The Steemit Crypto Academy Week 5: Task @gbenga - A post about a Security problem with Cryptocurrency//By @graciee20
Hello Steemians, I'm so delighted to participate in this week 5 Crypto Academy. This week's lesson given by professor @gbenga is titled Blockchain security. It is indeed a very insightful lecture and I really want to appreciate our Professors; @gbenga, @besticofinder, @steam4u, @yohan2on and @sapwood for taking out there time to put all of these piece together. After going through the lectures and making further research on Blockchain security, here's my week 5 homework task.
INTRODUCTION
A cryptocurrency is a virtual or digital financial asset designed to work as a medium of exchange that uses cryptography to secure its transactions, to control the creation of additional units, and to verify the transfer of assets.
 image source
image source
Many Cryptocurrencies are decentralized network based on blockchain technology. One of the basic feature of cryptocurrencies is that they are generally not issued by any central authority, rendering them theoretically immune to government interference or manipulation. Virtual financial assets faces some serious security concerns and risks, such as the safety of wallets, double-spending, growing vulnerability to orchestrated attacks on Cryptocurrency exchanges, and fears of rogue miners engaging in selfish mining.
 image source
image source
These concerns can be very destructive towards Cryptocurrency. So I'm going to be showing you one security problem with Cryptocurrency (Eclipse Attack) and it's preventive measures.
 image source
image source
Please read on!
ECLIPSE ATTACK
The eclipse attack is a security problem in the World of Cryptocurrencies. This consists of isolating and eclipsing the victim's network connection by flooding them with false data about the blockchain network of which they are part of. It disconnects the victim from the valid data flow from the network thereby making the the victim to receive manipulated data from the attacker.
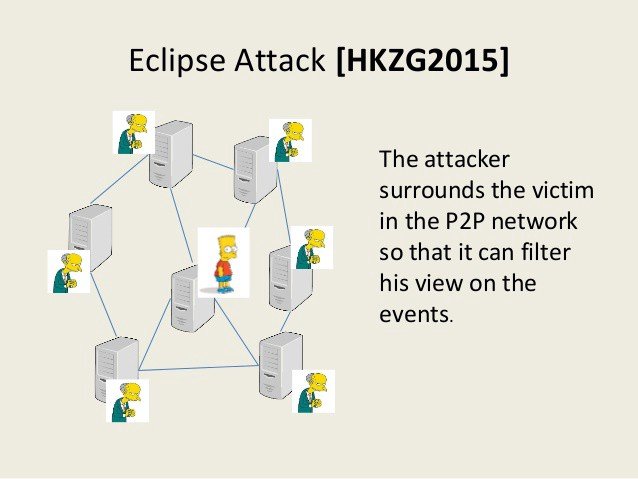 image source
image source
This attacks is possible because of the structure and limitations of peer-to-peer networks (P2P) communication protocol that a blockchain uses.
 image source
image source
 image source
image source
CONSEQUENCES OF ECLIPSE ATTACKS
➡️ It performs block racing engineering: This type of attack is performed on networks using the proof of work protocol (PoW). For instance, if two miners discover a block simultaneously, an attacker could use an eclipse attack for eclipsed miners to waste mining effort on orphan blocks. This will make the attacker to mine his own blocks and ensures his blocks are processed by the network under his control, then receives the reward. He can also divide the mining power of the network, thereby facilitating the launch of a 51%attack to help you rewrite the blockchain or ledger. This type of attack also opens up the possibility of attacks by double spending confirmation N. This means that an attacker can control a certain group of miners and from there report that the transaction has received a number of confirmations.
 image source
image source
➡️It exploits connections to control the networks: Here, a malicious attacker takes control of the network and keeps increasing the control, because the more he has a new node under his control, the more his presence on the network increases with ease. Node management helps attackers to manipulate the growth of the network by altering the blockchain ledger versions as they please.
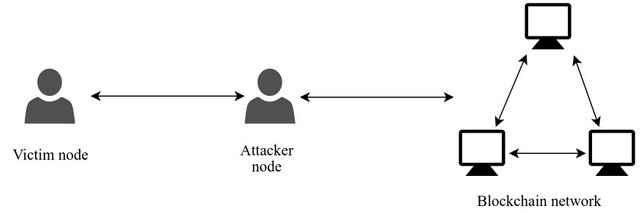 image source
image source
➡️It gives rise to new and more dangerous attack vectors: The Eclipse Attack is the source of more dangerous and far-reaching type of Attack (the Erebus Attack). This attack has the ability to execute a large scale Eclipse Attack on the network and this can lead to partitioning. Anyone who performs the Erebus Attack has the ability to split the network and manage it as they wish and also do a Daniel of Service (DoS), perform a 51% Attack or even create a blockchain hard fork.
➡️ Another consequence of Eclipse Attack is that of making an Attack on second layer protocols ( making vulnerable to protocols such as lightning network, OmniLayer o RSK in Bitcoin or even to creations derived from smart contracts like all those executed on Ethereum, EOS o TRON). All of this can hay because an Eclipse Attacker would trick his victim into seeing an unreal state of the network. For instance, a lightning payment channel would show as 'open' to the victim while the attacker has closed the channel, taking the funds with them. In the case of smart contracts, users will see inconsistent states of the blockchain.
HOW TO PREVENT ECLIPSE ATTACKS ON BLOCKCHAIN NETWORKS
Series of measures has been implemented to avoid these attacks and some of these measures are still on implementation process with some improvements. They are:
➡️To avoid eclipse attack, have a reliable peer selection process for the network. Another important point to avoid eclipse attacks is to have a reliable peer selection process for the network. For example in Ethereum this process uses a protocol based on Kademlia. This allows Ethereum to have each element associated with a key and is stored only in those pairs whose node ID is "close" to its associated key. This "closeness" is defined as the binary Hamming distance between the key and the node ID. In this way, the network ensures that it has a series of well-identified and related nodes.
➡️ The Peers in the network should have a unique and unrepeatedly identification system.
➡️ Incoming and outgoing connections should be properly controlled. With this, communication limits are established with the nodes of the network so that in the event of an attack on a node, it cannot affect a large part of the network.
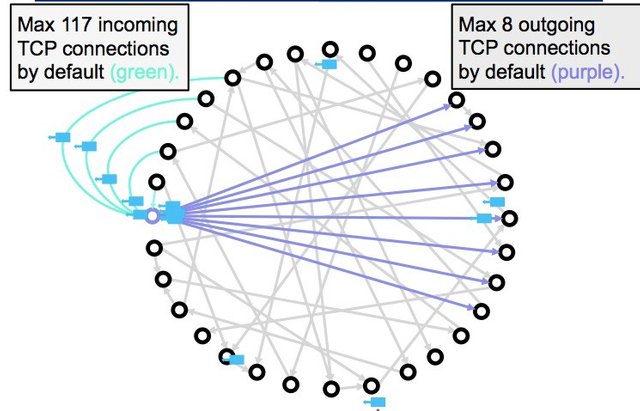 image source
image source
CONCLUSION
The best ways to secure your Cryptocurrency account from Eclipse Attackers by shielding your nodes if you have one, be sure to use a payment system and wallets with good reputation, by keeping your wallets and nodes updated, avoid accepting 0-Conf payments or without without confirmations and but not the least, always review your node or wallet connections periodically and learn to create a list of trusted nodes for you to use at all times.
I'm new here and in the crypto World, I don't have a personal experience to share, but I believe I've done justice to this homework task and with time, I'll be used to everything happening in the Cryptocurrency World.
Sir, @gbenga,
here is my homework submission post entry.
If you missed this lecture from @gbenga, I'd encourage you to check it here
Best regards
Cc: @steemcurator01
Cc: @steemcurator02
Cc: @stephenkendal
Cc: @trafalga
Cc: @gbenga
Hello @graciee20, copy and paste isn't welcomed in this community and on steemit generally. Copying any part or all of a post is referred to as plagiarism and it makes steemit look like the dumping ground.
Your Post
Original content
Source: https://academy.bit2me.com/en/what-is-eclipse-attack-eclipse-attack/
profe @gbenga veo que mi tarea se le perdio
https://steemit.com/hive-108451/@risedaniel/publicacion-de-tarea-de-la-semana-5-de-cryptoacademy-para-gbenga-hakeo-de-criptomondas
puede revisarla porfavor?
Profesor @gbenga e visto que no ha evaluado mi tarea https://steemit.com/hive-108451/@shoday/publicacion-de-tarea-de-la-semana-4-de-crypto-academy-para-gbenga-uniswap porfavor puede dale un vistazo.
Well written @graciee20. I wish you success at your homework. Have a splendid day.
Thank you @onos-steve