pfSense 2.4.3 Setup Guide
How to Setup pfSense 2.4.3
Step 1: Login to your pfSense router.
Step 2: Decide which gateway you would like to connect to, and obtain its hostname. You can find a list of all of our region hostnames available on our network page.
Click on any location to determine the available servers.
Step 3:
Determine the certificate for the encryption cipher you would like to use. At the moment we recommend AES-GCM over AES-CBC.
Step 4:
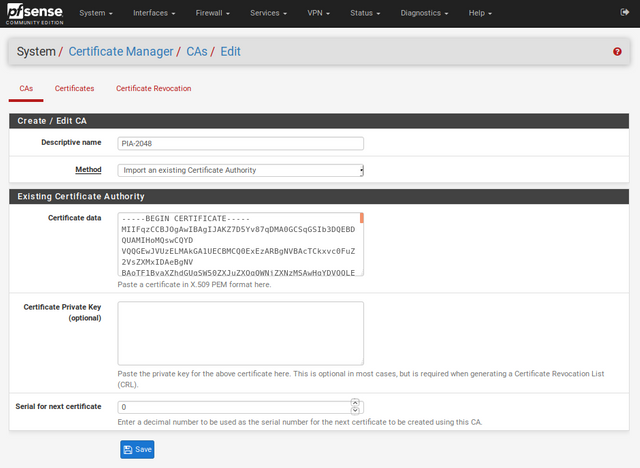
Import the Certificate Authority for the encryption cipher you would like to use. You can find all of our certificates, including their corresponding encryption ciphers and ports, available here.
In this guide, we'll be setting up pfSense to use the AES-128-GCM encryption cipher, so we're going to import ca.rsa.2048.crt.
Navigate to System>Cert.Manager and select Add. Enter a name into the Descriptive name field, such as PIA-2048.
Leave the Method as "Import an existing Certificate Authority".
Download the certificate and open it in a text editor. Copy the entire contents of the file into the Certificate data field.
Then, press Save.
Step 5: Navigate to VPN>OpenVPN>Clients and select Add.
Enter the following settings:
General Information
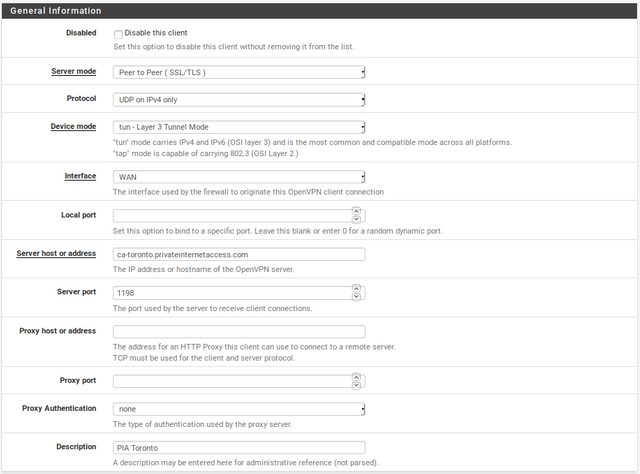
Disable this client: leave unchecked.
Server mode: Peer to Peer (SSL/TLS)
Protocol: UDP on IPv4 only
Device mode: tun – Layer 3 Tunnel Mode
Interface: WAN
Local port: leave blank
Server host or address: The hostname for the region you picked out on our network page
Server port: 1198
Proxy host or address: Leave blank
Proxy port: Leave blank
Authentication method: None
Description: Whatever you would like to title your connection profile
User Authentication Settings
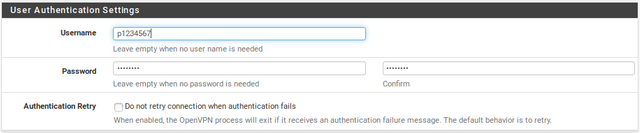
Username: Your PIA username
Password: Your PIA password in both fields.
Authentication Retry: Leave unchecked
Cryptographic Settings
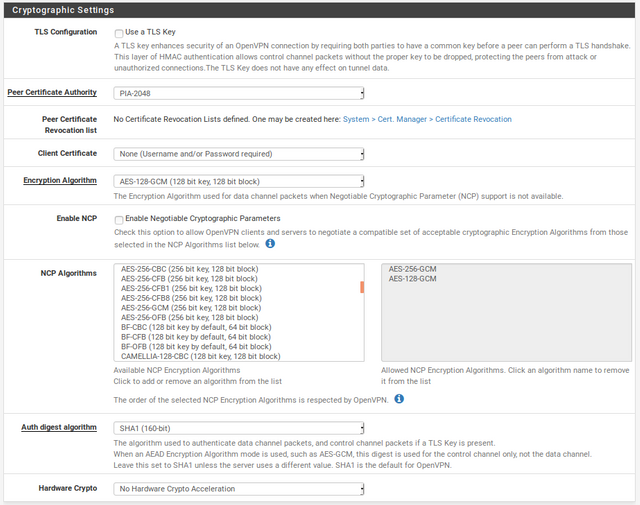
TLS Configuration: Unchecked
Peer Certificate Authority: PIA-2048
Peer Certificate Revocation list: Leave undefined
Client Certificate: None
Encryption Algorithm: AES-128-GCM
Enable NCP: Leave unchecked
NCP Algorithms: None
Auth digest algorithm: SHA1
Hardware Crypto: No Hardware Crypto Acceleration
Tunnel Settings
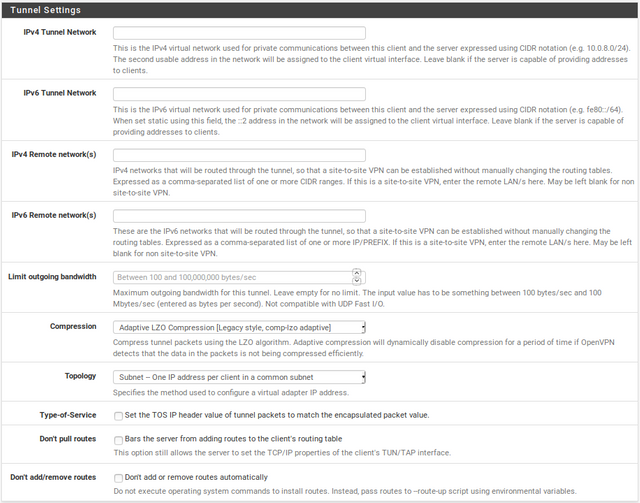
IPv4 Tunnel Network: Leave blank
IPv6 Tunnel Network: Leave blank
IPv4 Remote network(s):Leave blank
IPv6 Remote network(s): Leave blank
Limit outgoing bandwidth: Leave blank
Compression: None
Topology: Subnet -- One IP address per client in a common subnet
Type-of-service: Unchecked
Don't pull routes: Unchecked
Don't add/remove routes: Unchecked
Advanced Configuration
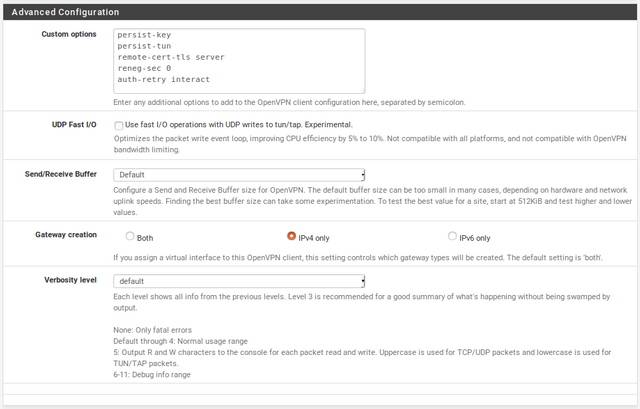
Custom options:
persist-key
persist-tun
remote-cert-tls server
reneg-sec 0
auth-retry interact
copyUDP Fast I/O: Unchecked
Send/Receive Buffer: Default
Gateway creation: IPv4 only
Verbosity level: Default
Then, click Save.
Step 6.
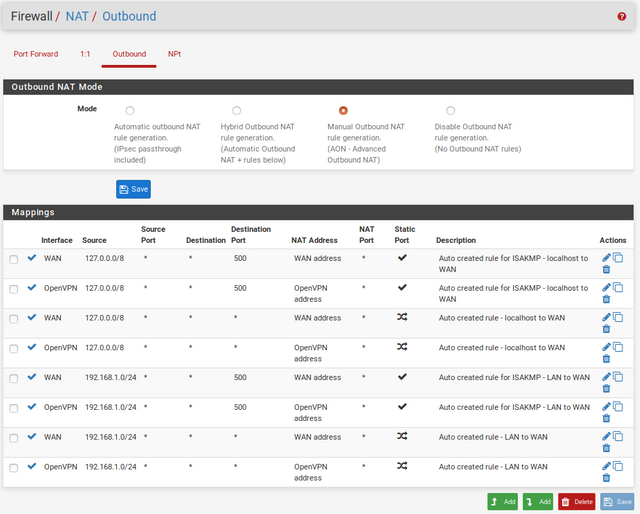
Navigate to Firewall>NAT>Outbound, and select Manual Outbound NAT rule generation. You should see 4 rules.
Under the Actions heading, you should see an icon that looks like two pages, called Add a new mapping based on this one. Duplicate each of the 4 rules exactly, but change their interface to OpenVPN, clicking Save after each rule is duplicated.
Step 7:
Navigate to System > General Setup and set DNS Servers to:
209.222.18.222
209.222.18.218
Step 8:
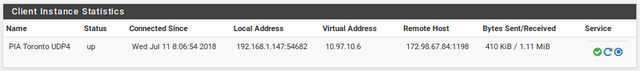
Verify your connection. Navigate to Status>OpenVPN and check to see whether your OpenVPN client is up.
Finally, visit What's My IP to verify that you are protected.
Posted from my blog with SteemPress : https://undergroundmod.com/2020/03/07/pfsense-2-4-3-setup-guide/