Goldilock: the security of another planet in our hands

Goldilock Gold Security
One of the biggest investments in the world of cryptoactives in recent years is aimed at improving the quality of security. Despite the high standards of trillion dollar security protocols have been hacked to thousands of cryptocurrency holders. This makes it clear that a fundamental need is to improve security when it comes to safeguarding digital assets.
Reliability in blockchain systems is what will determine much of the future of these technologies. The populazation of these platforms while they have serious security flaws and put investors' capital at risk is almost impossible.
Goldilock is aware of this. Goldilock breaks the current schemes on which the security of digital assets is conceived. It is revolutionizing the way in which data is stored on the web, for this purpose it makes available to individuals and institutions a platform capable of safeguarding information or assets of users.
This system leverages existing technologies by combining multi-factor authentication, biometrics, regressive triggers of non-IP technology and cryptography to change the burden of keeping wallets secure regardless of whether they are cold or hot systems.
Two roads the same destination

The investment in digital assets as its subsequent administration required up to now the difficult choice two formats of information storage. The first of the storage solutions is linked to the acquisition of personal hardwares. Each individual in this modality will select some of the devices of their best agreement according to their tastes and needs. This type of storage allows the cryptocurrency holder to be sure that their information is stored in a device without internet connectivity, which makes their information virtually impossible to hack.
The second option are the so-called hot wallets. They are digital platforms with permanent internet connection which allows customers to dispose of their assets anywhere in the world and at any time.
Both storage options in cold or hot have a lot of advantages. However, these information management methods are also associated with great weaknesses. For example, cold storage devices are constantly being pirated, lost by their owners, and may even be destroyed or confiscated; On the other hand, hot online wallets, due to their condition of permanent connection to the internet, are highly vulnerable to piracy, denial of service and collapses of the companies that provide the service.
The perfect combination

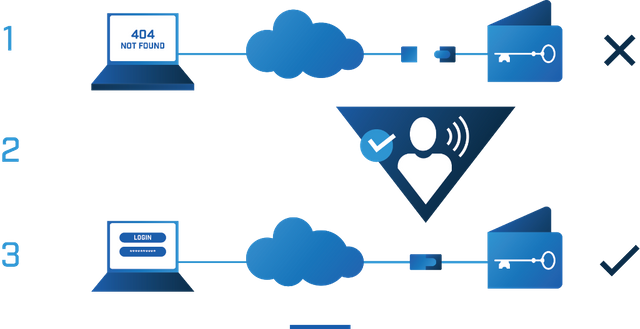
Goldilock combines the best of the two systems. It stores the data in a device that will be stored inside a vault of a data center for greater security. The device is always physically disconnected from the Internet until the client decides to access it.
This connection will be achieved through an authorized Non-IP command by the consumer on the Public Switch Telephony Network (PSTN). The storage device will be mounted remotely and will be accessible online through a secure web login. Clients can instantly access their data using custom channels where they can complete transactions.
We will have the certainty that our information can not be hacked because it is not available on the web since the connection will be at the moment and the time period determined by the user. Also, there is no risk of loss of information due to the loss of hardware and we can rest assured that our information will always be available to us at the time and place of our convenience.
The Three Pillars of Goldilock
Goldilock's team bases the design of its ecosystem on three fundamental ideas that were born from observing the daily use that users had about their cryptoactives:
Users need access to information protected quickly, but only occasionally and for short periods of time. This fact makes it possible for the data to be protected and only after the owner's request is available. Online data are more vulnerable. This condition opens a window of possibilities for hackers to steal stored information.
Security protocols for data (including private keys) require an isolated storage, secured unwanted physical contact and human errors. The system guarantees users a full backup of their information.
A robust security system should not be an impediment for personal data and private keys to be quickly accessible when necessary. Goldilock knows this, for this reason the access times are reduced, giving great importance to the client's time.
Why NEO
Thanks to all that NEO has to offer, the Goldilock token (Lock) has a series of very important features that raise the quality of the product perfectly. This is the reason why Goldilock opted to use NEO on its platform. This was a great choice.
Goldilock chooses Neo first of all for the set of benefits and facilities that this platform provides for the smarts contracts, the contracts in neo guarantee the maximum reliability to the users on the fulfillment of the established terms. On the other hand you can be sure that the execution times are optimized without going against security.
This association makes possible a safe, fast and with a wide range of options for users.
Goldilock Applied in all areas
Every day there are more people and institutions that need to have their information safeguarded and available when required. This makes Goldilock the most versatile tool for digital security.
Currently there is a large field where Goldilockcan be applied:
Identity Safeguard
This is one of the most common uses of block chain technology users. Much of the information used by users on the web is exposed to being stolen when it is kept online. Goldilock allows users to access their data and digital assets without running the risk of being hacked. Once the user has finished consulting and manipulating their information, the data is again out of line. Inaccessible for those who want to see or access them.
Wallet
Goldilock can be used for cryptocurrency storage. The stored information is disconnected from the internet until the moment the user requests that his or her individual encrypted node be connected to the Internet. For this purpose, users will use an analog command from the Internet, with which they can access their data through an encrypted channel after completing the security protocol.
It is important to note that, using Goldilock, the private key never leaves the individual node, which means that it can not be stolen or damaged while it is connected.
Use Case
Justine and Juliette are developing a new drug for the cure of degenerative diseases. In the project companies have invested millions of dollars in the research and development process to achieve the next product to go to market.
Both are extremely concerned about the security of the information since any leakage of information would represent billion-dollar losses and irreparable damage to its reputation. Justine chooses to keep the information on portable hard drives with access codes for better protection. Juliette opts to pay for a digital information custody service to safeguard the information.
As the investigation was developed, Justine's devices began to fail and some of the access codes were lost. Months later, the custody company hired by Juliete suffered some hacking attempts. These events caused some investors to make serious complaints about the security of the information and it was demanded that a different way of keeping all the information safe was sought.

An old friend of the university, suggests to them that they use Goldilock. Goldilock arrived to provide the desired security for both. Now Justine and Julitte can fully concentrate on finishing research. The security of information will no longer be a major concern.
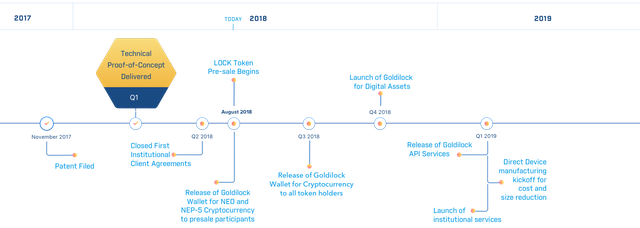
Road Map
Team leader

Advisors
Partners

Goldilock overviews
Social Media
- Goldilock Website
- Goldilock WhitePaper
- Goldilock Token Description
- Goldilock Telegram
- Goldilock Discord
- Goldilock Facebook
- Goldilock Twitter
- Goldilock GitHub
- Goldilock Linkedin
- Goldilock Redit
Here is the link to my tweet about Goldilock
This is the entry for the @originalworks contest
goldilocktwitter
goldilock2018





This post has been submitted for the @OriginalWorks Sponsored Writing Contest!
You can also follow @contestbot to be notified of future contests!
You've received a lifting from @botox ! Consider delegating to earn passive income 20SP,50SP,100SP,200SP.
Tu viens de recevoir un lifting de @botox ! Envisager de déléguer pour gagner un revenu passif 20SP,50SP,100SP,200SP.
They have enlisted the help of the @alliedforces!
We gladly answer your call!
(@alliedforces is a collaboration of witnesses @jatinhota & @enginewitty)
Have you supported your favorite witnesses?