Securely Delete Files in Linux

Now I am going to show you how to securely delete/shred files from your hard-drive, obviously we are talking about things like cryptocurrency private keys which you may have saved in a text file but if you don't shred it, it will remain there, possibly forever if we are talking about a 1TB or bigger drive.
In the previous post I've shown how to delete normal files:
However sensitive information must always be "shredded", otherwise you risk exposing it given how malware could possibly access it later, or when you sell your hard-disk later the new buyer could (with some effort) recover it, or even scumbags at hardware repair shops could steal it!
Formatting a hard-drive is not enough, especially if it's just a "quick format", that leaves almost all the files intact there and anyone can recover it with publicly available forensic software. Even a "slow format" is usually just a 1 time pass and sophisticated forensic experts could probably still recover it with some time and effort.
If you have worked with active Bitcoin private keys on your drive, and you later want to sell it, it might not be a good idea. It is possible to erase the entire drive but it will take a lot of time, so it's just better if we erase the files after we are done with them.
Securely Deleting sensitive files
The way files are deleted is that their location on the drive is basically overwritten with random data. Since the contents of a flash memory have no exact pointers, their location is probabilistic, which means that 1 round might not be enough to overwrite it all, so multiple rounds are needed.
The Gutmann method provides the most security, it consists of 30-40 rounds, which can be made more precise on some Linux based filesystems. A "zero" round can be included optionally, which fills up the entire memory region with 0 bytes in the last round, thus hiding the fact that data was erased or that it even existed there (unless other logs in the computer or the filesystem record it), thus providing plausible deniability in case on an extortion attempt.
Some filesystems do keep shapshots and logs about the files for checksums or other reasons so not all filesystems provide plausible deniability. Some of the bad filesystems will need more rounds perhaps 40-50. These are:
JFS , ReiserFS, XFS, Ext3, Ext4, NFS, RAID - based ,etc...
We will use the shred software that is already built in many Linux based Operating Systems.
The command is:
shred --iterations 40 --exact --zero --verbose <filename.extension>
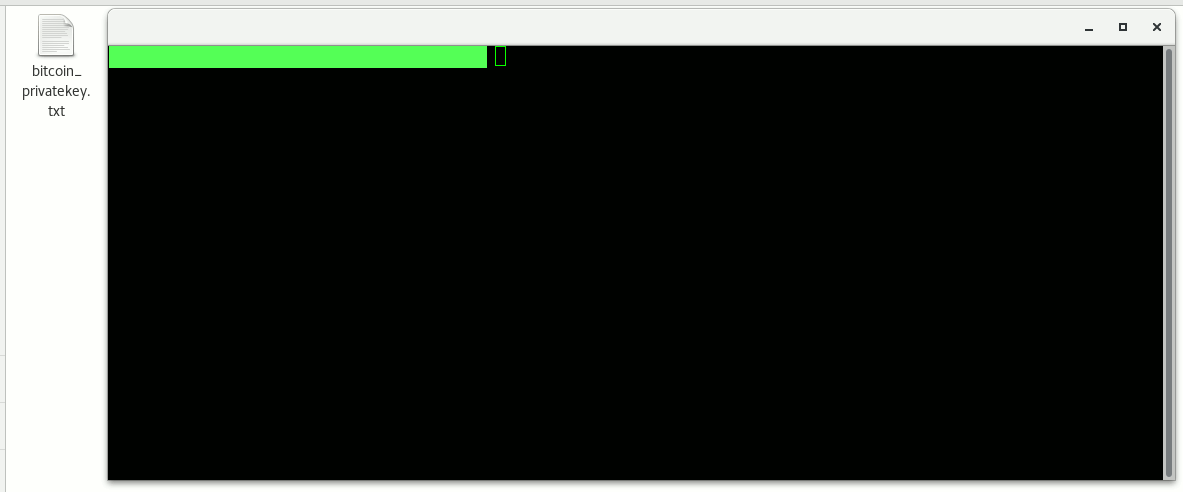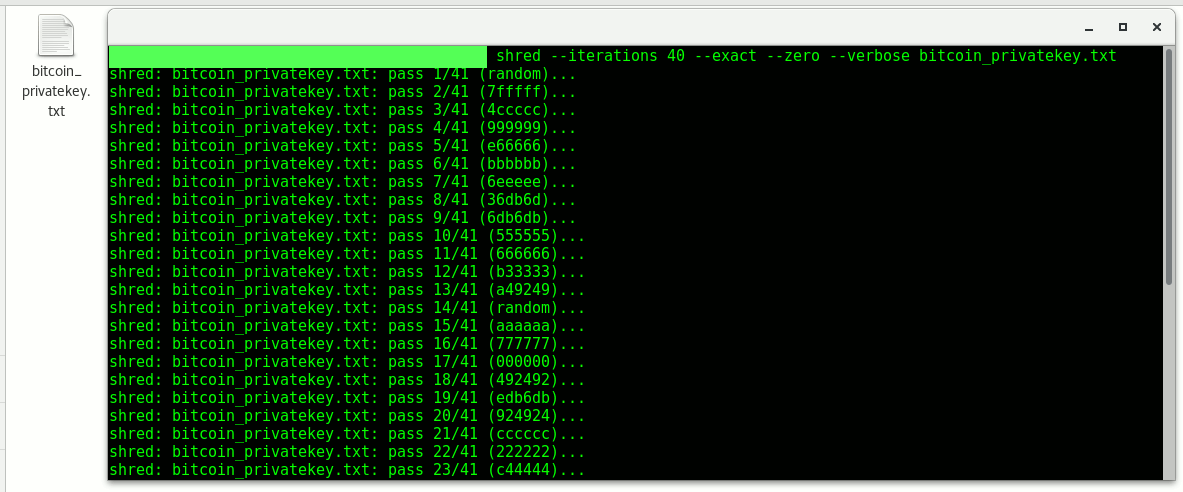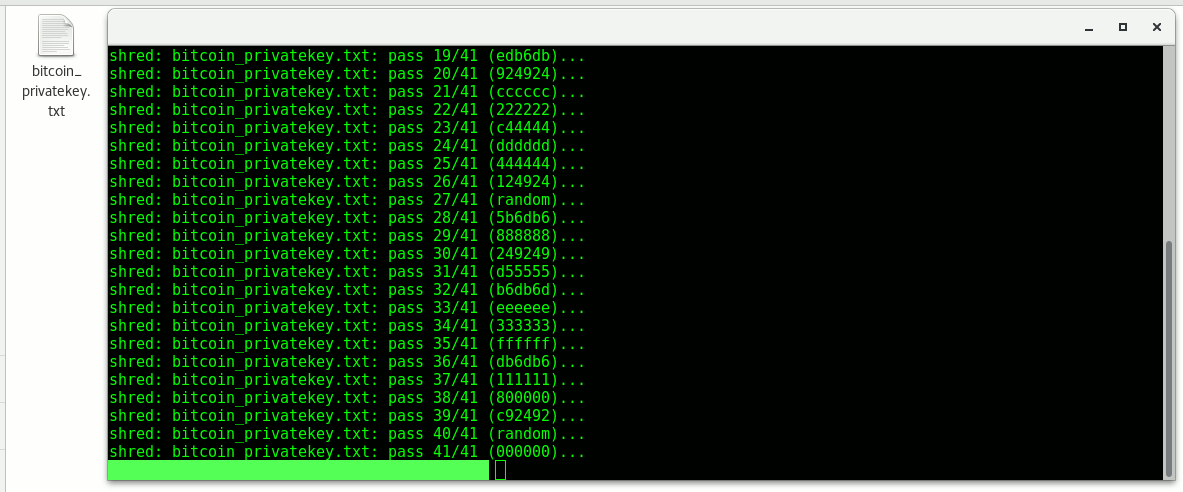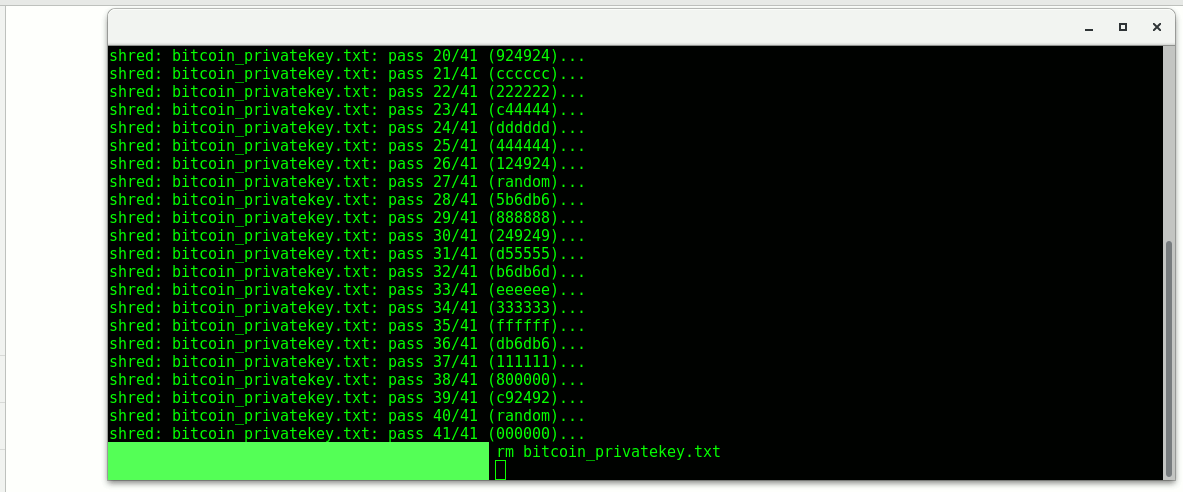
Of course the iterations can bet set too. For files above 50 Megabytes, it might take a longer time, certainly don't try to wipe your entire drive, that might take days or weeks. But for Bitcoin or ETH wallet files which are a few Kilobytes, it's recommended to set it to 40 or higher.
As you can see the file is not removed, only the data is overwritten, to remove the file itself just enter:
rm <filename.extension>
This is because as above mentioned Linux filesystems like Ext3 and Ext4 stores the file metadata (name,size,timestamps) separately from the data itself. But I guess in the case of a Bitcoin wallet the name of the wallet doesn't matter does it? Otherwise just use plain filesystems like FAT32.
But if we open the shredded file before deleting it, you can see that it's all zero-ed out, so the private key is destroyed:
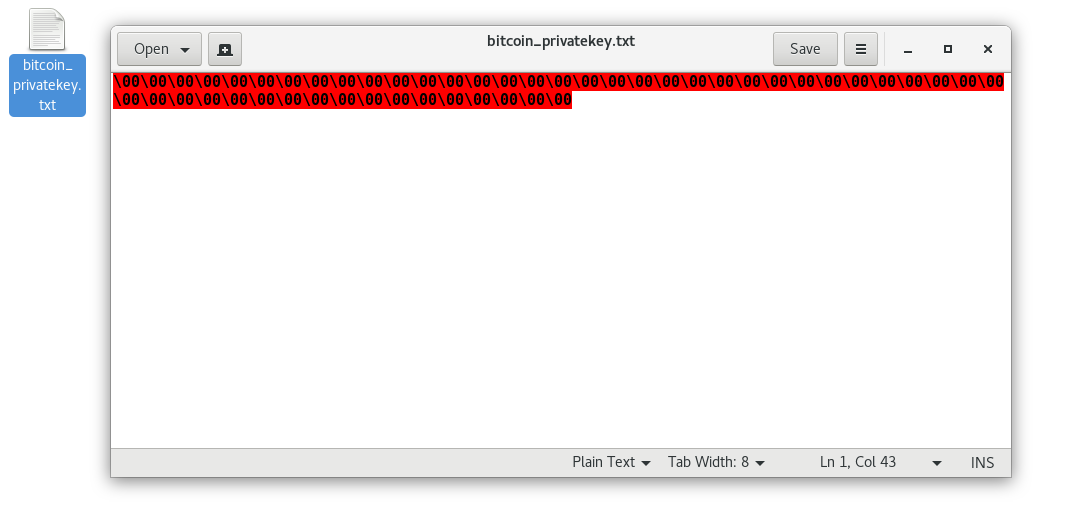
That's it, that is how you can securely delete a private key or any other sensitive file from your hard-drive after no longer using it.
Sources:
https://pixabay.com

Much more elegant than drilling into the discs themselves. :)