Features of Uncloak more details

Uncloak is the name of the blockchain networking site which has taken some steps forward to make sure the users can play safely in their way of working. It is basically a cybersecurity threat management of next generation that works for the betterment of the users. It is the world’s first blockchain powered cyber threat solution for the business and it keeps the users always a step ahead of the hackers.
Features
The Uncloak application has developed some in-house current features that include:
Automatic identification of client’s public internet footprint to cover the websites, email servers, applications and computers on the internet in readiness for a security scan reducing the timescales around the security scanning setup.
It is easy to understand for dashboard checking progress to scan the reports, request for external IT consultancy by setting up the schedule scanning jobs.The Uncloak software also stimulates the stability with an attempt of hacking against the email server to check the antivirus protection of the clients.
Market Requirements
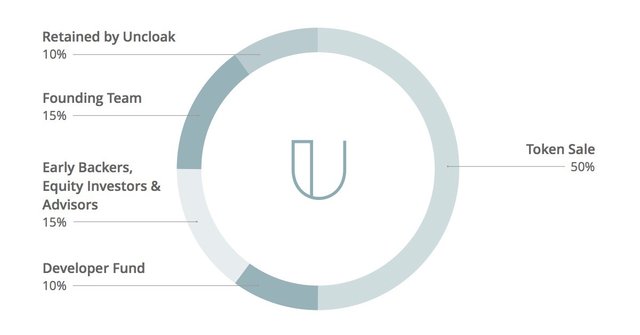
Uncloak is thinking about meeting up with the market requirements for innovative use of the blockchain for artificial intelligence ensuring the cyber security market leading as the best opportunity to secure with proactive computing infrastructure that includes:
On-premise software tool enables the users to scan their internal network for threats and vulnerabilities to report back to the central dashboard
Advanced network discovery tool manages the cloud environments to scan the ability for vulnerable cloud environment based on public, private or hybrid ranging the environment
Intelligent security compliance tool for the innovative engine for checking against the cyber essentials compliant to the requirements
Blackhat extreme mode converses the online security database for a number of additional tools in order to check the vulnerabilities of multiple operating systems by the issuance of ranging the website, workstation, and database.
Bug Bounty
The companies are positioned to be aware of imminent cyber threats to release the public domains causing financial damages to the company reputation. The current vulnerabilities also scan for applications relying on the stale cyber threat security information diagnosing the company website risking the website.
Uncloak aims to change such pressing issues and works through the number of smart contracts functioning a set of predetermined actions by the issuance of ethical hackers on the basis of new cyber threat vulnerabilities to be found and checked for other hackers into the community.
Using Tokens
The UNC token usage is based on the Uncloak platform of smart contracts that creates the voting rights enabling the community to register IT security experts or software developers can also collaborate as hunters to find the cyber threats within the applications in the network devices whilst it finds the remediation needs to resolve the cyber treat issuance. If any vulnerability found for the application it can be checked for the database ensuring cyber threat.
The hunters have the authority to check the vulnerability taking up to 4 validates to check and find the authenticity record for real cyber threat. The hunters can discover 10,000 UNC tokens to this unique platform checking the platform with the validity of vulnerabilities given for 1500 UNC tokens each with conversion criteria to the tradable platform for UNC tokens. This can be exchanged through Ethereum on a public exchange.
It has some requirements developing the application spurred by the demands to be reactive. It is developing MVP for Uncloak’s expertise in the cybersecurity for every shaped enterprise protecting the infrastructure with an approach for thwarting the hackers.
Website : http://bountie.io/
Whitepaper : http://bountie.io/docs/whitepaper.pdf
Twiiter : https://twitter.com/BountieGaming
Facebook : https://www.facebook.com/BountieGaming/
Telegram : https://t.me/bountietoken
God Bless You!