Reverse CSI 10 – Twin Towers Radio Drama, Con Air Marcy's Ganci Snuff, First Ladies' IP Amerithrax Bridge

David 'Sherlock' Hawkins, co-founder of Abel Danger, is developing 3-act CSI storyboards for radio dramas and theatre plays involving scene-by-scene reverse engineering of the Twin Towers attacks of 9/11; the alleged deployment of snuff-film SWAT teams by Field McConnell's sister, Kristine "Con Air" Marcy, to kill high value targets such as Peter James Ganci Jr, Chief of the New York City Fire Department, and the alleged use of the federal bridge certification authority by former First Lady / IP lawyers Hillary Clinton and Michelle Obama to 'spin' media and Senate leaders with an Amerithrax false flag attack and patented devices in the custody of Serco's investment banker N M Rothschild & Sons Ltd.
In Reverse CSI 10, Hawkins identifies images and references for a storyboard collage to promote his Twin Towers Radio Drama in a joint venture with Jason Goodman's Crowdsource The Truth program which Jason describes as an Open Source Fact Checking "Truth Engine" and political social media movement.
In the 1938 radio drama War of the Worlds, Orson Welles narrated a fictional account with fake news injects of an attack by aliens from Mars who ultimately die because they have no resistance to pathogens Earth.
In the radio drama Twin Towers, David Hawkins will narrate an account where crisis actors inject news of the real-world 9/11 attack on America allegedly executed by Con Air SWAT teams booked on Kristine Marcy's Justice Prisoner and Alien Transportation System (JPATS) and an account of the HVT deaths of prospective expert witnesses such as the late Peter Ganci associated with patented devices including biological bullets or anthrax sabotage spore powder (SSP) in the custody of Serco's investment banker N M Rothschild & Sons Ltd.
Patreon sponsors are invited to help David and Jason develop the reverse engineering CSI storyboard approach to radio dramas and/or theatre plays where the audience is taken through 9 scenes in 3 acts focused on Act 1: Script & Spot, Act 2: Shoot & Snufff, Act 3: Spin & Spoil.
https://www.patreon.com/reverseCSIstoryboards
https://www.patreon.com/crowdsourcethetruth
Images & Video for storyboard collage
CSI 10 – Images for consideration for promo collage for Twin Towers Radio Drama


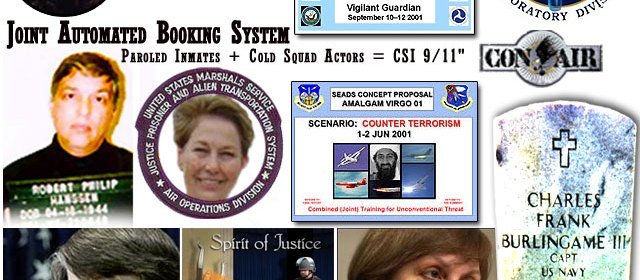


References for Twin Towers Radio Drama
"Digital Fires Instructor Serco – [Marine Corps Base!] Camp Pendleton, CA Uses information derived from all military disciplines (e.g., aviation, ground combat, command and control, combat service support, intelligence, and opposing forces) to determine changes in enemy capabilities, vulnerabilities, and probable courses of action."
"The War of the Worlds" is an episode of the American radio drama anthology series The Mercury Theatre on the Air. It was performed as a Halloween episode of the series on Sunday, October 30, 1938, and aired over the Columbia Broadcasting System radio network. Directed and narrated by actor and future filmmaker Orson Welles, the episode was an adaptation of H. G. Wells' novel The War of the Worlds (1898). It became famous for allegedly causing mass panic, although the scale of the panic is disputed as the program had relatively few listeners.[3]
The program began with the theme music for the Mercury Theater on the Air and an announcement that the evening's show was an adaption of The War of the Worlds. This was followed by a prologue read by Orson Welles which was closely based on the opening of H.G. Wells' novel. The next half hour of the one-hour broadcast was presented as typical evening radio programming being interrupted by a series of news bulletins. The first few updates interrupt a program of dance music and describe a series of odd explosions observed on Mars. This is followed soon thereafter by a seemingly unrelated report of an unusual object falling on a farm in Grover's Mill, New Jersey. Another brief musical interlude is interrupted by a live report from Grover's Mill, where police officials and a crowd of curious onlookers have surround the strange cylindrical object. The situation quickly escalates when Martians emerge from the cylinder and attack using a heat-ray, abruptly cutting off the panicked reporter at the scene. This is followed by a rapid series of increasingly alarming news bulletins detailing a devastating alien invasion taking place across the United States and the world, climaxing with another live report describing giant Martian war machines releasing clouds of poisonous smoke across New York City. After a short break, the program shifts to a more conventional radio drama format and follows a survivor dealing with the aftermath of the invasion and ultimately discovering that the Martians have been defeated not by humans, but by microbes.
The illusion of realism was furthered because the Mercury Theatre on the Air was a sustaining show without commercial interruptions, and the first break in the program came almost 30 minutes after the introduction. Popular legend holds that some of the radio audience may have been listening to Edgar Bergen and tuned in to "The War of the Worlds" during a musical interlude, thereby missing the clear introduction that the show was a drama, but research in the 2010s suggests that happened only in rare instances.[4]:67–69
In the days after the adaptation, widespread outrage was expressed in the media. The program's news-bulletin format was described as deceptive by some newspapers and public figures, leading to an outcry against the perpetrators of the broadcast and calls for regulation by the Federal Communications Commission.[3]The episode secured Welles's fame as a dramatist."
"Peter James Ganci Jr. (October 27, 1946 – September 11, 2001) was a career firefighter in the New York City Fire Department killed in the September 11 attacks. At the time of the attacks, he held the rank of Chief of Department, the highest ranking uniformed fire officer in the department.[1]
Career[edit]
Prior to joining the Fire Department, Ganci served in the 82nd Airborne Division in the War in Vietnam.[2][3]
Ganci joined the New York City Fire Department in the 1960s, serving in engine and ladder companies in Brooklyn and the Bronx, beginning with Engine Company 92 in the Bronx and then subsequently Ladder Company 111.[1][4]
During this time the FDNY, a time described by The New York Times as "an era of crisis", fire companies battled arson fires almost continually in the city's poorest neighborhoods. Ganci was promoted to lieutenant in 1977, captain in 1983, battalion chief in 1987, and deputy chief in 1993, when he was working in Bedford-Stuyvesant, Brooklyn. In 1994 Ganci was made the head of the Bureau of Fire Investigation following the appointment as fire commissioner of Howard Safir, who needed a uniformed chief to address conflicts between fire marshals and uniformed firefighters, a conflict whose resolution Safir credits to Ganci. In January 1997 Ganci replaced his boss Donald Burns as Chief of Operations, the second highest uniformed position in the Fire Department.[1][5]
During the September 11 attacks[edit]
On the morning of the attacks, Ganci's best friend and executive assistant, Steve Mosiello, was going to drive Ganci to court, where Ganci had been scheduled for jury duty.[6] Immediately after American Airlines Flight 11 hit the North Tower (1 World Trade Center), however, Ganci, Mosiello, and Chief of Operations Danny Nigro rushed there from their command post in downtown Brooklyn.[7] Driving there in Ganci's car, they arrived on the scene in less than 10 minutes, and set up a command post on a ramp leading to a garage near the North Tower, in time to see United Airlines Flight 175 hit the South Tower.[6] According to Newsday, Ganci and others were in the basement of the South Tower when it collapsed, but they dug themselves out of the rubble that had caved in on them.[7] Ganci ordered his men to set up a different command post in a safer location, further north of the buildings, and ordered Mosiello to acquire backup. However, Ganci himself returned to the buildings,[6] coming to stand in front of 1 World Trade Center, where he was directing the rescue efforts with a multichannel radio, when the building collapsed. He and Mayor Rudy Giuliani had spoken just minutes before, when Giuliani had left for his command post, following Ganci's instruction to Giuliani, the fire commissioners and others to clear the area because it was apparent the North Tower would fall. However, Ganci himself did not evacuate the area, saying, "I'm not leaving my men", and remained at that location with William Feehan, first deputy commissioner of the fire department.[7]
Ganci and Feehan were killed when the second tower collapsed.[7] After a rescue dog located Ganci's body,[8]Ganci's fire team, including Moseillo, pulled it from beneath four feet of debris.[6][7] Ganci's former supervisor, Howard Safir, commented that Ganci "would never ask anyone to do something he didn't do himself. It didn't surprise me that he was right at the front lines. You would never see Pete five miles away, in some command center."[1]
Ganci was survived by his sisters, Mary Dougherty and Ellen Ganci, his brothers, Dan and Jim,[7] his wife, Kathleen, their sons, Peter Ganci III (a firefighter assigned to Ladder Company 111 in Brooklyn) and Christopher (also a firefighter in the FDNY[9][10]), and their daughter, Danielle, who lived with Ganci in Massapequa, New York.[1]"
"Con-Air" in 1/6 San Diego Union Tribune [news article] From: [email protected] (Glenn Campbell, Las Vegas) Date: Tue, 7 Jan 1997 10:37:42 -0800
Subject: "Con-Air" in 1/6 San Diego Union Tribune [news article]
A correspondent passed this 1/6 article on to us. He adds: “The article in the hard-copy paper has a couple of pictures to go with the story (no pix on-line). One picture shows the shoulder patch on the aircrew uniforms, another shows prisoners lined up about to board a Convair 580. The paint job on the plane looked like INS or maybe US Marshals Service, it was a green stripe with an eagle forward of the door."
From http://www.uniontrib.com/uniontrib/mon/news/news_1n6conair.html
(Password required)
The article is relevant here because of recent discussion of Con-Air flights using the "Janet" company name.
…..
In the Disney film, Nicolas Cage plays a hapless prisoner who wanders into a hijack plot aboard a Marshals Service plane carrying a group of high-security inmates.
The Hollywood marshals rough up some of the prisoners, and the plane crashes, leaving the real Marshals Service frowning on the silver screen’s invention, said Kristine Marcy, a top official in charge of detentions.
"We don't beat up our prisoners, and our planes certainly don’t crash," Marcy said on a recent trip to San Diego, where she was trying to find more jail space for federal prisoners.
……
Marcy said the air transportation system inspires a high level of commitment in its personnel.
"People are always willing to be on standby or to work overtime," she said, noting that the planes are not always used for prisoner transport.
After a hurricane flattened parts of the Virgin Islands last year, the prisoner transportation system flew in some of the first reinforcements to help establish law and order, she said.
After the Oklahoma City bombing, the airline flew evidence to the FBI crime laboratory [Quantico] in Washington, D.C., she said."
"History - National Prisoner Transportation System On August 20, 1985, the U.S. Marshals Service acquired its first Boeing 727 used for prisoner transportation. The Marshals Service operated the National Prisoner Transportation System, one of the largest transporters of prisoners in the world."
"Serco Awarded $95 Million Patent Classification Contract with the U.S. Patent and Trademark Office November 30, 2015 RESTON, VA – November 30, 2015 – Serco Inc., a provider of professional, technology, and management services, announced today the Company has been awarded a patent classification services contract with the United States Patent and Trademark Office (USPTO). Serco will provide initial patent classification and reclassification services to support USPTO's core mission of examining, granting, and disseminating patents and trademarks. The recompete contract has a one-year base period with four one-year option periods, and is valued at $95 million over the five-year period, if all options and award terms are exercised."
"The 2001 anthrax attacks, also known as Amerithrax from its Federal Bureau of Investigation (FBI) case name, occurred within the United States over the course of several weeks beginning on September 18, 2001, one week after the September 11 attacks. Letters containing anthrax spores were mailed to several news media offices and two Democratic U.S. Senators (Tom Daschle and Patrick Leahy), killing 5 people and infecting 17 others. According to the FBI, the ensuing investigation became "one of the largest and most complex in the history of law enforcement".[3]"
The attacks followed a week after the September 11 attacks which had caused the destruction of the World Trade Center in New York City, damage to The Pentagon in Arlington, Virginia and the crash of an airliner in Shanksville, Pennsylvania. The anthrax attacks came in two waves. The first set of anthrax letters had a Trenton, New Jerseypostmark dated September 18, 2001. Five letters are believed to have been mailed at this time to: ABC News, CBS News, NBC News and the New York Post, all located in New York City and to the National Enquirer at American Media, Inc. (AMI) in Boca Raton, Florida.[16] Robert Stevens, the first person who died from the mailings, worked at the Sun tabloid, also published by AMI, died on October 5, 2001, four days after entering a Florida hospital with an undiagnosed illness that caused him to vomit and be short of breath.[17][18] Only the New York Post and NBC News letters were found;[19] the existence of the other three letters is inferred because individuals at ABC, CBS and AMI became infected with anthrax. Scientists examining the anthrax from the New York Post letter said it appeared as a clumped coarse brown granular material looking like dog food.[20]
Two more anthrax letters, bearing the same Trenton postmark, were dated October 9, three weeks after the first mailing. The letters were addressed to two Democratic Senators, Tom Daschle of South Dakota and Patrick Leahy of Vermont. At the time, Daschle was the Senate Majority leader and Leahy was head of the Senate Judiciary Committee. The Daschle letter was opened by an aide, Grant Leslie, on October 15, and the government mail service was shut down. The unopened Leahy letter was discovered in an impounded mailbag on November 16. The Leahy letter had been misdirected to the State Department mail annex in Sterling, Virginia, because a ZIP code was misread; a postal worker there, David Hose, contracted inhalational anthrax.
More potent than the first anthrax letters, the material in the Senate letters was a highly refined dry powder consisting of about one gram of nearly pure spores. A series of conflicting news reports appeared, some claiming the powders had been "weaponized" with silica. Bioweapons experts who later viewed images of the attack anthrax saw no indication of "weaponization".[21] Tests by Sandia National Laboratories in early 2002 confirmed that the attack powders were not weaponized.[22][23]
At least 22 people developed anthrax infections; 11 of which contracted the especially life-threatening inhalational variety. Five died of inhalational anthrax: Stevens; two employees of the Brentwood mail facility in Washington, D.C. (Thomas Morris Jr. and Joseph Curseen) and two whose source of exposure to the bacteria is still unknown; Kathy Nguyen, a Vietnamese immigrant resident in the borough of the Bronx who worked in New York City, and the last known victim Ottilie Lundgren, a 94-year-old widow of a prominent judge from Oxford, Connecticut.
Because it took so long to identify a culprit, the 2001 anthrax attacks have been compared to the Unabomber attacks [Marcy has Ted Kaczynski in ADX Florence on 9/11] which took place from 1978 to 1995.[24]"
"MONDAY, MAY 28, 2007 Technical Intelligence in Retrospect: The 2001 Anthrax Letters Powder
Technical Intelligence in Retrospect: The 2001 Anthrax Letters Powder
Authors: Dany Shoham; Stuart M. Jacobsen
DOI: 10.1080/08850600600889027
Published in: International Journal of Intelligence and CounterIntelligence, Volume 20, Issue 1 March 2007 , pages 79 - 105
Introduction: In a sense, the very fact that the late 2001 anthrax letters attack on the United States has still not been solved is no less meaningful and important than that unprecedented act of bioterrorism itself. A wide range of far-reaching implications - geopolitical, legal, strategic, technological, scientific, and medical - emanate from that failure. An attempt is made here to take an integrated look into some of these various aspects so as to gain a better understanding of this potentially colossal event. Special attention is paid to a reconstructive analysis of the sabotage spore powder (SSP) contained in the lethal letters, and its structure. The anthrax bacterium is a pathogen of major concern, whose potency is afforded by the aerial dispersibility attained through the peculiar powdery texture of the material used for this act of bioterrorism. This peculiarity constitutes a key attribute, which can be traced and deciphered through retrospective technical intelligence that may lead to the SSP's provenance. It further demonstrates the significance of technical intelligence at large as a prime tool of the intelligence services.
In contrast to the wealth of empirical data collected and published with respect to the specific anthrax Ames strain of the 2001 letter attack, the resultant medical cases, and the dispersal of the SSP, a relative paucity of information has been brought out regarding the structure and composition of the SSP itself. That still poses an enigmatic, extremely complex intelligence issue that needs to be elucidated, for numerous reasons. Consequent to the absence of definite intelligence regarding the SSP's provenance, the need to apply technical intelligence methodologies seems to be vital. The Federal Bureau of Investigation (FBI), the Central Intelligence Agency (CIA), and the Defense Intelligence Agency (DIA) have all been deeply involved, indeed, in an attempt to meet this need."
"Evonik Degussa GmbH's Hydrophobic silica Priority date 1999-12-22 2007-10-16 US7282236B2 Grant Abstract Methods of making hydrophobic, pyrogenically produced silica having a tamped density, of 55 to 200 g/l. Said silica is produced by hydrophobizing pyrogenically produced silica by reaction with a halogen free silane and then compacting it with means consisting of a roller compactor or a belt filter press. The silica may be used for the production of dispersions."
"Police conclude search of Starnet [which forfeited its network to IRS and Customs SWAT teams]
CBC News · Posted: Aug 24, 1999 11:26 AM ET | Last Updated: August 24, 1999
Police have wrapped up several days of searching the offices of Starnet Communications in Vancouver. They entered the company offices and homes of some directors on Friday.
Police were looking for evidence of illegal gambling, distributing child pornography, and money laundering.
Since the raid, Starnet officials say police just don't understand their business.
The search warrant details 18 months of police investigation. It traces a network of companies registered in American and Caribbean jurisdictions.
The warrant also identifies Vancouver as the centre of Starnet's operations, even though this is a grey under Canadian law.
Police note that Starnet's revenues grew dramatically in the past two years, from betting and sex shows and from lucrative licensing agreements for its gaming software.
The investigations and pornography from company sites were grounds for Friday's raid and seizure of company materials.
RCMP Constable Peter Thiessen says investigators left Starnet offices yesterday morning. He says, "They spent the better part of three days going through the business. And as a result of that search the investigation is continuing, but no charges have been laid."
Starnet's many investors were spooked by the raid. Share prices dropped almost 70-percent on Friday. However, the company insists the raid had minimal effect on its operation. Stocks rose slightly yesterday after a day of very heavy trading.
In written statements, company CEO Mark Dohlen said the Wall Street Journal calls Starnet the leader in Internet gaming and entertainment. He says companies like his, those on the cutting edge, are often misunderstood.
Yesterday, Starnet announced it will sell off the sex side of its business. It plans to focus more resources on gaming.
The Police investigation is expected to last for several more months."
"The White House FBI files controversy of the Clinton Administration, often referred to as Filegate,[1] arose in June 1996 around improper access in 1993 and 1994 to FBI security-clearance documents. Craig Livingstone, director of the White House's Office of Personnel Security, improperly requested, and received from the FBI, background reports concerning several hundred individuals without asking permission. The revelations provoked a strong political and press reaction because many of the files covered White House employees from previous Republican administrations, including top presidential advisors. Under criticism, Livingstone resigned from his position. Allegations were made that senior White House figures, including First Lady Hillary Rodham Clinton, may have requested and read the files for political purposes, and that the First Lady had authorized the hiring of the underqualified Livingstone."
"Barack Obama & the gay connection
By Eli
May 4, 2016
Fox News host Greg Gutfeld stated that "Obama is now out of the closet" after the president announced his support for gay marriage. In response, former George W. Bush speechwriter, David Frum, stated, "You cannot 'get' Gutfeld's joke unless you 'get' that a large part of his audience ardently believes that Obama is in fact gay, that his marriage is a sham, and that Mrs. Obama leads a life of Marie Antoinette–like extravagance to compensate for her husband's neglect while he disports himself with his personal aides". Like many gay men, Obama is not monogamous and therefore most of his relationships overlap, sometimes even for years. Consequently, like most of his public persona, his marriage to Michelle Obama is a colossal hoax which has been perpetrated on the American public for the sake of politics.. The notion that the president is gay is corroborated by the fact that Obama routinely goes on business trips and vacations without his wife while Michelle often travels domestically and internationally without her husband, something unprecedented for a sitting U.S. President and his First Lady.
The Obama's are so distant they've spent a record third straight Valentine's Day apart. Obama generally spends the romantic holiday with male "friends" while Michelle is often accompanied by her daughters or mother. In order to help sell the notion that Barack and Michelle are indeed a real-life couple, a propaganda film entitled "Southside with You" (2016) about the Obama's first date was released at the Sundance Film Festival on January 24, 2016. As depicted in the report entitled "Was Barack Obama Married in College?", Obama has been photographed on multiple occasions wearing a ring on his ring finger prior to his engagement to Michelle in 1991.
Since Obama was groomed by the CIA in Switzerland to become America's first dictator, every part of Obama's life has been carefully scripted. Consequently, the ring worn by Obama was evidently part of a script designed to: a) draw attention away from the fact that Obama is a homosexual, and b) serve as a sign for women to "stay away" from Obama lest it become apparent that he has no interest in them. In the event that Obama is fully outed as being gay during his presidency and subsequent dictatorship, a story about the ring will likely become a national scandal over speculation about a possible engagement or marriage to a woman prior to Michelle. Needless to say, like the marriage of Bill and Hillary Clinton, the Obama's marriage is fraudulent in nature and only maintained for public consumption.
"Nortel Networks Ltd's Method for efficient management of certificate revocation lists and update information Priority date 1995-11-13 1997-12-16 US5699431A Grant Abstract A method which allows implementation of the revocation of public-key certificates facilitates engineering of certificate revocation lists (CRLs). It solves the practical problem of CRLs potentially growing to unmanageable lengths by allowing CRLs to be segmented, based on size considerations or priority considerations related to revocation reasons. The method is used to distribute CRL information to users of certificate-based public-key systems. It is also applied more generally to update any field in a certificate by reference to a secondary source of authenticated information."
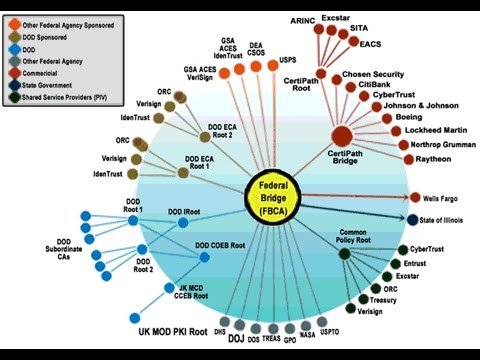
"States Work with Feds for PKI Interoperability BY: Drew Robb | August 14, 2001 The 1977 epic A Bridge Too Far recaptures one of the most fruitless battles of World War II -- a costly attempt to capture six bridges that connected Holland and Germany. A major gamble from the outset, the campaign led to defeat and more Allied casualties than in the entire Normandy invasion. Fortunately, the folks at the Federal Bridge Certification Authority (FBCA) are having an easier time of it in an initiative aimed at handling some of the thornier questions in government security -- exactly who do you trust when it comes to the handing out and acceptance of digital certificates during e-Government transactions, how do states and federal agencies interoperate to make such certs usable across the government spectrum, and what will it really take to establish "digital" trust to make paperless e-government a reality? The Cast FBCA has gathered an impressive array of federal agencies, states and vendors in an effort to make the initiative a success. On the federal side, there is heavy involvement by the Department of Defense, National Security Agency, General Services Administration, Treasury and the Federal CIOs Council. From the vendor community Entrust Technologies and Baltimore Technologies are directly involved in the FBCA from the technology side, but other PKI/security vendors such as RSA, Cylink, Verisign and Spyrus are also coordinating with the project. At the state level, Illinois is working closely with the FBCA in an interoperability pilot that will probably form the basis of how states share digital certificates with federal and possibly commercial entities. "We are just in the process of developing the cross-certification agreement between FBCA and the State of Illinois CA so we have not tested any applications yet," said Brent Crossland, Deputy CIO for the State of Illinois. "Our timetable is to have the agreement in place by September along with some initial applications." According to Crossland, Washington and New Jersey are also in discussions with the FBCA."
"Barack Obama served three terms in the Illinois Senate from 1997 to 2004, when he was elected to the United States Senate. During this part of his career, Obama continued teaching constitutional lawpart time at the University of Chicago Law School as he had done as a Lecturer from 1992 to 1996, and as a Senior Lecturer from 1996 to 2008.[1][2][3]"
"Meeting Riconosciuto and Gunderson at the hotel were two representatives of the mujahadeen, waiting to discuss their armament needs. One of the two was named "Ralph Olberg." The other one was called Tim Osman (or Ossman [Office of Strategic Services (OSS)!]).
"Ralph Olberg" was an American businesman who was leading the procurement of American weapons and technology on behalf of the Afghan rebels. He worked through the Afghan desk at the U.S. State Department, as well as through Senator Hubert Humphrey's office. Olberg looked after the Afghanis through a curious front called MSH - Management Sciences for Health.
The other man, dressed in Docker's clothing, was not a native Afghan any more than Olberg was. He was a 28-year-old Saudi. Tim Osman (Ossman) has recently become better known as Osama Bin Ladin. "Tim Osman" was the name assigned to him by the CIA for his tour of the U.S. and U.S. military bases, in search of political support and armaments."
"The Office of Strategic Services (OSS) was a wartime intelligence agency of the United States during World War II, and a predecessor of the modern Central Intelligence Agency (CIA). The OSS was formed as an agency of the Joint Chiefs of Staff (JCS)[3] to coordinate espionage activities behind enemy lines for all branches of the United States Armed Forces. Other OSS functions included the use of propaganda, subversion, and post-war planning. On December 14, 2016, the organization was collectively honored with a Congressional Gold Medal.[4]"
"Nathaniel Mayer Victor Rothschild, 3rd Baron Rothschild, (1910-1990), was a biologist, a cricketer, a wartime officer for the UK Security Service (MI5), a senior executive with Royal Dutch Shell and N M Rothschild & Sons, and an advisor to the UK governments.
Early life
Known throughout his life as Victor, he was the third child and only son of Charles and Rozsika Rothschild. The family home was Tring Park Mansion. He had three sisters, Miriam (1908–2005) who became a distinguished entomologist, Nica (1913–1988), who became a patron of highly influential jazz musicians, and Elizabeth, known as Liberty (1909–1988).
He attended Harrow and Trinity College Cambridge, where he worked in the Zoology Department before gaining a PhD in 1935. At Trinity College, Cambridge, he read Physiology, French and English. While at Cambridge Victor was said to have a playboy lifestyle, enjoying water-skiing in Monaco, driving fast cars, collecting art and rare books and playing cricket for the University and Northamptonshire. Victor married Barbara Hutchinson in 1933, and the couple had three children, Sarah Rothschild (b.1934), Nathaniel Charles (Jacob) Rothschild (b.1936) and Miranda Rothschild (b. 1940). The marriage was later dissolved.
Victor became the third Lord Rothschild in 1937 on the death of his uncle Walter. He sat as a Labour Party peer in the House of Lords, but spoke only twice there during his life (both speeches were in 1946, one about the pasteurization of milk, and another about the situation in Palestine).
Wartime service
During the Second World War Victor worked for the Intelligence Service, and earned the George Medal for his bomb disposal work. In early 1939, he travelled to the United States where he visited the White House to discuss the issue of accepting Jewish refugees from Nazi Germany. In 1939, he was recruited to work for MI5 where he remained for the duration of the War. He was attached to B division, under deputy director Guy Liddell, responsible for counterespionage. In 1940 he produced a series of secret reports on German Espionage Under cover of Commerce and later founded section 'B1c' at Wormwood Scrubs, the wartime home of MI5. This was an 'explosives and sabotage section', and worked on identifying where Britain's war effort was vulnerable to sabotage and counter German sabotage attempts. This included personally dismantling examples of German booby traps and disguised explosives. For this, he was awarded won the George Medal in 1944 for dangerous work in hazardous circumstances. This involved dismantling a pair of German time bombs concealed in boxes of Spanish onions in Northampton. By late 1944, Victor was attached to the 105 Special Counter Intelligence Unit of the SHAEF, a joint operation of MI5 and X2, the counterespionage branch of OSS, a precursor of the CIA, operating in Paris."
"Serco Receives "Supplier of the Year" from Boeing for Enterprise Architecture Expertise
We are extremely honored to receive this recognition for our work in support of Boeing. This prestigious award demonstrates our passion for excellence and ability to apply Serco’s Enterprise Architecture expertise across a broad range of applications.
RESTON, VA (PRWEB) MAY 19, 2011
Serco Inc., a provider of professional, technology, and management services to the federal government, has been recognized as Supplier of the Year by The Boeing Company in the Technology category for its state-of-the-practice Enterprise Architecture solutions.
The Boeing Supplier of the Year award is the company's premier supplier honor, presented annually to its top suppliers in recognition of their commitment to excellence and customer satisfaction. This year's 16 winners represent an elite group among more than 17,525 active Boeing suppliers in nearly 52 countries around the world. This selection was based on stringent performance criteria for quality, delivery performance, cost, environmental initiatives, customer service and technical expertise. This is the second time Serco has been recognized as Supplier of the Year by Boeing. In January 2011, Serco also received the Boeing Performance Excellence Gold Award in recognition of the Company's performance excellence.
"We are extremely honored to receive this recognition for our work in support of Boeing. This prestigious award demonstrates our passion for excellence and ability to apply Serco’s Enterprise Architecture expertise across a broad range of applications,” said Ed Casey, Chairman and CEO of Serco. "We continue to grow our EA practice, and over the past 15 years we have deployed solutions to support enterprises and systems across federal and commercial environments."
Serco's Enterprise Architecture Center of Excellence is based in Colorado Springs, CO. The team provides a variety of services in support of Boeing’s business units as well as research and development efforts. Serco’s architecture employs object-oriented (OO)/Unified Modeling Language (UML) to define, design and satisfy defense agencies’ mission-critical requirements, including Command, Control, Communications, Computers and Intelligence (C4I). This approach improves system developer’s understanding of operational requirements and how best to integrate enterprise operations and systems for the optimal fulfillment of C4I and other operational needs."
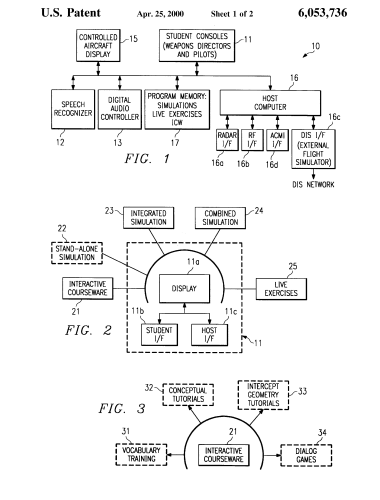
Southwest Research Institute's (SwRI) Interactive training system for AWACS weapons directors Priority date 1997-10-17 2000-04-25 US6053736A Grant Abstract A training system for training AWACS weapons directors. The training system is programmed so that the student can select between a number of different training modes. These include interactive courseware, simulation, and live exercise modes. The system includes a voice recognition unit that is trained to recognize AWACS terminology and to interactively teach them.
Darren Rubin's Biological active bullets, systems, and methods US9200877B1
Airliner irreversible-control anti-hijack system 2005-01-18 US6845302B2 Grant including ATI (automatic/tranquil-Infusion)
Howard Lutnick's Real-time interactive wagering on event outcomes CA 2460367 A.
"Jerome H. Lemelson's Prisoner tracking and warning system and corresponding methods US6054928A A system and method for tracking, monitoring and learning prisoner or parolee behavior involves obtaining prisoner or parolee data and monitoring data for at least one individual prisoner or parolee, storing the prisoner or parolee data and monitored data into a database, learning prisoner or parolee behavior from the prisoner or parolee data and the monitored data in the database, and updating the prisoner or parolee data and the monitored data in the database. Expert system (i.e. including but not limited to fuzzy logic, reinforcement learning, neural networks, artificial intelligence, etc.) algorithms are executed for determining and analyzing deviated behavior by the prisoner or parolee. A parole level is assigned to the prisoner or parolee and it is determined whether the prisoner or parolee is to be moved up or down a parole level depending on whether the prisoner or parolee behavior does not constitute or does constitute prisoner or parolee violations. Furthermore, the system tracks, monitors, and learns the behavior of the prisoner or parolee by controlling and regulating the permitted/prohibited locations or sectors, the permitted/prohibited location or sector dwell times, the permitted/prohibited travel routes, the permitted/prohibited travel times that the prisoner or parolee spends at or between various locations."
"BAE Systems PLC Proximity fuze Priority 1998-12-23 2004-12-28 US6834591B2 Grant. Abstract A proximity fuze for use in a tube launched projectile carrying a payload, comprising an oscillator for generating a radio frequency signal which has a varying frequency, a single antenna for transmitting the radio frequency signal and for receiving an echo of the radio frequency signal, a first signal processor for generating a range signal corresponding to the time delay between the transmission of the radio frequency signal and the receipt of the echo signal, second signal processor for comparing the range signal with a reference signal and depending on the result of the comparison generating an activation signal for activating the payload, wherein a directional coupler is used for coupling the radio frequency signal from the oscillator to the antenna and to the signal processor and for coupling the echo signal from the antenna to the signal processor, and wherein the second signal processor comprises a threshold detector, a peak detector and a comparator, the threshold detector being for allowing the comparator to utilise the output from the peak detector only once the range signal has reached a predetermined magnitude."
Darren Rubin's Biological active bullets, systems, and methods 2015-12-01US9200877B1 Grant A novel biological active bullet able to be discharged from a firearm, the ammunition essentially comprising a bullet in a cartridge, the bullet associated with/containing at least one biological active substance, along with a method of use of delivering with this bullet at least one biological active substance having at least one biological effect in the target upon impact and penetration, in addition to the bullet wound, and thus, having additional functions and applications than prior art bullets.
"Jerome H. Lemelson's Friend or foe detection system and method and expert system military action advisory system and method 2000-12-26 US6166679A Grant Abstract A friend or foe detection system and method is disclosed. Friend or foe warning unit 20 has a geographic locating system, a communication system for communicating with each of the warning units, and a military force detection system for detecting military forces in a combat area and has a signal routing and control circuitry 50 for controlling operations. A number of components, devices, or sub-systems, such as a transmitter/receiver radio 28, an antenna 26, a microphone 30, a speaker 32, a battery 34, a display 36, a microprocessor 38, a memory 40, a camera 56, a radar/lidar input 54, on/off switch 52, a GPS location system 45 that includes a GPS processor 46, a GPS receiver 42, a GPS antenna 44, are coupled to the circuitry 50. Display 36 provides a display to the user of the unit 20 and shows the location of friendly forces as well as unfriendly or unidentified forces in the area. Display 36 displays text messages for the user of the warning unit 20. The microprocessor 38 together with memory 40 provide microprocessor control of the operations of the warning unit 20. The geographic locating system includes GPS processor 46, GPS receiver 42, and GPS antenna 44, and it is used to determine the exact location of the warning unit 20. The unit 20 is able to broadcast and receive military force information, such as location and status (i.e. friendly, unfriendly, unidentified statuses). An expert system military action advisory system and method for advising military troops or personnel of firing decisions is also disclosed. A firing index is determined based on the membership variables, and the firing index is used to help make the firing decisions. The membership variables and the firing index are defined for an expert system or fuzzy logic system, and the expert system or fuzzy logic system helps determine making the firing decisions. The system and method operate by transmitting target and friendly force GPS coordinate information to determine danger. Alternatively, only target coordinates are transmitted with fire danger indices calculated on a distributed basis by individual warning units and transmitted to the source of fire without friendly force location coordinates to assist in making final firing decisions."
"Boeing Co's Encryption for asymmetric data links Priority date 2001-05-04 US 7023996B2 Grant Abstract A method is provided for asymmetrically encrypting data communicated between a ground platform and multiple airborne platforms. The method includes packet encrypting ground-based data so as to preserve routing information while encrypting the remaining data. The packet-encrypted data is then transmitted to the airborne platforms. The method also includes bulk encrypting airborne-based data so as to maximize security. The bulk-encrypted data is then transmitted to the ground platform."
"Vencore Services and Solutions Inc, Cyveillance Inc Social Engineering Protection Appliance 2015-09-01 US9123027B2 Grant Abstract Methods and systems for detecting social engineering attacks comprise: extracting one or more non-semantic data items from an incoming email; determining whether the one or more non-semantic data items match information stored in a data store of previously collected information; performing behavioral analysis on the one or more non-semantic data items; analyzing semantic data associated with the email to determine whether the non-semantic data matches one or more patterns associated with malicious emails; and based on the determining, performing, and analyzing, identifying the email as potentially malicious or non-malicious. The system also includes processes for collecting relevant information for storage within the data store and processes for harvesting information from detected social engineering attacks for entry into the data store and seeding of the collection processes.
"Motorola Solutions Inc's Dynamic encryption key selection for encrypted radio transmissions 1993-06-22 US5222137A Grant Abstract A radio (100) transmits and receives encrypted signals having unencrypted key identifiers, allowing other radios having the corresponding key identifiers and encryption keys to communicate with radio (100). Prior to transmitting an encrypted message, radio (100) selects a unique key identifier automatically and uses the corresponding encryption key to encrypt the message that will be transmitted. Radio (100) transmits the key identifier in an unencrypted format with the encrypted message in order to allow other radios to determine the encryption key used in encrypting the message. When receiving an encrypted message, radio (100) uses the predetermined process stored in the radio (100) to properly select the proper encryption key for use in decrypting the incoming message."
AWACS Weapons Directors – In a recent exercise, ROADRUNNER '98, several agencies interacted to create several battlespace missions in which "friendly" fighter aircraft and command and control crewmembers participated as trainees, while supporting roles and enemy forces were either played by operational personnel (virtual players) or created by intelligent agent technology (constructed forces).
"QinetiQ Acquires Cyveillance, Inc. to Strengthen Cyber Security Dominance with Leading Open Source Intelligence Solutions Combined Services Will Offer Comprehensive, Superior Intelligence Solutions to Both Commercial and Government Customers
May 06, 2009 08:57 AM Eastern Daylight Time
ARLINGTON, Va.--(BUSINESS WIRE)--Cyveillance today announced that it has signed an agreement to be acquired by QinetiQ North America, a provider of information technology and engineering solutions to the U.S. government. Under terms of the agreement, pending regulatory approval, Cyveillance will become a QinetiQ North America subsidiary. The company will continue to deliver Internet risk and threat intelligence to commercial organizations worldwide, while providing QinetiQ North America with the technology and expertise to enhance its innovative government-focused Cyber Security and Intelligence solutions."
"Cyveillance launches Cyber Threat Centre
Posted 17 September 2014 · Add Comment
QinetiQ company Cyveillance, has launched its comprehensive cloud-based intelligence platform, the Cyber Threat Centre.
The Centre allows security and risk professionals to undertake their own collection and analysis of online threat intelligence, and to identify and respond to threats faster and more effectively.
The Cyber Threat Centre combines web search, social media monitoring, global intelligence reports, and a suite of investigative tools and databases in an easy-to-use, cloud-based portal. Professionals who are responsible for physical and IT security, incident response, cyber investigations, and online compliance can distill information from thousands of sources outside the firewall into useable intelligence, tailored for their business needs.
"The Cyber Threat Centre is built on our experience from more than 16 years in the cyber security industry," said Cyveillance President Scott Kaine. “It is the natural evolution of our offerings. By taking advantage of the fact that we have already done the work of collecting and tagging vast amounts of data, the Cyber Threat Centre enables security and risk professionals to spend more time on analysis, and less time searching and configuring multiple different portals and data feeds."
The Centre gives organizations access to the same powerful sources, tools and databases already used by Cyveillance analysts, as well as extensive data for cyber investigations and better intelligence. Cyveillance continues to grow its traditional threat analyst practice, which provides tailored, customer-specific threat intelligence to organisations around the world.
"The Cyber Threat Centre is a user-friendly, scalable offering that puts the tools directly in the hands of our global customers and partners," added Sanjay Razdan, Managing Director for QinetiQ New Technologies."
"Serco Receives "Supplier of the Year" from Boeing for Enterprise Architecture Expertise
RESTON, VA (PRWEB) MAY 19, 2011 Serco Inc., a provider of professional, technology, and management services to the federal government, has been recognized as Supplier of the Year by The Boeing Company in the Technology category for its state-of-the-practice Enterprise Architecture solutions. … Serco's Enterprise Architecture Center of Excellence is based in Colorado Springs, CO. The team provides a variety of services in support of Boeing’s business units as well as research and development efforts. Serco's architecture employs object-oriented (OO)/Unified Modeling Language (UML) to define, design and satisfy defense agencies’ mission-critical requirements, including Command, Control, Communications, Computers and Intelligence (C4I). This approach improves system developer's understanding of operational requirements and how best to integrate enterprise operations and systems for the optimal fulfillment of C4I and other operational needs.
About Serco Inc.: Serco Inc. is a leading provider of professional, technology, and management services focused on the federal government. We advise, design, integrate, and deliver solutions that transform how clients achieve their missions. Our customer-first approach, robust portfolio of services, and global experience enable us to respond with solutions that achieve outcomes with value. Headquartered in Reston, Virginia, Serco Inc. has approximately 11,000 employees, annual revenue of $1.5 billion, and is ranked in the Top 30 of the largest Federal Prime Contractors by Washington Technology. Serco Inc. is a wholly-owned subsidiary of Serco Group plc, a $6.6 billion international business that helps transform government and public services around the world. More information about Serco Inc. can be found at http://www.serco-na.com."
"Motorola announced that their semiconductor division would be divested on October 6, 2003, to create Freescale. Freescale completed its IPO on July 16, 2004.
On September 15, 2006, Freescale agreed to a $17.6 billion buyout by a consortium led by Blackstone Group and its co-investors, Carlyle Group, TPG Capital, and Permira.[26] The buyout offer was accepted on November 13, 2006, following a vote by company shareholders. The purchase, which closed on December 1, 2006, was the largest private buyout of a technology company until the Dell buyout of 2013 and is one of the ten largest buyouts of all time.[27]
Freescale filed to go public on February 11, 2011, and completed its IPO on May 26, 2011. Freescale is traded on the New York Stock Exchange under the ticker symbol FSL. At the time of the IPO, the company had $7.6 billion in outstanding debt on its books,[28] and the company is being investigated for misconduct related to this IPO.[29]"
"Serco suffers profits collapse but on 'path to recovery' says CEO
Troubled outsourcer Serco details full extent of its woes and kicks off £555m rights issue
By Alan Tovey, Industry Editor 11:22AM GMT 12 Mar 2015
Troubled outsourcer Serco has launched a £555m rights issue as it starts on what chief executive Rupert Soames called "the path of recovery". Shares in the company, which had more than half a billion pounds wiped off its market value in November when it stunned the market with a huge profit warning, [after fraudulently charging UK government for transporting fake prisoners in Con Air SWAT teams] tumbled again as Mr Soames set out the full extent of the Serco's troubles. … The company's rights issue, on which Rothschild is advising cf Victor Rothschild, Pearl Harbor and the Henry Tizard Patent Pool, will see 549m new shares issued. The scheme is on a 1:1 basis and is priced at 101p, a deeply discounted 51.1pc compared with the previous closing price, and a 34pc discount on theoretical ex-rights price. The fundraising – which is subject to shareholder approval – is fully underwritten and the proceeds will be used to cut Serco's debt by £450m. At the end of the year Serco's net debt stood at £682m. The company said that subject to the rights issue's completion, it had struck an agreement with its creditors to refinance its funding."
"Boeing Begins World Headquarters Operations in Chicago
The Boeing Company began operations on schedule today [Sep 4, 2001] at its new world headquarters building in downtown Chicago.
Approximately 200 employees began unpacking and familiarizing themselves with the building, located on the Chicago River at 100 North Riverside. The company expects approximately 400 employees to be working on the building's top 12 floors by the end of the year.
Boeing and a team of more than 70 subcontractors, vendors and consultants delivered the finished office space, sophisticated telecommunications system, and computing infrastructure on schedule after 117 days of focused, intense effort. The aggressive schedule was driven by the company's commitment to employees with families to coordinate the opening with local school schedules.
Boeing Chairman and CEO Phil Condit - who will officially commemorate the opening of the new Boeing World Headquarters during a ceremony at the building tomorrow - announced in March a broad rearchitecture of the company that included the headquarters relocation. In addition, the leaders of the company's business units were given increased authority and responsibility to run their operations based on the needs of their customers, markets and communities where they do business.
"Boeing is in the midst of many exciting changes, and our new world headquarters in Chicago is part of our ongoing transformation," Condit said. "We intend to grow our enterprise here and create businesses that open frontiers and advance technology, while allowing our business leaders in other locations to drive their businesses to their full potential."
The building is designed with a vision of instant access to information by anyone from anywhere. More than 225 miles of data, communications and security cable were installed to support the more than 300 computers and 500 telephones needed on opening day.
Office spaces have been equipped with more than 3,000 data and telephone connections to support future information technology advancements along with systems needed to meet the goal of wireless connectivity in the future Boeing employees in Chicago are just a mouse click away from any Boeing facility, customer or supplier in 145 countries. Boeing employees, customers and suppliers visiting the new world headquarters will find a number of "mobile desk" touchdown spaces that provide Internet and LAN access, and equipment needed to be productive while away from their home offices."
Consider assisting Abel Danger's David Hawkins with his Reverse Engineering CSI storyboards by going to Patreon to take back the narrative on crime scenes the media will not report on. Abel Danger (AD) started as a two man team back in 2006. That was when aviation pilot whistleblower Field McConnell contacted David Hawkins, a Cambridge graduate and global forensics economist. Over a decade later, a globally based network of average people join us to listen, share and partake in our C2CSI (Cloud Centric Crime Scene Investigations). We invite you to help fund us through Patreon to prepare presentation treatments and plot points for up to five injured-community theater clubs where David and the AD team will describe in a series of ten minute videos the suggested names for each clubs, the cast of real characters to be played and the story lines which connect plot points and wrongful deaths with the use of patented devices at some of the most iconic crime scenes of recent times.
https://www.patreon.com/user?alert=2
Posted from my blog with SteemPress : https://www.abeldanger.org/reverse-csi-10-twin-towers-radio-drama-con-air-marcys-ganci-snuff-first-ladies-ip-amerithrax-bridge/