Lebanese crypto-currencies stolen Users - sms attack

● The attacks were isolated to Touch users and happened over a specific period of time.
● More than $30K worth of cryptocurrency has been stolen
● The attack is most probably targeting Touch’s SS7 firewall
What is going on?
On Sunday, October 26th, while the Lebanese revolutionary protests were raging a number of Touch users took to twitter and WhatsApp groups to convey that they were the victims of active SIM swapping attacks.
SIM swapping attacks (also known as SIM hijacking attacks) are identity theft attacks in which malicious actors get control of a target’s mobile phone number by convincing mobile phone service providers to swap the phone number to a SIM card controlled by the attackers via social engineering or with someone from inside the telecom provider.
What is being hacked into?
Most probable scenario was:
Signalling System No 7 (SS7), which is called Common Channel Signalling System 7 (CCSS7) in the US or Common Channel Interoffice Signaling 7 (CCIS7) in the UK.
The SS7 is a very old system that was invented in 2917 which is used to connect one mobile phone network to another. Most telecom networks accross the world are regularly updating to the newer Diameter protocol which is much more secure. It does not seem that touch made that update.
What does SS7 normally do?
SS7 is a set of protocols allowing phone networks to exchange the information needed for passing calls and text messages between each other and to ensure correct billing. It also allows users on one network to roam on another, such as when traveling in a foreign country.
What can access to SS7 enable hackers to do?
Once they have access to the SS7 system, all a hacker needs is an individual’s phone number and can essentially have access to the same amount of information and snooping capabilities as security services.
In more technical terms, since the SS7 firewall provides authentication IDs for every SIM card on the network (besides the phone number) called the IMEI. When a number is sending or receiving a transmission like an SMS the attacker can make spoof or mimic this authentication.
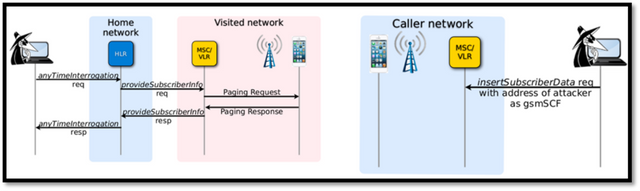
With access to the SS7 the attackers can transparently change the location of phone number without authentication from the central server as scene in the figure above. In lamen terms they can get access to the phone number’s transmission from anywhere in the world. This also enables them to forward calls, giving them the ability to record or listen in to them. They can also read SMS messages sent between phones, and track the location of a phone using the same system that the phone networks use to help keep a constant service available and deliver phone calls, texts, and data.
Who is affected by the vulnerability?
Should a hacker gain entry to the SS7 system on any number of networks, or if they are used by a law enforcement agency as part of its surveillance, anyone with a Touch SIM card on their phones could be vulnerable.
The risk of surveillance of your average user, given the millions of mobile phone users across that use Touch, is small. Those in a place of power, within organizations or government, could be at risk of targeting, as all that’s required to perform the surveillance is access to the SS7 system and a phone number.
One of the biggest dangers, beyond someone listening to calls and reading text messages, is the interception of two-step verification codes that are often used as a security measure when logging into email accounts or other services sent via text message.
As shown in one of the victim’s email notifications, a number of attempted sign-ins were originating from 146.185.34.241 which is a static IP for Touch’s network.
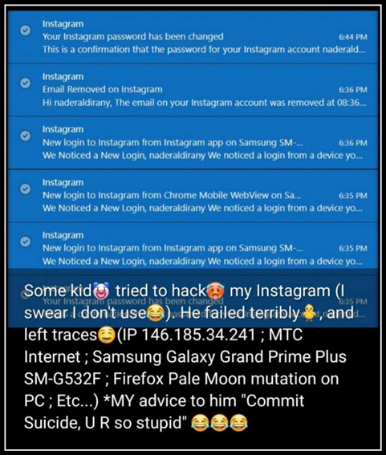
As per talks on Lebanese whatsapp groups there are supposedly more than $30K worth in unverified amounts of cryptocurrency was stolen from the attack until now.
Two individuals with Touch SIM cards lost their cryptocurrency funds up on popular online wallets and crypto-exchanges. The two individuals were active on the Lebanese cryptocurrency group Atomic Swap. Which explains how the attacker was able to establish that they own digital assets. All the attackers had to do after that is place their phone numbers on a caller identification application like True Caller to receive full names and move on from that to acquiring their Gmail and other account names.
As the victims secured their accounts with SMS, the attackers purportedly reset the password on online accounts and/or request two-factor authentication (2FA) codes that allowed them to bypass security measures. After gaining access to the crypto wallet accounts the thieves were able to quickly sent the funds to other addresses.
A cybersecurity expert and an admin on Atomic Swap attempted to reach out to Touch via email conveying a number of IPs that belonged to attackers, to get an explanation of the situation.
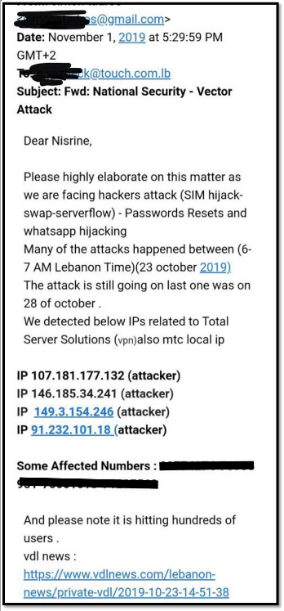
Up until now, there is no response from Touch. However, the expert explained that it’s pretty clear that there can be two possibilities the hijackers could have infiltrated the Touch SMS server: The first is a vulnerability inside Touch’s internal network, and the second could be Touch’s third part data clearinghouse, EDCH, based out of the UAE.
An undisclosed IT source in Touch has confirmed that Touch is still using the old SS7 protocol and has not upgraded to a more secure Diameter Protocol to secure communications on its network.
In all cases, if Touch’s SMS service has been compromised then this, in turn, makes this a national security issue, which could affect politicians, journalists, and major influences. Not to mention that the information acquired from accessing millions of SIM cards could be hoarded and sold to the highest bidder on the dark web.
A Victim During The Attack - His Telegram Under the SMS Login Take-Over while his line not able to register on network :)
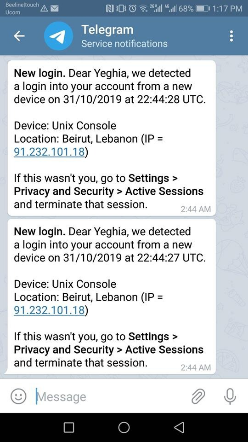
The End!
Congratulations @aro.steem! You have completed the following achievement on the Steem blockchain and have been rewarded with new badge(s) :
You can view your badges on your Steem Board and compare to others on the Steem Ranking
If you no longer want to receive notifications, reply to this comment with the word
STOPTo support your work, I also upvoted your post!
Do not miss the last post from @steemitboard:
thank you!