Winners announcement of the July contest #1 by sduttaskitchen|Advanced technology opens the door to advanced crimes!
 |
|---|
Greetings, everyone
| Here is the time to announce the winners of the first contest of July that was announced by methe-july-contest-1-by-sduttaskitchen-or-advanced-technology-opens-the-door-to-advanced-crimes |
|---|
The concept presented herein arose from my experience with a phishing attack on the Steemit platform. At that time, I received considerable assistance from @randulakoralage. It was during this incident that I first encountered the terminology associated with "phishing attacks."
On the morning of the event, I awoke to messages from her inquiring, "Have you engaged in this activity?" Surprised, I responded with, "What?" She prompted me to check my account, and upon doing so, I discovered that someone had sent fraudulent messages purportedly from my account.
Randulakoralage recommended that I change all of my security keys. Fortunately, I did not suffer any financial loss in terms of Steem. However, after modifying my keys, I proactively communicated with all contacts to clarify that the unauthorised activity was not conducted by me and advised them not to click on any suspicious links.
Before announcing the winners, I would like to thank all participants for their meaningful engagement in the contest. Your contributions have been invaluable.
| Hashtags | #sdk-july1, #techvsadvcrime |
|---|---|
| Total number of entries | 22 |
| Number of Valid entries | 21 |
| Number of Invalid entries | 01 |
Club Status | Number of entries |
|---|---|
| Club5050 | 16 entries. |
| Club75 | 00 entries. |
| Club100 | 02 entries. |
| No Club | 04 entries. |
| Position |
|
|
|
|---|---|---|---|---|
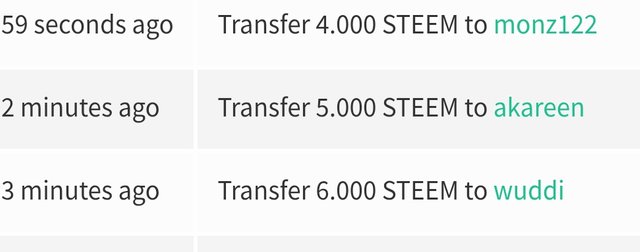
| @wuddi | Post link | 6 Steem |  | |
| @akareen | Post Link | 5 Steem |  | |
| @monz122 | Post Link | 4 Steem |  |
|
|---|
 |
|---|
- Author:-@wuddi
- Club Status-#club100
- Country- UK
For example over here we have recently such fraud when the elderly people will be phoned and the number looks like of police, they say that the son or daughter or a person had caused an accident and in custody and need immediately money to pay for deposit for release.
Indeed, this phenomenon is increasingly prevalent in today's society. Certain individuals impersonate high-ranking government officials and resort to intimidation by presenting deceptive arguments.
The author provided essential insights, particularly for senior citizens who may not be accustomed to using smartphones. I found the content highly informative, which is why I have nominated the post for first place recognition..
 |
|---|
- Author-@akareen
- Country- Nigeria
- Club Status-#club5050
In Nigeria, youths who engage in these illegal activities are called 'yahoo boys,' and they use another person's social media identity, such as Facebook, for fraud by collecting money from people whom they promise to help buy goods. Once they receive the money, they block the victim from accessing their account again. This advanced technology draws the attention of people to commit crimes, such as using computers or smartphones, which are increasingly used to commit online fraud or cybercrimes.
Examine the ways in which individuals perpetrate fraud and the necessity for society to identify and categorize these individuals by specific names to raise awareness among citizens. It is imperative that we exercise caution before placing our trust in any online applications, and it is equally important to educate both children and the elderly to minimize the risk of falling victim to such schemes. Accordingly, I have nominated this post for inclusion in the winners list.
 |
|---|
- Author-@monz122
- Country- India
- Club Status-No Club
Day by day with the advancement of technology malware attacks are also increasing in the world of technology with the sole motive of damaging the device. Other crimes in the name of investment different different sites are looting people and making them fool in the name of multiplying their capital.
The hackers have now became too smart to fool people and innocent people are being trapped by them so before finding any modern technology it is must that we should keep a check that whether our personal information should not be leaked in the form of data.
In the above noted text, the author articulates how advanced technology, particularly smartphones, can be utilized to target vulnerable individuals. During busy periods, individuals often receive messages and calls that can disrupt their focus. As a result of this distraction, they may inadvertently click on links or respond to communications that enable hackers to infiltrate their devices. I found the post to be highly informative; therefore, I have nominated it for inclusion in the winners' list.
|
|---|
I hope those who participated in the contest comprehend the significance of the subject, and I hope in the future;
A few more friends would come to participate in our upcoming contests.
I thoroughly enjoyed reading our friend's viewpoints and creations related to the topic. Congratulations to all the winners.
|
|---|
|
|---|
50 Sp 100 Sp 150 Sp 200 Sp 250 Sp 300 Sp 350 Sp 400 Sp 450 Sp 500 Sp 600 Sp 700 Sp 800 Sp 900 Sp 1000 Sp
1500 Sp 2000 Sp 2500 Sp 3000 Sp
| OUR COMMUNITY DISCORD LINK:- |
|---|
|
|---|
|
|---|
Incredible India Community twitter link
|
|---|
Incredible india Instagram Link
Stay Tuned with our Incredible India Community, and continue your journey by sharing various quality content. |
|---|
 |
|---|
Thankyou so much for choosing my post mam!
যে সকল ইউজার এই সুন্দর প্রতিযোগিতায় বিজয়ী হয়েছে তাদেরকে অভিনন্দন ও শুভেচ্ছা জানাই।
Congratulations all winner