[EN]Social Engineering - Human weakness
Many people understand the term IT security as the technical security of systems.
In order to be able to comprehensively protect systems, however it is necessary to see security as a whole picture, in which a potential attacker always looks for the easiest way.
In this article, the relevance of social engineering in the area of IT security will be demonstrated.
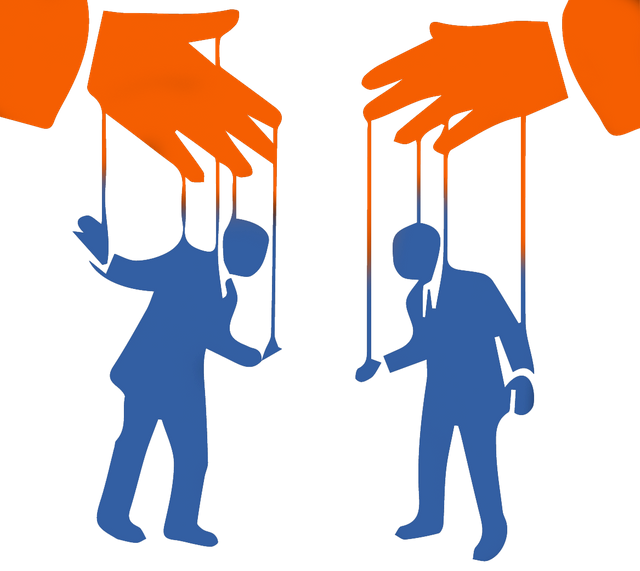
What is social engineering?
Social engineering refers to the possibility of getting confidential information and data from person to person on a social level.
The weak point here is therefore not of a technical nature, but the human being who is manipulated with partly psychological tricks.
The targets range from identity and data theft to industrial espionage.
Among other things, attackers make use of the following features:
- People want to avoid anger and conflicts in principle
- People would like to help other people
- People like to be respected
- People have the need to trust other people.
Social Engineers make use of these features (and some more) in a targeted way, for example by using:
to appeal to the Assistance:
I am a colleague from the marketing department. I just need to answer a quick e-mail. My PC has already been shut down. Can I use your computer for a moment while you're taking a break?
to flatter someone:
I am a journalist and write about creative entrepreneurs in the FinTec area. I noticed you very positively. Do you have a few minutes? I would like to ask you about your person and current intentions
This now seems strange, but the success rate of such attacks is enormously high. A good social engineer knows how to build trust in people with small talk, for example.
Basically, a social engineering attack can be divided into the following steps:
1. Collect information
2. Make contact.
3. Pretending a false identity.
4. Get information.
5. Make yourself inconspicuous and quick as possible go on the run
6. Applying the "captured information."
What types are there?
There are a lot of different types of social engineering attacks. The following is a brief overview of known procedures.
Phishing
Phishing is the most commonly used variant of social engineering. In this case it is usually in the form of a spoofed (falsified / copied) internet page or e-mail as someone else.
Further information on phishing and common variants is already described in a contribution in German(If you would like to read that in English too i will translate this article). That is why I do not want to go into it any further at this point.
Interesting facts and figures can be found in the APWG Phishing Reports.
USB Dropping
Who isn't curious when they find a USB stick? Maybe you just want to track down the person who lost the stick. The first intuition is often:"Let's see what's on it".
This is very dangerous, however, as malware can get onto the systems via modified firmware or a minicomputer disguised as a USB stick.
Dumpster Diving
The term itself already reveals what happens here: Paper waste containers are searched for sensitive information. It is not for nothing that there are document shredders that should be used when documents are confidential.
Here, too, it is sufficient if an employee throws away a post-it with a note of a password carelessly.
Shoulder Surving
Especially when working on the move, it is possible that a social engineer looks over your shoulder at work.

Source
Therefore, you should be careful not to let anyone see anything, especially if passwords are entered or sensitive data is being processed. What you probably do intuitively when entering your PIN at the ATM should also be done, if you enter your access data on your PC/smartphone.
Tail Gating
An attempt is made to enter secure areas without access authorization. Running after someone and walking through the door is usually very easy. If someone with a big and seemingly heavy cardboard box would come along, you would surely be nice enough to stop the door for the poor man.... wouldn't you?
further proceedings
In addition to the approaches mentioned here, there is much more. Depending on the situation, social engineering attacks can be planned for a very long time. This could go so far as to fake a partnership in order to obtain the relevant information.
How can I protect myself?
Since people themselves are "attacked" here, it is also necessary to "protect"them primarily.
After reading this article, you already have a basic understanding of the existence of social engineering and what such attacks might look like. In principle, it is important to be sensitive to attack vectors of this kind. I'm not saying you're not supposed to be nice anymore, stopping someone's door or helping them with problems. The basic knowledge and security awareness often helps to detect social engineering attacks.
In the environment of companies, a policy is recommended which must be adhered to. In addition, it makes sense to develop awareness trainings that address specific application scenarios depending on the position and activity within the company and help to build up security awareness.

Thank you for reading! Stay safe, but don't exaggerate ;)


Schön dass du deine Posts in beiden Sprachen hochlädst. :)
Für längere Titel kann ich empfehlen [DE] bzw [GER] für deutsche Artikel und [EN] für englische an den Anfang des Titels zu stellen.
Die Benachrichtigungen einiger Apps schneiden nämliche einen großen Teil des Titels ab, sodass nur "Social Engineering ..." bei deinen Followern ankommen könnte.
Gruß Fuchsfalke
Vielen Dank für dein Hinweis !
Werde das ändern :)
Guter Tipp! Direkt in den Hinterkopf geschrieben. ;)
@security101 Highly intriguing topic. No security system on a hardware or software basis will suffice, when people are as easily tricked as they often are.
One of the most dangerous human features in this context, that opens many doors: People are lazy. :D
Well written.
Danke für deine Anmerkung !
Habe es verbessert :)
Gern :)
Congratulations @security101! You have completed some achievement on Steemit and have been rewarded with new badge(s) :
Click on any badge to view your own Board of Honor on SteemitBoard.
For more information about SteemitBoard, click here
If you no longer want to receive notifications, reply to this comment with the word
STOPThank you for your article and for listing the types of social engineering attacks. I wrote a post on social engineering taken to the next level. Please have a look and let me know if you find it interesting https://steemit.com/life/@cryptasana/you-ve-been-rated