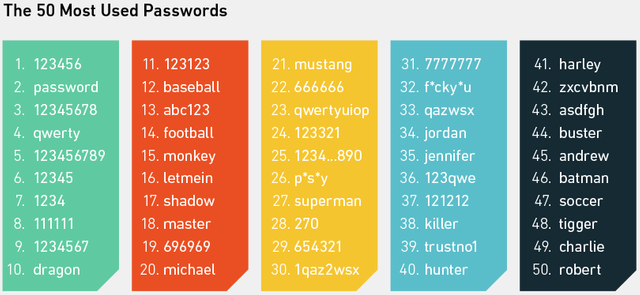
Brute-Force Attacks - Cracking Passwords with Savage Violence and How to Simply Protect Yourself

Often deemed as inelegant, brute-force attacks can be very successful. This method uses simple trial and error to solve cryptographic algorithms, which uses any possible combinations of numbers, letters, blank and special characters. Hackers as well as authorities use brute-force attacks to decode any encrypted data such as passwords, messages or DES keys.
In a recent post about the Caesar cipher we learned that each letter in the plaintext is replaced by a letter with a constant number further in the alphabet. We will use this Caesar cipher to show a very basic and simple brute-force attack.
I love to encrypt my password for Steemit encrypted with ROT3 results in F ilsb ql bkzovmq jv mxpptloq clo Pqbbjfq . The key to decipher is I. A brute-force attack will try all the keys from A to Z to receive the plaintext.
| G jmtc rm clapwnr kw nyqqumpr dmp Qrcckgr | Key: G | |
| H knud sn dmbqxos lx ozrrvnqs enq Rsddlhs | Key: H | |
| I love to encrypt my password for Steemit | Key: I | |
| Character Set | Length | Table Size |
ABCDEFGHIJKLMNOPQRSTUVWXYZ |
14 | 0.6 GB |
ABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789 |
14 | 3 GB | ABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789!@#$%^&*()-_+= |
14 | 24 GB |
ABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789!@#$%^&*()-_+=~`[]{}|:;"'<>,.?/ |
14 | 64 GB |
|
Trying coke : failed Trying yourmama : failed Trying justin: failed ... Trying letmein : failed Trying St33mit : success! |
Trying aaaa : failed Trying aaab : failed Trying aaac : failed ... Trying acdb : failed Trying acdc : success! |
How to simply protect Yourself
There are ways to secure yourself against attacks like brute-force, dictionary and rainbow tables. When it comes to choosing your password, consider the following advice:
- Use many characters: Try to increase the amount of characters you use. The more characters you use the longer it will take to break your code.
- Avoid: Short passwords like “hello”,”mynameis” etc.
- Use different characters: Use as many different characters as possible. Use digits, letters, special characters etc.
- Avoid: Don’t focus on letters only. Try to avoid the same characters in a row like: “abcabc” or “123123”
- Don’t replace letters for special characters like “Name → N@me“
- Don‘t use words from a dictionary
- Change your password periodically
- Don‘t use personal information like your name, names of friends, birthdays etc.
The more complex the password, the more time it takes to brute-force it:
| Password consists of | Possible combinations | Time to decode |
|---|---|---|
5 characters |
365= 60.466.176 |
60.466.176 / |
7 characters |
527= 1.028.071.702.528 |
1.028.071.702.528 / |
8 characters |
688= 457.163.239.653.376 |
457.163.239.653.376 / |
9 characters |
949= 572.994.802.228.616.704 |
572.994.802.228.616.704 / |
12 characters |
9412= 475.920.314.814.253.376.475.136 |
475.920.314.814.253.376.475.136 / |
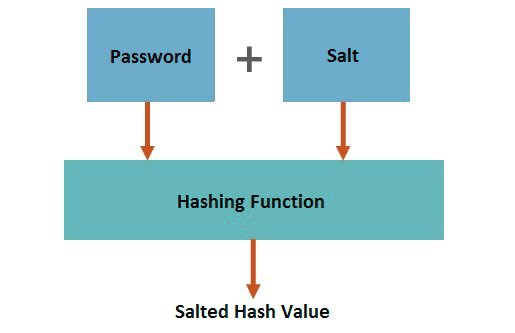
When it comes to protection against Rainbow Tables the use of Salt is recommended. Two users with the same password will have the same hash. By adding an additional string to the password before hashing we create a randomized hash. These new hashes make the use of Rainbow Tables almost impracticable. There exist Rainbow Tables with additional Salts but these tables are way too large and are not efficient enough. The salt is stored in database along with hash. When the additional string is stored desperately we speak of pepper. Combining pepper and salt is very effective.
Privacy is our right and we need to know how to protect ourselves
Recent Posts:
- The most famous Field Cipher: ADfGVX - And its important Role during WWI
- Who’s the real Threat to your Security? Rogue Hackers vs. the Government
- Caesar used Encryption and so should You
Don't miss the next Steemit Crypto Challenge this week. More information will follow tomorrow. Solve the Crypto puzzle and win a generous reward. Show us your code-cracking skills.
Feel free to tell us what you think about Encryption and what you would like to read next
-Tim Said
Great post! Thanks a lot!
Very well informed post Timsaid, thank you for educating our community.
When it comes to security I want to help. Privacy is our right, our human right.
Interesting! :)
Enable 2FA and geolocation blocks, whenever possible (If you never step into China... why enable access from that place?).
Change your password periodically, even when your password is long, and it takes a lot of time to "crack", it will eventually be cracked. Changing the password once a week, or 10 days. Totally ruins the bruteforce method.
Dont forget, the estimated calculations of the bruteforce are limited to 1 device trying. A 100 node botnet would take roughly a month to crack a 9 character password.
In theory password expatriation is a good thing. But in practice it is considered not.
https://cryptosmith.com/password-sanity/exp-harmful/
2fa isnt necessarily by itself sufficient because then you are depending on your cell phone providers security protocols which is not a good idea.
True but you can use 2fa with apps instead of the cell phone networks.
Good information and presented in a readable way! Nicely done, as explaining password complexity is not an easy task.
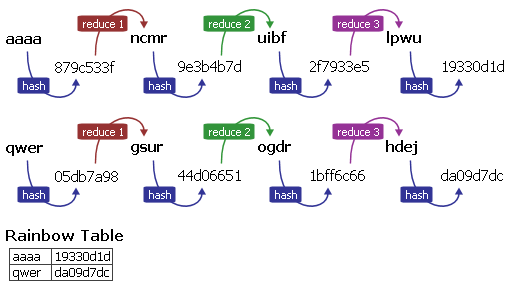
This stuff is so interesting, a few years ago I created some rainbow tables and then realized I had no idea what I was doing or how to even use them, but my PC spent a few days at 100% and I got my rainbow tables.
In winter-times a good way to heat your room
Your definition of rainbow attack is wrong. This attack is a "time-memory" trade off. From Wikipedia:
You could summarize the table as a set of "chains of passwords". So the size of your table depends of how long you want your chain to be.
To break the rainbow attack we use salt. They force the attacker to rebuild the whole table for one specific target, hence the protection.
So conclusion: you can only trust your password so unless you checked the code of the server make it as secure as possible. Two videos with "real life paswords cracking:
Algorithms that also make use of space–time tradeoffs include: Rainbow tables in cryptography, where the adversary is trying to do better than the exponential time required for a brute-force attack. Rainbow tables use partially precomputed values in the hash space of a cryptographic hash function to crack passwords in minutes instead of weeks. Decreasing the size of the rainbow table increases the time required to iterate over the hash space.
So i would not say it is wrong.
Well he doesn't show that it is a trade-off.
And the numbers about how large the tables need to be gives a wrong idea. This sound like just a dictionary attack while the generation is very different. Your definition is "complete and correct" if I can say so which is why I am upvoting it :).
Best explanation I have seen cheers
me follow you and upvote
if you can back upvote my blog ?
https://steemit.com/photography/@zein/the-beach-where-i-live-original-work
Greatly explained! Looking forward to more articles from you ! :)
As you ask for inspiration for some of the next articles, I would find it interesting to have a discussion about - The National Institute of Standards and Technology (NIST) - whether you should focus on NIST verified encryption or when there might be backdoors implemented also combine it with different crypto libraries?
I think also explaining NIST challenge helps understanding crypto.
Thanks! :)