The Biometric ID Management System
The Bio-Metric ID management system
A bio-metric system must be managed so that all of the user’s personal data that the system can access is considered and protected. Bio-metrics require users to log into a given system utilizing bio-metric data. When a user must access a bio-metric controlled lock, it can take the image being scanned and make active comparisons to what is already captured, it is here that a bio-metric ID management system enters the picture. Bio-metric ID management systems provide the user with the means to provide their personal bio-metric data instead of a token, PIN, or password. The ID management system contains at least four elements in addition to seven key requirements. It is of utmost importance that the ID management system carries a diverse range of features and functions. This makes managing the ID management system easier for the individual user.
Verification and identification are the generally present functionalities that are provided for. Personal bio-metric data is generally housed on one server. That server is then connected to the system of bio-metric locks, thus establishing, a secure network. When someone scans their fingerprint or other piece of bio-metric data at a bio-metric lock, a request is sent to the server to attempt verification and identification of the user requesting access to said lock. Some of the advantages of a Bio-metric ID management system are accountability, increased security, added convenience and information that is precise in nature. That being said, there are also several risks such as finite limitations, one point of vulnerability and spoofing.
Now that you have a heightened security system in place that contains one or more locks, the need will arise for some type of system that actively manages the personal bio-metric data of authorized users. In order for all this to work, you need the ability to add users, monitor those users, which locks they accessed and with time-stamps. We must also be able to delete users and physical control/manage each and every lock. Many bio-metric identification systems have an on-board management system which simplifies its process. When I started working on this paper I came across something called Supremas’ Bio-station T2. This system came with an on-board management system termed Bio-star. When the times comes to shop for a bio-metric system it is not enough to simply find a good system but to also find a system with a great management system. Some companies with seemingly greater resources might shop for separate systems when they can afford to and there is a specific need that the on-board system does not contain.
As with any identification system, there requirements that are key to focus on when choosing or purchasing a system. These include such requirements as self-service to user data, resetting of user authentication information, work flow, provisioning and de-provisioning. There must also be a method or means to manage lost user authentication data. All of these functions can make or break a bio-metric ID management system.
When speaking about self-service to user data, we refer to the ability to add/modify/delete any new or currently existing users if that user’s bio-metric data becomes compromised. An example of this would be to add data for additional finger prints so that if a fingerprint is compromised, it can be shut off without disabling the authorized users access. In contrast, it is significantly easier to replace a compromised password as you can’t replace a finger once it is compromised. Addressing this, some bio-metric systems also use a PIN in conjunction with the bio-metric data to for a two-step authentication method.
This takes us into the ability to reset a password and manage those that become lost or compromised. This would seem basic common sense but there are many systems out there that do not make this method easy or even possible in some instances.
There are generally two functionalities that a bio-metric recognition system performs. These would be verification and identification. We want to make sure that a user attempting access to a system is, in fact, the actual user that is authorized. An example of this would be a police officer taking a fingerprint from someone to run a check and make sure they are who they are claiming to be. In identification, we ensure that the authorized user is actually present and authorized in the systems database. The second functionality identification, is making sure that the user attempting to use the bio-metric system is ran against the database to verify they exist in the database. As in the previous example, if the police officer runs the fingerprint and gets no results, he could conclude that the person in question has never been in the system.
There are only two possible results this bio-metric system could come up with and that would be a positive result or a negative result. When a positive result occurs, the person is in the system, negative, they are not. Each one of these bio-metric systems either operate on or are attached to a server on the network. This is where all the user data is stored and the biometric locks are attached to the same network system. When a user accesses a lock, the identification and verification requests are directed to the network server.
Bio-metric ID management systems, as with just about all other systems, have pros and cons. An example of the pros would be heightened security, added convenience, better accountability, and more precise data.
The bio-metric ID system is kept updated like any other software and updates are performed whenever the vendor puts out a patch or update. These updates ward of possible hacks, viruses or even fix bugs found in the system. This ensures that the user data stays as private as possible. Easily, a great advantage to these systems is also in convenience. A great bio-metric ID management system can greatly simplify things if you have a large organization. In this case, all you should have to do is perform a search on user data to find it. Things such as name, id numbers, etc should be fully indexed and searchable with a provided edit button that instantly displays all possible user options. That being said, there exists some pieces of software that are very poorly designed destroying the pro of convenience. This can make an administrators life extremely confusing.
The accountability of your users and what they can access is very important. In example, it is very easy to lose or have stolen, things like badges and pins. Bio-metrics can add greater accuracy ensuring that whichever user is attempting access to the bio-metric system are in fact really who they claim to be. These days data that is that precise is a commodity. Prior to computers, users that had to gain access to restricted areas interacted with an actual person checking their credentials. This can create a real problem for the new guy that hasn’t figured out who everyone is yet. In this case, it is feasible that someone could gain unauthorized entry by using fake or counterfeit credentials.
The risk of freezing up a bio-metric ID management system is a concern also. Things like limitations, points of vulnerability and other miscellaneous risks can bring a system to its knees. Bio-metric technology is constantly adapting, where a limitation exists today could be gone tomorrow with so little as a patch or update. As with all technology, it is a state of evolution and perpetual upgrade.
There is one large problem with bio-metric ID management systems and that is in the data that is stored on the server. Generally, without knowing any better all user data is stored on one central server. If a person were to hack into this server, they would gain access to user data site wide. That is one main issue with management systems, because all data must reside on a central server that all locks have the ability to access, it usually means all data is on one server.
Since we cannot reset bio-metric data like a password, that makes it unique. If it is hacked it cannot just be replaced. A different finger or other eye would have to be used. We’ve all seen the movies where a person’s finger is cut off and used to access a finger print reader. This is known as fingerprint spoofing and initiated the invention of a liveliness detector that can determine if the bio-metric data is alive or dead. This works to thwart putty but does not counter thin silicone layer on the finger pad. There are also great risks in the enrollment of the system as well as its administration.
A person in the charge of enrolling users could enroll an unauthorized person that gives them access all system locks. This creates the need for greater oversight that assists in reducing these issues, as well as, ensuring that policies are updated along with the software on a regular interval.
To conclude, bio-metric ID management systems must have a location to house user data as well as a program to manage it. The bio-metric ID management system lets a user edit their own personnel data, manage their passwords, their tokens, or PIN. This ID management system is made up of four core elements: data editing tools, a directory, a system access regulator, and a valid system of reporting.
As well, there are seven areas that an organization must focus on in their ID management system. Those are: registration, storage, assurance, protection, issuance, life cycle management & system management.
Generally, two functions are provided, verification and identification. Verification ensures the who and identification verifies the existence of the verified user in the system.
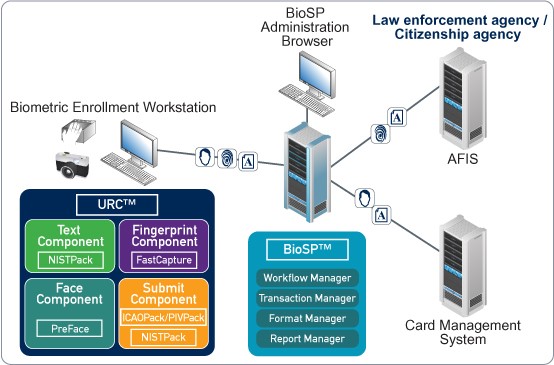
Examples of Biometric Workflow:

References
Biometric identification systems. (n.d.). Retrieved June 15, 2016, from http://www.technovelgy.com/ct/Technology-Article.asp?ArtNum=12
Biometric Single Sign-On & the| Biometric System. (2014, May 31). Retrieved June 15, 2016, from http://www.iritech.com/blogs/biometrics-single-sign-ons/
Biometric Solutions for Citizen ID, Passports, Elections. (n.d.). Retrieved June 19, 2016, from http://www.aware.com/biometrics-software-solutions/citizen-id-and-elections/
¿Qué es la biometría?, (n.d.). Retrieved June 19, 2016, from http://www.aware.com/portfolio-items/que-es-la-biometria-documento-informativo/
Dimitriadis, C., & Polemi, D. (2003). Biometrics Risks and Controls. Retrieved June 15, 2016, from http://www.isaca.org/Journals/archives/2004/Volumes/4/Pages/BiometricsRisksandControl
Jain, A. (2004, June 5). Biometric authentications. Retrieved June 15, 2016, from http://www.scholarpedia.org/articles/Biometricauthentication
Newman, Robert. Security and Access Control Using Biometric Technologies. Cengage Learning, 09/2009. VitalBook file.
Trader, J. (2013, April 6). Advantages of a Biometric ID Management System. Retrieved June 15, 2016, from http://blog.m2sys.com/biometrichardware/advantagesbiometricidentification-management-system/
Trader, J. (2013, July 21). Liveness Detection to Fight Biometric Spoofing Retrieved June 15, 2016, from http://blog.m2sys.com/scanningandefficiency/livenessdetectionfight-biometric-spoofing/
Waters, J. (2003). The ABC’s of ID Management. Retrieved June 15, 2016, from http://www.csoonline.com/articles/212038433/identitymanagement/the-abcs-of-identity-management.html