Tech Aide: Added Security Steps for Downloading Open-Source Software
In our "trustless" world, I am writing a post this morning on what I have learned to do to add an additional layer of security to my downloading and installation of software. Particularly open-source software, which we encounter a lot of when choosing to invest in blockchain technology and the resulting "digital asset" class.
 Image Source: Pixabay
Image Source: PixabayAs an older man, with a lot of experience in life, I have always enjoyed a good quote. The older I get, the more I like them ... 😊
Here is one which might be applied to our topic this morning:
"Eternal vigilance is the price of liberty"
So ... Let's talk about being prudent in taking some pretty simple steps to add some protection to our use of downloaded open-source software.
Checking Validity of Downloaded Software
While making no claim to being a "technical wizard" when it comes to this topic, I am well enough aware of the potential for any software to be a potential threat to my home network, that I take the following steps, when downloading and installing open-source software.
- Note: When downloading from large corporations, e.g. Microsoft, Apple, Google, etc., we typically don't even think about this, as we assume our protection is "built in" to their services to us. Hopefully right, but not the topic of this post.
This post is specifically about software accessible through open-source channels, e.g. "digital asset" wallets, as in the example which follows:
Yesterday, I wrote an update post in which I mentioned @arkecosystem and learning about the latest ARK wallet, for a digital asset in which I have chosen to invest.
Well, this morning I was following up and getting this installed, as I like to stay on top of ensuring I have the "latest, greatest" version of any software I use. Here are the steps I followed, which will provide you an outline for what I always do, no matter what the specific software may be.
- Step 1: Opened the link I maintain in a database, to the GitHub repositiory for the ArkEcosystem's software, and downloaded into the subfolder on my computer where I store ARK wallet sofware.
Note: If you are not already familiar with it, GitHub is the largest repository in the world for software code writers. If you choose, you can open an account there easily, so you can communicate with them.
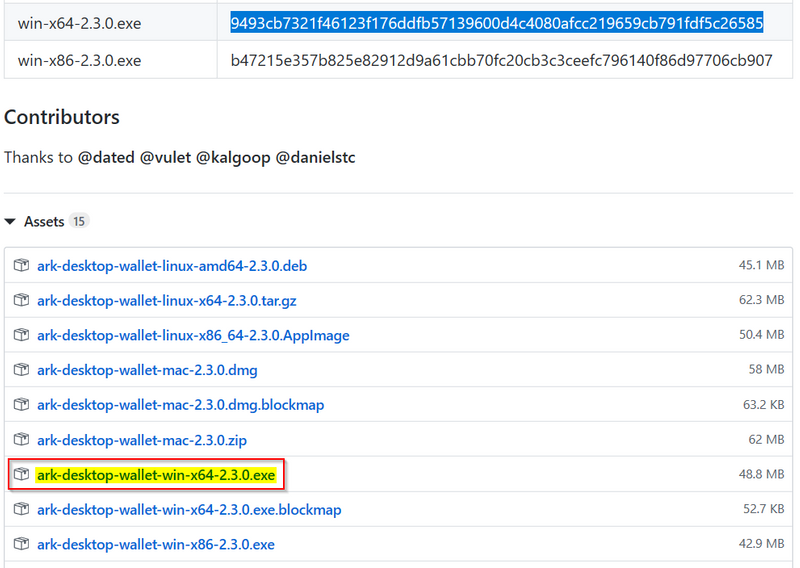
Image 1: Click on Software Link and Download
- Step 2: Opened the ReadMe file stored in the subfolder into which the file above was downloaded, and updated it with information from this latest download, as shown below.
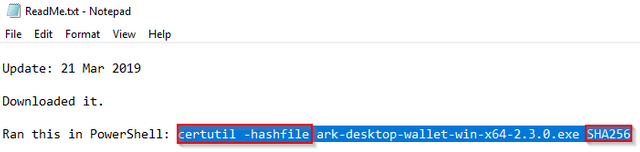
Image 2: Update CertUtil Specs in ReadMe.txt File
- Step 3: In the subfolder storing the downloaded file, hold down the Shift key the right click with your mouse, anywhere on the screen. This opens an instance of Windows PowerShell, as shown below. Copy and paste the CertUtil string stored in the ReadMe file into PowerShell and execute.
Note: If you are not already familiar with it, CertUtil is a Windows utility which has a number of uses ...
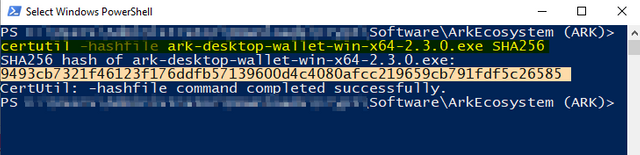
Image 3: Execute CertUtil Command in Windows PowerShell
- Step 4: Copy and paste the SHA256 hash generated in Step 3 into a spreadsheet designed to compare this string, with the one provided on the webpage from which the software was originally downloaded. See Image 1 above.
Note: Sadly, not all web sites provide the hash info needed. I have myself written to the software authors, when I have found this valuable info missing, and have been generally pleased at their responsive in providing it for future releases.
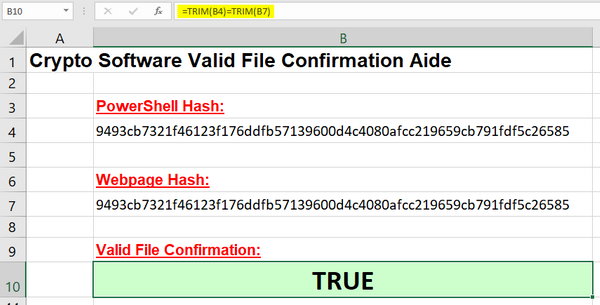
Image 4: Compare SHA256 Hashes in Spreadsheet
As most of us have already experienced, the cryptographic strings found in this new "digital asset" class universe are bewilderingly complex. Rather than take the time and trouble, all while risking the chance of error, to compare them manually, I built a spreadsheet to "automate" the process.
The spreadsheet shown above is comparatively simple. The key is the formula shown in the B10 cell. It strips any leading or trailing "white space" and compares the two strings - one from the PowerShell command and one from the website. The formula returns TRUE if the strings match. FALSE if they don't.
So ... What just happened?! 😉
The SHA256 hash value is a sophisticated store of a number representing the file you just downloaded. By comparing it to the value generated by a copy of the software now downloaded on to your computer, you are checking to ensure that you are not working with a tampered version of the file.
Hackers and those with nothing better to do with their lives than cause us trouble can be very sneaky in what they can embed in these files. Unbeknownst to you. The SHA256 hash value is one common way of testing for this.
Disclaimer: While not bulletproof, these steps provide just what this post says - "added security." For just a bit more peace of mind ...
So ... Safe to install the newly downloaded sofware now right? Yeah ... Well no ... Not entirely ...
- Step 5: You may, as I commonly have, experience the following dialog, when you begin to install your newly downloaded software. If you want to proceed, this illustration shows you how to do it - click on the "More Info" hyperlink, then on the "Run anyway" button.
Note: Again, far from an expert, but my understanding is Windows Defender (if you have it activated, as I do ...) is checking to see if there is a Microsoft certificate for the software publisher on file in their security systems.
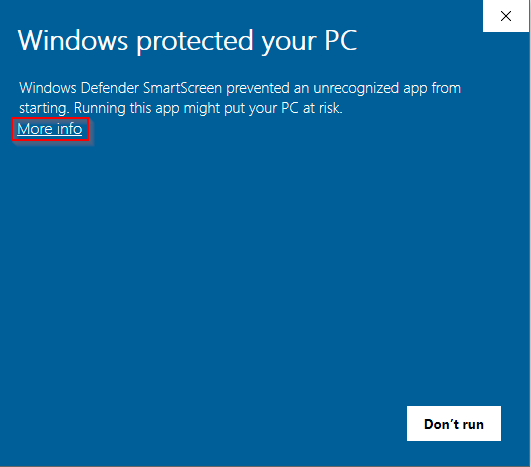
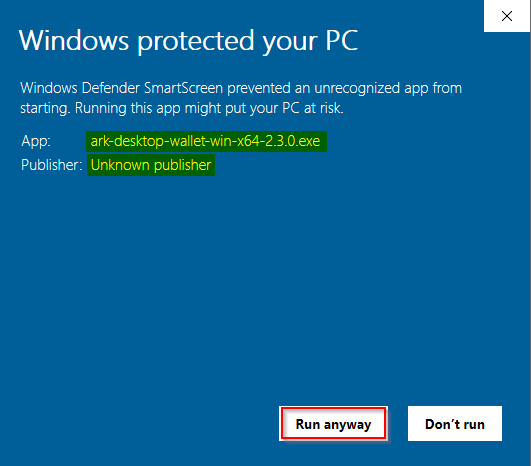
Image 5: Getting Past Windows Security Check?
While this may initially be alarming, keep in mind that many, many code writers in the open-source community produce what they do in their "off hours," when they are not working at their "day jobs." Many elect, for various reasons not to take the time to register for these certificates. Perhaps as a philosophical "statement," perhaps due to a lack of time, etc.
After researching this issue and reading up on what it represents, I have always done what I show above and, so far, have not lived to regret it. You will have to decide for yourself whether this is a risk worth taking.
These are the steps I successfully followed a short time ago. Along with taking the time to capture the screenshots above for this post.
 Image Source: Pixabay
Image Source: PixabayWrapping up, while never a fan of being paranoid, I have long been an advocate for being prudent. Keeping at least "one eye" on your digital security is highly recommended.
I hope this will be of some help to you dear reader.
Closing
Just this morning, I was writing to my good Steemian friend, @insight-out, about writing whatever is on your heart. "Practicing what I preach" I have long written on a number of topics on the Steem blockchain. And organized them into what I typically refer to as "series."
So ... Here you have my latest contribution to my "technical aide" series. I’d love to hear any feedback you may be inspired to provide.
Until "next time," all the best to you for an even better tomorrow, as we all work together to build our Steem Community! 👍 😊
Respectfully,
Steemian @roleerob
Posted using SteemPeak and “immutably enshrined in the blockchain” on Thursday, 21 March 2019!
P.S. If anyone reading this would have any tips for me on better tags / channels to use for posts like this one, I would be very appreciative of any help provided!

Interested to read more of my “technical aide” posts? Great!
- Welcome to the Steemisphere! Getting Off to a "Flying Start," Version 1.0 – Covers the full spectrum of what a new Steemian needs to know to get off to a “flying start.”
- User's Guide to the Steemisphere, Version 1.0 – Covers the recommended apps and tools a new Steemian needs as they begin to engage with our Steem blockchain.
- Tech Aide: Investing in the Steem Blockchain on Binance and Bittrex - Covers investing in STEEM and SBD on these popular exchanges.
Very well written, and a great informative article, @roleerob ! I think a lot of people would benefit from reading this, for sure. In this age, it can be hard to know what to do and how to do it, specially when it comes down to being secure and safe electronically.... A great resource of a post, for sure <3
Coming from one of our faithful Steem curators @veryspider ...
... that means a lot. Thank you! 😊
Great stuff! I would have stopped at the Windows warning unless the instructions said differently! I have become somewhat paranoid of all these things given everything we read so much this is a great piece of information I will probably be using. These sort of things are what often holds me back from using other wallets and software.
Posted using Partiko iOS
Glad to know @newageinv ...
... my post might be of value to you. You definitely don't want to be leaving any of your digital assets on a centralized exchange, so getting comfortable with taking this step is vital to your portfolio's ultimate safety.
As well, I personally believe this is also one of the keys to long term profitability. When investing in these digital assets becomes as simple and as common as buying shares in a company through your broker, I will not be surprised if the profit making potential doesn't drop considerably.
In other words, getting over these technical challenge hurdles is part of making more money. If the potential of this asset class is ever fully realized ... 😉
P.S. While I didn't put it in this post, the particular asset wallet detailed in my post here is backed by my Ledger Nano S, which greatly increases security ... 👍
Dear @roleerob
Another great piece.
I found it quite ironic that more we are connected with each other, less trust there is between us. Didn't you ever think about it? Im sure you did :)
To difficult for not-native english speaker (like myself) to understand ...
I lost you half way through your post... but I tried :)
Cheers, Piotr
Yes @crypto.piotr ...
... it is ironic. And ... Yes, I have ... 😉 Mankind has a tendency to attribute far more to technological advancement than it should. Problems with human nature are unchanged and ancient ...
Speaking of which ...
Eternal is forever ... Vigilance is carefully watching out all the time, for danger ... Gotta keep watch for the "bad guys" ...
And liberty! Liberty is a great word. One I prefer to freedom. I wrote one of my first posts about what I learned from a great man:
For English not being your native tongue, I think you do quite well @crypto.piotr! Hope this helps with the interpretation a little bit ... 😊
This post was shared in the Curation Collective Discord community for curators, and upvoted and resteemed by the @c-squared community account after manual review.
@c-squared runs a community witness. Please consider using one of your witness votes on us here
Thank you very much @c-squared, for your support. I really appreciate it!
Hi @roleerob!
Your post was upvoted by @steem-ua, new Steem dApp, using UserAuthority for algorithmic post curation!
Your UA account score is currently 4.111 which ranks you at #3386 across all Steem accounts.
Your rank has improved 35 places in the last three days (old rank 3421).
In our last Algorithmic Curation Round, consisting of 226 contributions, your post is ranked at #58.
Evaluation of your UA score:
Feel free to join our @steem-ua Discord server