Mobile banking Trojan BankBot was disguised in Google Play for games, "flashlights" and software for clearing memory
Mobile banking Trojan BankBot was disguised in Google Play for games, "flashlights" and software for clearing memory
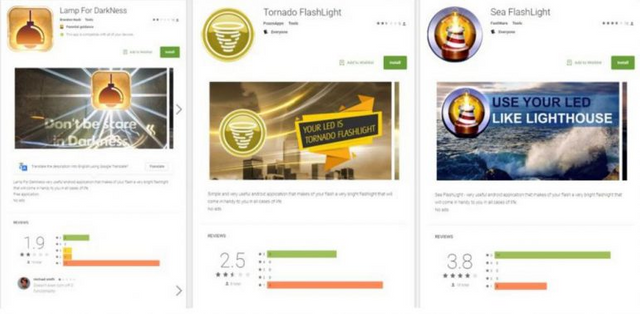
Experts from ESET warned owners of Android-smartphones about a new campaign to distribute the mobile banking TroBank BankBot on Google Play. At the first stage, the malicious users published in the content store the flashlight applications Tornado FlashLight, Lamp For DarkNess and Sea FlashLight with malicious functions, on the second - applications for playing solitaire and software for cleaning the device's memory.
After the first start, the loader checks the installed programs on the device with an encoded list of 160 banking mobile applications. When one or more matches are found, it asks for the device administrator rights. Then, two hours after the activation of the rights, the loading of the mobile Trojan BankBot starts - its installation package is disguised as an upgrade to Google Play.
All detected loaders download the same version of BankBot from the address hxxp: //138.201.166.31/kjsdf.tmp. Downloading is possible only if the user's device is allowed to install applications from unknown sources. If this option is not enabled, an error message will appear on the screen and the attack can not be continued.
After installation, BankBot acts as typical for mobile bankers - when a user opens a targeted banking application, the Trojan downloads a fake form of entering a login and password. The entered data will be sent to the attackers and used for unauthorized access to the victim's bank account.
Note that throughout the whole of 2017, ESET experts found on Google Play malicious applications disguised as legitimate. For example, in February, mobile bankers were offered under the guise of weather applications, and in September - under the guise of the game Jewels Star Classic. A new wave with games, "flashlights" and software to clear memory occurred in October-November. Typically, these fakes are removed within a few days, but during this time they manage to infect thousands of user devices.

This post has received gratitude of 1.18 % from @appreciator thanks to: @kobusu.