Crypto Academy | Season 4 Week 2. Homework Post for |@fredquantum| - Mimblewimble Protocol
Hello buddies and welcome to the week 2, season 4 of Crypto Academy. Here I will be undertaking the homework post of our dear professor @fredquantum.

Question 1. In detail, explain your understanding of the Mimblewimble protocol.
Mimblewimble Protocol
Since the advent of Blockchain, many advances have been made and we have seen both the strengths and weaknesses of blockchain (like the issues of Scalability and privacy). It is generally agreed that Blockchain has brought a level of privacy to the way people run their transaction, just like the Bitcoin network. However, this privacy is not absolute, because even though the personal detail of the person undertaking the transaction is not known, other information can be revealed by the network - like time, amount, etc. To maintain further privacy, Mimblewimble Protocol was created.
Now what is Mimblewimble Protocol? In Blockchain space, Mimblewimble Protocol is a protocol created by an anonymous entity called "Tom Elvis Jedusor" in the year 2016 with the principal aim of allowing for an absolute and exclusively private transaction which is basically undertaken by a framework of security. What this correlates to is that there are no addresses in Mimblewimble Protocol, which also means that transactions are highly confidential - as contained in the Mimblewimble Protocol official Whitepaper.
One of the conditions that necessitated the need for obscurity and anonymity of transaction was the notorious hack was was perpetrated in 2016 where some cyberpunks attacks an exchange and made away with about $72million. Soon after that unfortunate incidence, Mimblewimble Protocol was launched and it gained widespread adoption because it is centered on full anonymity.
Question 2. Discuss in detail how the Mimblewimble blockchain protocol works.
Principles and practice of Mimblewimble Protocol
Transactions done in Mimblewimble are based on Elliptical Curve Cryptography - ECC which is a form of Confidential Transaction. When you talk about elliptical curve, I am sure you will be quick to remember your secondary school maths - logarithms, even though it is a bit more complex in ECC and consequently, in Mimblewimble. Here is how it works:
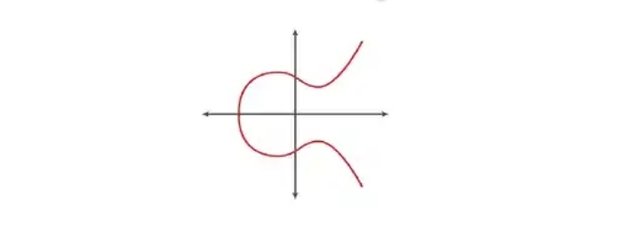
You will agree with me that:
2⁸ = 256. Which is multiplication.
In logarithms however, the reverse becomes the case.
log2 (256) = 8.
From the two above equations, you will discover that the number "2" is being multiplied by itself for 8 times to get 258, and the second equation is the log of the initial one.
In Mimblewimble however, the principles combine both logarithm functions and discrete probabilities - that is, the area of probability that is concerned about distinctive mathematical functions.
Now one may ask, how are all these related to Mimblewimble? In its simplest form, Mimblewimble combines together sets of ECC (which is known to perform strings of distinctive logarithmic functions), and other cryptographic functions. The purpose of these combinations is to hide both the addresses of the transactions, transaction value, and the identity of the parties involved in the transaction.
The Cryptographic protocols that are involved in Mimblewimble's Elliptical Curve Cryptography (ECC) are:
- CoinJoin
- Dandelion
- Confidential Transactions (CT)
This now leads us to question 3.
Question 3. Discuss in detail your understanding of Confidential Transactions (CTs).
Meaning of Confidential Transaction - CT
This is a kind of protocol that allows only the parties involved in a transaction to know details about the transaction - like the amount that was transferred, the address of sender and receiver. This is quite different from the normal blockchain transaction where anyone can get details about transactions from a blockchain explorer. Here is a pictorial depiction of how normal transactions and confidential transactions are different.
In the normal transaction, the amount and address identity of the sender and receiver are known, as shown in the image below.
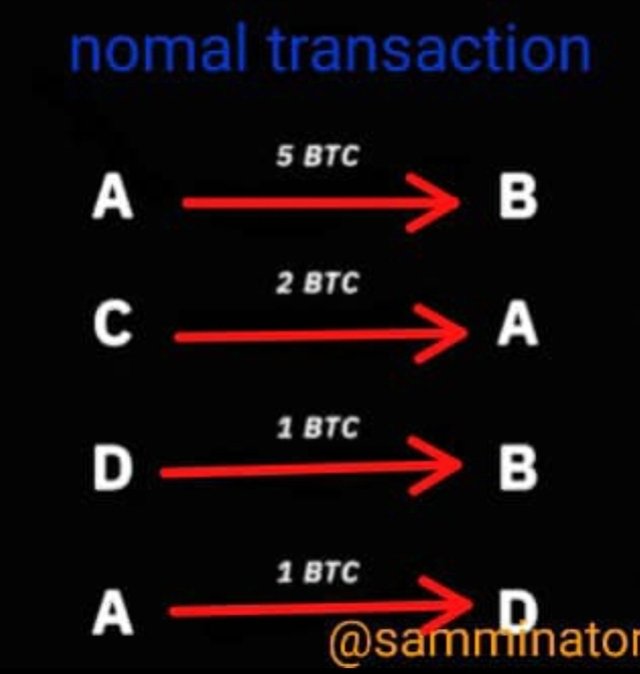
When you look at this, you will notice that the amount that is transacted is open for the public to see. In addition, the addresses of both the sender and the receiver are also open.
Now let us look at how a confidential transaction looks like from the Image below.

Here, you will notice that the identity of both the sender and receiver, and the amount that is transacted are all kept private and concealed.
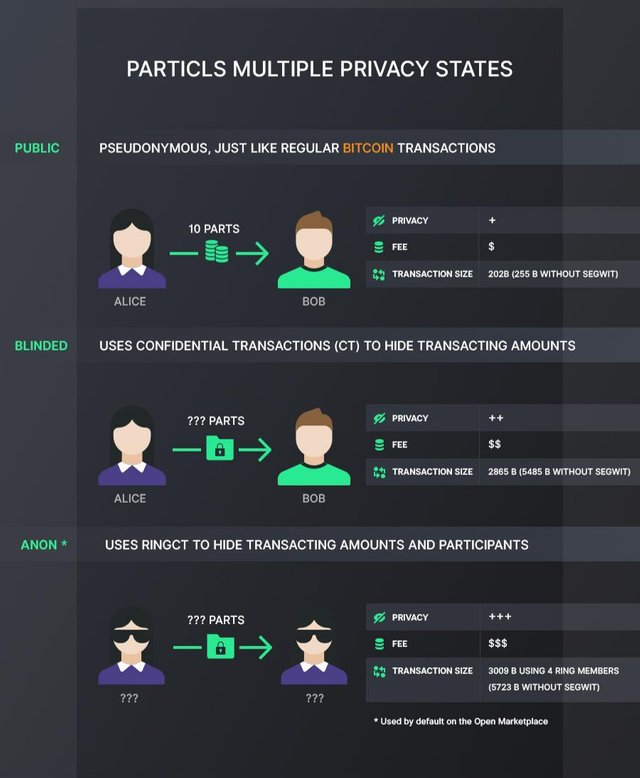
The Cryptography behind CT
To make CT possible, encryption must come into play. However, the knowledge of traditional encryption we are familiar with (the one that involves locking or putting a file into cipher to prevent external party from viewing it) does not apply here. The kind of encryption that applies in CT is known as homomorphic encryption - which is simply an encryption protocol that conceals the content of a transaction from outsider or third-party, while the properties remains verifiable, as shown in this infograph below.
Question 4. How do you think Mimblewimble Protocol can be utilized on the Bitcoin Network to enable anonymity of transactions and improve scalability?
Since the inception of the genesis block on the Bitcoin Blockchain, every single transaction has been recorded and kept in history that is open to the public. What this means is that every transaction that has been done in Bitcoin Blockchain can be downloadable by anyone.
On the other hand, what a Mimblewimble blockchain does is to only keep the record of indispensable information without compromising privacy in the process. The authenticators in Mimblewimble also ensures that the transactions cannot be falsified either through "double spending" or through irregularities in circulating supply of coins.
Utilisation of Mimblewimble Protocol in Bitcoin Network
You will agree with me that Bitcoin network comes with a standardized scripting system which predefines the rules on how transactions are organised. This scripting system is what causes a reduced scalability in Bitcoin network. Now, incorporating Mimblewimble Protocol into the Bitcoin network will act as a way of removing that standardized scripting mechanism.
When the standardized scripting mechanisms are removed, the Bitcoin network will be more scalable - this is because the data that will be generated per transaction will become minimal. Furthermore, it will further make for privacy because addresses will lose their traceability.
Question 5. State the Pros and Cons of the Mimblewimble protocol.
There are advantages and disadvantages that are inherent in Mimblewimble and we will take a look at them.
Advantages of Mimblewimble Protocol
Privacy and Anonymity: As against the Bitcoin Protocol that shows the addresses of both sender and receiver in a pseudonymous way, in Mimblewimble, transaction details (like addresses) cannot be traced or tracked. With this, the identity of the party performing the transaction cannot be revealed.
Scalability: The size of blocks in Mimblewimble Protocol is much reduced because of the removal of scripting system. The result of this is that the Blockchain will become more scalable.
Increased Fungibility: The term fungibility in the crypto space refers to the ability of a digital asset to be exchanged for eachother. Mimblewimble makes for an increased fungibility because it overrules the possibility of a coins being tainted or marked.
Reduction of Blockchain Size: Applying Mimblewimble Protocol in Blockchain will result in the compression of data, thus reducing the size represented in Blockchain. With this, verification of nodes will take up very small storage space.
Disadvantages of Mimblewimble Protocol
Over-dependence on digital signature and non-resistance to quantum computers: Mimblewimble has a heavy dependence on digital signature. What this automatically means is that attacks that are perpetrated from a quantum computer will make the Mimblewimble protocol very vulnerable.
Increased transaction throughput: Throughput in Blockchain is simply the quantity of transaction that is being transmitted in a particular time. The support for Mimblewimble Protocol and Confidentiality Transactions makes it inevitable for a lower transaction speed, thereby increasing the transaction throughput.
Question 6. Discuss in detail at least a Crypto that uses the Mimblewimble protocol.
There are quite a number of cryptos that use the Mimblewimble protocol like:
- Beam
- Grin
- Litcoine
- MimbleWimbleCoin
For the purpose of this homework, I will discuss two - Grin and Beam.
Grin

This is a privacy coin that was initiated in 2016 and finally launched in 2019 and it became the first cryptocurrency to conceptualise the use of Mimblewimble in Blockchain as indicated in the official Grin website. The creator of this coin has remained anonymous and goes with the codename "Ignotus Peverell".
Features and technology behind Grin
Grin is exclusively created to be a transactional cryptocurrency in contrast to the Bitcoin that was created to also be a store of value. This also means that the issue of scripting is totally sidelined, as no additional data can be made to Grin blockchain. Consequently, this feature will make Grin almost impossible to be used for the creation of DApps or smart contracts.
The transaction that are carried out in Grin Blockchain are devoid of addresses and does not contain amounts, making each transaction unique and private.
Furthermore, Grin cryptocurrency implements what is known as Cuckoo Cycle. That is, when transaction is made, or during the mining process, the prove of work algorithm makes use of bandwidths stored in memory, instead of processing power. This feature makes is easy for the Blockchain to be maintained.
Grin's wallet is uniquely different from other traditional crypto wallets. For you to perform a transaction in the Grin wallet, both parties - the sender and the receiver, will need to be active and online. Here's a typical example of Grin wallet.
Furthermore, transactions that are done on Grin Blockchain is basically initiated through file transfer or Hypertext Transfer Protocol directly from the IP address. This is to rule off the eventuality of privacy being compromised.
As at the time of making this post, Grin coin is valued at $0.3 on CoinMarketCap and is tradable on major exchanges like KuCoin and Gate.io.
Beam

Beam is another cryptocurrency that uses the Mimblewimble Protocol. It was created by Guy Corem between 2018 and 2019, and it conceptualises privacy just like Grin. In Beam however, the transaction is always one-sided. That is, the receiver of the transaction will have to send their own side of the transaction detail to the send. Upon reception of this package, the sender will then complete and authenticate the transaction before it will be uploaded on the Blockchain.
Features of Beam
The Beam Blockchain adds a layer of privacy that makes any transaction detail to be revealed by only the parties involved in the transaction. That is, personally data and transaction information are entirely in the hands of the parties performing the transaction and not public as indicated in official Beam's Whitepaper.
Beam also has a wallet just like Grin, but in contrast to Grin, it support atomic swaps. Here's a pictorial depiction of Beam wallet.
Beam wallet is available on mobile for download on Apple store and Google playstore. As at the time of writing this post, Beam is valued at $0.66 on CoinMarketCap and it is tradable on major exchanges like Binance and Gate.io.
Conclusion
The Bitcoin Protocol is known to have inherent limitations which includes privacy and scalability. This is the reason Mimblewimble Protocol was create. With this privacy in place, cryptocurrency can now go further mainstream. We have also looked at how Mimblewimble can be implemented in Bitcoin network and the strengths and weaknesses of Mimblewimble.
With the features of Mimblewimble Protocol, one thing is still very certain; the implementation can only come as a side-chain to the Blockchain of Bitcoin, this is because the original Bitcoin Network's Protocol has gained massive dominance.
Thanks all for reading, and special appreciation to @fredquantum.
Thanks for reading

