SECURITY TOKENS
Initial Coin Offerings has been the talk of the blockchain investors for a couple of years now. ICOs enjoyed an all-time high in 2017, and since then they have been generating tons of investments and it has been reported that they even surpassed the venture capital funding. The benefit of ICOs is tremendous if they are launched on a blockchain platform as you could add a smart contract that will execute terms and conditions associated with that ICO. Now there are three types of tokens that ICOs offer
- Equity Tokens
- Utility Tokens
- Security Tokens
Utility token is a non-physical digital token of a cryptocurrency that will help to fund the development of that cryptocurrency, and once that currency establishes, it could later be used to purchase good or service offered by the issuer of the cryptocurrency. Equity token is easy to understand for a person who understands 21st-century stocks. They represent your share in any company.
But why there is a need for another token. It is because the security token is capable of everything that other token can’t do.
To put it simply, a security token is a physical and portable device that stores some information such as personal information electronically so as to authenticate that person. Security tokens don’t necessarily give ownership rights of a company but they do take some value from the company. People invest in security token with the hopes that it will increase in value someday which later on they will be able to sell and collect profit.
Security tokens are cryptographic digital contracts that pay dividends, share profits, pay interest or invest in other tokens or assets to generate profits for the token holders, and can be traded independently. By basic definition, the security tokens are the type of tokens that pass Howey test (test). The Security tokens are introduced as new standards in the crypto market after ERC-20 and ERC-777.
The security token is a product of an amalgam of both the traditional finance sector and blockchain sector. This is because the assets divvied up via tokens already exist in the traditional market — even the biggest markets like public or private equity and real estate.

Advantages of Security Tokens:
Reduce cost:
Smart contracts remove intermediaries, which in turn cuts down the costs of service delivery. And the administrative costs of buying and selling are zero.
Increase Speed:
On the other hand, it speeds up execution by removing the middlemen involved, and by removing these the security tokens become a more attractive investment
Global:
The tokens may be entitled to global trading depending on their set up which means as long as you have a wallet you trade from anywhere in the world.
24/7 trading:
Crypto trading outshines traditional trading because it is non-stop. You can trade any time day or night.
Rapid adoption:
Security tokens are being adopted at a fast pace than other tokens.
SEC Compliance:
The security token is fully compliant with SEC, meaning no breaking of the law.
Disadvantages of Security Tokens:
Security tokens come with many regulations. There are limitations on who can invest and how they can be exchanged. Thus, they can’t be traded freely. This affects liquidity significantly.
Applications of Security Tokens:
Bcap (Blockchain Capital)
Bcap is accepted to be the main organization to present an open offering for a securitized token. Through its ICO, Bcap delivered a critical change in the upcoming token dealing industry in a few different ways. In the first place, the offering just acknowledged assets from authorizing speculators. Furthermore, it likewise built up an outline for upcoming tokenized securities and put resources into different ICOs that grasped the best procedures.
Science Blockchain
Science Blockchain is a reserve for funds and incubator that spotlights on Blockchain speculations and investments. The fund was raised through a security tokens (SCI) ICO. Token holders will appreciate up to a greatest of 70 percent of the surge of salary from portfolio organizations. To add to that, it is normal that the returns from the store’s liquidity occasions will be utilized to repurchase tokens through a buyback program. This will enable financial specialists to profit by value appreciation.
SPiCE VC
While the facts demonstrate that VCs keep on assuming a tremendous job in every huge interruption within recent memory, the investment business stays immaculate. SPiCE VC is ready to change this industry by utilization of its tokenized show. This VC demonstrate offers for instant liquidity to speculators. While LPs in the customary investment reserves needed to sit tight for between seven to twelve years to gain access to their assets, token holders in the SPiCE do not just get a bit of the left pie, however, they likewise get the chance to appreciate a tradable resource. The organization intends to wander into utility tokens later on. Be that as it may, they are at present centered around security tokens.
Working:
Security tokens have three components:
Tokenization democratizes capital markets, and break down large assets into smaller pieces and increase liquidity.
After that tokenization makes the market more efficient. Blockchain smart contracts guarantee ownership and secure trading which reduces the end result for all parties.
And finally, tokenization opens up trillions of dollars in liquidity. The best use case for security tokens is worth trillion dollars alone which makes huge potential.
The Security Token offerings (STO) will dominate the blockchain market in the very near future and this is a new way of contributing to a project.
Creating Security token:
Security tokens are registered on different platforms, which solves the problems of security by creating an ecosystem on ethereum.
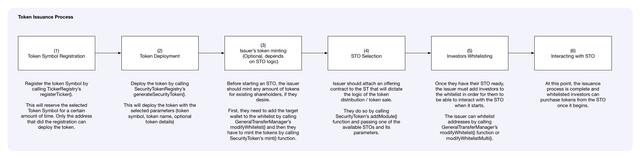
To deploy our security token on blockchain service it includes few steps:
Registering a token on PolyMath which means no one else can own it. I have registered a token named RNS with address of (0xec31074C61b10dc623F8cc2EfeF3C575404316Ed) using a
function registerTicker(address _owner, string _symbol, string _tokenName, bytes32 _swarmHash)
The function takes 4 parameters which have:
Address _Owner the same account calling the function
String _symbol: Token symbol to be registered e.g RNS
Token _Name: Name of the token to be registered e.g RNS Solutions
Bytes32 _swarmHash : used to store additional data
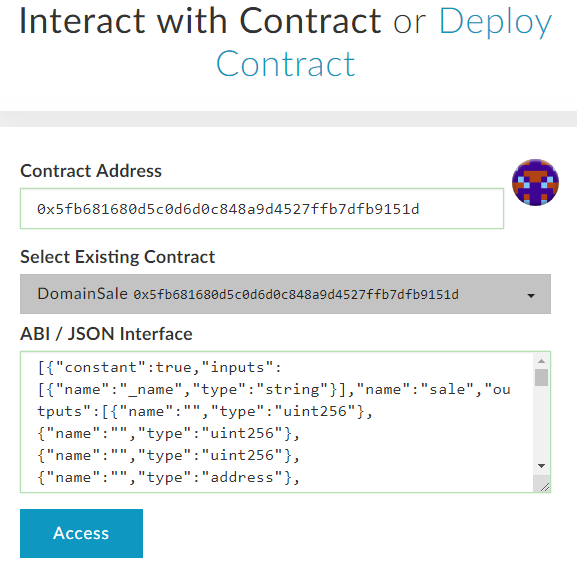
Once the registerTicker is executed a new token and symbol is added to the registry.
Interacting with smart contracts and MyEtherWallet:
-Meta mask should be running with Ropsten and having few ethereum in it. In this, there are 12 Eth on the meta mask. More ethereum can be added using (https://faucet.metamask.io/).
-Select Ropsten from the top right bar in the menu after opening ethereum wallet.
-The next step involves going into contract section, where the smart contract has been deployed along with Application binary interface which allows communicating with the smart contract from “outside”.
-Then select the Buy Contract from existing contracts and enter ABI value written above and copying that in textbox and press on the WRITE button.
-After filling the parameters, a prompt appears to sign the transaction.
-Signing the transaction, a form has to be filled that shows gas limit for the transaction that is automatically generated for each contract.
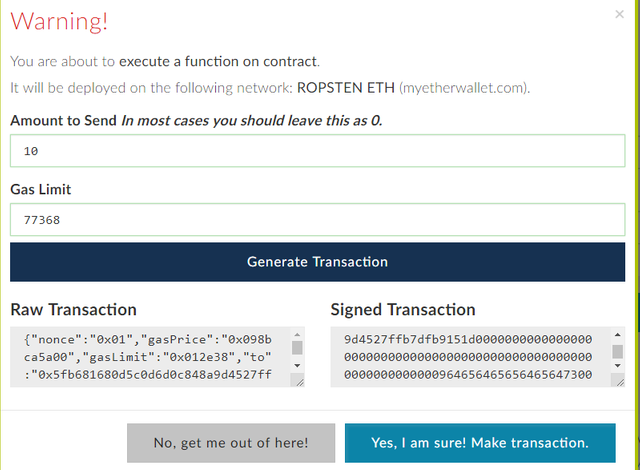
-Clicking on “Generate Transaction” button will create a signed transaction ready to submit to meta mask. A meta mask prompt will appear urging to review and confirm the transaction that was just made.
-Once confirmed, it sends the transaction to the blockchain for processing.
-The transaction can be viewed by clicking on meta mask. This will open Etherscan and shows us all out transactions that were made in event logs.
-Once event Logs(1) is opened, one can see that it has more than 1 transactions with additional data. To see the event log for the transaction that was just made, click on the last transactions to see ours.
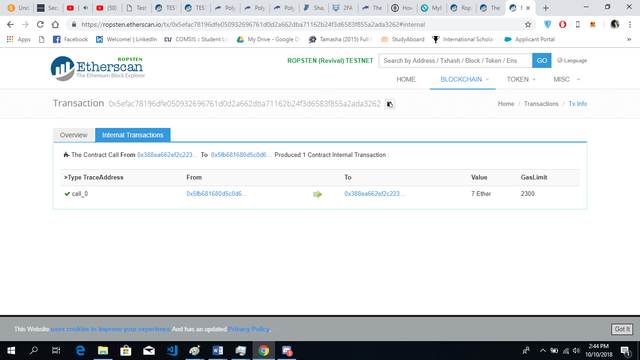
-All the values in Hex drop downs are a default. They could be displayed differently though.
-Now we have or token registered, the next step is to deploy the token SecurityTokenRegistery.It is responsible for deploying the corresponding token and also keeping track of them.
-This requires
function generateSecurityToken(string _name, string _symbol, uint8 _decimals, bytes32 _tokenDetails)
that takes 4 parameters :
string _name: The name of the token being registered. For example: RNS Solutions
string _symbol: The token symbol to register. It has to be the exact same token symbol as entered on the TicketRegistry.uint8 _decimals: The token decimals for the token. Generally, 18 decimals.
bytes32 _tokenDetails: Used to store additional off-chain data if needed. Can be empty.
-Once this method is executed, a new token will be deployed to the blockchain. Clicking it on the list from meta mask will show the transaction. This meta mask will redirect us at Internal transactions.
As the GenerateSecurityToken method has done its assigned functions, click on “To” addresses, the first transaction that will be clicked would display the Security Token that has been deployed.
