What You Should Know About Hashing
Canvas
Firstly this post will be subdivided into two which the first part will be used to discuss what "hashing is, and then the second part will be used to discuss"SHA algorithm". When it comes to adding additional security, note that hashing is the core principle behind such ideology which is why the first part of this post is specifically designed for hashing. Let's delve deeper into it.
Hashing
In a blockchain and the tech space generally, there is usually a way of making information not be reproduced to its main form which is the process that is used to scramble information (raw data) to the point that the information cannot reproduce the same the output to its original form is known as hashing.
Hashing takes information and passes the information through a function that mathematically operates on a plaintext. The function that we are talking about here is known as the "hash function" which the output that the function produces is known as the "hash value.
Canvas
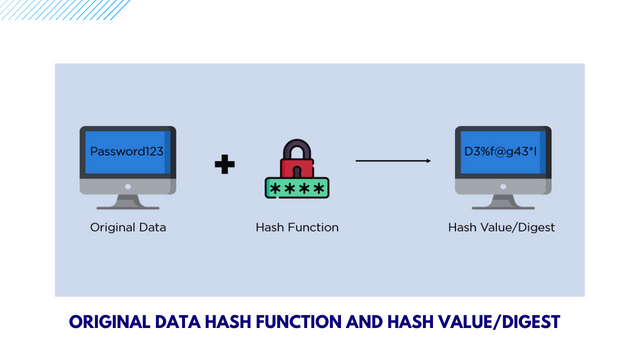
By looking at the above image, you will notice that it is the hash function that is responsible for converting the plaintext to its respective hash value or digest.
The original data, hash function and the hash value/digest you have seen on the image, are designed to be irreversible, which implies that the digest shouldn't in any way reproduce the original plaintext by any chance. In a situation where the input remains unchanged, despite the number of iterations, it is the hash function that will provide the exact output value.
| Applications of Hashing |
|---|
Hashing is made of two main applications which are;
- Password hashes
- Integrity Verification
Let's briefly look into them.
Password Hashes:
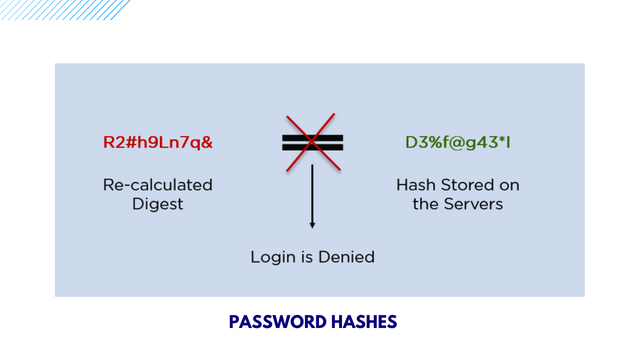
This will be best understood if you have been using website servers to log in to whatever platform you like. Having said so the password hashes help to convert your password into a hash value before storing it for you on the server.
Canvas
If you are using a browser like Google Chrome, to log in to Steemit or any website for the first time you will notice that the browser will ask you if you want to shave your password or not. The password hashes help you to compare the has value recalculate the value and store it in the database so you can log in without rei putting your past.
Integrity Verification:
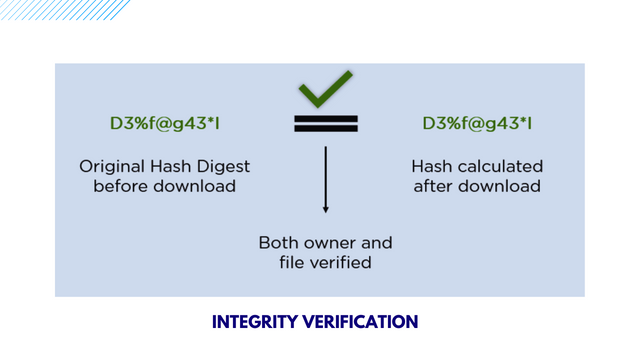
Normally on a website such as Steemit and others, we upload files which is the integrity Verification that helps to share your file with the hash as a bundle.
Canvas
To this as a user of a website, if you download a file, it will recalculate the hash and compare the hash to establish data integrity. Since we have discussed on this let's now discuss briefly about "SHA 256"
SHA algorithm
Secure Hash Algorithm is what SHA stands for. It is a modified version of the MD5 algorithm that is used for hashing of certificates and data. It is used to shorten the input of information into a smaller form that cannot be understood by using modular, compression functions and bitwise operations. Message Length, Digest Length, and irreversible are the key features of the SHA algorithm.
Conclusion
In this post, we have discussed what hashing means we also talked briefly about the two applications of hashing which are password hashes and integrity verification. Please note that this post is written for educational purposes.
https://x.com/AkwajiAfen/status/1813572326719701001
Note:- ✅
Regards,
@theentertainer