Cyber Security and Maritime Industry : Securing the vessels, ports and sea
Cyber Threat is considered to be one of the most serious economic and national security challenge. Studies and security incidents prove that the maritime industry is facing major security risks. As more and more onboard systems are connected online, it gives hackers an opportunity to gain access to navigation system, steering, cargo handling systems by installing malware or viruses that could infect these system. We will be discussing about these cyber threats and incidents related to the shipping industry.
Maritime transport or shipment of people and goods by sea is one of the most ancient and widely used forms of transport known to man. As the maritime and offshore energy industries connect ships and oil rigs to computer networks, they expose considerable weaknesses that hackers can exploit. It was discovered that pirates of the coast of Somalia and other key piracy areas hand pick their shipping targets by tracking online the navigation track of the vessel through AIS (Automatic Identification System), ECDIS (Electronic Chart Display and Identification System) and radar.
“Cyber-security remains a significant threat for ports around the world as levels of automation increase and hackers methods also improve” says security consultancy, CyberKeel. “These intrusions and attacks are taking place every minute and every second of every day. The threat is very real” Rear Admiral. Marshall Lytle, assistant commandant responsible for U.S. Coast Guard Cyber Command said. Modern ships are completely computerized. Everything is connected on networks.
How are Information Systems used on Shipping vessels ?
Cyber threats in the shipping industry is a major concern. With the advancement of technology, ship and cargo operations use Information System for communication and monitoring. Let us discuss about the types of Vessel Information systems, its usage, security concerns and the lessons learned.
Vessel Navigation System
The vessel location and navigation systems are mobile information platforms, which integrate GPS, GIS and wireless communication to offer extensive data such as location, speed and status of a ship in real time mode. This data is processed and the location and moving track of the ship can be shown on digital maps.
GNSS or Global Navigation Satellite Systems have been used in the maritime environment since the late 1960's as the TRANSIT system, which was used mainly by the US Navy. Today, GPS is used as the primary mechanism for navigation in the maritime sector. GPS system gives you accurate positions and it has now become easier to find out if the vessel is deviating from its course.
GPS Hacking
During 2013, Security experts from University of Texas managed to hack the GPS of a yacht in the Mediterranean and bring it off its programmed course. The experiment was carried out using homemade GPS spoofing device small enough to be concealed in a suitcase. By turning up the signal on the spoofing device until it was stronger than the signal coming from the GPS satellites overhead, the researcher was able to gain control of the vessel's navigation systems. From there on, it was plain sailing for the "attacker." By posting a change of direction signal, even by just three degrees, the ship's crew are alerted that the ship is drifting off course—erroneously. The crew correct the navigation system, thereby altering the correct course to one that really is three degrees off course.
Lesson Learned: The above experiment was performed with nothing more than a small antenna, a laptop, $3,000 device known as a GPS “spoofer” and some basic hacking knowledge. The solution to this issue includes the implementation of the military level P(Y) code encryption. This would be expensive on the receiving end and put a heavy burden on the satellite networks
Satellite communication system
These satellites are designed specifically for maritime industry to provide extensive coverage of world’s ocean region. They provide real-time communication for ships and cargo surveillance, vessel monitoring, voice, video and data services for ship-to-shore connectivity.
Common services include voice calling, data services for satellite email and Internet Access, and weather and oceanographic data access for navigation and fishing. Many vessels also use satellite vessel tracking services in order to keep shoreside operations apprised of their location. Many vessels are now deploying (Voice over IP) satellite VoIP services to take advantage of the lower data rates. This solution requires using VoIP service that is specifically designed for satellite.
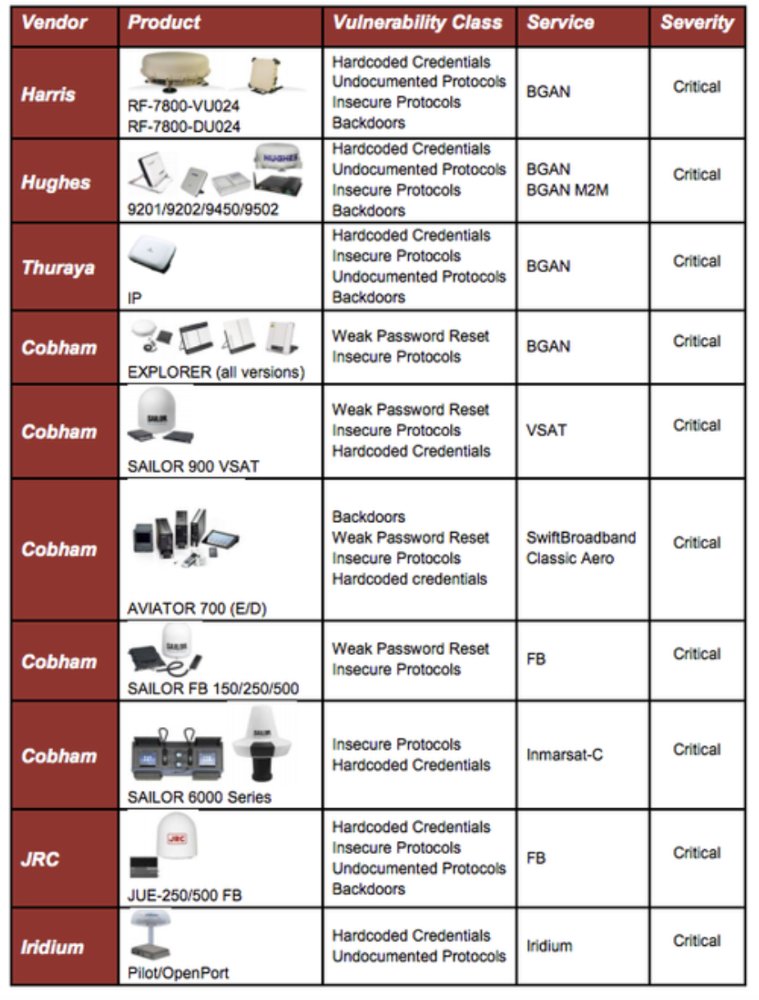
During 2014, Security researchers have found that many satellite communication systems have vulnerabilities and design flaws that can let remote attackers intercept, manipulate, block and in some cases take full control of critical communications. The IOActive researchers said "We uncovered what would appear to be multiple backdoors, hardcoded credentials, undocumented and/or insecure protocols, and weak encryption algorithms.” These vulnerabilities were identified in the firmware of popular satellite communications (SATCOM) devices. These vulnerabilities allow remote, unauthenticated attackers to compromise the affected products. In some cases, an attacker need only send an SMS text message to launch an attack. “You could attack one of these devices with SMS, and trigger features to install new firmware or to compromise it," says Ruben Santamarta, principal security consultant for IOActive, who discovered the security flaws last fall and published a report on his findings today. An SMS from one ship to another could compromise some satellite communications, the report says.
Dan Kaminsky, co-founder and chief scientist at White Ops, says the IOActive findings demonstrate how hacking has evolved and satellite technologies have not kept up.
Lesson learned: Regularly perform penetration test to identify vulnerabilities in the satellite communication system and devices. Hardcoded credentials and weak password management were the major findings as per the above analysis. Organizations must consider addressing such issues since the severity is critical.
Automatic Identification System (AIS)
The Automatic Identification System (AIS) is an automatic tracking system used on ships and by vessel traffic services (VTS) for identifying and locating vessels by electronically exchanging data with other nearby ships, AIS base stations, and satellites. When satellites are used to detect AIS signatures then the term Satellite-AIS (S-AIS) is used. AIS information supplements marine radar, which continues to be the primary method of collision avoidance for water transport. AIS works by acquiring GPS coordinates and exchanging a vessel’s position, course and information with nearby ships and offshore installations.

A study by TrendMicro discovered flaws in the AIS system which can allow attackers to hijack communications of existing vessels, create fake vessels, trigger false collision alerts and even permanently disable AIS tracking on any vessel. Due to the unauthenticated and unencrypted nature of AIS, TrendMicro researchers showed that AIS is vulnerable to different threats like spoofing, hijacking and availability disruption. These threats affect both the implementation in online providers and the protocol specification, which make the problems relevant to all transponder installations (estimated at 300,000+).
Lesson learned: The above study highlighted that AIS protocol was designed with zero security considerations. The AIS protocol must implement Validity checks, authentication and integrity checks. Fixing the flaws in AIS is not trivial, as they exist right down to the core of the protocol. Even if the AIS internet providers altered their sites, the underlying protocol is still open to lots of abuse. At a minimum, a new version of AIS would need to incorporate defenses for the three core issues outlined: validity, authentication and encryption.
Vessel Traffic Management Service (VTMS)
Similar to air traffic control systems, a VTMS is a marine traffic monitoring system established by port authorities to ensure smooth operation of vessels. A standard VTMS deploys a combination of radar, close circuit television cameras and AIS to track vessel movements and ensure navigational safety in a particular geographical area. The system presents real-time navigational data overlaid on an electronic chart system display. "For the purpose of vessel traffic management, GIS is used for shore-based management of vessel traffic flow. For example, the monitoring of keeping an allocated tidal window of a ship is realised by means of supporting display functions integrated into the GIS," explains Dr Michael Baldauf from World Maritime University.
A recent report by CyberKeel shows that 37% of maritime web servers running Microsoft were not patched and thereby open to remote control risk. According to CyberKeel vulnerable sites included three major container line and systems at a number of ports, such as the vessel traffic management system in Gothenburg, the road haulier identity system in Felixstowe and the main site of the Copenhagen port authority. CyberKeel CEO Lars Jensen tells that organizations must instruct IT departments to quickly install software patches since hackers communities operate on decidedly short timeframes. Everything is connected on cyberspace and modern cargo operation and ship operation are completely computerized and functions through automation.
Lessons learned: Identifying and installing the latest security patches on servers.
Electronic Chart Display and Identification System (ECDIS)
An ECDIS system displays the information from electronic navigational charts (ENC) or Digital Nautical Charts (DNC) and integrates position information from position, heading and speed through water reference systems and optionally other navigational sensors. Other sensors which could interface with an ECDIS are radar, automatic identification systems (AIS), and depth sounders.
It is thought that ECDIS has some underlying software security vulnerabilities that could lead to disastrous results for ships at sea. The basis of ECDIS is a navigation based charting system that use a computing system to digitally display nautical charts along with the exact location and track of own ship. This is a dramatic alternative and improvement to paper charts and the current system of hand plotting positions. ECDIS’s are installed on the bridge of a vessel and larger vessels are required to have two of them, one as a backup. When they are properly used with an ENC chart they can take the place of paper nautical charts. This is an increasing trend in the maritime industry.
Where the problems arise is not when the ECDIS’s are in standalone mode but when they are networked together and when data is downloaded via an external source, whether through a USB port via a memory stick or via the net.
Lesson learned: Restricting portable media and implementing antivirus software
Marine Radar systems
Radar is a vital component for safety at sea and near the shore. Captains need to be able to maneuver theirs ships within feet in the worst of conditions and to be able to navigate "blind". This means inside a dark room with no visibility they need to safely navigate their way through waters in the worst of weather. Radars are rarely used alone in a marine setting.
AIS systems supplement marine radars, which is a primary method of collision avoidance for waterborne traffic. Shipping companies these days have begun to deploy modern technologies to ensure enhanced monitoring, efficiency and security of their fleet. The newer radars have 3D displays that allows one to see above, below and all around the ship, including overlays of satellite imaging. In port or in harbour, shore-based vessel traffic service radar systems are used to monitor and regulate ship movements in busy waters.
Stop phishing in the sea
“There is the potential for a major cyber-attack on the maritime industry to significantly disrupt food and energy supplies given that shipping transports 90% of the world’s global trade. Certainly there is the possibility for AIS, GNSS (Global Navigation Satellite System), ENC (Electronic Navigation Chart) and ECDIS charts to disappear from bridge screens or be modified, but the issue today is that most adversaries want to obtain data for financial gain or criminal activities.” warns ESC Global Security’s head of cyber security division, Joseph Carson.
He says that payment systems, for example, can be easily attacked using phishing scams to raise fake invoices or even to change shipping manifests in order to transport illicit goods, drugs and weapons. Employee awareness programs can reduce such phishing scams.
Conclusion
Hackers are also reported to have breached computers connected to the Belgian port of Antwerp in order to locate a consignment of smuggled drugs, which they then made off with. Some attacks target control systems using various forms of malware, now widely available on the Dark Web. This would generally be with a view to demanding payment using ransomware. Ships which have been directed off course into unsafe waters are also vulnerable to physical attack from pirates.
Recently motherboard reported about spying on ships and cargo vessels, Ruben Santamarta, a security researcher at the well-known firm IOActive, found that a particular model of Voyage Data Recorder (VDR), the popular Furuno VR-3000, a device that’s essentially the equivalent of an aircraft’s black box, has several bugs that make it very easy for the crew to tamper with it or for a hacker to hack it remotely.
“Basically, almost the entire design should be considered insecure,” Santamarte wrote in a blog post. “Remote attackers are able to access, modify, or erase data stored on the Voyage Data Recorder, which includes voice conversations, radar images and navigation data.”
Cyber criminals will use weaknesses to obtain a financial payoff, and the main victim of such attacks is the company losing the money. However, the nature of shipping also results in a situation where cyber-attacks, even those “only” aimed at a single company, can have significant ripple effects into entire national economies.
This post was initially published on:https://www.linkedin.com/pulse/cyber-security-maritime-industry-securing-vessels-ports-ashiq-ja-
Congratulations @crypto-ja! You have completed some achievement on Steemit and have been rewarded with new badge(s) :
Click on any badge to view your own Board of Honor on SteemitBoard.
For more information about SteemitBoard, click here
If you no longer want to receive notifications, reply to this comment with the word
STOP