Things To Know About IoT Security
We are currently witnessing a growing number of IoT deployments and solutions around the world.
IoT security is emerging as a key component of these deployments and companies are recognizing they need to get it right from the beginning – By 2022, the IoT security market is forecast to reach $4.4 billion. Various industry surveys , as well as our own research, indicate cybersecurity is the #1 concern for industrial IoT users today.
IoT Security spending is rapidly increasing:

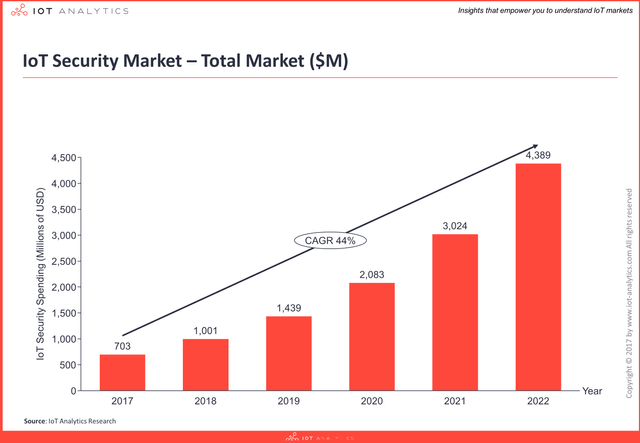
Global spending end-users of 3rd party security solutions is currently estimated at $703M for 2017 and is forecast to grow at a CAGR of 44% to become a $4.4B market by 2022, driven by new regulation and increasing IoT adoption.
In addition to the security tools provided by IoT platforms (which is not part of this figure) the IoT security market is an aggregation of innovative startups and established firms such as global chip manufacturers, infrastructure providers, as well as cloud and enterprise software companies. There are at least 150 independent IoT security vendors addressing the challenges across all industries – of which Industrial/Manufacturing is the biggest segment for IoT security.
Example: A large auto OEM we talked to recently performed an assessment of factory vulnerabilities and concluded that there were significant gaps in today’s infrastructure. They expect to increase related spending significantly.
IoT introduces an increased number of security threats
![Cybersecurity-Risks-Small.png]
( )
)
IoT security happens on 4 different layers
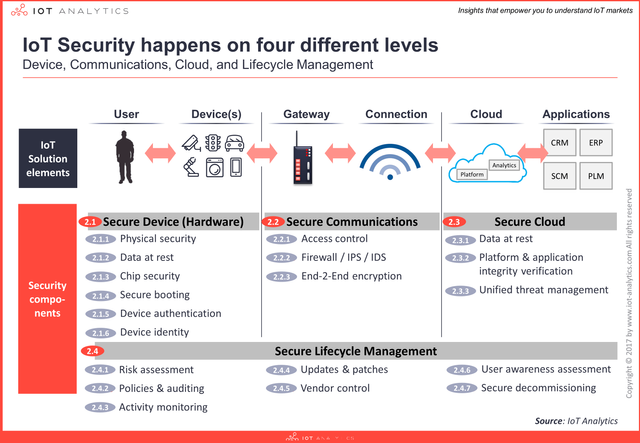
IoT solution architectures require multi-layered security approaches that seamlessly work together to provide complete end-to-end security from device to cloud and everything in between throughout the lifecycle of the solution. The 4 layers consist of:
Device: The device layer refers to the hardware level of the IoT solution i.e., the physical “thing” or product. ODMs and OEMs (who design and produce devices) are increasingly integrating more security features in both their hardware and software (that is running on the device) to enhance the level of security on the device layer. Security components include: physical security, data at rest, chip security, secure boot, device authentication and device identity.
Communication: The communication layer refers to the connectivity networks of the IoT solution i.e., mediums over which the data is securely transmitted/received. Whether sensitive data is in transit over the physical layer (e.g., WiFi, 802.15.4 or Ethernet), networking layer (e.g, IPv6, Modbus or OPC-UA), or application layer (e.g., MQTT, CoAP or web-sockets) unsecure communication channels can be susceptible to intrusions such as man-in-the-middle attacks. Security components include: access control, firewall, IPS, IDS, and end-to-end encryption.
Cloud: The cloud layer refers to the software backend of the IoT solution i.e., where data from devices is ingested, analysed and interpreted at scale to generate insights and perform actions. IoT cloud providers are expected to deliver secure and efficient cloud services by default to protect from major data breaches or solution downtime issues. Security components include: data at rest, platform and application integrity verification.
Lifecycle management: Secure Lifecycle Management refers to an overarching layer with continuous processes required to keep the security of an IoT solution up-to-date i.e., ensuring sufficient security levels are in place from device manufacture, initial installation to the disposal of things. Security components include: risk assessment, policies & auditing, activity monitoring, updates & patches, vendor control, user awareness assessment, and secure decommissioning.
One should also note, at this point (Q4/2017) there is no single IoT security vendor that can provide the complete end-to-end out-of-the-box security solution. However, some companies offer more than others and together with their partner ecosystem some can provide a complete end-to-end IoT security solution.
Increasing automation of IoT security tasks
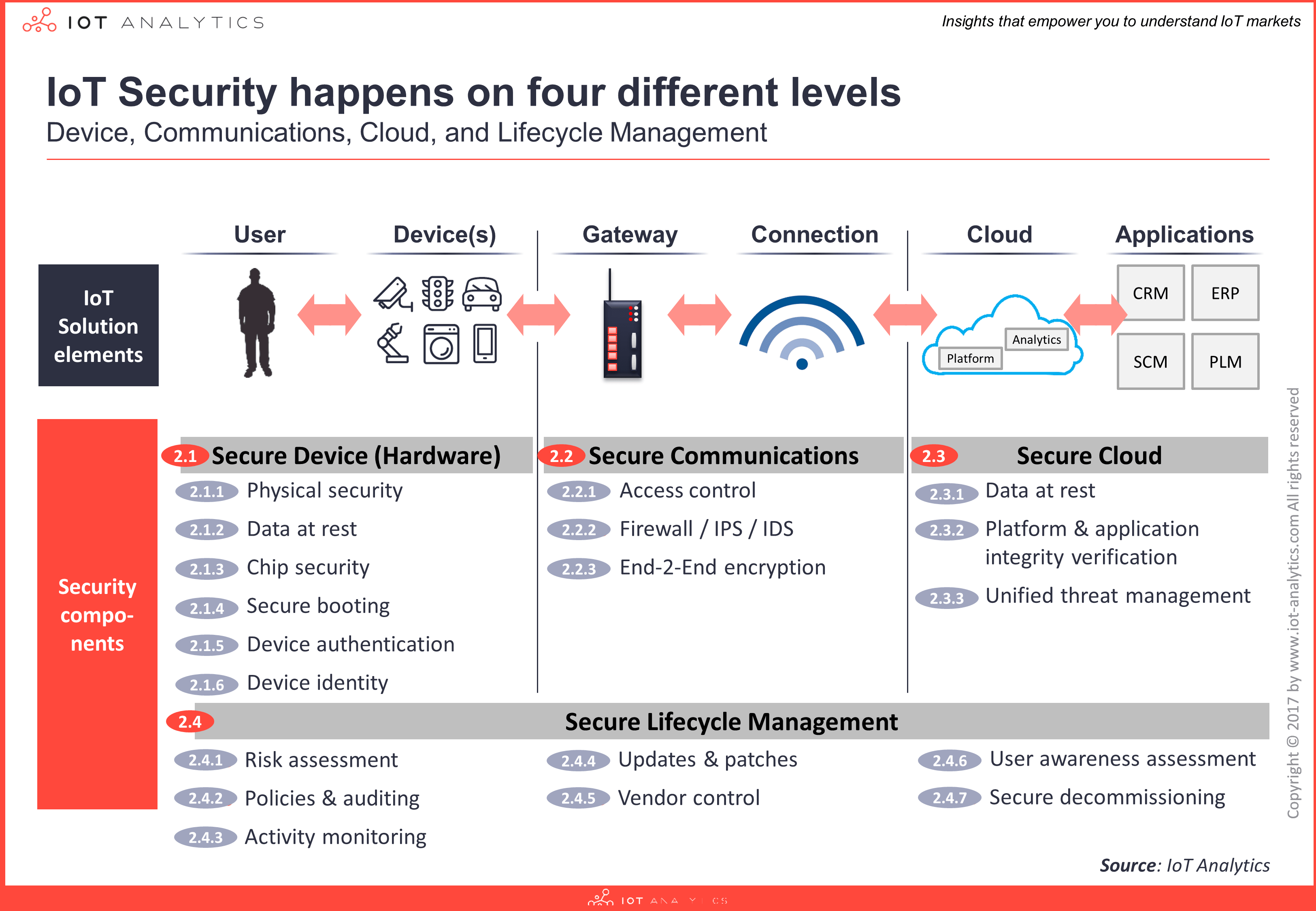

IoT solution architectures require multi-layered security approaches that seamlessly work together to provide complete end-to-end security from device to cloud and everything in between throughout the lifecycle of the solution. The 4 layers consist of:
Device: The device layer refers to the hardware level of the IoT solution i.e., the physical “thing” or product. ODMs and OEMs (who design and produce devices) are increasingly integrating more security features in both their hardware and software (that is running on the device) to enhance the level of security on the device layer. Security components include: physical security, data at rest, chip security, secure boot, device authentication and device identity.
Communication: The communication layer refers to the connectivity networks of the IoT solution i.e., mediums over which the data is securely transmitted/received. Whether sensitive data is in transit over the physical layer (e.g., WiFi, 802.15.4 or Ethernet), networking layer (e.g, IPv6, Modbus or OPC-UA), or application layer (e.g., MQTT, CoAP or web-sockets) unsecure communication channels can be susceptible to intrusions such as man-in-the-middle attacks. Security components include: access control, firewall, IPS, IDS, and end-to-end encryption.
Cloud: The cloud layer refers to the software backend of the IoT solution i.e., where data from devices is ingested, analysed and interpreted at scale to generate insights and perform actions. IoT cloud providers are expected to deliver secure and efficient cloud services by default to protect from major data breaches or solution downtime issues. Security components include: data at rest, platform and application integrity verification.
Lifecycle management: Secure Lifecycle Management refers to an overarching layer with continuous processes required to keep the security of an IoT solution up-to-date i.e., ensuring sufficient security levels are in place from device manufacture, initial installation to the disposal of things. Security components include: risk assessment, policies & auditing, activity monitoring, updates & patches, vendor control, user awareness assessment, and secure decommissioning.
One should also note, at this point (Q4/2017) there is no single IoT security vendor that can provide the complete end-to-end out-of-the-box security solution. However, some companies offer more than others and together with their partner ecosystem some can provide a complete end-to-end IoT security solution.