The uselessness of passwords (part 2)
In my previous post, I've listed all the defects of the current implementation of passwords on most websites.
In this post, I'll try to witness the current solutions for the relevant issues.
What is a password, after all ?
A pass word is supposed to be a secret that's only known to a (very) limited number of participants to authorize an action (whether it's allowing to pass a gate or displaying the account's management dialog)
Because it's secret, it must be hard to guess.
Because it's secret, the participant's count should be kept as small as feasible.
Because it allows an action, its power should be limited to that action only.
The difficulty of guessing passwords
To increase the difficulty of guessing passwords there are only few possibilities:
Limit the number of guesses.
That's exactly what your credit/SIM card's PIN is doing. The number of possible passwords is low (for a 4 digits PIN, it's only 10000 possible password), so the security only comes from the limited number of "tries". With 3 tries, you have a probability of finding the correct password of only 1/10000 * 1/9999 * 1/9998, which is very close to 10^-12.
However, this forces to store the number of (failed) tries securely (actually in your card), which is hard to do on a distributed network.
Increase the password entropy
As Randall Munroe described: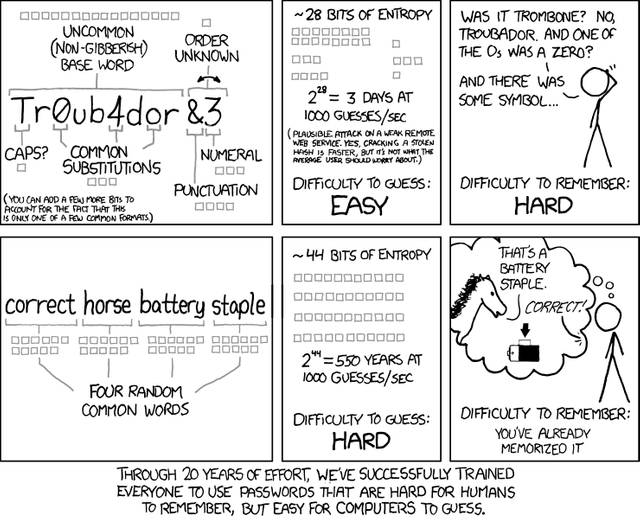
One could increase the entropy of password. However, it's just a race between the computer processing power and your brain. Said differently, if a password is hard for you to remember, it's not necessarily hard for a computer to guess.
IMHO, text-based password is just stupid.
Generating text is something that's very well supported by computing science since decades so computers perform that task like an army of ants.
For example, if a password is hashed with SHA256 (or worse SHA1), you're likely already screwed. The Bitcoin network is currently computing 17 million terahash per second (or 17*10^18). If you are using a password that's only 8 characters, the difficulty to guess requires only 66^8 = 360x10^12 tries (worst case).
This means that it would take only 1µs for the Bitcoin network to find out your password if it was required, or the Bitcoin network could "break" one million password per second if it was ordered to do so.
Obviously, the Bitcoin network is not trying to break passwords, nor does it compute PBKDF function. Yet...
The conclusion I'm drawing from this fact, one should not use text to store password.
A secret should be hard for a computer to guess, yet easy for a human to remember. Text does not fit.
Pictures could have worked in the previous 10 years but with Deep Neural Network, computers are becoming also good at recognizing / classifying items in pictures, so using some pictures for a secret could also be analyzed by a computer probably faster than a human.
The solution here lies with tasks that humans are better suited than computer to perform well and fast.
Currently, we are good at solving unstructured problems, finding a sense in a bench of data (abstraction of meaning), semantic processing like identifying irony (for most of us, I expect).
Therefore, the entropy of the secret should be "spent" in a task that's feasible for us, but not for computer.
Split the secret
Let's say I know a big secret made of many small parts. I can share some of them with someone else without breaking the complete secret.
That what your bank is probably doing when it asks you to only enter the first and fourth digit of your password to authorize a payment.
Please notice that is only secure for a limited number of guess, and this reduces the difficulties of guessing the other items.
In the next part, I'll try to introduce a solution to this problem taking advantage of all the facts listed above.
As usual, if you have any comment, feel free to comment below...
Thanks for reading.
