Crypto Academy / Season 3 / Week 8 - Homework Post for [@stream4u] - Let's Open The CryptoGraphy.
So hello everyone how are you all hope so everyone is well and good so friends i am back with my homework post for Professor @stream4u i will try my best to complete it in the best possible way.

Question 1:
Explain the Blockchain CryptoGraphy and mention few names which are the Blockchain Platforms ?
Answer 1:
Whenever we tend to learn about cryptocurrency the blockchain is the first word which comes up infront of us as blockchain is a series of database on which data is stored and whenever a new data is been added in the block it gets connected to the other one hence making it a break free chain.
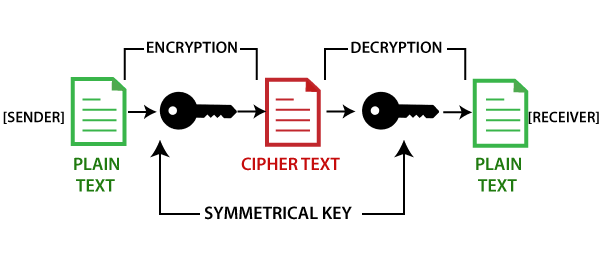
In the same way when we tend to make new algorithms and try to make the transaction secure so that only the person who is given the access can get the information is called cryptography. Usually end to end encryption and decryption is done so that the transaction get secured making it free from any third party intervention.
src
We all know that blockchain is known for its security as it is one of the most secure platform on which you can store your data and at the same time without revealing your identity as whatever transaction we do on the platform makes it non traceable and secure this was the main reason why cryptography was done.
Blockchain Platform:
There is a huge list of platforms which have integrated blockchain and are running on it with there own specific codes:
- Eos
- Wax
- Steem
and many more the list is never ending.
Question 2:
Explain the Public Key CryptoGraphy ?
Answer 2:
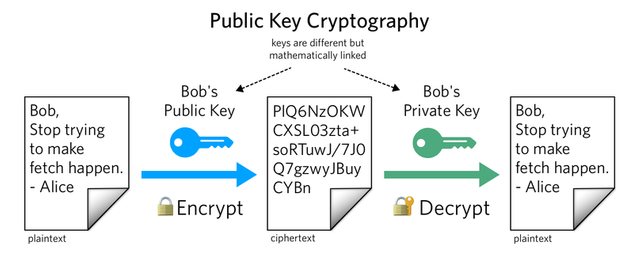
Public key is a key which is available for everyone and basically this key is assigned for making a identification of a wallet or address so that cryptocurrency can be transferred in those accounts.
For every public key there is a private key which is use to secure the address and account these key are with the person who is having the complete authority of that address and these are used to gain the full authority of the account.
src
From private key public key can be retrieved but the vice versa can not take place as it is a one way route not a two way making it a very secure algorithm on the blockchain for the safety purpose.
Public keys are made up of alphanumeric for a unique identification which is very necessary so that no repetition takes place.
Question 3:
Explain the Private Key CryptoGraphy?
Answer 3:
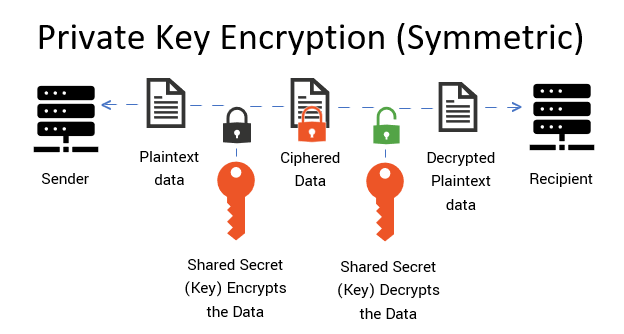
Private keys are also the alphanumeric codes which are assigned to every public address as they tend to give the complete authority of that address to the person holding it making it a very important key and it should be kept securely so that no loss of funds can take place.
src
Basically every address has this private key and any one having this key can access all your funds so it is better said to keep it securely so that only the true owner can have the information regarding it.
Question 4:
Explain the Digital Signatures CryptoGraphy and what is Singing Of Transaction/Message?
Answer 4:
Digital signature is just an replica of real life signature which we do in our daily lifestyle. Though digital signature are just done to show the validation and authentication of transactions and information as without it there is no other way to know the genuineness of the transaction and information so it is really very important.
The digital signature which we perform are unique and can only done by the person in authority to it or someone who is having the private key of it for validation purposes.
Real life use of signature and the one done digitally are similar but still differs in lots of ways as the chances of getting your digital signature hacked are very high still it is not that easy but yes the chances are always there.
Signing of Transaction:
Whenever a person wish to sign any transaction or message he just have to authorise it with the private key which is been assigned to him and the transaction will be signed making it a sign of validation.
As said earlier anyone with the authority or the private key can sign it for validating it and approving it.
Question 5:
Explain what is Symmetric and Asymmetric cryptography?
Answer 5:
No matter what in this crypto world we all are very keen to save our privacy and identity as these are the primary focus of almost everyone so different types of methods are security features are been developed in order to protect the user information and identity and for that most popularly symmetric and asymmetric cryptography methods are used they both have there own set of advantages and disadvantages based on which people generally use them as per there needs.
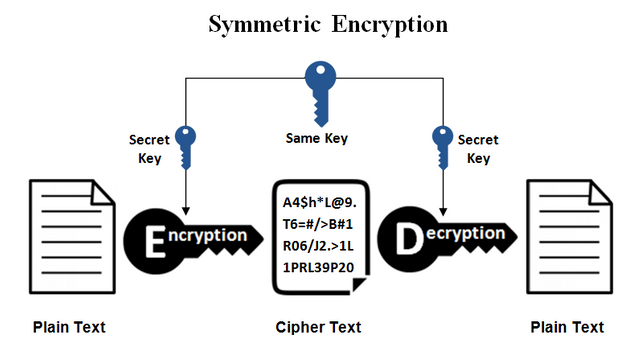
Symmetric Cryptography:
When a single key is been used for the encryption and decryption process then it is called symmetric Cryptography. This is really very secure as without decryption it is not at all possible to get the access also the implementation is very easy which is a very big advantage for it. We can also say that the process of Cryptography through this process is really very fast and smooth.
src
Though this system is safe but we can't completely rely on it as there are many flaws to making it prone to decryption of data and after it is done the data can be accessed.
Asymmetric Cryptography:
When two keys are used one at the time of encryption and one at the time of decryption then it is called asymmetric cryptography. Rhe key which gets used at the time of encryption is known as public key and when that message get decrypted then that key is called private key which is an important key as with the help of it only the receiver can encode the data which is been sent by the sender.
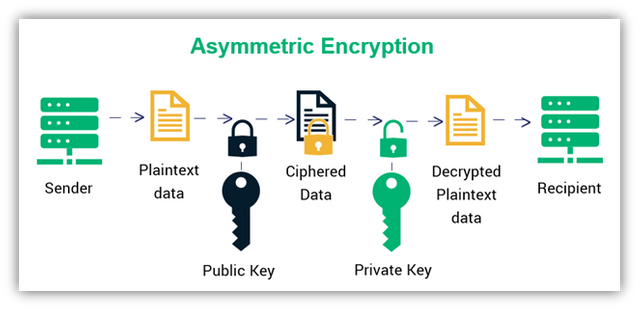
src
This type of encryption are basically more secure then the previous one but as said no system in this world is full proff so even it has its own flaws but in comparison to the previous one it has an outer edge over it.
As it's security is high making it a bit slow as compared to symmetric cryptography apart from it is very reliable and great.
Question 6:
How Blockchain Wallets CryptoGraphy works and explains the available types of Crypto Wallets.
Answer 6:
Blockchain wallets are just like any conventional wallet where we can store our cryptocurrency and keep it safely there. Every wallet is assigned with a specific address which is a alphanumeric and with set length making it a user specific address in which we can accept our cryptocurrency from other users.
The authority of our wallets get's proven by the private key which we get and with the help of those keys we can access our wallet and perform all kinds of functions such as transfer of funds checking of account etc.
In many case there is no chace of recovering of your private key so one need to be very careful while dealing with these as once you forgot your password then there is no turning back and all your funds get's lost as no one can access it.
Types of Crypto Wallet:
In general there are 3 types of wallets:
- Hardware Wallet
- Software Wallet
- Paper Wallet
Hardware Wallet: These are the wallets which are in the ofline mode and can be accessed through the password assigned to it as they are in the form of specific device which is needed to be connected to the computer in order to access it so it gets completely secured as in ofline mode it can never get hacked still it might get stolen but not hacked for sure.
There are many types of hardware wallets in the market such as ledger wallet which are one of the Industry leaders.
Software Wallets:: These are the wallets which can installed in the form of software in your desktop or in mobile phone in the form of apps and can be used in the online mode as they are softwares so the data is been protected by the software company and the data remains online which makes it prone to Hacking very easily.
Paper Wallets: Paper Wallets are just like any other wallet which is available online and in this case there is no need of installation of any software or hardware making it one of the most easiest wallet to use.
Though these are very simple onces but it is not suggested to be used for bigger transaction due to its own limitations still for trail purpose and for person making small transaction it can be a great wallet.
Question 7:
What is the Merkle trees and What its importance in blockchain?
Answer 7:
Merkle tree plays are very important role in blockchain as the it uses the cryptography function to convert the raw data into hash and store it for further use. Most popularly it is called hash tree as it saves the data in terms of hash which is the main reason why it is called hash tree.
It was invented by Ralph Merkle in the year 1979 and it was named after him it was invented by him just because of the complexity of the transaction validation which use to take place and to solve this he made this system which stores hash and later can be validated easily.
As the name suggests it is just like a tree with branches and leaves the top portion of the Merkle Tree is called root hash which get formulated with the pair of hash coming from the lower branch. Root part contains hash which are very easy to store.
By following it the cost effectiveness and time saving is something which we can see making it very viable for us to use.
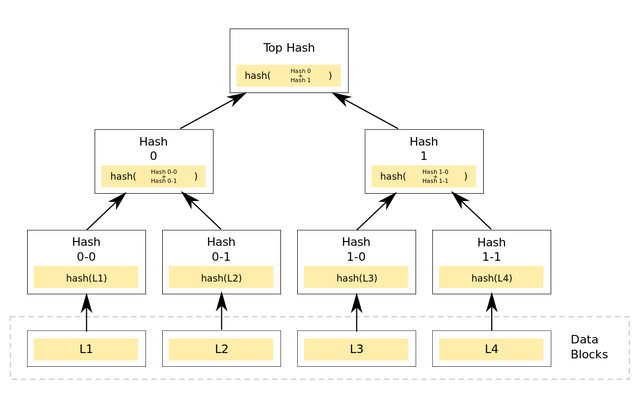
src
This is the basic diagram through which we can understand the Merkle Tree. The lowermost layer of blocks are termed as leafs and further going up they make the branches in pair and further it gets to the top part called root.
Importance of Merkle Tree:
- It saves a lots of time as before the validation use to take a lot of time but now it takes a very less time.
- The storage data was also consumed high but after the Merkle Tree it also falled drastically making more space.
- No alteration is possible in the data stored in the hash making it tampering proff.
Question 8:
Practical + Theory, do some practical research, study on Blockchain Demo: Public / Private Keys & Signing and then explain the functionality of Key, Signature, Transaction, Blockchain with proper screenshots of yours practical.
Answer 8:
After you go to the website you will first see a randomly generated private and public key.
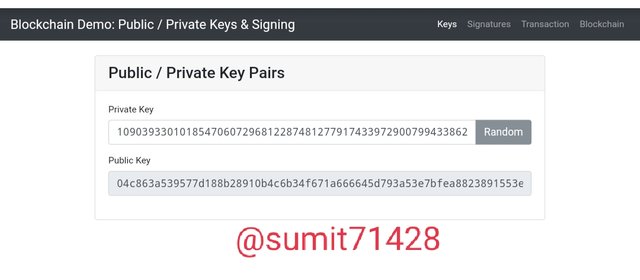
The private key is: 109039330101854706072968122874812779174339729007994338622894632845335971477457
The public key is: 04c863a539577d188b28910b4c6b34f671a666645d793a53e7bfea8823891553e179e2d828eb3296d0cd9294b14f16452c9863a68e8174572852e531876a152569
As far as first theory is concerned so when we change the private key it automatically changes the public key so let us confirm that by changing the private key.
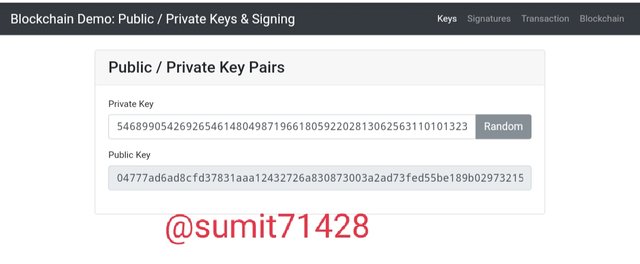
So you can see that when we change the private key the public key also gets changed.
New private key: 54689905426926546148049871966180592202813062563110101323049876189650233626563
New public key: 04777ad6ad8cfd37831aaa12432726a830873003a2ad73fed55be189b02973215f76a605ab7f7e8dead2f0177c6af10c7bcb6575b3ac3b0ee990f652818e304a31
From this we can also state that the two private keys can't be same as private and public key goes on pair and no private or public key can have 2 keys.
Using Signature:
Signature can be used but only with the help of private key so i will use it and try to sign this transaction by Crypto Academy.
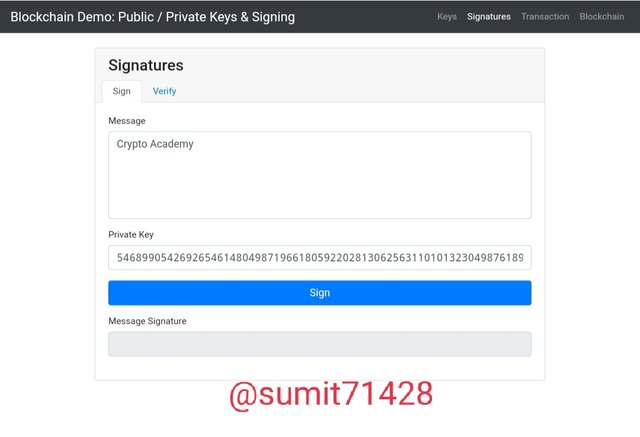
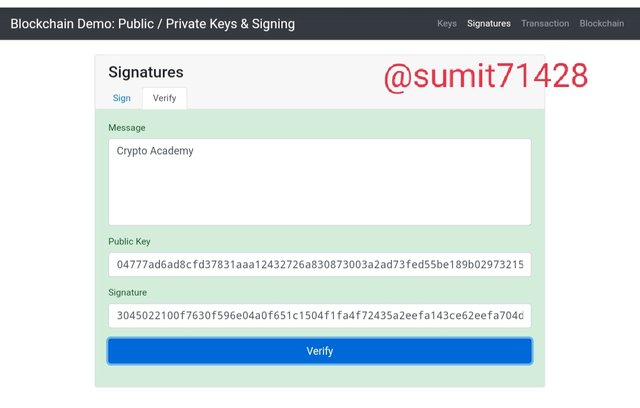
After signing the transaction you can verify it and for verification purpose you need to put your public key and once it is put you can see the page turning green in border which is the indication of message being verified.
Transactions:
For making an transaction you need 3 things one is your private key which will be use to validate your transaction second your public key from which the transaction will be made and third the public key of the user you want to send.
From public key: 04777ad6ad8cfd37831aaa12432726a830873003a2ad73fed55be189b02973215f76a605ab7f7e8dead2f0177c6af10c7bcb6575b3ac3b0ee990f652818e304a31
To public key: 04cc955bf8e359cc7ebbb66f4c2dc616a93e8ba08e93d27996e20299ba92cba9cbd73c2ff46ed27a3727ba09486ba32b5ac35dd20c0adec020536996ca4d9f3d74
I used the amount 20$ for this transaction and now i will sign it with the help of my private key.
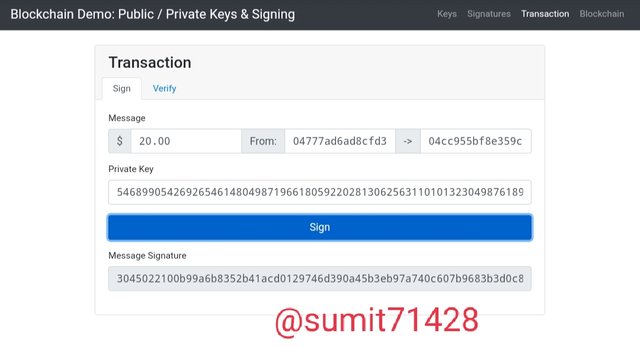
After signing the transaction i got this message signature: 3045022100b99a6b8352b41acd0129746d390a45b3eb97a740c607b9683b3d0c8bf334a6af022035374359f9286c9b86cd450f6d96500c01a5103b716314dc3a1ec4886bcb710f
You can easily verify your transaction by entering the signature message and after nthe border turn out the green which means the transaction have successfully taken place.
Blockchain
As all the transaction are stored in the blockchain in terms of hash so we can verify it and check weather the transaction has been validated or not.
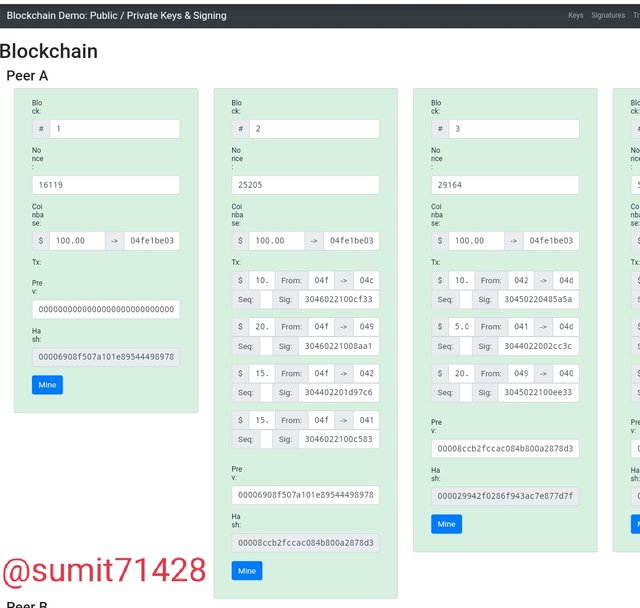
So as you can check that the borders are green which means that the transaction has been validated and updated on the server.
Now i will try to change the value of block and see what happens.
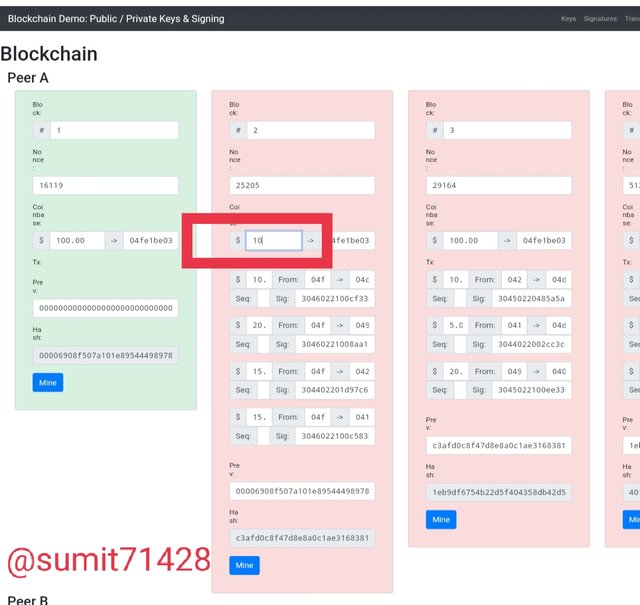
You can see that the blocks have turn out to be red indicating that the transaction has not been validated.
So by this we come to the end of the homework been assigned by professor @stream4u
Conclusion
Blockchain Cryptography was completely a new concept for me and i am really thankful to professor @stream4u for making it a fun excercise and learning. From my experience the cryptography is really very important as it helps to blockchain safety in many ways.
Also i have got to know about the limitations with the different wallet and it's advantages and i personally will suggest to use the hardware wallet making it the secure among all.
Overall it has been a great experience learning and doing this homework i really enjoyed it a lot.
Thanks friends have a great day ahead.
Respected Sir, please verify my achievement 1 introduction post
https://steemit.com/hive-172186/@mehvishh/achievement-1-introduction-post-by-mehvishh