Crypto Academy / Season 3 / Week 8 - Homework Post for [@stream4u] Let's Open The CryptoGraphy.
It is always an honor to be able to participate, and this time it will not be the exception, that is why we are all going to learn together !! ☺️🙌


1) Explain Blockchain CryptoGraphy and mention some names that are Blockchain platforms.
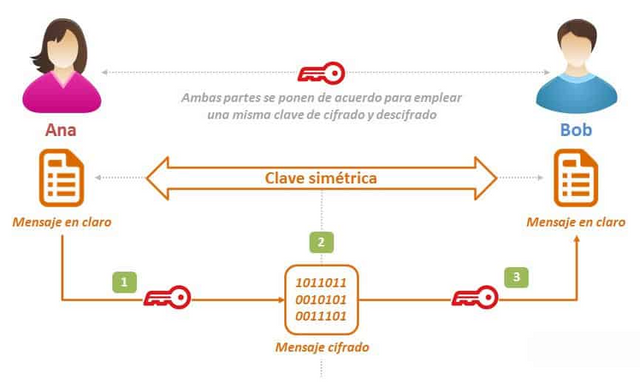
Cryptography has been part of humanity for millennia years, in fact in many distant wars they used this method to communicate and transmit very private messages. That is why when blockchain technology emerged, it was not left behind, but rather joined to be implemented with the decentralized system that characterizes the network, this in order to grant users a higher level of privacy and security.
Blockchain cryptography is ideal so that privacy attacks such as the one the teacher explained to us in class do not occur, we could see how the email sent by Mr. Warren in the past was exposed by the entities centrals that supported said platform. That is why cryptography comes together in the world of blockchain in order to provide users with the assurance that the information they send to another person is kept completely secure without fear of interception by both parties.
We will ask ourselves, How is it possible that this happens? It is simply very easy, since cryptography is in charge of transforming said information into a series of algorithms that only both parties can understand, with the advantage that this information cannot be changed or altered and then be disseminated elsewhere. This is one of the great benefits of blockchain, since thanks to the implementation of cryptography data and information can be protected without the fear of putting privacy and security at risk.
To obtain a better result through cryptography, the use of public and private keys are implemented that will be used in order to protect the required information. The messages are translated by computational algorithms in order to encrypt the information, then when it is sent to the receiver, it will have to apply the assigned key and change the computational language for the human.
We can also find several types of cryptography that make specific use depending on the key that we use, however, it is a topic that we will talk about later in further development. So we can see how blockchain cryptography offers us thousands of benefits so that we can send messages or information in a safe and reliable way, to avoid great risks like that of the dear friend Warren Buffett.
• Name of blockchain platforms:
Although we do not know it, most of the applications that we use daily that implement blockchain technology also offer us the cryptography system on their network, therefore, they guarantee us the security of being able to send files or documents totally safe and reliable, without the fear that they will be spread or seen by unwanted people.
For example, one of the most common that we usually use daily, or at least in my case, is the Steem blockchain platform, as well as other relevant ones that are part of the blockchain ecosystem which are:
• TRON
• WMware
• Ethereum
• Witnet
• Hyperledger
• Augur
• IOTA
• Syscoin

How do we know there are several types of blockchain, whether they are public, private, etc. As well as there are several types of blockchain platforms according to their classification, for example, there are blockchain platforms based on cryptocurrencies, on development tools, on sovereignty, on shared data, on applications that develop other applications, etc. They are an infinity of blockchain platforms that specialize in a particular field, that is why each of them collaborate with the ecosystem, as well as the participation of each one of us.

2) Explain the public key CryptoGraphy.
The implementation of the cryptography of the public key is very important to carry out any operation within a blockchain network, that is, this key, as its name says, is totally public and visible to the recipient to whom we are going to send any type. information, file or transaction. In addition, with the public key we do not run the risk of exposing our security as with our private key, since both are two very different things and with different uses.
The public key is really important to encrypt a message that wants to be sent in a very private way, as well as the private key, since both form a fundamental role so that any information or operation can be sent / received with total success. This key allows us to send any type of message or information to another person, that is, I must have the public key of the recipient to be able to send the information, and once the recipient receives it, he must implement his private key in order to decrypt the encrypted message.
We are going to put a clearer example to understand better, suppose that I want to send a very secret message to my friend Pedro, but in order to send him this message he must indicate his public key so that he can get the information. Then once you see that my friend receives the message, he must implement his private key to be able to decipher and read the withheld information, we must also know that both keys are linked together, that is, the private to the public, however the private it is totally secret and should not be shared with absolutely anyone, as its name says it is private.
Then we can see how the public key is a fundamental part of cryptography, since to perform any type of encryption operation this key is one of the main ones, since in fact it is compared with asymmetric cryptography, of which We will talk later. However, we must clarify that the public key cryptography is also linked together with the private key, since one is used to encrypt and the other to decrypt.
So we can see how public key cryptography offers us a series of advantages and benefits once we are going to perform an encryption operation, for example, it gives us authenticity, it gives us security since this key does not put us at all risk, also guarantees us the freedom to send said message or operation

3) Explain the private key CryptoGraphy.
Now we will talk a little about the cryptography of private keys, that is, the opposite of the previous key. We must know that private key cryptography only works in the encryption of a single key, that is, here a private key and the other public are not needed to be able to operate, since both parties, that is, the sender and the recipient must enter the same private key in order to encrypt and decrypt the message to be sent.
We must know that when we perform operations with private key cryptography, both users must establish a private key that is the same, since both will enter the same at the time of performing this operation. Therefore, both parties must agree to create a secret or private key that works for them to encrypt or decrypt the message, whether to send or receive, that is why this is where a very important part comes in. , since when implementing said key, it must be taken into account that it is delivered by a secure means of communication, if it is in person it is much better, since it would not be putting at risk that the private key is exposed by malicious people.
So let's put a clear example about private key cryptography so that we can understand better:
My friend Pedro and I decided to carry out encryption operations through private keys, but for this, we have to agree to implement a secret key that is the same in order to carry out this process. Then externally we meet and share the key that we will both use, so that no one can look at it, then when we go to send the message each one must enter the private key that we have both established, since both are used to encrypt and decipher the message.
So we can see how the roles change in the cryptography of private keys, many users may not have so much confidence in only having a single key to carry out the encryption process, however, it also gives us a lot of security and privacy when we want to send any type of file or information.

4) Explain the CryptoGraphy of digital signatures and what is Singing Of Transaction / Message?
We all know that signatures play a fundamental role within conventional finance, therefore, they also form an essential part within digital finance, that is why the implementation of digital signature cryptography has offered an alternative more reliable so that we can operate more safely.
The cryptography of digital signatures is a great tool so that we can protect ourselves against cyber attacks, since through it we can create a mechanism that helps us protect our message or information that we are going to send to our receiver, so that he himself can verify the authenticity of that message.
That is, when we are going to send a message through the cryptography of digital signatures, we must know that the data is linked in both users, since the sender is in charge of placing a digital signature so that the receiver can authenticate said message, but for this he must implement his public key to be able to see what has been sent to him.
We are going to give a clear example about it, that is, I decide to send an encrypted message to my friend Pedro, and for this he must place my digital signature and a private key that only I know in order to protect the information, then my friend Juan verifies the message with his public key to verify that the message is from the sender he is waiting for. Thanks to this, the receiver can verify that the message is completely correct thanks to the use of his public key.
• Singing Of Transaction
• We must know that when the sender is going to send the message, the information is transformed into a hash value, that is, into a series of alphanumeric data, in order to protect the information.
• Then the issuer must enter a secret digital signature that only he can know, so that said information is converted into a hash value.
• After the message is sent to the receiver, he himself must enter the public key that matches the sender's address, and then decrypt the Hash value of said message.
Then we can conclude that digital signature cryptography is very safe and reliable, since the set of private and public keys play a fundamental role in the encryption and decryption of the message. That is why when the digital signature is entered, the message is automatically converted into a hash value, then the signer must verify that the address is correct and then enter the public key in order to see the message.

5) Explain what is symmetric and asymmetric cryptography.
We all know that cryptography is a fundamental part of blockchain technology and of the thousands of cryptocurrencies that currently exist in the market, this in order to support important data and information in your network. That is why there are also several types of cryptography, one of them is:
• Symmetric: This type of cryptography is one of the oldest methods that has existed in the world, in it we can only use a single key to manage the operation in both users, that is, either to encrypt or decrypt the message that we are going to send / receive. We could compare it a bit with private key cryptography, since in it we also use the same private key to encrypt and decrypt our message.
How do we know when implementing the same key for encryption and decryption, perhaps it does not have as much computational power as other types of cryptography, as well as the level of security is not as high, however it is still a great cryptographic power that allows us to maintain safe our most private information. However, in order to have a higher level of security, it is important that the private key that both users implement is established through an external method, since this would be avoiding a possible case of hacking in the use of keys.
• Characteristics:
• This type of cryptography, by implementing the use of a single key for encryption and decryption, makes its computational power less, that is, operations are carried out more quickly and effectively without having to wait so long to obtain the message.
• Symmetric cryptography allows us to perform a large number of operations with the advantage that they are executed quickly, since it does not require so much computational power.
• It is important to know that symmetric keys have a series of alphanumeric numbers with lengths between 128 bits or more.
• Perhaps one of the aspects that can be a great limitation is the use of a single key for the encryption and decryption of messages, this means that the security level of this type of cryptography is not as high as others.
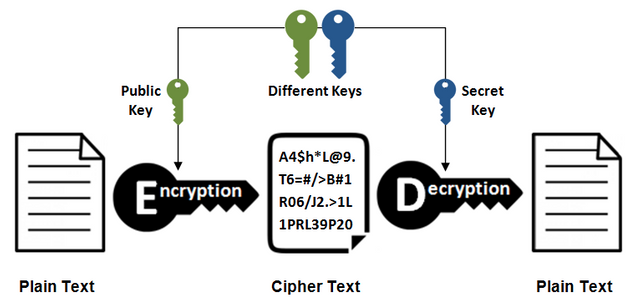
• Asymmetric: Now if we go to the case of cryptography in an asymmetric way, we can say that it is totally opposite to the previous one, since here it is necessary to use two keys that serve to encrypt and decrypt said message, better known as public or private keys. These keys are linked between both users, but the two are totally different and are used for different cases.
In the case of the public key, it is the key that we are going to share with our user so that he can carry out the process of encrypting the message, as its name says, it is a totally public key that does not put us in absolute risk. On the other hand we also have the use of the private key which is very important, since thanks to it the user or sender can decrypt the message that they have sent, remember that this key is very private and must be protected in an extremely safe place.
• Characteristics:
• By having two types of keys that allow the encryption and decryption process to be carried out, it makes its security level higher and less prone to future attacks.
• Of course its computational level is higher, this means that the operations carried out through asymmetric cryptography will be a little slower to process.
• Asymmetric cryptography is ideal for sharing very private information or messages by both users, as it guarantees them a higher level of protection through the implementation of two types of keys for the use of encryption and decryption.
• However, perhaps one of its limitations may be the large amount of computational power it possesses, which may cause operations to run more slowly.
Then we can see how both types of cryptography offer us different uses and different advantages, and that is the best, since we can choose which is the best option that is best for us to operate through it. Blockchain technology advances more and more, and in this case it will not be the exception, that is why the implementation of cryptography is a great advantage for millions of users in the world who seek to protect their security.

6) How Blockchain Wallets CryptoGraphy works and explains the available types of Crypto Wallets.
We already talked a little about the different types of cryptography and its different uses, now we are going to detail a little about the importance that it has in today's blockchain wallets, of course, these wallets play a great fundamental role within our finances, and that is why the implementation of cryptography offers us a higher level of security so that we can store, safeguard, or carry out certain types of operations with our funds.
We know that blockchain digital wallets are not the same as the conventional wallets that we are used to using, these wallets differ in great aspects that in turn give us more benefits and a higher level of security, such as the fact of being Based on blockchain technology, they make them more secure and that we ourselves can have absolute control of our funds, as well as another series of advantages of which I will name below.
The cryptography of blockchain wallets offers us the advantage that we can obtain a ** public key ** and that we can generate a ** private key **, this in order to be able to carry out operations in said wallet through these keys, which are extremely important. For example, the use of the public key is a series of numbers and letters together that serve as our wallet address, that is, if someone wants to send funds to our account, we must pass our public key to them in order for them to funds successfully reach our account, let's see it as the point of view that the public key is the identity of our wallet.
Now, the implementation of the private key can be used in several aspects, for example, when we want to send funds to another account we must implement a private key to completely end the transaction, this private key is established by ourselves with the appropriate characters that are safe and reliable, it is also important to clarify that this key cannot be shared with absolutely anyone, since if we expose our private key, we are exempt from losing absolutely all our funds.
The implementation of cryptography in blockchain wallets offers us security and privacy, since it guarantees that our operation data or our keys are not disseminated or exposed by cyber hackers. We have been able to see how cryptography is a very old security method, and that is why as the years go by it develops more and more, that is why each time the security levels that the security grant us are higher. blockchain wallets in the use of cryptography
• Characteristics:
• Cryptography offers blockchain wallets security and total transparency, so that the user can feel very safe having their funds there.
• Blockchain wallets are a more alternative and secure way where we can protect our assets without the fear of being stolen.
• The implementation of public and private keys play a very fundamental role within the wallet, in addition the use of cryptography guarantees transparency and security.
• There are several types of blockchain wallets that thousands of services can offer us, whether they are cold and hot wallets, software, paper, etc. All so that the user can use the one they like best.
• Types of blockchain cryptocurrency wallets:
We know that cryptocurrency wallets are the safest way where we can store or protect our assets, that is why we have at our disposal the possibility of having several wallet options with which we can operate, one of them is:
• Cold wallets: Security and privacy are very important tools, that is why today there are wallets that work offline, that is, without an internet connection or any system that records your transactions. This type of wallet is better known as cold wallets, which are responsible for protecting the privacy of the user.
We all know that when we carry out operations online we are more prone to cyber attacks, that is why cold wallets are an ideal solution to protect our funds, since the operations we carry out will be without any type of internet connection.
These wallets are ideal for large investors who handle a large amount of money.
• Hot wallets: These types of wallets are the ones that we are used to using almost daily, they are those that work through an internet connection, therefore, we are a bit prone to cyber attacks by of malicious agents.
• Desktop wallet: These are those wallets that are downloaded from the extension from your computer, and are not available for other types of electrical equipment such as the telephone. An example of this is the Electrum and Sqrl wallet.
• Hardware Wallets: These wallets are a bit out of the ordinary that we are used to using, since this type of wallet works through USB devices and other storage tools but in a physical way. They also work without an internet connection, which makes them very secure.
• Software wallets: Now these wallets are the ones we usually use, such as those for telephones, those for computers, etc. These wallets are completely connected with an internet connection, which can be a great limitation, since we are prone to cyber hacks.
• Exchange wallets: Today there are cryptocurrency exchanges that offer us internally the possibility of having a wallet so that we can protect our assets, however, we must know that this type of wallet is not 100% secure , so it is advisable to use one that is not linked to Exchanges.
• Paper wallets: As the name implies, they are wallets that work through paper, where of course, they work offline, guaranteeing the user security and privacy. These wallets also have public and private keys that are extremely important for development within it.
• Mobile wallets: We all know that mobile wallets are a much easier and feasible option through which we can operate, therefore these wallets were created with the ability to support the size of a mobile device, guaranteeing the user greater comfort.
So we can see how there are several types of cryptocurrency wallets, which offer us different benefits and tools, we just have to choose the one we feel comfortable with the best. An example of cryptocurrency wallets are: TrustWallet, Metamask, Electrum, Tronlink PRO, Ledger Nano s, Sqrl, Telos, etc.

7) What are Merkle trees and what is their importance in blockchain?
The Merkle tree is an incredible structure created in order to concisely organize a large amount of data, that is, can you imagine how tedious it can be to verify each of the Hash of the transactions of each block one by one? Yes, it is quite a slow process. That is why the Merkle tree was created in 1979 by its creator Ralp Merkle in order to create a structure that would facilitate this data verification process.
We all know that a tree has several branches and a main root, because in this case the Merkle tree has in each of its branches a specific node from which the leaves of its other branches will be created, we must know that the first initial nodes go in the first root, then from them is that the other branches are created until reaching the main root or Merkle root.
It may sound a bit confusing, but in reality it is the opposite, since the Merkle tree has a system where we can group each of the nodes / leaves in order to get to our main root. A very important fact is that the leaves of the tree cannot be altered in their entirety, since otherwise we could get an unwanted hash that is not the main root of our Merkle tree.
I am going to give a brief example about the creation of the Merkle tree, that is, the first thing I have to have are my initial nodes / leaves which are:
(SCA1; SCA2; SCA3; SCA4; SCA5; SCA6; SCA7; SCA8.)
• Then each of these sheets we are going to get its Hash value, for this I used the SHA-256 page to obtain the same
• We are going to introduce each of these leaves until we obtain our Hash of our first leaves.
• Then the grouping process begins, since in our first level we must gather or group our Hash of the main sheets in order to obtain our sheets of the first level.
That is, we are going to group the leaves two by two of our initial leaves to obtain our first level branches, then it would be: (SCA1SCA2) (SCA3SCA4) (SCA5SCA6) (SCA7SCA8) and we will obtain a different hash for our first branch.
• Then we have to assemble our Hash of our second branch, and for this we must join the leaves three by three until we obtain our Hash of our second branch, that is: (SCA1SCA2SCA3SCA4) (SCA5SCA6SCA7SCA8)
• Now finally we must join each of our initial leaves in order to obtain our main root or Merkle root, which would be: (SCA1SCA2SCA3SCA4SCA5SCA6SCA7SCA8)
• Once we have grouped this together, we will obtain our main root which will be our root address.
• I am going to present the following image that I made in one of my cryptoAcademy classes so that we can understand the creation of the Merkle tree:
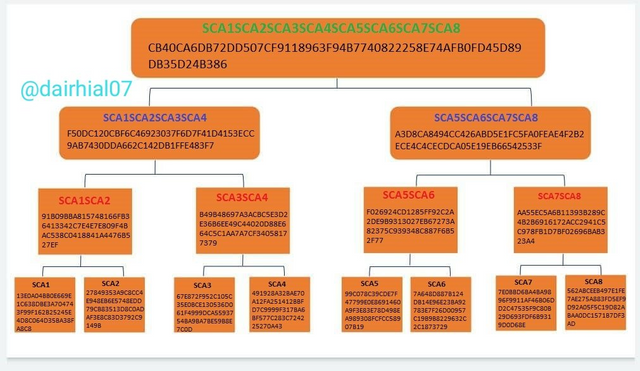
• Then we can see that the Merkle tree is read from bottom to top, and that our first level is our initial leaves with which we will create each of our branches.
• In our first branch we put together our initial leaves two by two in order to obtain the ideal hash for each one of them.
• Then in our second level we are going to put our leaves together three by three until we can obtain the ideal hash of each one of them.
• And finally to obtain our main root we must put together all our initial leaves to obtain the desired result.
• Importance of the Merkle tree in blockchain:
As a result of our explanation we can see how important this process is for the blockchain ecosystem, since thanks to the Merkle tree the process of verifying each of the operations and transactions of the blocks can be facilitated.
It is also important to clarify that each of the leaves of our tree must be composed evenly, since if you ever see the leaves of the tree turn out to be odd, it is impossible to continue with the process, since its structure was created so that each one of the leaves were accompanied. However, if this were to happen, what we can do is duplicate the pair of the sheet that is next to it, and continue in the same procedure.
That is, we are going to give an example of it, if one of the main leaves is missing in my tree, it is impossible to continue with the verification of the rest:
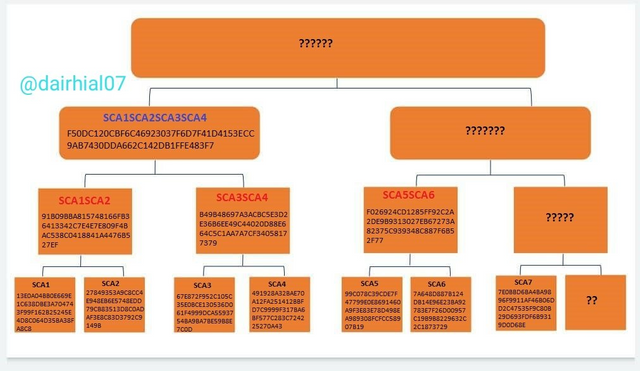
However, what we can do is duplicate the sheet of the missing partner in order to continue with the procedure, then it would look something like this:
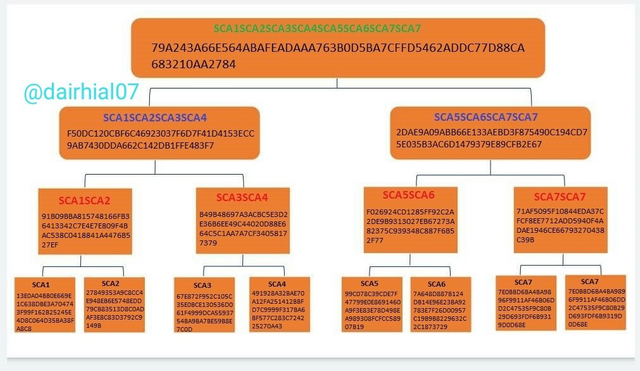
And we can see how each of the branches automatically change in their main value, since as I said before, when altering one of the leaves, the main result would not be the same.
So we have no doubt of the great importance of the Merkle tree in blockchain since:
• It allows us to verify information quickly and safely.
• The network that implements this structure in its system will give it high scalability power.
• Security is a very fundamental element that characterizes the Merkle tree, since it prevents each of the leaves / nodes from being poorly organized and from transmitting false information.

8) Practice + Theory, do some practical research, study on Blockchain Demo: Public / Private Keys and Signature and then explain the functionality of Key, Signature, Transaction.
In this case, we are going to explore some features of Blockchain Demo a bit:
• Keys:
In the section of keys we can see how they show us two types of keys, which are public and private, these keys we have already talked about beforehand about them and about the fundamental role they play in cryptography.
As we talked about previously, the use of public and private keys are firmly associated with each other, in the case of asymmetric key cryptography the implementation of each of them is very important, since both allow operations to be carried out successfully. .
How can we see, we automatically receive our private and public key, which the first is associated with the second, we can see an example of it:
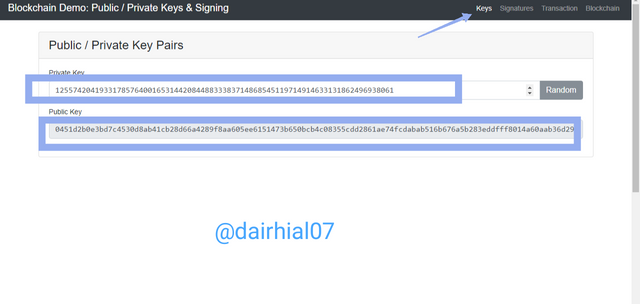
• Private key: Here we can see how the private key is a series of numbers which have a total of 77 characters:
12557420419331785764001653144208448833383714868545119714914633131862496938061
• Public key: Now in our public key we can see that it is a series of alphanumeric data, which has a total of 130 characters between letters and numbers.
0451d2b0e3bd7c4530d8ab41cb28d66a4289f8aa605ee6151473b650bcb4c08355cdd2861ae74fcdabab516b676a5b283eddfff8014a60aab36d290a6b5e6816a6
In this case we can notice the difference between both keys, since one is longer than the other and one has letters and numbers, while the other has only numbers.
How do we know the private key is linked to the public one, therefore, if we change the first one, the second one will automatically change, let's see a brief example about it:
In this case I decided to change the last three digits of my private key, and I could automatically see how my public key changed:
• Private key:
12557420419331785764001653144208448833383714868545119714914633131862496938741
• Public key: And my public key changed to
04f38a4bf44a0d3daafc877584592a99e2a00a0a2ac5543bd9f5df06581e63e8bf578bca8c7d3d75d080108079bc298f0e88bbabe801187e1242b5b5fb4e76c265
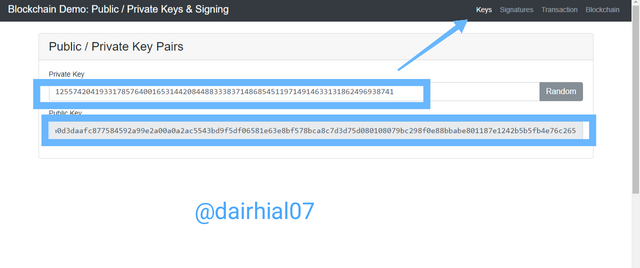
We can also change our private key by clicking the "Random" button and automatically the public key will also be changed.
So we can see how our private key is linked to our public key.
• Signatures;
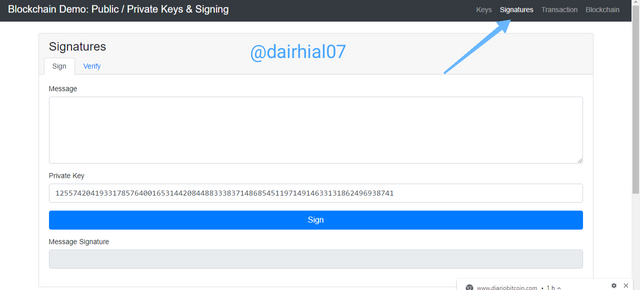
Now we will go to the section of the signatures, as we know the signatures form a fundamental part of any operation, that is, they give validity and authenticity to them. As we can see, the signature is linked to our private key, therefore it will appear here.
In this case, as its main page shows us, we can see a large box with the word "message" in which we are going to enter the message that we want to provide to the operation. We can also see my primary private key that I got in the "Keys" section
• Then I entered the word "Steemit crypto academy season 3"
• We must also enter a private key of our choice, in my case I entered "471"
• We will click on "Sing"
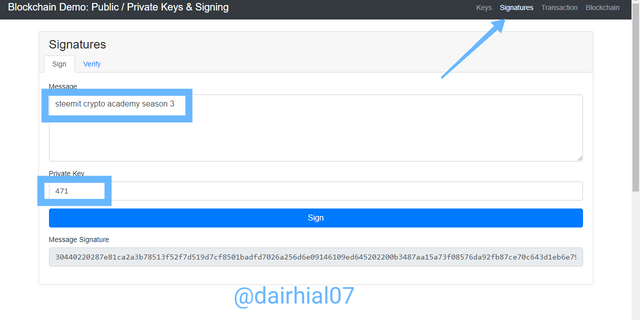
Then they automatically provide us with a generated message signature, which in my case is:
(30440220287e81ca2a3b78513f52f7d519d7cf8501badfd7026a256d6e09146109ed645202200b3487aa15a73f08576da92fb87ce70c643d1eb6e79761b203c1078e83d72392)
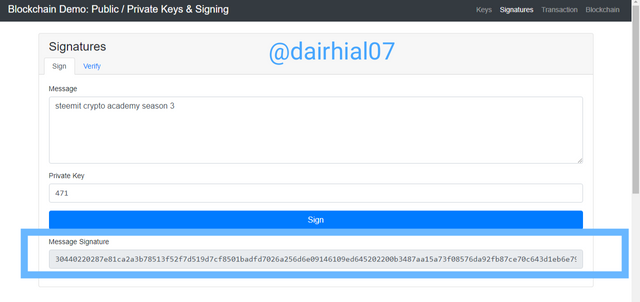
Then we have to verify this operation successfully, therefore we will click on the "verify" box
• An interface will appear with more extensive details, as well as our messages, our public key and the message signature key.
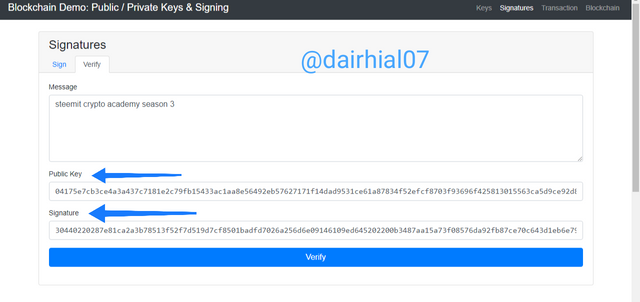
• To correctly complete the operation, we will click on "verify"
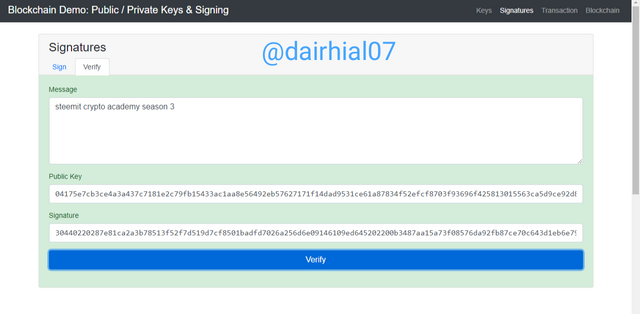
• Then show operation will come out with a completely green box, and there we will know that our operation was totally successful.
• Transaction:
In our third tool we have the transaction tool.
• We are going to go to your page and an interface will appear with our public key already entered automatically, as well as our private key that was previously linked.
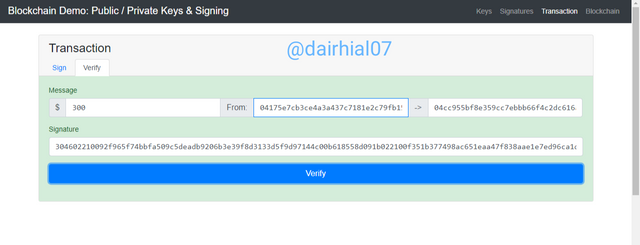
• Then we are going to enter the amount, in this case I entered $ 300
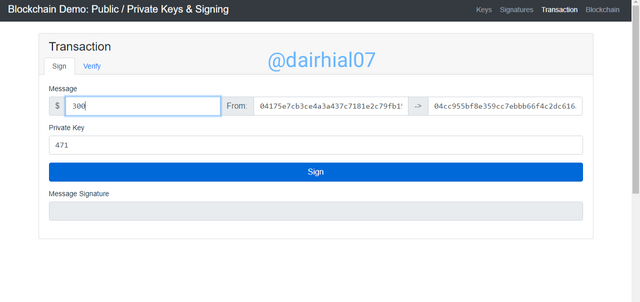
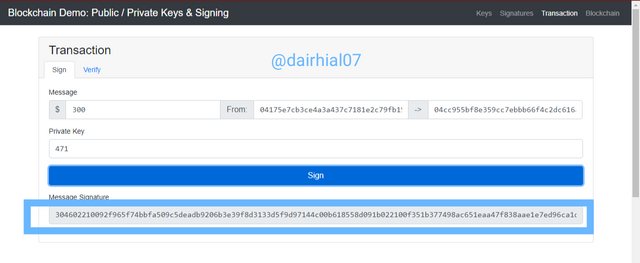
• Then we are going to click on "Sing" and our signature message will appear, which is:
(304602210092f965f74bbfa509c5deadb9206b3e39f8d3133d5f9d97144c00b618558d091b022100f351b377498ac651eaa47f838aae1e7ed96ca1d2f08957ba6bd34468f4777134)
• Now we are going to proceed to fully verify our operation, we are going to click on the "verify" box
• It will take us to another interface where we are going to verify our operation, where we can see our message signature and other important data.
• After making sure that the data is correct, we will click "verify".
• If everything is correct, a green interface will appear, indicating that everything is fine.
• Blockchain:
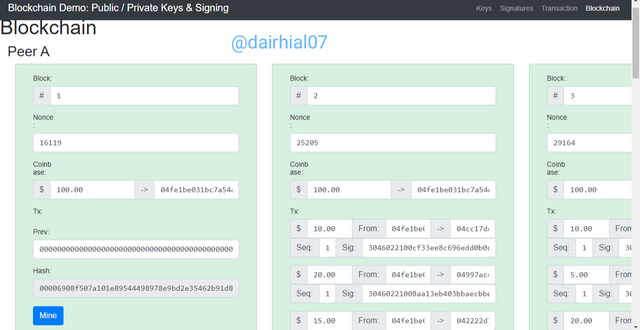
Our latest blockchain tool we can find how transactions are organized in blockchains.
• We are going to click on the "Blockchain" tool and its main interface will appear.
• Each of the available blocks will appear, as well as some extremely important details, such as the block number, the Hash value, the nonce, etc.
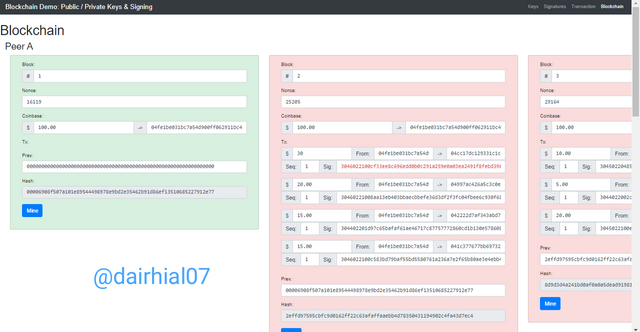
• Now if we detail very well we can see that if we were to alter some of these values automatically the block would not be valid and the color would change to red.
• Just as block three would change automatically and would also be invalid.
• We saw an example of this in the structure of the Merkle tree, where I explained that if we were to change or or alter any value, everything else would automatically change, since the same happens in this case
• However, we can click on the mining button and the block would look valid, and its nonce value would change.
• As we can see, the value of the nonce of block 2 was 25205 before being changed, after I altered it it changed to 143478
• In the same way, block three before being changed had a nonce of 29164, after I altered it it changed to 19411
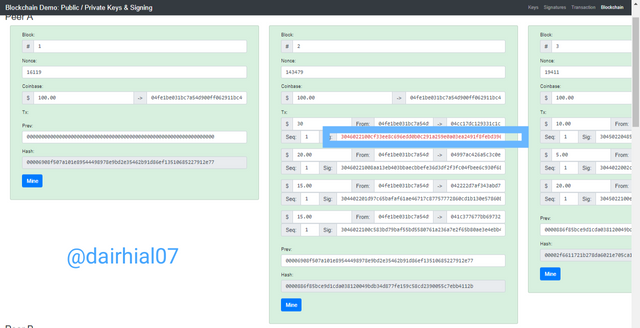
But even though the block was validated, it is still invalid, since if we look closely we can see the signature of block two is still in red, which means that it does not match the previous signature.
This part is extremely important, since here we can know how safe and real the transaction is thanks to this method.

Conclusion
We have reached the end of our task and I can only say that it has been an excellent class full of many knowledge and interesting things, therefore I could understand that:
• Cryptography is a very important method that gives us security and a lot of protection, the different ways of using cryptography offer us more alternative tools so that we can operate, such as the case of asymmetric and symmetric cryptography.
• The use of public and private key cryptography and digital signatures are different methods with which we can operate, we just have to choose the one that seems best to us.
• The use of cryptography covers many levels, in the case of the blockchain world they provide us with incredible tools with which we can operate, such is the case of wallets and their different uses. The implementation in them makes their security level increasingly secure and reliable to protect our assets.
• Another very fundamental tool that helps the blockchain ecosystem is the integration of the Merkle tree, we could already see all the work that it facilitates us by being able to verify data instantly and efficiently.
That is why I thank professor @stream4u for this incredible class, where I learned a lot about the world of cryptography and all the advantages that he has to offer us. It was an honor to participate, until next time.