Password Brute Force Attacks Threaten Millions of App Users

In September of 2014, private photos of a number of celebrities, including Kate Upton and Jennifer Lawrence, were leaked onto the image-based bulletin board 4chan. It was soon discovered that this leak occurred as a result of a brute force attack against Apple’s iCloud, which until then had not limited the number of login attempts for each user account.
Hackers exploited this oversight via the use of a password-breaking tool known as iBrute, which enabled them to gain unauthorized access to several celebrities’ accounts and steal their private photos from available data backups.
It is important to note that iCloud is not the only service to have been recently threatened by brute force attacks, however. This type of attacks also affects online accounts stored on users’ mobile devices, as a recent study conducted by AppBugs reveals.
Of some 100 mobile apps analyzed, AppBugs found that 53 mobile apps are vulnerable to password brute force attacks. These vulnerabilities threaten the password security of approximately 600 million users, both on the Android and iOS mobile platforms.
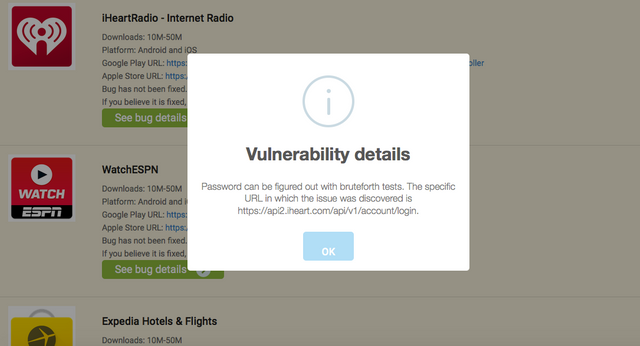
“Every single issue is an imminent threat to all users using that app,” AppBugs warns. “Once an attacker knows an app is vulnerable to brute force, this person can launch immediately attacks to guess user’s password from the web service of the vulnerable app on all user accounts.”
As with the iCloud leak, AppBugs’ study reveals that these apps, which include iHeartRadio, CNN, and Walmart, do not set a limit on the number of times a user can try to access their account.
AppBugs is right. According to a research paper written by Joseph Bonneau of the University of Cambridge, passwords in general contain between only 10 and 20 bits of security against any form of attack.
An attacker who can make a login attempt to a vulnerable app service at least 30 times a minute can therefore successfully crack a password using between 1,024 and 1,048,576 guesses, the latter of which can be completed within at most 24 days. Depending on the strength of any given password, the time required to break a password may decrease to as little as half an hour.
Some app developers have attempted to counter this vulnerability by deploying web application firewalls (WAF) or other rate limiting techniques that can reset a connection with a particular IP address after a certain number of login attempts. However, AppBugs observes that these mitigation strategies do not work
“Resetting the connections will just slow down the attacks. The attacker can simply make less connections in every minute to circumvent the defense. Blocking some IP addresses will just force the attackers to use some other IP addresses. For real attackers with a botnet, this is totally not an issue.”
Most attackers do not operate under such constraints, however.
“Attackers have no problem launching the attacks from multiple IP addresses on multiple user accounts in parallel and often can make guesses more than 30 times per minute,” AppBugs notes. “If today the attacker launches such attack against most user accounts in parallel, he will be able to get most user passwords within 24 days.”
So far, AppBugs has released the names of 15 apps after giving them 30 days to fix their password brute force attack vulnerabilities. Only three of those—Wunderlist, Dictionary, and Pocket—have issued fixes.
Unless they request extensions, AppBugs intends to release the names of the remaining 38 apps on July 30.
To learn more about AppBugs and its efforts to help strengthen mobile security, please visit the company’s website here.
Congratulations @mrhacker1024! You have completed the following achievement on the Steem blockchain and have been rewarded with new badge(s) :
Click on the badge to view your Board of Honor.
If you no longer want to receive notifications, reply to this comment with the word
STOP