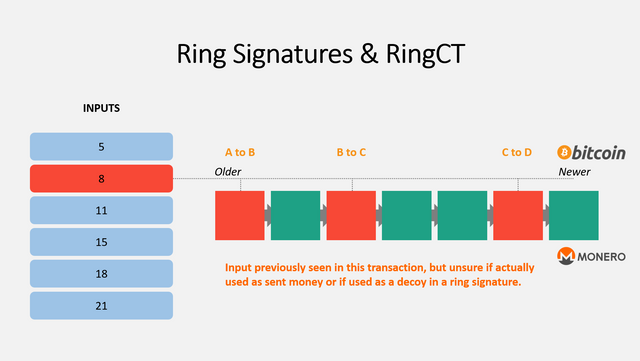
In the picture above, I have created a theoretical history for the output you control. All of the blocks highlighted red are ones where the output appears. If this was for Bitcoin, you would be able to easily tell that this output was transferred from user A to B to C, etc. However with Monero, this is not so simple.
There are three reasons for an output to show up in a block:
- It is new money and a coinbase transaction
- It was actually spent
- It was added as a decoy in a ring signature
Since there is no way to differentiate between case #2 and case #3, outside observers have no idea if an output is actually being spent, even though it appears on the blockchain several times. Since every transaction includes multiple decoys, it's more likely than not that the output is not actually spent despite appearing in a certain block.
And with that, we have completed the discussion on ring signatures and RingCT! takes a deep breath
If you want someone else to explain ring signatures and RingCT, see these excellent videos:
Ring signatures video
RingCT video
Kovri and Transaction Broadcast
There's a lot of misconception about what this means and what the impacts of this attack vectors are. I will create a future post clarifying these in further detail.
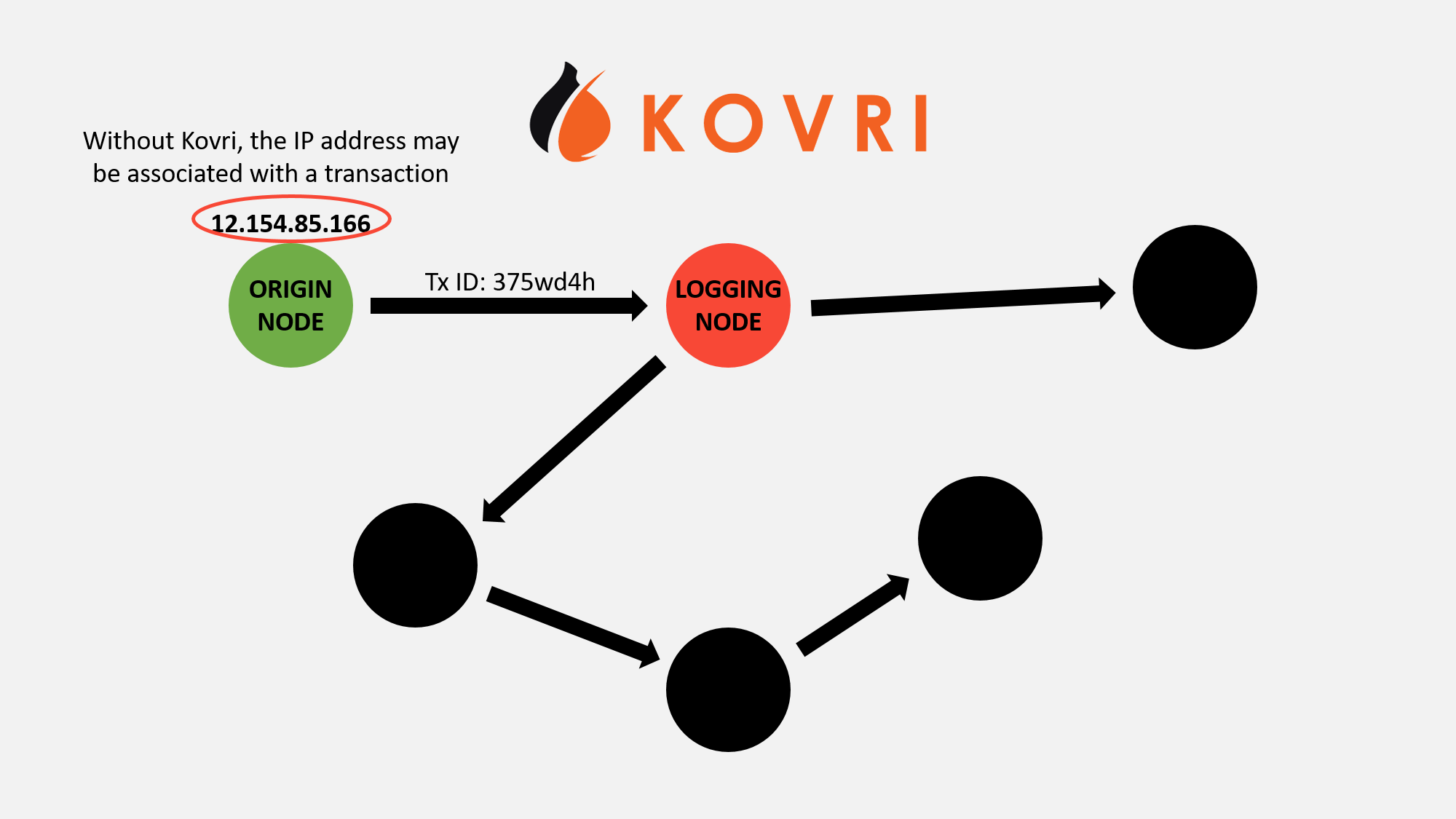
When you connect to the peer-to-peer network of nodes to broadcast your transaction, you leak some information about yourself. You leak your IP address and metadata (eg: date, time). Monero is working on a project to hide this information called Kovri.
Kovri is an anonymizing router. In the future, nodes will connect to each other through both the clearnet and through an anonymous network. There will be ways to run either entirely with clearnet or darknet, though few users should change this setting.
Kovri will prevent malicious nodes from rejecting transactions from certain IPs or from monitoring what IPs broadcast these transactions. Perhaps most exciting though is that Kovri works with any project that wants to incorporate it, including other cryptocurrencies. It would be relatively trivial for another coin to adopt it.
People can use Tor today to mitigate this risk, but they open themselves up to several other risks.
To be clear: this does not undermine the other features, and malicious nodes still do not know if the IP addresses they receive are the real ones. It may have been broadcast through a different node first. Given the high false positive rate and significant effort needed for an attacker to collect this data, the attack is already unlikely.
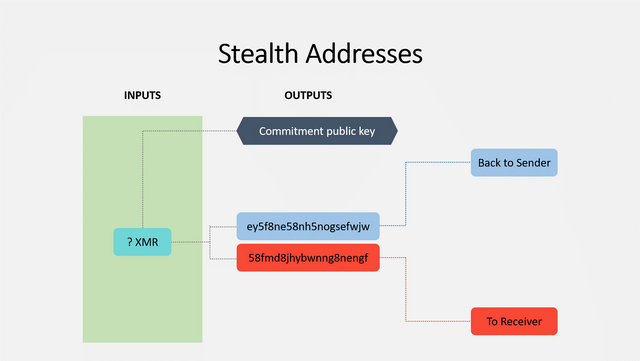
Stealth Addresses
Time to discuss how Monero breaks the connection between outputs and the addresses they belong to.
When you send money to someone with Bitcoin, you basically give it to them directly. You assign it to their public key (address), and they can use their private key to open it.
With Monero, things are a bit more complex. Each wallet has a pair of private keys and public keys. The cryptography is too complex to get in to here, but it basically functions like this: you create a one-time safety deposit box that only the receiver can open. It is never reused.
Receivers need to search every single one of these "boxes" to see which they are able to "unlock". They then have control over the ones assigned to them. They can take this money and place it into another "box" for someone else.
Suppose you have 10 XMR and want to send 1 XMR to me (thanks!); in this case, you will create two outputs: one for me with 1 XMR , and one for yourself with 9 XMR. You basically send the change back to yourself.
If you want someone else to explain stealth addresses, see this excellent video:
Technology Summary
As we went over, a Monero transaction has an ambiguous output origin, an unknown amount in a commitment, and an unknown receiver. For every transaction on the network, all of the information stored on the blockchain is obfuscated.
Some Other Items
Monero's primary focus is privacy, though there are still several other aspects that make it interesting. I have highlighted some of these below.
It has an aggressive upgrade schedule. The community does not shy away from hard forks, having three in 2017 alone. These are necessary to provide the highest level of security and privacy. Monero isn't perfect, though hard forks allow it to get better. RingCT was enabled through a hardfork at the beginning of 2017, for example.
It has a dynamic block size and dynamic fees. No Bitcoin block size debate. The number of transactions that can fit into a block will slowly increase if the demand is large enough, and it will decrease again if there is not enough demand. The fees will decrease based on transaction volume.
It has always-on privacy. I discussed this earlier, but I really want to emphasize it again. Few other coins that promise privacy can even get 10% of their transactions to use privacy features. With Monero, all of them use it, there is no way to opt out, and thus no transactions look suspicious for using privacy features.
It has view keys to provide transparency. With most coins claiming to provide privacy, the feature is either on or off for everyone in the world. With Monero, it's always on for everyone except those you allow to see certain transaction information. No matter what, information on the blockchain is obfuscated. However, you can provide a certain key to someone else so they can understand what is happening.
It has a critical community. Many people misinterpret this as harsh. While some users may be, the overwhelming message of most Monero community members has been to think critically of projects. Every Sunday, Monero users discuss the top criticisms of the coin in /r/Monero. The Monero community has a growth mindset, and is always looking for ways to improve.
It has a world-class research lab. Several researchers dedicate their time to research projects for Monero. You can learn more about these projects on the official Monero website.
It was launched fairly. There was no premine, instantmine, or ICO. There is no governing corporation or developer tax. Monero stands as a truly community-based entity.
It has a more accessible mining algorithm. Bitcoin can only be mined on specialized equipment. Monero's mining algorithm (CryptoNight) is memory-intensive, and the reward of developing specialized equipment is outweighed by the cost of developing it. You can still mine Monero on a CPU and make some money. Most people mine on GPUs. This allows even novice miners to meaningfully contribute to the network. There are arguments for and against this type of mining, but I believe it leads to decentralization.
Conclusion
That's about it! Thanks for making it all the way down here! If I piqued your interest, you can use the following links to learn more:
Monero website
Monero subreddit
Monero trading subreddit
Monero activist subreddit
Monero Twitter
Monero Facebook
Monero Github
Monero StackExchange
A list of Monero communication channels
Monero.how, a community-run site
About the Author
Justin Ehrenhofer is a junior at the University of Minnesota studying finance and management information systems. He is the co-president of a university cryptocurrency club called Crypto@UMN, with one of the largest active memberships in the world.
Crypto@UMN has three major focuses: education, advocacy, and community. His passion has been fostering these in the Monero community.
He studied abroad in Spring and Summer 2017 in Vienna, Austria. During his time in Europe, he traveled extensively, pairing his travels with discussions about Monero. You can see many of these presentations here. You can see more about his talks here.
He moderates the biweekly Monero community meetings, and he has started a new monthly Monero Coffee Chat initiative.
https://getkovri.org/ More info about kovri
https://github.com/monero-project/kovri For the devs who want to contribute to the project
Awesome sharing, brainstorming me from the basic.
I'm glad you like it!
You may like how I got started with monero
https://steemit.com/monero/@elliotyagami/how-i-got-started-with-mining-monero
Here's a step by step guide to setting up a wallet and buying Monero: https://buyingmonero.com/
The problem is to find a (fiat) bank accepting your trades with Cryptos. 2012 and even one year ago they laughed about dumbasses talking about BTC and LTC and so on .. now they found out its dangerous for them .. so how can someone buy and sell online without being registered with full name and address and bank account ?
This is one of the best Monero guide that I have ever read. Thanks for the info!
Monero for Beginners
https://www.tokens24.com/cryptopedia/monero-for-beginners/
Nice introduction... I have written a similar article on the same subject... with a list of the best 7 anonymous cryptocurrency