Hacked bitcoin hardware wallet! Method revealed inside
Trezor — security glitches reveal your private keys!
As we all know, a few weeks ago there was a presentation about Trezor “glitches cause stitches” attacks at DEFCON 25. These attacks are possible because Trezor is using non-secure chips made by STMicroelectronics. The most important question everyone should ask is:“Is the ST32F05 vulnerable to fault injection?”“Absolutely, yes!” — that’s the answer we got at DEFCON 25. So, the ST32F05 chip is really doomed.
There is absolutely nothing that Trezor can do about it. They can’t replace all existing hardware. And the really bad news is that this also applies to Keepkey and to the upcoming Trezor v2 — it also uses similar STMicroelectronics chip!A simple version of the hack revealed here also works without fault injection and is demonstrated below.Trezor so far greatly downplays the importance of this hack. There is no long-term access needed to copy all your secret information from Trezor using this hack, it can be done just in 15 seconds. If your Trezor is stolen, you don’t even have time to transfer you funds to a new address. Government authorities can access all your Bitcoins and other crypto currencies without even asking for your consent. If you are crossing an international border, TSA can easily check your balances, etc. IRL, Trezor is as safe as leaving your cash or wallet on the table. On top of all that, your Trezor can be restored to its original state or replaced with identical Trezor with the same configuration, you wouldn’t even notice any difference until it is too late.The HackThis is one of the hacks that was discovered more than six months ago. A proof-of-concept version of this hack was developed on March 29th, 2017. Since Trezor has finally provided the hot-fix for this particular hack we can also fully disclose how it works.Here we demonstrate how the hack works without even needing “fault injection”.Your seed words are never supposed to be accessible outside of the Trezor device. This should be the most well-kept secret — but it’s not! This is the only reason why Trezor should exist.Not only extracts this hack your 24-word seed but also your PIN code and Device Label! WTF!! With this information, you could make exact copy of the Trezor device!
1. We start with an empty Trezor device:

2. Let’s name it “Leak55”:
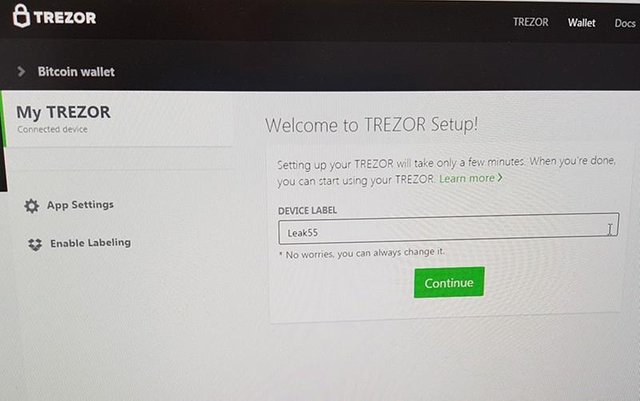
3. Usually people have 4 digit PINs. Let’s have an insane 9 digit PIN. No need to remember it anyway…
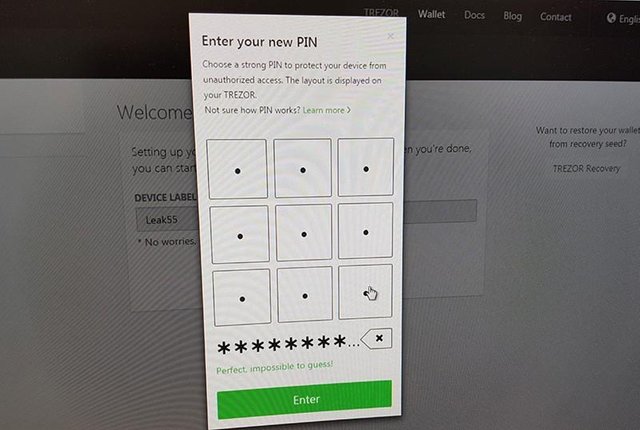
4. Now the Trezor device is ready to display us 24 words that make up the private key. We assume that these words are only kept inside the Trezor device and stored really securely...

5. OK, let’s disconnect and shut down the device

6. And now, without knowing the PIN or anything about the device, just in 15 seconds it can be hacked and all private information can be extracted! Detailed steps are described H. This is a combination vulnerabilities of both in hardware and software design that can’t be fixed without replacing the devices. After hacking, the device can be left in it’s original state, all data intact. You will never know that it was hacked!
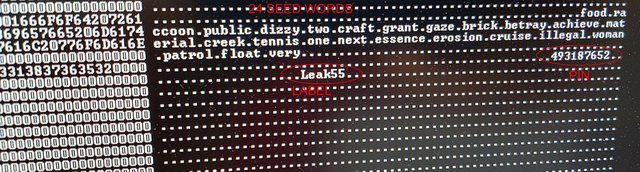
If you are performing this hack multiple times, you can make your life simpler like this:

The key to performing this hack is simply connecting two pins inside the Trezor device at the right time, even paperclip is suitable for this.Only a simple version of this hack requires the disassembly of Trezor. A more advanced version also exists. No disassembly is required!Why this hack works? As soon as you connect your Trezor to a power source such as a computer, without entering any PIN codes or opening any websites, the Trezor device firmware by itself fills the SRAM with all your sensitive secret information. How stupid is that? Even more troublesome is the fact that during the firmware update, the bootloader is doing exactly the same thing! This goes against all security best practices that we know about.Download the firmware to perform this hack from HERE.Please note that, Trezor hotfix 1.5.2 still has the following issues:1) reset_handler fix (filling memory) is not executed when you run “Frozen Trezor” attack.
2) bootloader reset_handler fix only affects new Trezors, it doesn’t do anything for the majority of existing ones.
3) Private keys & PIN are still kept in SRAM, they are still kept in unnecessarily expanded format. Why risk it?...
Congratulations @bhaskarsinha! You have completed some achievement on Steemit and have been rewarded with new badge(s) :
Click on any badge to view your own Board of Honor on SteemitBoard.
For more information about SteemitBoard, click here
If you no longer want to receive notifications, reply to this comment with the word
STOP