One Plugin, Over 4,200 Victims – When Thousands of Government Websites Were Hijacked to Mine Monero

Thousands of websites around the world were targeted by cryptojackers over the weekend to mine Monero. The targets included websites run by the US and UK governments that were secretly hijacked by attackers to mine cryptocurrency using a compromised plugin, Browsealoud.
Over 4,200 websites are in the victims list [link], including The City University of New York, the US court information portal (uscourts.gov), Lund University, the privacy watchdog The Information Commissioner’s Office (ICO), and several other government, health and educational websites across the world.
“This was a very serious breach. They could have extracted personal data, stolen information or installed malware. It was only limited by the hackers’ imaginations,” security researcher.
This plugin developed by a British firm is used to read out websites for people with visual impairments. It is unclear whether it was an employee who thought it was a good idea to stealthily make some money using client websites (wouldn’t be the first time this has happened; Wccftech itself became a victim last year by a different company), or if an attacker managed to compromise it before hijacking websites.
Initial report by the Register suggested that the attack went on for several hours as Browsealoud inadvertently ran a mining code on the computers of those visiting these 4,000+ websites, generating money for attackers. The Coinhive mining script was added to the plugin’s code some time between 0300 and 1145 UTC.
Security experts recommend websites to try SRI to protect against attackers hijacking their sites to mine cryptocurrency
While most antivirus and adblockers have now started to block Coinhive, attackers still manage to make millions from mass-targeting websites proving that many remain at risk. Security researchers are now advising websites to take some action, especially government websites like the ICO. “The sheer number of sites affected by this is huge and some of them are really prominent government websites!” security researcher Scott Helme wrote.
“If you want to load a crypto miner on 1,000+ websites you don’t attack 1,000+ websites, you attack the 1 website that they all load content from.”
However, while CDNs and other hosted assets remain vulnerable, Helme says it’s actually “pretty easy to defend yourself against this attack.” How? By adding SRI Integrity Attribute that allows the browser to determine if the file has been modified, in which case it will simply reject the file.
Let’s take the ICO as an example, they load the affected file like this:
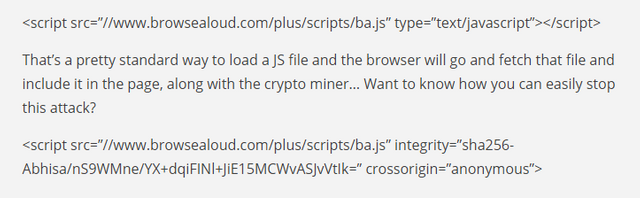
As for the plugin maker is concerned, Texthelp (the company behind Browsealoud) wrote that it does have automated security tests in place, which “detected the modified file and as a result the product was taken offline.” However, in the meantime, thousands of sites were affected for hours. The company assured that “no customer data has been accessed or lost,” promising to update its clients after further investigation which will be carried out by an independent firm.
Rafia Shaikh
https://wccftech.com/government-websites-hijacked-mine-monero/
Your Post Has Been Featured on @Resteemable!
Feature any Steemit post using resteemit.com!
How It Works:
1. Take Any Steemit URL
2. Erase
https://3. Type
reGet Featured Instantly � Featured Posts are voted every 2.4hrs
Join the Curation Team Here | Vote Resteemable for Witness