Fighting the autocratic technocracy - ZenCash brings blockDAG, Privacy, Partnership with IOHK and other big guns to help humanity

The Human Right to Privacy and Autonomy
In a previous article for the privacy coin NAV, I made a significant point to discuss the human right to privacy and autonomy. My thoughts on the matter haven't changed. I think that this topic is critical to discuss, and for new readers it's pertinent to go over those concepts again.
The degree of Human rights and freedoms you can enjoy are often largely dependent on your nation of residence, and are usually built upon foundations of implied and explicit rights. The United States; for example, enshrines the rights of their citizens within the Bill of Rights. Australia on the other hand, doesn't have a bill of rights, but the rights of citizens are implied or included in other documents of federation, law and so forth. Those rights are underpinned by a set of responsibilities. As citizens of respective countries and regions we must be responsible for the preservation and expansion of the aforementioned rights and freedoms.

More research:
- Privacy Australia shares many concepts and tools for people new to these ideas to get started on their journey.
- Wikipedia - The Right to privacy.
- Privacy International
- Data Protection Day 2018: A Global Perspective To Privacy
- The Privacy Advocates Resisting the Spread of Surveillance
<iframe src="
Speaker: Trevor Paglen Although people around the world are becoming increasingly aware of the United States' global geography of surveillance, covert action, and other secret programs, much of this landscape is invisible in our everyday lives. The drone war, for example, seems to happen "somewhere else" while surveillance programs take place among the (largely) invisible infrastructures and digital protocols of the internet and other communications networks. Moreover, the state agencies responsible for secret programs strive to make them as invisible as possible. In this talk, artist Trevor Paglen discusses his work attempting to "see" the various aspects of the secret state. In examples ranging from tracking spy satellites to foraging through the bureaucratic refuse of CIA front companies, Paglen will discuss methods used to identify and exploit structural contradictions in classified programs which render them visible, and comment on the aesthetics and politics of attempting to "see" secrecy.
<iframe src="
Speaker: Security researcher Jacob Appelbaum revealed what he calls "wrist-slitting depressing" details about the National Security Agency's spy programs at a computer conference in Germany on Monday where he presented previously unpublished NSA files. "They would be able to break into this phone, almost certainly, and turn on the microphone," Appelbaum said at one point as he re-inserted the battery into his mobile device. "All without a court, and that to me is really scary." Indeed, classified files shown later during his presentation revealed a device that for $175,800 allows the NSA or another license client to construct a fake cell tower than can allow officials to eavesdrop on texts and talks alike.
As I mentioned last time, I dedicated considerable time and effort studying Privacy, Surveillance, Ethics and Rights during my masters degree. The right to Privacy, and by virtue, the right to Autonomy is a fundamental human right recognized in the UN Declaration of Human Rights. Privacy underpins human dignity and other key values such as freedom of association and freedom of speech. Interestingly, I have read Australian legislation that allows us the freedom of thoughts, but not the full unfettered freedom of expression and speech. One could argue that privacy has become one of the most important human rights issues of the modern age.
The surveillance of human activity, including financial activity, could be argued to be in violation of these fundamental human rights. However, there are also societal boundaries, arguments for the rule of law and the safety of citizens from harm that a positioned contrary to this. It is a thin line that must be adequately defined and crossed with utmost caution. Modern technology has opened up the landscape to a position that was not able to be predicted by the religions, traditions and foundations that have been the bedrock of our civilisation. The Australian Privacy Charter says that Privacy is a value that underpins human rights, and that “A free and democratic society requires respect for the autonomy of individuals, and limits on the power of both state and private organisations to intrude on that autonomy”. The surveillance of individuals without consent violates their human rights and as such is morally wrong. The Charter goes on to say that “People should be notified if they are being watched in public places, or else the surveillance system should be obvious".
Is decentralised blockchain a public place?
If it was, then the surveillance of the activities on the public blockchain needs to be made obvious; and the people being monitored need to be notified. This is the situation for public places in Australia; but I am sure that I can make the assumption that other countries around the world don't play by these rules. This is where decentralisation can pose an ethical and moral hazard.
Researchers often claim that the invasion of privacy results in a depreciation of autonomy. It has been long argued that when individuals become aware of being monitored, they change their behaviour as a result. Despite this, some studies find that some individuals often not only accepted but even defended being monitored. The idea is raised that the surveillance systems are sold to those being monitored as something good, but rarely the discussion captures of whom it is good for. The ideals of higher efficiency, security or convenience are often toted as positive reasons for intrusive surveillance. Through the progression of these investigations however, it’s found that individuals find their behaviour changes in such entirety that there is a clear desertion between their identity exhibited under surveillance and the one expressed in “private life”.
Surveillance systems are inherently social control mechanisms. Their purpose is the supervision, monitoring or control of persons or places. They are implemented to control individuals' behaviors and their relations with others, and attempt to alter their behaviors. They challenge human identity, personal autonomy, and agency in different ways. Therefore the questions that arise between surveillance systems and individuals' sense of autonomy and agency need to be addressed. In this sense, philosophical dimensions of privacy constitute an important conceptual framework within which one can better understand how surveillance technologies influence the way individuals make sense of their behaviors, agency, personal growth, dignity and autonomy, and creation, maintenance and alteration of identity.

‘Round the clock’ surveillance of a given area becomes not only acceptable, but often requested in areas which raise a potential danger to the public. Law Enforcement has no objections in utilising surveillance as part of its protocols to better protect the public and in turn, lower crime and meet the increased demands of anti-terrorism. The technologies permit not only the recording of images and data but also attach the identities of those captured to these images and data.
As society moves into a new era of technological advancement the old notions regarding the infiltration of human rights, particularly which invade privacy need to be questioned and debated. Utilitarian motives skim over the rights of individuals and simply providing an opt-out solution may not always be feasible or acceptable and certainly may not circumvent the violation of one’s privacy, autonomy or agency. Corporations, needing not to abide by a specific rule set, are left to be self-policing. The direction of which is left in the hands of those that control them; leaving users of their products at the mercy of the morality and ethical viewpoints of those few individuals. Government surveillance fairs no better; with the only option left to the individual is to avoid areas under surveillance when signage is noted, breaching autonomy and the human right to freedom.
Privacy Coins
If you take the position that you will inevitably monitored, and take issue to this - you have to take action on your own and not rely on protection by government or self governance by corporation. You could face the argument that there is no privacy now. Banking and Finance is heavily regulated, audited, facing compliance and other obligations. There are a number of privacy coins within the cryptocurrency space. One that appears to be highly undervalued when I learn more about this space, is ZenCash.

ENTER ZENCASH - PUBLIC, PRIVATE, AND ANONYMOUS
- 21 million ZenCash cap - no premine, no ICO (Total eventual supply: 21,000,000 (21 million), as per Bitcoin
- PoW block reward: 12.5 ZEN
- Current number of coins: ? Updated every few minute?
- Division of each PoW block: 3.5% Secure Nodes reward , 8.5% Team's treasury, 88% miners reward.
- Coins per month: 216000 ZEN's
- Blocktime: 2.5 minute
- Reward halving period: every ~4 years, as per Bitcoin
- Algorithm: Equihash
- Designed for Long-Term Operation
- Thousands of Secure Nodes in operation - 3.5% of mining reward
- Treasury funds for development, support, marketing - 8.5% of mining reward
- Strong team & representative governance - Zen Blockchain Foundation
- Wallets and communication clients for international users
- Marketing globalization - tailored approach to different markets
- Secure Nodes provide a resilient, distributed network
What is ZenCash
Addressing multiple requirements and use cases; at it's core, ZenCash is a platform designed for private communications and private economic activity. It uses Cutting-edge cryptography and zero knowledge proofs enable fully anonymous peer to peer communications. ZenCash's incorporates a distributed and encrypted networking design and is resistant to traffic correlation and metadata analysis. ZenCash was launched May 30th, 2017 and it's goal/end-state is to be a platform for secure communications and for deniable economic activity. When ZenCash was forked from ZCash, there was no ICO or any Pre-mining. It based on the assertion that the current operating paradigm is one of hyper-regulation and surveillance. Many existing cryptocurrencies do not provide anonymity, and frighteningly, this includes some privacy coins. ZenCash addresses this by being designed to be fully encrypted as a both a network, as well as a means to send and distribute money. It is an evolution of the Zcash code base aimed at primarily enabling secure communications and resilient networking. As a distributed blockchain system with both public and private transactions, private messaging, fully encrypted communications, and a social and governance model designed for long term viability, Zen will contribute to the human right to privacy and provide the necessary networking infrastructure for people to securely collaborate within a border-less ecosystem.<iframe src="
ZenCash Introduction
So as alluded to, ZenCash is not just a coin; it is in fact a complete ecosystem of products, services, and businesses built around an enabling technology stack employing highly secure zero-knowledge proofs. Zero-knowledge encryption allows for private economic activity where the recipient, sender, and amount of activity is kept confidential. It is a distributed blockchain system leveraging the latest censorship-evading techniques, utilizing fully encrypted communications, and a social and governance model designed for long-term viability The system integrates multiple best-in-class technologies to form an open platform for permission-less innovation that can evolve with user preferences.
ZenCash requires secure nodes, which ensures the nodes maintain a basic standard of security and performance to enable the system remains distributed, resilient, and secure. By enforcing encrypted communication between nodes, and between nodes and wallets, Zen protects against eavesdropping and man-in-the-middle attacks. Zen also addresses a metadata weakness of other cryptocurrencies. By communicating in a potentially compromised fashion and then sending currency, the participants in a currency transaction are potentially exposed to identification by transaction correlators. ZenCash will incorporate secure messaging within shielded transactions, so users can agree on the transaction, send it, and then verify receipt.
Secure nodes are a feature that make node communication appear like any other encrypted internet traffic. This represents a significant milestone for users who reside in countries with restrictions surrounding cryptocurrency use. Secure nodes make ZenCash the world’s first end-to-end encrypted cryptocurrency network. The nodes run a full copy of the ZenCash blockchain, process transactions, and contain a valid SSL/TLS certificate, which authenticates the identity of users and grants permission to use encrypted communication.
ZenCash also rewards its node operators, who run secure nodes on Zen’s network, by granting them 3.5% of mining rewards. Operators must maintain a minimum of 42 ZEN, create and maintain a valid TLS certificate, have a server with sufficient processing capacity and memory to protect against DDoS attacks, maintain a full copy of the ZenCash blockchain, and operate the node at least 92% of the time.
ZenCash is also deploying a custom treasury model, which is provably fair, and transparent economic system to manage its governance. The system has a funding pool for governing proposal. Voting is delegated to trusted users, who are rewarded for their participation in the process.
Read more:
ZenCash Products

ZenCash - allows for easy transfer of value by using regular (T) and private (Z) addresses.
T addresses are regular addresses and transactions similar to bitcoin. Z addresses are called shielded addresses and leverage the latest privacy technology to obscure sender and recipient addresses, as well as amount sent.Balances in shielded addresses are private. If spending to one or more shielded addresses, the value stays private but any transparent addresses on the receiving end will deshield the token and reveal the value received on the blockchain.
ZenCash is compatible with Bitcoin- and Z-derived applications, exchanges, and wallets.
ZenChat - is the most secure messaging application on the market and can be used as a standalone product or embedded within our Wallets.
Users are able to communicate 1-on-1, through group messaging, or set up dedicated private channels. Channel communication costs a minimal amount of ZenCash to prevent clutter and spam.
ZenChat messages are stored permanently in the blockchain to prevent metadata leakage and are encrypted with algorithms such as AES-256 with Perfect Forward Secrecy (PFS), matching current standards of encryption for secure communication. Secure Nodes communication relay is non-traceable.
ZenPub - Gives users the ability to anonymously publish data, documents, and media in a way that is resistant to censorship.
The purpose of ZenPub is to allow individuals to freely publish data or information without fear of reprisal by allowing the individuals to publish from a shielded address (anonymous) via the InterPlanetary File System.ZenHide - Domain fronting is a versatile censorship circumvention technique that hides the remote endpoint of a communication.
It works at the application layer, using HTTPS, to communicate with a forbidden host while appearing to communicate with some other host, permitted by the censor.The key idea is the use of different domain names at different layers of communication. One domain appears on the “outside” of an HTTPS request–in the 9 DNS request and TLS Server Name Indication, while another domain appears on the “inside”–in the HTTP Host header, invisible to the censor under HTTPS encryption. A censor, unable to distinguish fronted and non-fronted traffic to a domain, must choose between allowing circumvention traffic and blocking the domain entirely, which results in expensive collateral damage.
Domain fronting does not require special cooperation by network intermediaries. We identify a number of hard-to-block web services, such as content delivery networks, that support domain-fronted connections and are useful for censorship circumvention.
ZENCASH ROADMAP
Check out the Roadmap on Trello.

ZenCash and IOHK are R&D Partners!

In January, ZenCash partnered with leading blockchain research and development company IOHK (the development team behind top 20 cryptocurrencies Cardano and Ethereum Classic). ZenCash and IOHK will collaborate on key research and development projects, including the creation of a protocol-level treasury model and a joint study on blockchain scalability. The partnership will enable ZenCash to implement a custom version of the IOHK reference treasury model. The model will ensure efficient allocation of decentralized resources and promote community-driven governance, and will also be integrated into the Cardano blockchain in the coming months. IOHK will also assist ZenCash in developing a core protocol upgrade to its blockchain, with a prototype expected by the second quarter of 2018.
<iframe src="
Previously, I have reviewed Cardano at length and I hold the IOHK team in very high regard. The partnership speaks volumes to me about the opinion of ZenCash from IOHK. In this case, the research projects will be lead by Prof. Roman Oliynykov, a cryptographer. Prof Oliynykov is an IT researcher, and lecturer.
Prof. Oliynykov’s team will provided prototypes and guidance to InfoPulse, a software engineering firm that has been contracted directly by ZenCash to provide resource and expertise in assisting the ZenCash engineering team with the implementation of the two research projects. At the time of writing this article, the eta for completion was not available.
<iframe src="
The first component of the IOHK research project is to implement a custom version of IOHK’s reference treasury model for efficient decentralized resource allocation and community-driven preference adoption in governance. The second key component of the IOHK research project is a core protocol upgrade to the ZenCash blockchain to address one of the primary issues in the blockchain and cryptocurrency space: Scaling. Read more here: ZenCash and IOHK Partner
Welto
In October 2017, ZenCash established a strategic partnership with Welto, an application that allows users to directly pay bills through their cryptocurrency wallets. The partnership lets users directly pay their bills in ZenCash within 24 to 48 hours. Users can also track the status of their ZenCash payment until the confirmation of its final receipt. Through the Welto platform, ZenCash users have the ability to monitor their spending and track the exchange rate of ZenCash to U.S. dollars, which is automatically updated every 15 minutes. The platform also allows users to schedule bill payment in ZenCash in advance and offers a finance manager system that tracks outgoing expenses in ZenCash.
The Team

ZenCash Co-Founder Rob Viglione is a former physicist, mercenary mathematician, and military officer with experience in satellite radar, space launch vehicles, and combat support intelligence. Contributions within the crypto space include being part of Zclassic’s core team, support to the Bitshares project, heading up BlockPay’s U.S. & Canada Ambassador program,and consulting for Bitgate. He’s currently a Ph.D Candidate in Finance at the University of South Carolina researching cryptofinance and teaching “Bitcoin & Blockchain Applications in Finance.” Rob holds an MBA in Finance & Marketing and the PMP certification.

ZenCash Co-Founder Rolf Versluis is an experienced business owner in the IT industry and owns a mid-size bitcoin and altcoin mining operation in Alpharetta, Georgia. Rolf has prior experience at Cisco systems, the semiconductor industry, and and as a nuclear-trained officer in the U.S. Submarine force. Rolf is an experienced data network security professional with over a decade of experience designing, installing, and troubleshooting systems.
Check out the full team: here
ZenCash Treasury
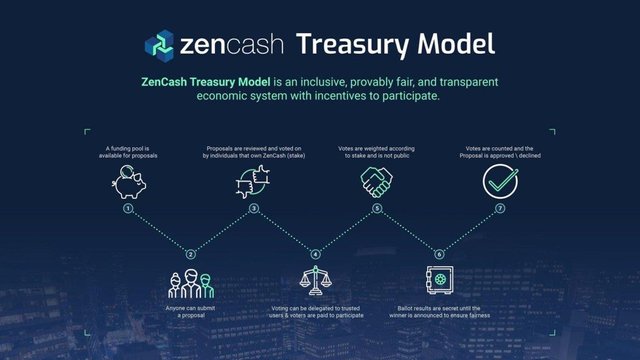
The ZenCash Treasury Model aims to be an inclusive, provably fair, and transparent economic system with incentives to participate. It is the arguably the result of the partnership with IOHK and Infopulse.
The ZenCash Treasury and Voting model is a Decentralized Autonomous Organization (DAO) model. As an interim solution, the legal entity for ZenCash, allocates 8.5% of mining rewards to fund integrations, engineering, marketing, research and development, etc. This funding model claims to enable ZenCash to continue growing regardless of whether the market is in bull or bear mode.
The partnership with IOHK is arguably fruitful, the two main deliverables are:
- DAO Treasury and Voting proof-of-concept that enables a programmatic approach to allocate resources.
- A Scalability Study to evaluate next generation blockchain solution to ensure ZenCash is able to scale.
The stated benefits of such a system are:
- A funding pool is available for proposals. The funding process occurs during a fixed amount of blocks (approximately one month). We’ll define this period as a treasury epoch. In order to vote, Zen stakeholders will have to lock an amount of ZEN as collateral at the beginning of each epoch. The stake will be kept on a special smart contract address that returns the funds at the end of the treasury epoch. Stakeholders will receive X amount of ballots, proportionally to the stake they have locked up. Stakeholders will not know the value of their stake.
- Anyone can submit a proposal, there will be a small submission fee to discourage spam.
- Eligible Zen stakeholders review and vote on proposals. Results are hidden using zk-SNARKS cryptography.
- Votes are weighted according to stake and is not public.
- Zen stakeholders can delegate voting responsibilities to trusted users.
- Ballot results are secret until the winner is announced to ensure fairness.
- Votes are counted. Approved proposals are sorted out in descending order, from the highest positive vote count to the least. The system will fund every proposal in this order until it reaches 90% of the funding pool.
- The remaining 10% of the funding pool is allocated to reward voters. At the end of the treasury epoch, the locked funds (stake) is returned to the voters along with their respective compensation (proportional to their stake) for participating in the voting process.
When is the ZenCash DAO going live?
IOHK is delivering the ZenCash DAO Treasury and Voting proof of concept in 2Q 2018. Read more here: ZenCash Treasury And Voting Model UpdateMining ZenCash
Anyone with a modern Graphic Card can mine ZenCash. Having said that, Antminer Equihash ASIC miners are here. A fantastic guide on how to mine ZenCash is at Blockonomi: How to Mine ZenCash: Complete Beginner’s Guide
Highly Recommended Reading: As I write this article, this blog post has appeared: ZenCash Statement On Potential Equihash Algorithm Change
Storing ZenCash
<iframe src="
A recent fantastic development for ZenCash is the integration of ZenCash support on the Ledger Hardware wallets, such as the Nano S. This was announced to much fun fair in April 2018. Read more here: ZenCash Is Now On Ledger Nano S Hardware Wallet Support! Need more help with a Ledger? Check out our review here: Ledger Nano S – Protect your coins with a hardware wallet. Official and 3rd party warm wallets available here.
Buying, Selling and Trading ZenCash
ZenCash is tradeable on leading exchanges including Bittrex, OKEx, Cryptopia, COSS, Upbit, and Trade Satoshi.
Interview with Rob from ZenCash
Q1. Regarding to your observations in Afghanistan; looking through the lens of the concept of a border-less economy - what is ZenCash doing in regards to adoption in countries that are remote, have low access to technology, low connectivity or excessive government prying and scrutiny?
We created ZenCash with the idea of providing financial freedom to the areas of the world that most need it. We have a global community with representatives, node operators, and users from many different countries. For instance, we incentivize the users who operate nodes on the Zen blockchain by financially rewarding them for their efforts. This is one effort that provides our user base globally with the opportunity to earn a basic income by supporting and securing the network. As we build out our platform and dApp ecosystem, we’ll be looking to develop products specifically for frontier markets that have their own unique requirements.
Q2. Depending on the source, a significant amount of people world wide are illiterate. Often these people are the most vulnerable. How does ZenCash plan to address ease of use, or ease of adoption for such people?
User experience has always been a priority to our team, and we currently have a 24-hour help desk and ticketing service to assist users who have trouble using Zen. This help desk allows for the ability of a user to talk to a real member of the ZenCash team who can help them with their issue. We design our customer support services to be as user-friendly as possible in order to encourage greater participation among our existing users and to incentivize more users to join the Zen platform.
Q3. What measures does the ZenCash team have in place to prevent infiltration and subversion from nefarious parties?
Our first goal is to be censorship resistant, and to accomplish this, we’re building out the industry’s most decentralized node network and working actively to decentralize each major subsystem of the project. A critical element of this is democratizing decision-making via an on-chain voting system to harden the system against stakeholder capture. Other attack vectors are always under consideration and we actually have a Red Team forming to develop active mitigation plans that have resources available to quickly deploy.
Q4. What obligations do you feel ZenCash has in the event of an investigation by a government body? For example, for a AML case - would ZenCash assist the authorities in any manner?
While ZenCash does advocate the human right to privacy, we do not condone illegal activity, such as that which would be subject to AML prosecution. The Zen Blockchain Foundation, which currently employs the team maintaining and building the ZenCash infrastructure, is a Delaware-based company and subject to applicable rules of the jurisdiction.
Q5. Is the project resistant to impact from Green Policy, Eco-Terrorism and other changes in the Energy Space? An example foundation for this statement might be POW mining and its energy consumption.
New blocks are generated with a memory-intensive proof-of-work (PoW) mining algorithm called Equihash. As a PoW minable project, Zen does require energy input to generate new blocks. As far as resource allocation goes, this is not an overly burdensome measure relative to the security it provides for the network and the ultimate social value we hope to achieve with the system.
Q6. What measures are in place to avoid political and ideological roadblocks (think btc vs bch / eth vs eth classic)? Or are these irrelevant in the ZenCash space?
We are very community-driven and focused on making decisions democratically. We are currently working on a treasury voting system that would allow all members of the community with Zen to vote on community proposals. We think that this measure will prove useful in avoiding political and ideological disputes on the Zen blockchain.
Q7. What is the ZenCash team position on assisting authorities with tracing payments made utilising the ZenCash network? Is the ZenCash team aligned politically or economically to any nations party or lobbying group?
ZenCash is not aligned politically or economically to any nation’s party or lobbying group; however, we do believe that cryptocurrency regulation is something that should and will come eventually. We hope to include ourselves in that conversation as actively as we can in order to fight for the ideals that we think are most important in legislation.
Q8. You've made the comment before that privacy is not ZenCash only use case; considering you see ZenCash having use cases in regular markets - how do you see the project will remain compliant with regulation changes in the future? Are you looking proactively to deal with potential regulation and bake that into your solution?
We are trying to be as involved as possible in conversation regarding regulation; however, Zen is a global project with a highly distributed user base and team. This means that regulations in one jurisdiction may not ultimately affect every Zen user.
Q9. From the standpoint of industry revelations and new technologies, what is the ZenCash methodology to adopt such things? Lead from the front, or allow others to "bug test"?
ZenCash is currently conducting research and development projects in conjunction with leading blockchain research and development company IOHK in order to stay on the forefront of emerging technologies within the industry. Our research with IOHK is then implemented via a prototype model and relentless tested to ensure its security and usability for a market-ready product. We also have an active and growing engineering team that’s innovating on chain efficiency, sidechaining solutions, and platform concepts that will enable growth into a wide new set of market verticals.
Q10. How does ZenCash see it's positioning within the cryptocurrency space as a whole? Eventually, due to forces such as Pareto distribution; a certain number of coins will inevitably rise to the top to dominate; how does ZenCash fit into a highly competitive model of many coins and solutions?
In order for any coin to remain highly competitive for the future, there are a number of issues that need to be overcome in terms of technological advancements in scalability and consensus. Zen is currently in the midst of thorough research and development projects on both topics. In addition, we believe it is important for coins to offer more products than just currency. This is why Zen has released services such as ZenHelp, ZenPub, and ZenTalk. We have many more products and services also planned to launch in the coming year.
Q11. What is the ZenCash teams position on ASIC Mining vs GPU Mining?
The edge case for ASIC mining is that there is a risk of being effectively taken over by a single mining company with asymmetric advantage in hardware. On the flip side, more hash power from powerful machines — if relatively evenly distributed across the community — is a very good thing for system security. In an ideal world, everyone would have a super ASIC, but we don’t live in that world and the reality is that sometimes a single manufacturer can dominate. In this sense, we’re quite sensitive to the network being captured and are actively looking at alternatives to mitigate that risk. Much of our community is in support of changing the hashing algorithm to have it remain optimized for GPU mining, so we take this option seriously and are investigating the best alternatives that weigh risks and opportunities.
Our community is very important to our future and a decision of this nature would have to actively source the opinions of involved parties.
Q12. Can you clarify the incentives for people to partake in ZenCash mining; over other cryptocurrencies, including the reward structure and how such funds are derived and allocated. Why would someone choose ZenCash over another coin? Is the decision in your opinion weighted economically or ideologically?
Both considerations certainly play a role and it’s dependent on the miner. Many people support the project on a values driven basis and so provide support in a number of ways, including mining Zen. Other professional miners are typically motivated by the return on investment and ZenCash has consistently remained one of the top three most valuable Equihash coins to mine.
Q13. Can you explain the decision to engage the role of the treasury, DAO and its importance to ZenCash?
Censorship resistance is one of our most important goals, so decentralizing every subsystem of the project is imperative. How resources are allocated and other decisions made is a major aspect of the project that has to be decentralized and so we’ve chosen from the start to build an on-chain voting system. This reflects our commitment to the core value of democratic participation.
Q14. What plans does the ZenCash team have for more exchange and broker availability? Are you actively pursuing this?
Our business development team is working nonstop to make ZenCash more accessible and useful across exchanges and real-world business applications. Just this last week we announced five new exchange listings, including Binance, and I would predict these types of integrations will accelerate now that the project is gaining critical mass.
Q15. Is there any new information you can share in regards to the IOHK partnerships; specifically in the realm of scaling and currency improvement? What do you think ZenCash will implement to improve the currency architecture; such as increasing TPS, using DAG? Spectre? Is there anything in place currently to be handle a large spike in transactional volume should that happen?
We’re happy to announce that we have a successfully delivered prototype version of an on-chain voting system from IOHK that we’re currently working to include another round of improvements before handing off to a production engineering team. Additionally, our engineers are working closely with IOHK scientists on our new sidechaining architecture, as well as continuing to make progress on the blockDAG protocol upgrade for massive TPS scaling. The latest news on the scaling research is that the team has converged on an augmented protocol from SPECTRE called PHANTOM as the base for what our implementation might entail. From here, we’re looking to further optimize and tailor the protocol to fit our system. These are very exciting times!
Additional Research and Reading
- ZenCash HomePage
- ZenCash White paper
- ZenCash Twitter
- ZenCash Facebook
- ZenCash Blog
- ZenCash Blog on Medium
- ZenCash Discord invite
- ZenCash Forum
- ZenCash Telegram
- ZenCash on Bitcointalk
- ZenCash YouTube
- ZenCash Reddit
- ZenCash CoinMarketCap
- ZenCash on Github
- ZenCash on wikipedia
- Australian Privacy Charter
- Human Rights Law Resource Centre Ltd . (2009, June). Surveillance in Public Places: A Human Rights Perspective
- PRIVACY AND HUMAN RIGHTS An International Survey of Privacy Laws and Practice
- zensystem.io BlockExplorer
- zenmine.pro/insight BlockExplorer
- zen-solutions.io BlockExplorer
- ZenCash CoinMarketCap
- ZenCash SecureNode video guide
- ZenCash SecureNode tracker
- ZenCash on CryptoCompare
- ZenCash on Whattomine
- ZenCash on CoinWarz
- ZenCash on CoinGeko
- ZenCash on Minethecoin
- ZenCash on BitMakler
- ZenCash on BitScreener
- ZenCash on Revex
- ZenCash and IOHK Partner
- Roadmap on Trello.
- About SuperNodes
- How to Build a ZenCash SuperNode
- SuperNode profitability calculator
- SuperNode Tracking & Payment System
- Rolf Versluis at Texas Bitcoin Conference
- Robert Viglione & Charles Hoskinson & Jun Dam
- Robert Viglione Panel discussion | Nexus Conference 2017
- Robert Viglione ZenCash Decentralized Governance
- ZenCash Secure Node System - Challenge Response Explanation
- ZenCash Secure Node System Overview
- ZenCash Mining Pools
- How to start mining ZENCASH (ZEN) on pool @cryptomkd
- Antminer Z9 mini
- ZenCash Is Now On Ledger Nano S Hardware Wallet Support!
Posted from my blog with SteemPress : https://hodlitbro.com.au/2018/06/02/fighting-the-autocratic-technocracy-zencash-brings-blockdag-privacy-partnership-with-iohk-and-other-big-guns-to-help-humanity/