Crypto Academy | Season 3 - Week 8 | Homework Post for professor @ stream4u | Let's Open The CryptoGraphy | By @ladyofpolicy

Question no. 1
Explain the Blockchain CryptoGraphy and mention few names which are the Blockchain Platforms (Few names of the Blockchain Platforms)?
CRYPTOGRAPHY
In order to maintain the confidentiality of information from one party to another without any interference whatsoever the concept of Cryptography was introduced, to protect an encoded information which can be in form of a message or fund until it gets to the desired destination.
By now you will be asking yourself how does this happen. Very well, for an information to be received there must be a sender somewhere who is able to encrypt/encode these information so that the receiver will be able to decode them. Not that information can be sent through other means, but we are much concerned about the security of these information which other platforms lacks , which is why Crytography involves the use of different keys and addresses which I will explain in a short while to ensure security,storage, effective delivery and access to these informations and fund has been encoded
Blockchain Keys CryptoGraphy
As i mentioned earlier, in order to ensure the security of information stored or to be delivered, Crytography uses two important keys are as follows
PRIVATE KEYS
This defines the the owner of a wallet and allows him to gain access to his wallet and transfer fund/information.
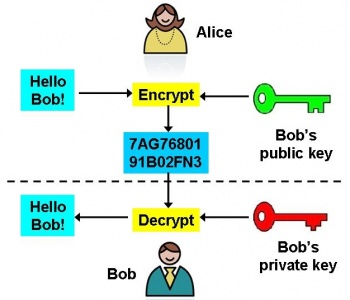
PUBLIC KEYS
This key is generated by someone who has a private key in order for his information to be encoded by the receiver, this ensure that only the receiver with the key can be able to acccess the encoded/encrypted information
(picture)
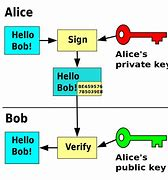
lDigital Signature
This acts like a means to verify that a transaction/information was sent by the owner of a private key, this is meant for security purpose
E.g Lets say you want to send a coin to someone from Binance and you request for a withdrawal using your Private Key, Binance will send a verification code to you which is always unique to each transaction, if you happens to be the owner (private key owner) of the Binance account, the code being sent to you now acts as a Digital Signature in order to verify the transaction using the Public key generated from the Private key
How Blockchain Wallets CryptoGraphy and what is Signing Of Transaction
Now when it comes to wallet CryptoGraphy, we are much concerned about how funds are kept save in an owners wallet, how this funds can be moved from wallet to another without any interception.
To secure funds in a wallet we need keys, these are the Private and Public keys just as we have keys to secure our houses from invaders and also enable us get access into our houses whenever we want to and to be able to take things out, so also is these keys.
The Private Keys acts as a lock to secure a particular wallet and enables the owner to gain access to his/her wallet anytime, but how can these funds be transferred from an owners wallet to another without disclosure of any information whatsoever of the receiver and also to prevent the interception of these funds before it gets to the receiver, this brings us to the concept of Wallet address, which is made up of combinations of many digits and numbers. that's a crazy combination, so by using this wallet address one can transfer fund, without disclosure of the receiver information, this is so delicate and should be scrutinized before any transaction is made as this can lead to loss of fund if sent to the wrong address as the receiver can't be detected, this is the only shortcoming in have noticed when it comes to wallet Cryptograph
I know by now you will be wondering of what use is the Public keys, if there is a Private key. This acts as another source of security to a particular wallet
SOURCE
This involves the use of a Private Key to sign a particular transaction/message in order to generate the Transaction Signature.
EXPLAIN SYMMETRIC AND ASYMMETRIC CRYPTOGRAPHY
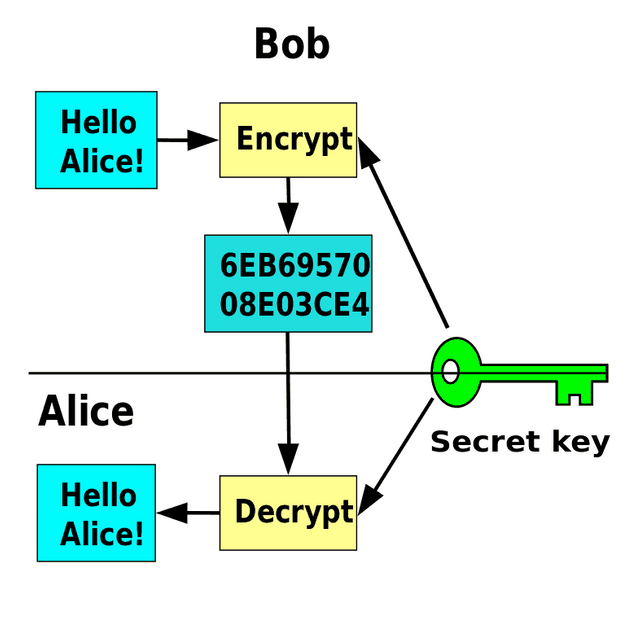
SYMMETRIC CRYTOGRAPHY.
SOURCE
Here the private key is used to encrypt and decrypt transaction/message. This information cannot be accessed by another person except the one in possession of the key.
ASSYMETRIC CRYTOGRAPHY
This can also be called Public -Key Cryptography, here anyone can encode/encrypt a information using a Public key, but this information can only be decrypted using a Private key. This can be of disadvantage due to insufficiency of assymetric key algorithm
Merkle Tree CryptoGraphy
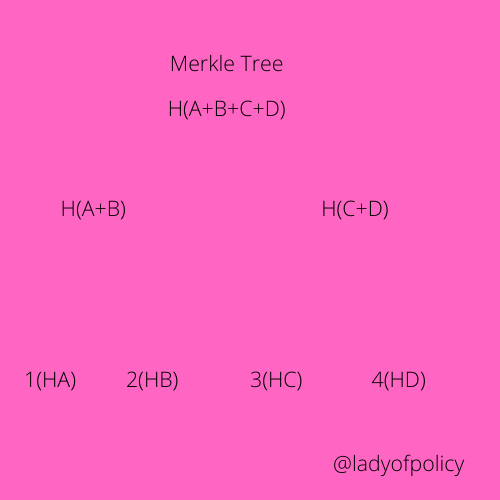
When we talk about the Merkle tree, we tend to see it as the fundamentals of part of Blockchain technology, which is very useful as it helps to provides in a very detailed way transactions in each block, this enables effective verification of transactions/message in a more simplified way without having to go through a complex of data
How It Works?
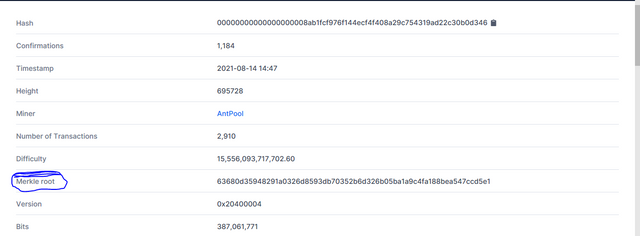
Since it records all transaction in a simplified way in blocks, it keeps on calculating the hashing to the very last one also known as the Merkle Root, this can be read from top to bottom
Looking at the diagram above 1,2,3,4 are the transaction with their Hash value A,B,C,D.
The first two hash value will give A, B and then the last two will give C,D
When the transaction is hashed for the last time we would get the Merkle Root which will be ABCD
With the help of Merkle tree transactions are now processed in a more effective and efficient way.
PRACTICAL
Visual Demo to understand #the functionality of Keys And Transction CryptoGraphy
In order to understand how this Keys , Transaction, Signature and Blockchain works am going to use a Demo to explain visually
Blockchain Demo: Public /Private Keys and Signing
#KEY'S
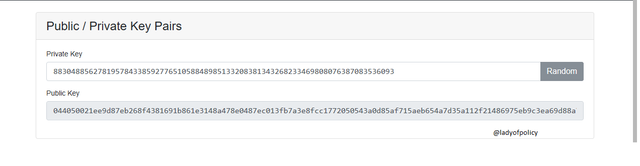
Looking at the screenshot above, we can see a Private key and a public key, this public key is linked to the private Key, Since the Private keys is so important to us and must not be disclosed, so the random bar by thee side of the Private key when pressed provides us with a random number for the Private key . So when one of the random numbers for the Private keys are entered it provides a public key linked to this Private Key
Lets enter 2 as the Private key, you will notice that it generated a public key linked to this Private key
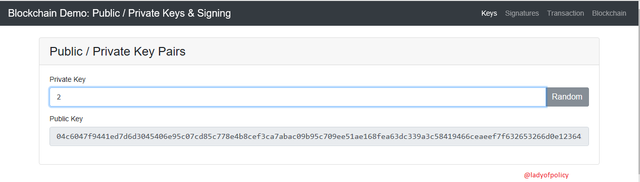
Public Key:
04c6047f9441ed7d6d3045406e95c07cd85c778e4b8cef3ca7abac09b95c709ee51ae168fea63dc339a3c58419466ceaeef7f632653266d0e1236431a950cfe52a
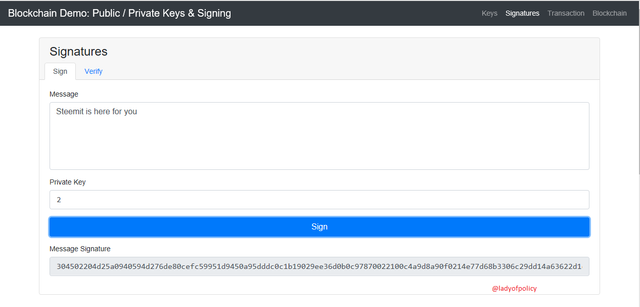
As we can see above we need a message/Transaction and a private key in order to sign this transaction, Remember our Private Key is Still 2, lets now put ''Steemit is here for you'' as our message, after that we click the sign button.
A transaction signature will be generated immediately, this will enable us to verify the transaction. So what we need here in order to sign this transaction are,
1.Message/Transaction
2.Private Key.
Now lets go to the verification, in order to verify this transaction, we need
1.The Transaction/Message
2.The Public Keys( which i made use of the sender's key)
3.The Transaction Signature

Cryptography in summary helps to provide security, storage, effective delivery of transaction/ message and i believe this is what the world needs at the moment.