IoT Chain Technical Structure
Dear Community,
The Internet of Things (IOT) brings forth an irreversible wave of industrial revolution in our modern society. A new generation of high-performance IoT blockchain, ITC is the chain of all things, dedicated to providing a safe and scalable public IoT chain for the Internet of Things, supporting and promoting its development.
The IoT Chain main net is releasing soon. Let’s learn about the system architecture of the IoT Chain network.
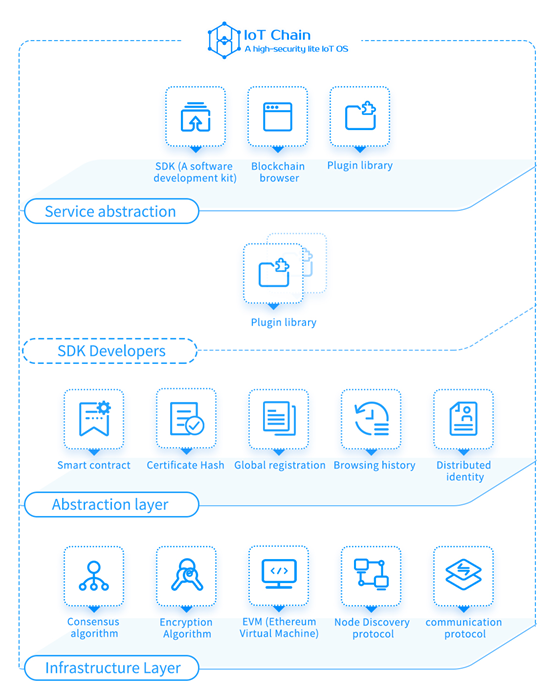
Infrastructure Layer
The underlying blockchain technology of the IoT Chain network, utilizing consensus algorithms, encryption algorithms, node protocols, network transport protocols, EVM, etc.
Abstraction Layer
The implementation of the blockchain system function of the IoT Chain network, utilizing smart contracts, hash functions, global registration, distributed identity, history browsing, etc.
Service Abstraction Layer:
For enterprise or stand-alone application developers, providing a variety of development components and services, including software development kit (SDK), blockchain browser, plug-in libraries and so on.
IoT Chain Technical Advantage
IoT Chain Using the BFT consensus algorithm
Maintaining the consistency of peers in the distributed network between transactions is the main problem faced by the blockchain consensus system. At present, the mainstream POW consensus algorithm faces performance limitations of insufficient scalability and a waste of computing power. IoT Chain satisfies BFT (Byzantine Fault Tolerance), meaning that if two-thirds of the nodes are trusted, it is impossible for a bad node to tamper with the transaction. This also helps to improve performance and is more suitable for high-frequency IoT applications.
IoT Chain using the Asymmetric Cryptographic Algorithm
If you are familiar with digital currency wallets, you may understand that a key pair comprises of a public key and a private key generated based on an asymmetric encryption algorithm (especially for private keys), operating as a digital signature and identity authentication in a blockchain network.
IoT Chain using the Kademlia
Kademlia (KAD) is a secure node protocol. Its advantage lies in the implementation of secure and efficient communication in distributed networks, helping nodes in the IoT Chain network discover and reach the target node faster and more accurately.
IoT Chain supports EVM
Supporting EVM (Ethereum Virtual Machine) is one of the IoT Chain’s network capabilities. This also means that Ethernet DAPP can be seamlessly migrated to the IoT Chain network.
P.S. For digital asset holders, in the ITC Wallet app you can freely manage your own ITC Main Ethereum Token and Ethereum ERC20 Token.