Bitcoin Cash / Electron Cash - Tutorial

You should upgrade to Electron Cash 3.1.2 as soon as possible, the latest release contains the full security fix for the RPC Electrum based bug which affects both Electrum for BTC and Electron-Cash for BCH. The bug was fixed in Electrum 3.0.5 and similarly in Electrum Cash 3.1.2.
This post is specifically about Bitcoin Cash, if you are not a Bitcoin Cash user, then this post is not for you. Electron-Cash is the lightweight secure python-based wallet for Bitcoin Cash (BCH).
There is a massive risk of MITM hijackings of websites, softwares and GPG keys out there, so you must be very careful when downloading new software. This bug forces many people to upgrade at the same time so, the risk of MITM hijackings is now even bigger, since potential hackers now know that all people will download new patches.
You must make sure you verify the authenticity of everything you get from the web, you can’t trust anything, in this tutorial I will show you how. This tutorial is mostly for Linux users anyway, if you don’t use Linux, then you are not secure anyway.
VERIFY ELECTRON-CASH (TINFOIL HAT VERSION)
Because you can never be paranoid enough when it comes to your hard earned money!
1) Go to the main website: https://electroncash.org , and leave that tab open!
2) Go to Wikipedia, and enter in the search bar “Bitcoin Cash”, it will show you the Bitcoin Cash website there in that article, click on that, and go to the Bitcoin Cash website from that Wikipedia article.
3) On the Bitcoin Cash website, you will see “Wallets” there at the top click on that an it will give you the list of wallets, find there the Electron Cash logo and click on that.
4) Okay, now you have 2 tabs open for the Electron Cash website, obviously it should be the same URL, but, there are sophisticated ways to craft shady links via hidden unicode characters, so you can’t trust your eye, and the HTTPS prefix alone is not safe anymore (hackers can buy HTTPS certificates too).
5) You must make sure the certificates match, so click on the “green lock icon” and click on “More Information”, you will see there the SHA256 fingerprint of the SSL certificate.
6) Make sure the certificates on the 2 tabs are the same and match this: 94:08:8C:B2:B8:35:2E:3E:42:01:F5:DD:6B:C3:C9:08:33:2A:62:CE:CD:3A:D5:3B:C7:8E:CC:25:2C:88:13:22 , issued by cPanel, Inc.
7) If they match, the website is genuine, if any of these digests don’t match, then your connection got probably hacked or at the very least glitched, then go back to step 1 and try again until they match.
8) Now grab the GPG public key there by clicking on the “Jonald Fyookball” link in the middle, it will send you to Github, click on “Raw” and then right click and save that to file.
9) Import the GPG key with gpg –import jonaldkey2.txt
10) Verify that the GPG key belongs to the developer, by checking the fingerprint, with the command gpg --fingerprint 0x4FD06489EFF1DDE1, where 0x4FD06489EFF1DDE1 is the ID of the key or 0xEFF1DDE1 the shortened version.
You can also check it via GUI if you have Seahorse installed on Linux, in that case just open Seahorse and check the key you just imported.
- The fingerprint should be this
D56C 110F 4555 F371 AEEF CB25 4FD0 6489 EFF1 DDE1(notice there is usually a secondary subkey there too, ignore that!) - Also cross verify the above fingerprint with the one on this website
- Also I have asked the developer to confirm that this key belongs to him, and yes it does:
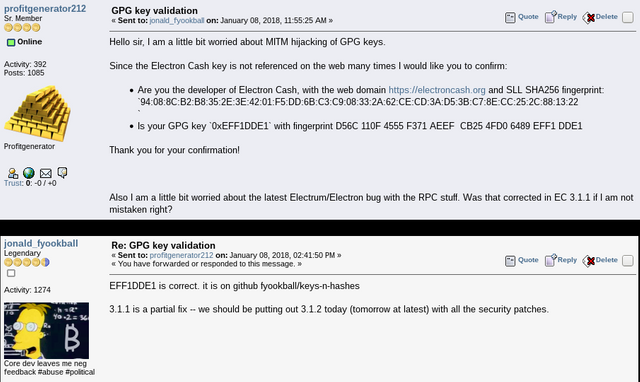
- So make sure the GPG fingerprints on the 3 sources above match yours, this should be proof beyond reasonable doubt that:
- The key belongs to the Electron-Cash developer
- The key has been retrieved correctly without MITM attack happening
11) Retrieve the 3.1.2 Electron Cash Source Code (Linux) from the website, together with the signature files and checksums below it. Now you can go to greater extents to verify these too, but it’s not necessary, if the public key is genuine then any mismatch can be detected against that.
12) Verify the downloaded Source Code: gpg --verify ElectronCash-3.1.2.tar.gz.sig (where both the signature file and the source code should be in the same folder). It should give out a “Good Signature” output, and the correct fingerprint that we checked above.
13) Optionally should can do a sha256sum ElectronCash-3.1.2.tar.gz on the Source code and check that against the checksum c355e0edb9d2253ce9b87c50c83412b10b84f7fefafd06c9907a0ab69c2404a2, if it matches, then it’s all good!
14) If all is good then your software has now been verified and it’s genuine. This doesn’t mean that it’s perfect, it can still have future bugs in it, however, it is genuine at least and no hijacking has happened. If you detected mismatches along the way, no need to panic, it could just be a memory glitch or a faulty download, although if you have reason to believe that MITM attacks could be done against you, then you should be extra careful, and redo the verification, possibly from a different IP address, or by using a VPN.
15) Now you can run Electron-Cash safely, you can either install it via sudo python3 setup.py install from the main folder or just run it as portable by entering ./electron-cash in the console.
Sources:
https://pixabay.com
https://www.pexels.com

okay post the best,,,,
upvote back yes my friend